Full context.
Full visibility.
Complete control.
With just partial visibility, you could leave unnecessary privileges, exposed resources, and hidden access routes open to attackers. Eliminate those blind spots by mapping every access path across environments and systems.
- Enforce least privilege everywhere.
- Reduce risk across your entire identity surface.
- Streamline operations.
Full context.
Full visibility.
Complete control.
With just partial visibility, you could leave unnecessary privileges, exposed resources, and hidden access routes open to attackers. Eliminate those blind spots by mapping every access path across environments and systems.
- Enforce least privilege everywhere.
- Reduce risk across your entire identity surface.
- Streamline operations.
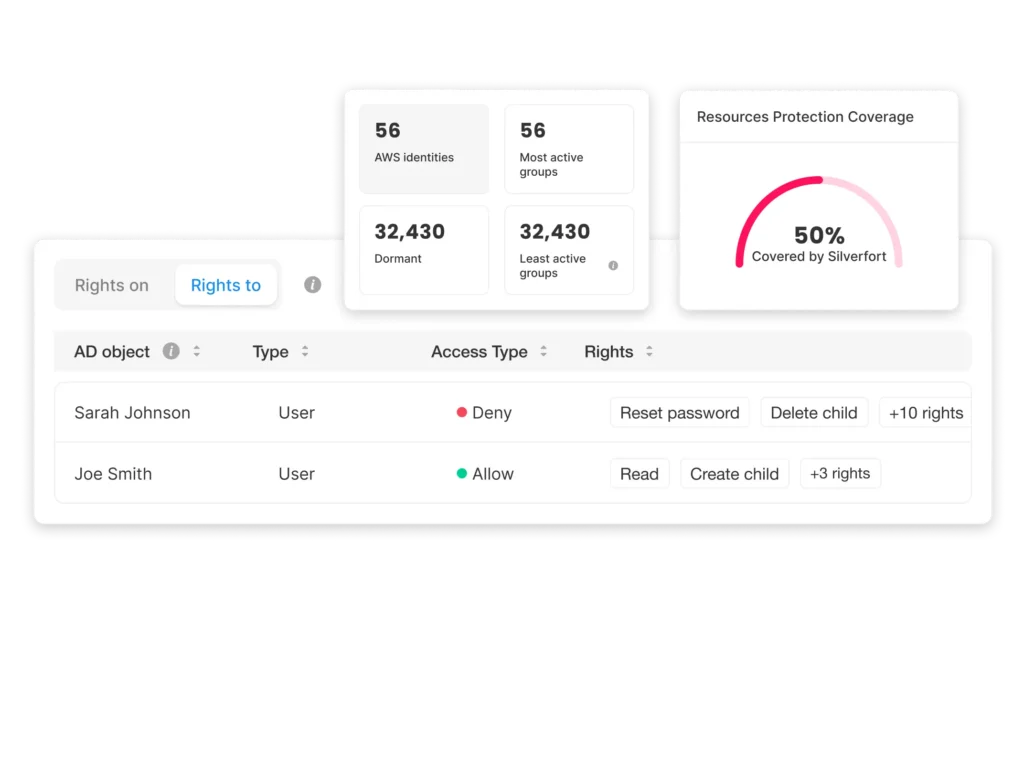
Most access paths are still hidden. Even your IAM isn’t telling you the full story.
Identity and access are never static. Privileges shift, resources expand, new technologies and apps get adopted, and with every change, new access paths emerge. Traditional tools show only a fraction of the picture, while attackers move freely across the whole landscape. They thrive in the blind spots you can’t see.
Partial visibility
Point solutions are like a city map that shows just one neighborhood, leaving hidden access paths undetected.
Privilege sprawl
Standing permissions and unused privileges accumulate, creating silent risks.
Blind to real usage
Security teams see who has access but not how they use it, missing early signs of misuse or escalation.
