Privileged Access Management
Protect your privileged accounts from compromise quickly and seamlessly with adaptive access policies that enforce MFA protection on all on-prem and cloud resources.

Accelerate Your PAM Deployment
Speed up your PAM rollout by automatically discovering all service accounts in your environment (as well as mapping their dependencies) and identifying any shadow admins.

Protect Accounts That Can’t Be Vaulted
Ensure end-to-end protection of all privileged access currently residing outside the PAM solution, including service accounts with hard-to-map dependencies and any other admin accounts.

Enforce Secure Access Everywhere
Harden your PAM solution by enforcing PAM-only access on all admins while also protecting access to the PAM solution itself with MFA everywhere.
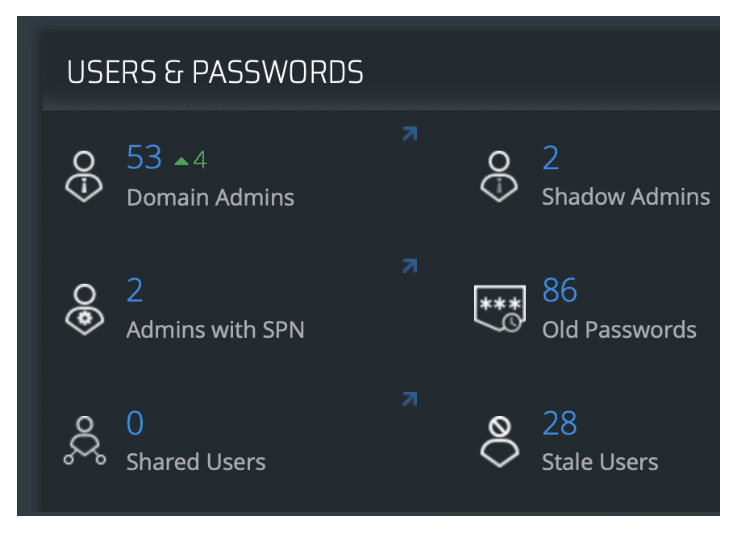
Automated admin account discovery
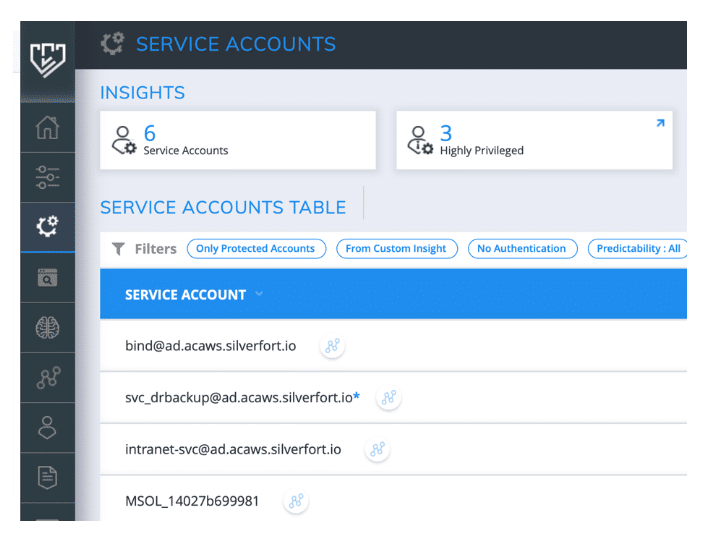
Service account protection
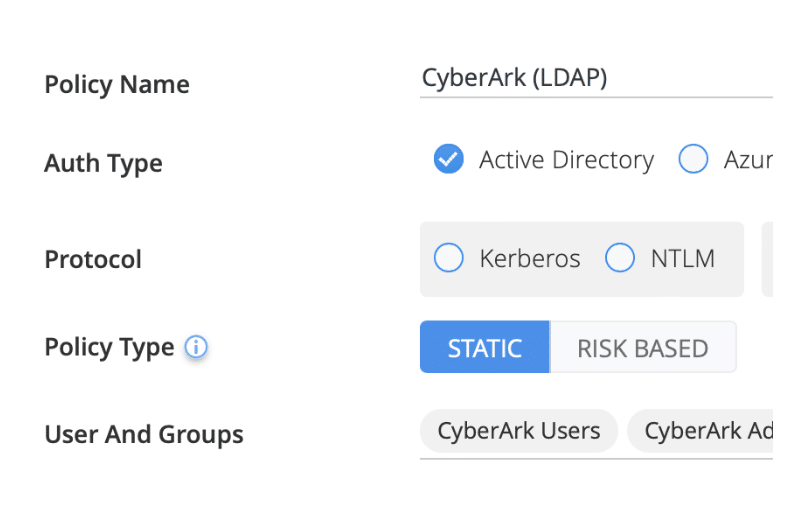
Safeguarding your PAM solution
"Since replacing my PAM solution with Silverfort, authenticating and securing my privileged users’ access has never been easier. Having a product that provides additional security controls and advanced visibility is absolutely a no-brainer.."
Katie McMillan | Lead Information Security Manager

Customer Challenge
Agilisys realized that the security of their privileged users and sensitive resources was of paramount importance. It was vital for Agilisys to secure all its users and resources with the proper level of multi-factor authentication (MFA) while deploying a scalable solution.
Silverfort Solution
Silverfort enables Agilisys to secure their privilege accounts, Remote Powershell Access, and Active Directory with multi-factor authentication in a matter of weeks, compared to PAM solutions which can often take months or even years to deploy.
How they rate us:
4.7 – 28 Reviews

We dared to push identity security further.
Discover what’s possible.
Set up a demo to see the Silverfort Identity Security Platform in action.