Deploy AI agents with confidence, not compromise
AI agents move fast and automate at scale. Silverfort keeps them secure from day one, so you can scale AI automation without expanding your attack surface.
- Discover every agent.
- Connect all agents to accountable owners.
- Enforce least privilege access.
Deploy AI agents with confidence, not compromise
AI agents move fast and automate at scale. Silverfort keeps them secure from day one, so you can scale AI automation without expanding your attack surface.
- Discover every agent.
- Connect all agents to accountable owners.
- Enforce least privilege access.
AI agents drive innovation. But at what cost?
Enterprises deploy AI agents to accelerate workflows and unlock new capabilities. But as these agents integrate with critical systems, the lack of identity controls turns them into attack vectors with business-critical access.
Agents operate outside traditional visibility
AI agents span clouds and SaaS, bypassing standard identity monitoring and creating blind spots in your security posture.
No clear ownership or accountability
Agents act autonomously, but when they access sensitive data or trigger actions, there's no chain of responsibility back to a human owner.
Overprivileged access creates exposure
Agents are granted broad permissions for convenience, yet excessive access becomes a pivot point for lateral movement, privilege escalation, and data exfiltration.
Innovation vs. control creates friction
Lock down agents too tightly and developers slow down. Leave them unsecured and risk expands. Traditional IAM wasn’t built for autonomous AI.
AI agents drive innovation. But at what cost?
Enterprises deploy AI agents to accelerate workflows and unlock new capabilities. But as these agents integrate with critical systems, the lack of identity controls turns them into attack vectors with business-critical access.