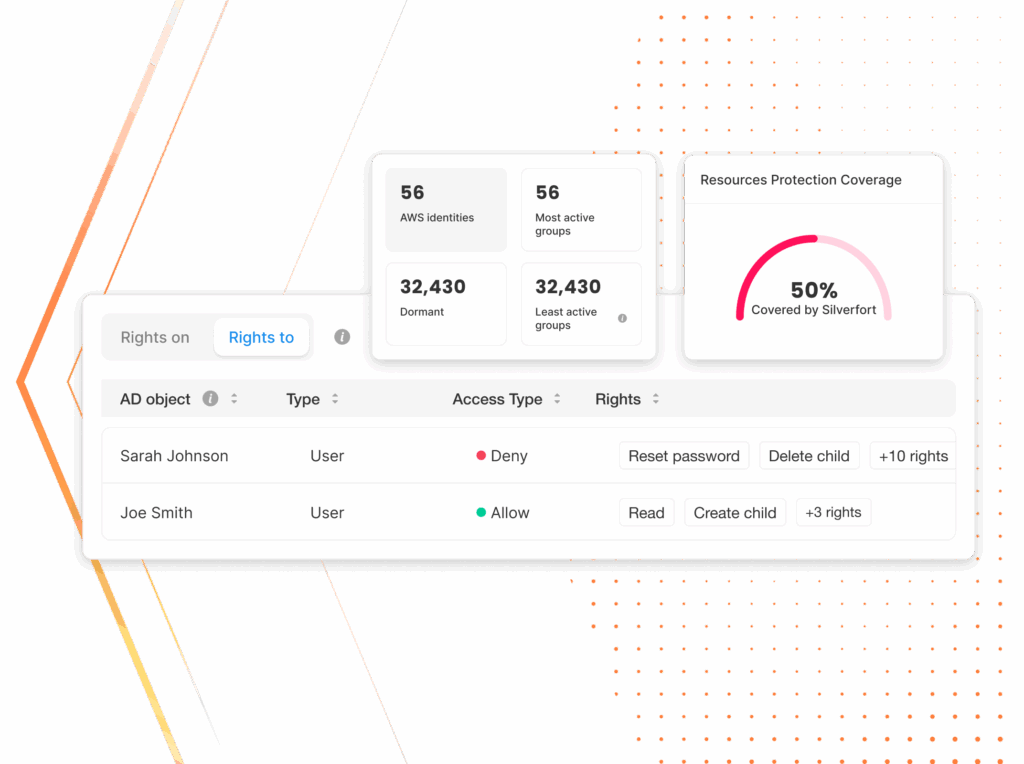
Most access paths are still hidden. Even your IAM isn’t telling you the full story.
Identity and access are never static. Privileges shift, resources expand, new technologies and apps get adopted, and with every change, new access paths emerge.Traditional tools show only a fraction of the picture, while attackers move freely across the whole landscape. They thrive in the blind spots you can’t see.
Partial visibility
Point solutions are like a city map that shows just one neighborhood, leaving hidden access paths undetected.
Privilege sprawl
Standing permissions and unused privileges accumulate, creating silent risks.
Blind to usage
Security teams see who has access but not how they use it, missing early signs of misuse or escalation.
Uncover every access path. Eliminate blind spots. Take action.
Map, analyze, and contextualize access behavior across users, service accounts, and AI agents in real time. See who is accessing sensitive resources, when, and how privileges are used across environments. Reveal hidden risks, stop privilege sprawl, and enforce least privilege—without slowing the business.
Hidden path analysis
Uncover unused, unnecessary, or unprotected access routes before attackers exploit them.
Real-time threat insights
Spot anomalies such as privilege escalation and unusual access patterns as they happen.
Real efficiency
Narrow the attack surface while streamlining audits, compliance, and access reviews.
