Enforce adaptive policies and advanced secure access controls across all resources, access interfaces and users in the hybrid environment
Silverfort integrates with all the identity providers in your environment to deliver secure authentication across every resource on-prem and in the cloud.
Standard Users
Privileged Users
Service Accounts
• Desktop Logon
• PsExec
• Remote PowerShell
• RDP
• Web Browser
• File Share
• etc
• Homegrown\Legacy Apps
• Workstations & Servers
• SaaS Apps
• File Servers & Databases
• IT Infrastructure
• Cloud Workloads
• Industrial Systems
On-Prem Directories (AD, RADIUS)
Cloud IdPs (Entra ID/Azure AD, Okta, Ping)
Federation (ADFS, PingFederate)
VPNs and Proxies
PAM
• Audit access request
• Update behavioral baseline
• Provide insights and reports
• Anomaly Detection
• Known Malicious Patterns
• External Risk Indicators
• Multi Factor Authentication
• Risk Based Authentication
• Service Account Protection
Leverage Silverfort’s agentless and proxyless architecture to quickly and easily cover all your users and resources without blind spots, increasing their identity protection from day one.
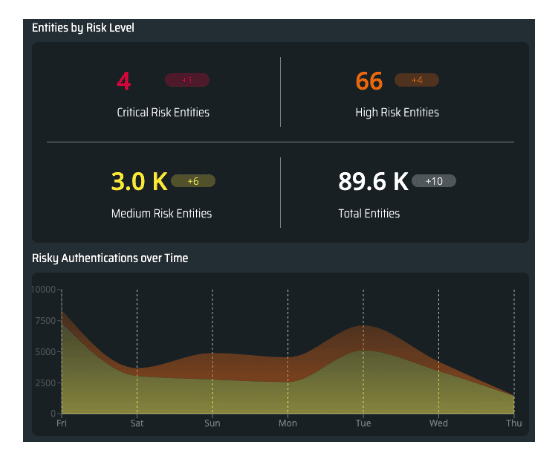
Ingest and correlate all authentication and access requests from all users to detect risk via anomalous behavior, malicious traffic patterns and external risk feeds.
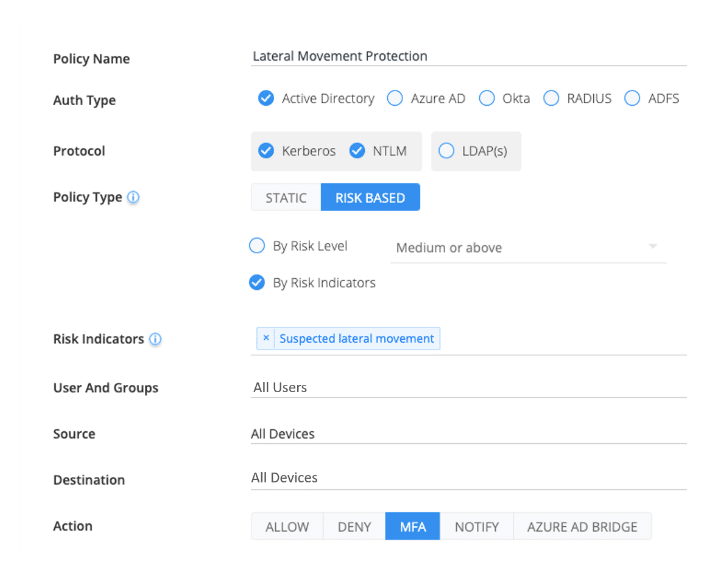
Proactively prevent threat actors from using compromised credentials to access on-prem and cloud resources by configuring access policies.
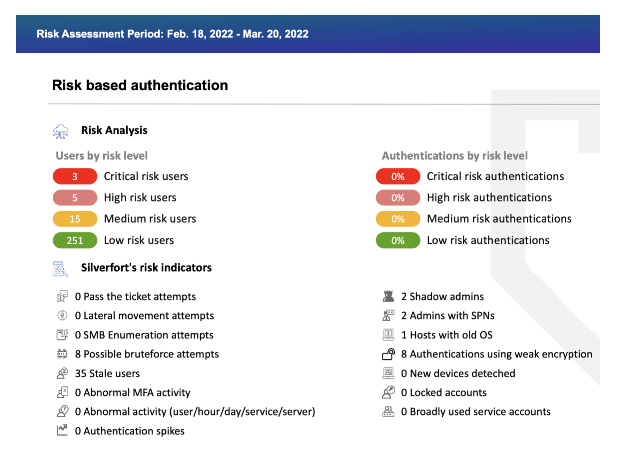
Gain real-time visibility into users’ login activities with alerts and custom reports tailored to your specific needs, so you can optimize inventory management, compliance and security operations.
Silverfort Unified Identity Protection is founded on four core technologies:
01
Monitor and control all authentication traffic without agents, proxies or modification of applications’ code
02
Gain insight into encrypted authentication protocols in real time without decryption (no need for keys, no exposure of secrets).
03
Correlate and analyze all user and machine access across all IAM platforms with a unified AI-based engine.
04
Act as a translator between different protocols and IAM solutions to connect all resources into a cloud IAM platform.