Agents operate outside traditional visibility
AI agents span clouds and SaaS, bypassing standard identity monitoring and creating blind spots in your security posture.
No clear ownership or accountability
Agents act autonomously, but when they access sensitive data or trigger actions, there's no chain of responsibility back to a human owner.
Overprivileged access creates exposure
Agents are granted broad permissions for convenience, yet excessive access becomes a pivot point for lateral movement, privilege escalation, and data exfiltration.
Innovation vs. control creates friction
Lock down agents too tightly and developers slow down. Leave them unsecured and risk expands. Traditional IAM wasn’t built for autonomous AI.
Complete visibility. Real-time control. Zero friction.
Unify AI agent discovery, risk assessment, and least privilege enforcement in one platform. Secure agent access without slowing developers or rewriting workflows.
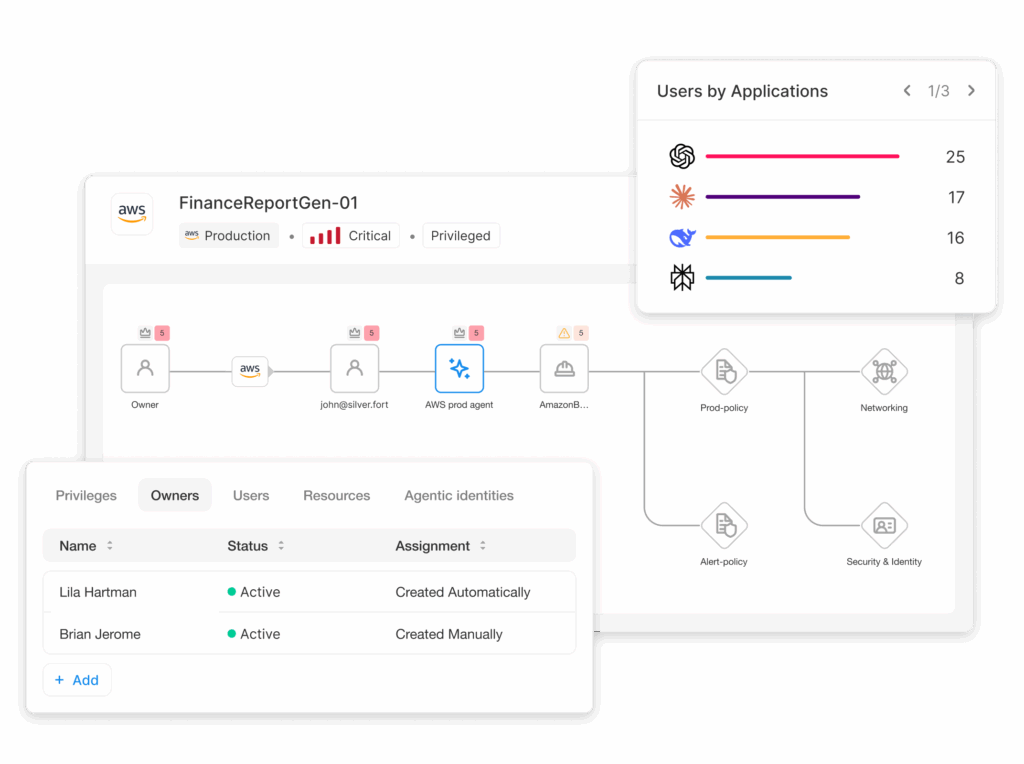
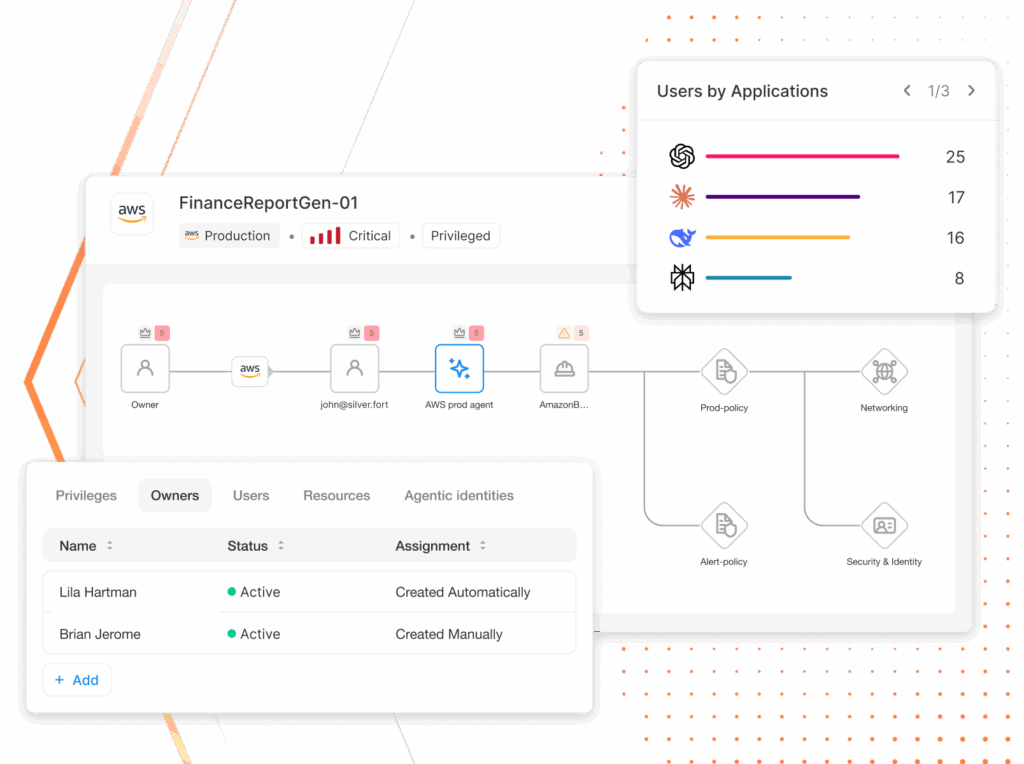
Complete agent discovery and ownership
Continuously discover all AI agents—sanctioned or rogue—across IdPs, cloud platforms, and SaaS apps. Storyline graphs map owners, roles, and access paths for full visibility with no blind spots.
Stop threats at point of action
Silverfort’s MCP gateway inspects every agent call in real time, evaluating authorization scopes before execution to block privilege escalation, lateral movement, or unauthorized access.
Deploy in days without disrupting developers
API-driven discovery requires no software or code changes. MCP enforcement integrates via a simple gateway redirect. Developers maintain velocity while security gains runtime control over agent behavior.