Critical identity visibility & access intelligence challenges we solve every day
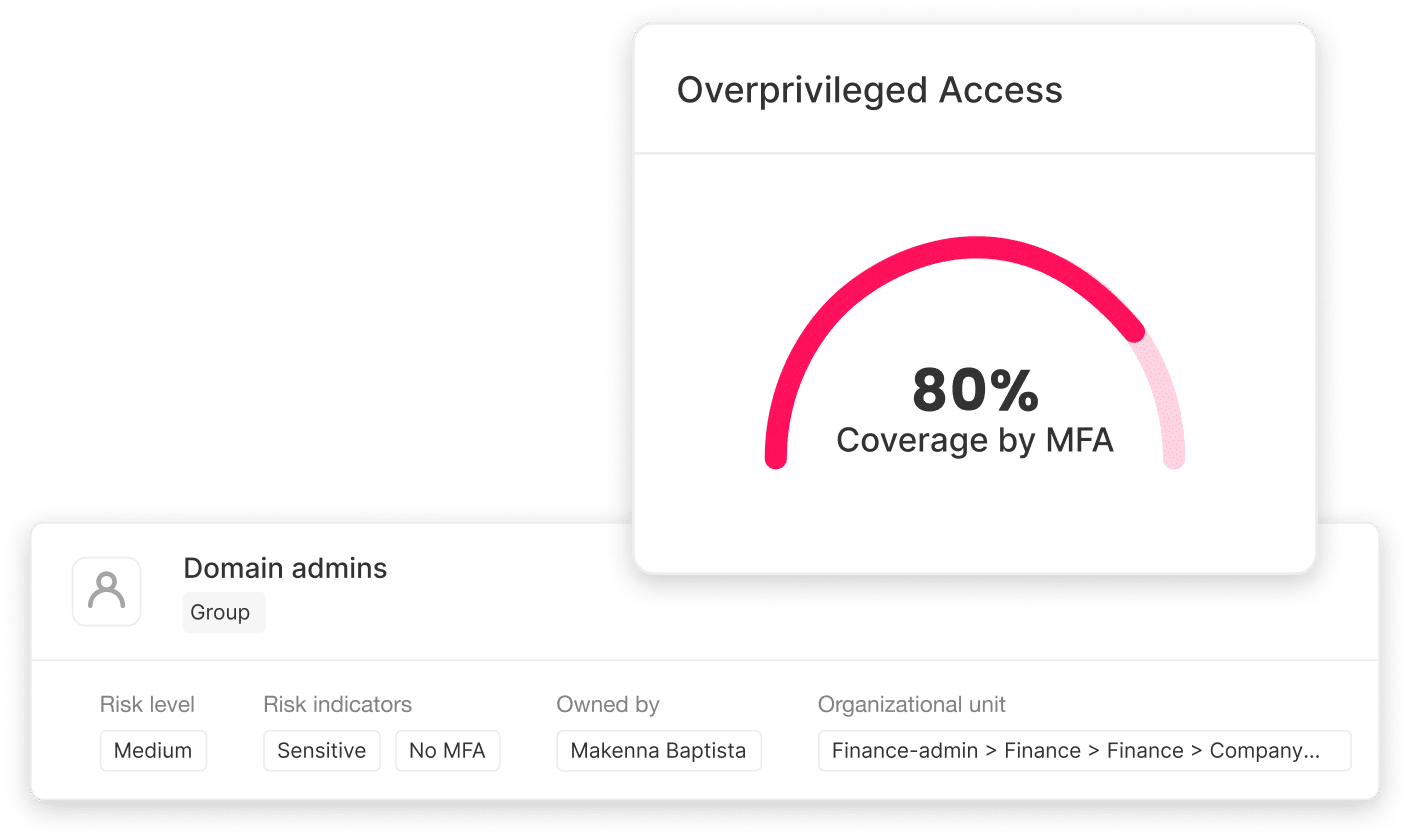
Uncover excessive and unused access
So you can safely remove standing privileges and reduce attack surface.
Detect abnormal access patterns
And spot privilege misuse or lateral movement before it escalates.
Clean up stale or orphaned permissions
Fix hygiene issues attackers often exploit.
Enforce least privilege with confidence
Backed by real usage data, not guesswork.
Meet audit and compliance requirements
With a live record of all access activity.
Accelerate investigations and breach containment
Instantly trace who accessed what, when, and how.
Cut costs by eliminating unused resources
Identify unused or shadow apps and resources for decommissioning
Maintain compliance readiness
Log and trace access to sensitive resources, supporting GDPR and other regulatory requirements.
Critical identity visibility & access intelligence challenges we solve every day
Uncover excessive and unused access
So you can safely remove standing privileges and reduce attack surface.
Detect abnormal access patterns
And spot privilege misuse or lateral movement before it escalates.
Clean up stale or orphaned permissions
Fix hygiene issues attackers often exploit.
Enforce least privilege with confidence
Backed by real usage data, not guesswork.
Meet audit and compliance requirements
With a live record of all access activity.
Accelerate investigations and breach containment
Instantly trace who accessed what, when, and how.
Cut costs by eliminating unused resources
Identify unused or shadow apps and resources for decommissioning
Maintain compliance readiness
Log and trace access to sensitive resources, supporting GDPR and other regulatory requirements.
How Silverfort fuses actionable context into every access path
From fragmented visibility to full access intelligence—automatic, interconnected, actionable.
Uncover every access path
Expose every route between identities and the resources they access—no coverage gaps.
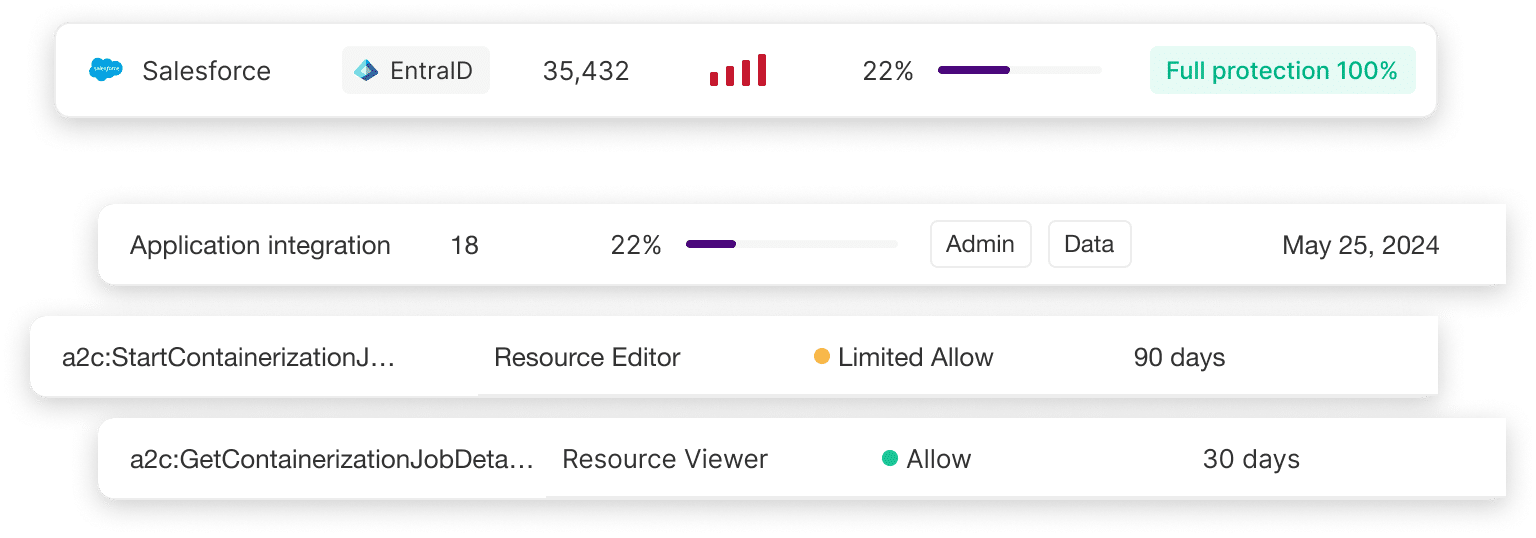
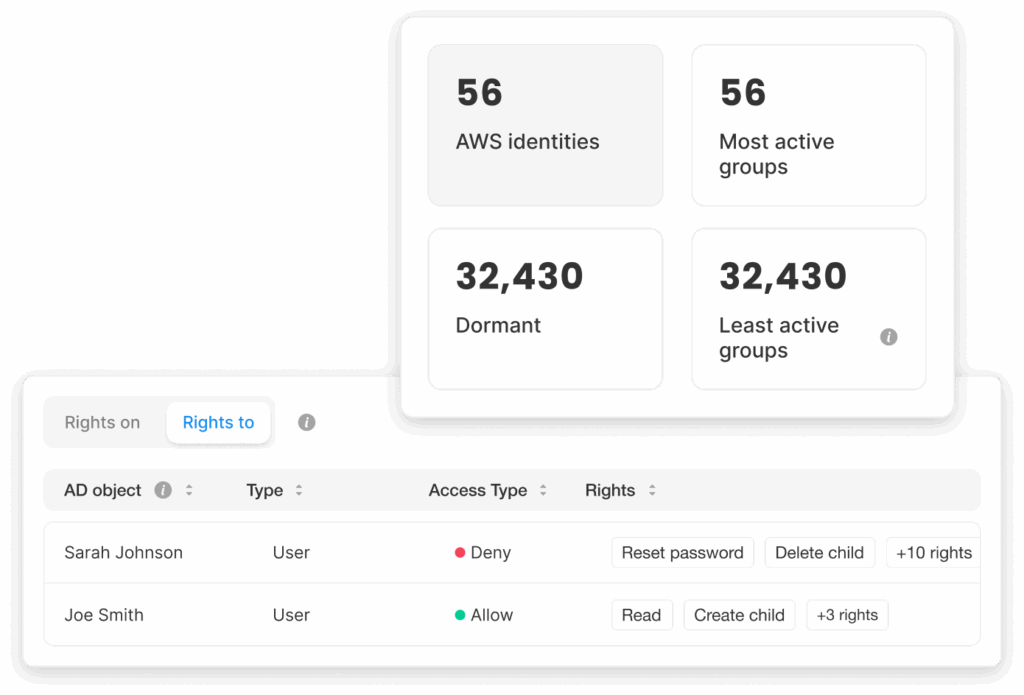
Analyze real usage
Knowing who has access isn’t enough—shift from static entitlements to dynamic behavior.