Critical AI agent challenges we solve every day
Shadow AI control
Discover and govern unknown agents before they become incidents.
Delegated AI governance
Enforce least privilege on every agent, preventing lateral movement and privilege escalation.
Accountability for audits
Map agent actions to responsible humans for compliance and investigations.
MCP identity control
Require approvals before agents execute sensitive tool actions (human in the loop).
NHI hardening
Apply least privilege to autonomous agents that use static API keys.
Critical AI agent challenges we solve every day
Shadow AI control
Discover and govern unknown agents before they become incidents.
Delegated AI governance
Enforce least privilege on every agent, preventing lateral movement and privilege escalation.
Accountability for audits
Map agent actions to responsible humans for compliance and investigations.
MCP identity control
Require approvals before agents execute sensitive tool actions (human in the loop).
NHI hardening
Apply least privilege to autonomous agents that use static API keys.
From shadow AI to complete control.
Auto-discover every AI agent across your environment
Silverfort connects to your IdPs (Entra ID, Okta), cloud platforms (AWS, Azure, GCP), and SaaS apps via read-only API to auto-discover every AI agent, including shadow and rogue deployments. The platform ingests identity and activity signals, normalizes the data, and builds a live agent inventory to deliver complete visibility from day zero. No blind spots. No manual tracking.
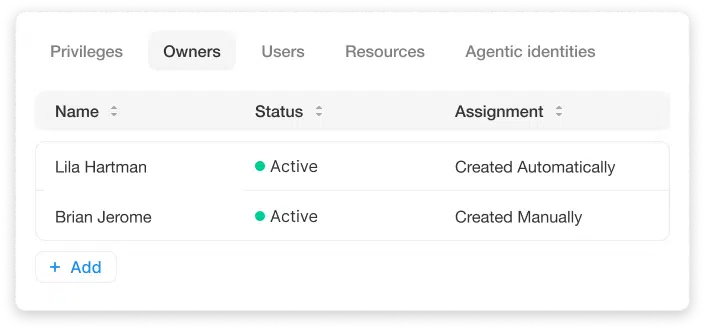
Bind each agent to a human identity
Silverfort maps each agent to its provisioning identity and human owner through visual storyline graphs showing roles, accessed resources, and permission chains.
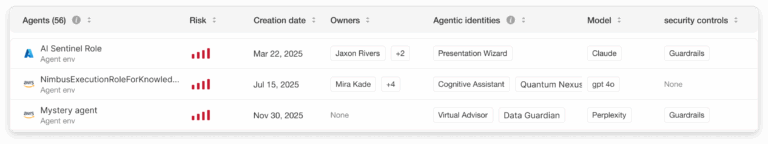
Prioritize and neutralize high-risk AI agents
Silverfort calculates dynamic risk scores based on privilege level, data sensitivity, and behavioral anomalies. High-risk agents—overprivileged, orphaned, or accessing sensitive data—are surfaced first for immediate remediation.
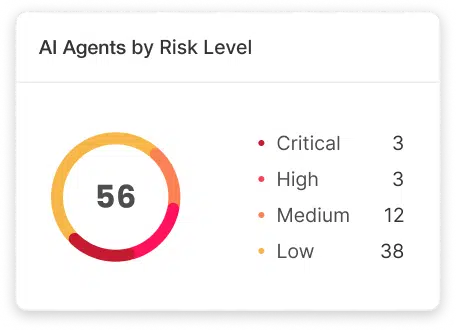
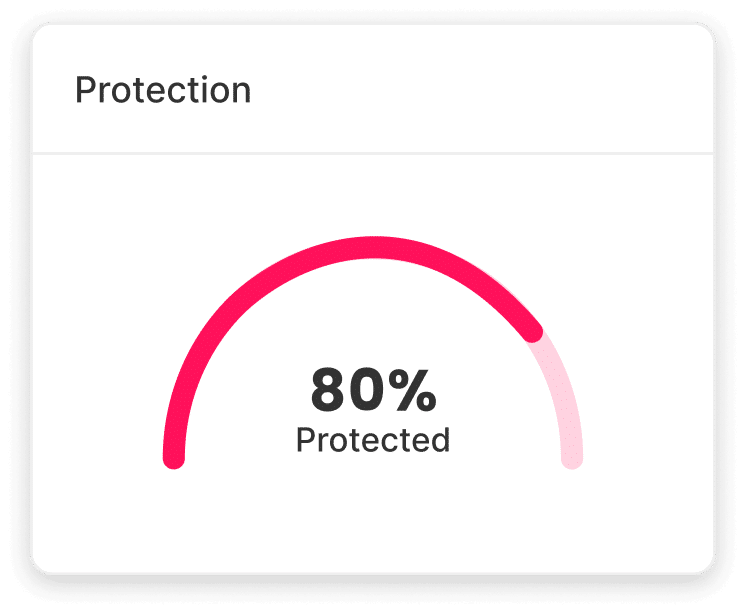
Enforce access policy on every agent call in real time
Gain control by redirecting MCP clients to your Silverfort gateway tenant URL. The gateway enforces SSO through your IdP, correlating each agent session to a human entity. Every tool call hits the gateway first. Silverfort evaluates against Authorization Planes and Scopes and denied calls block at the gateway. Permitted calls forward to backend systems and log to inventory.
From shadow AI to complete control.
Auto-discover every AI agent across your environment
Silverfort connects to your IdPs (Entra ID, Okta), cloud platforms (AWS, Azure, GCP), and SaaS apps via read-only API to auto-discover every AI agent, including shadow and rogue deployments. The platform ingests identity and activity signals, normalizes the data, and builds a live agent inventory to deliver complete visibility from day zero. No blind spots. No manual tracking.

Bind each agent to a human identity
Silverfort maps each agent to its provisioning identity and human owner through visual storyline graphs showing roles, accessed resources, and permission chains.

Prioritize and neutralize high-risk AI agents
Silverfort calculates dynamic risk scores based on privilege level, data sensitivity, and behavioral anomalies. High-risk agents— overprivileged, orphaned, or accessing sensitive data—are surfaced first for immediate remediation.

Enforce access policy on every agent call in real time
Gain control by redirecting MCP clients to your Silverfort gateway tenant URL. The gateway enforces SSO through your IdP, correlating each agent session to a human entity. Every tool call hits the gateway first. Silverfort evaluates against Authorization Planes and Scopes and denied calls block at the gateway. Permitted calls forward to backend systems and log to inventory.

How Silverfort secures AI agents at scale
Silverfort's MCP gateway sits between agents and MCP servers, inspecting every tool call in real time. Policies are checked and enforced inline - allowing, blocking, or restricting actions based on Authorization Planes and Scopes. Agents can only do what they're explicitly permitted to do. No standing privileges. No bypass.
Why Silverfort is different
Inline enforcement
Before actions are executed plus full discovery across environments
Complete human ownership mapping
Via Storyline graphs; see who provisioned each agent and who initiated each action
Real time least privilege enforcement
Via Authorization Planes and Scopes per agent
Block or restrict actions inline
Before they execute—no retroactive cleanup
No agents, no code changes, deploy in days
API driven discovery and gateway redirect for enforcement
Generic security tools
AI security niche vendors
Inspection mode
- Alert only, post incident analysis
- Behavioral monitoring, limited prevention
Inline enforcement
Before actions are executed plus full discovery across environments
Accountability
- No human to agent linkage
- Partial mapping, unclear ownership
Complete human ownership mapping
Via Storyline graphs; see who provisioned each agent and who initiated each action
Access controls
- Static policies, manual reviews
- Runtime alerts, limited enforcement
Real time least privilege enforcement
Via Authorization Planes and Scopes per agent
Prevention capability
- Detect and alert, no inline blocking
- Behavioral anomaly detection, reactive response
Block or restrict actions inline
Before they execute—no retroactive cleanup
Operational safety
- Manual configuration, high friction
- Requires instrumentation or code changes
No agents, no code changes, deploy in days
API driven discovery and gateway redirect for enforcement