Silverfort continuously analyzes authentication activity to show how identities actually use their permissions across accounts, systems, and protocols, and compare actual access vs. permitted access. This helps uncover unused or excessive privileges, spot abnormal patterns, and eliminate assumptions so you can right-size access.
Enable true least privilege & policy enforcement
Confidently remove standing permissions and excessive rights with data-driven insight.
Least privilege often fails because it relies on guesswork or rigid policies. Silverfort combines access behavior analysis with policy automation, so you can remove unnecessary access, restrict overly broad rights, and enforce context-aware controls—without disrupting users or operations.
How Silverfort fuses actionable context into every access path
From fragmented visibility to full access intelligence—automatic, interconnected, actionable.
Uncover every access path
Expose every route between identities and the resources they access—no coverage gaps.
Silverfort analyzes activity across cloud, on-prem, and hybrid systems. Even legacy, homegrown, unmanaged, or “forgotten” systems are surfaced automatically, giving you a complete picture of how access really happens across your environment.

Analyze real usage
Knowing who has access isn’t enough—shift from static entitlements to dynamic behavior.
Silverfort continuously analyzes authentication activity to show how identities actually use their permissions across accounts, systems, and protocols, and compare actual access vs. permitted access. This helps uncover unused or excessive privileges, spot abnormal patterns, and eliminate assumptions so you can right-size access.

Enable true least privilege & policy enforcement
Confidently remove standing permissions and excessive rights with data-driven insight.
Least privilege often fails because it relies on guesswork or rigid policies. Silverfort combines access behavior analysis with policy automation, so you can remove unnecessary access, restrict overly broad rights, and enforce context-aware controls—without disrupting users or operations.

Trying to achieve Least Privilege in an environment with hundreds of thousands of employees has been an expensive and endless effort. The automated approach introduced by Silverfort will solve my #1 security challenge.
SVP & CISO, Fortune 50 Manufacturing Company
Trying to achieve Least Privilege in an environment with hundreds of thousands of employees has been an expensive and endless effort. The automated approach introduced by Silverfort will solve my #1 security challenge.
SVP & CISO, Fortune 50 Manufacturing Company
Why Silverfort is different
Point solutions show pieces of the puzzle. Silverfort delivers a complete picture and enriches it with context.
Full mapping
All access paths, including unmanaged and legacy systems.
Behavior-based insights
Showing how access is actually used.
Unified view
Across cloud, on-prem, and hybrid; human, machine, and AI.
Continuous intelligence
That refreshes in real time.
Policy automation
Drives policy automation for least privilege and risk reduction.
Point Solutions
- Fragmented snapshots of permissions
Full mapping
All access paths, including unmanaged and legacy systems
- Focus on static entitlements
Behavior-based insights
Showing how access is actually used
- Coverage is limited to specific systems or identity types
Unified view
Across cloud, on-prem, and hybrid; human, machine, and AI
- Static reports, quickly outdated
Continuous intelligence
That refreshes in real time
- Passive findings with no enforcement
Policy automation
Drives policy automation for least privilege and risk reduction



