
Trust made easy.
Bring zero trust security to the identity control plane with adaptive least-privilege access policies across every on-prem and cloud resource—all without making any changes to your applications or infrastructure.
Zero trust that's fast and efficient.
Identity is the ultimate place to start your Zero Trust journey, with continuous analysis and enforcement of security control on every user access.
Rapid time to value
Protect and observe all user access within days of initial deployment, with no costly and complex changes to your network or identity infrastructure.
High precision analysis
Eliminate the possibility of malicious access with compromised credentials by preventing users to access resources without rigorous risk analysis and verification.
Real-time enforcement
Trigger MFA, JIT, and Deny Access to block malicious access to your resources and halt the spread of live attacks.
The Silverfort Identity Security Platform
How it works
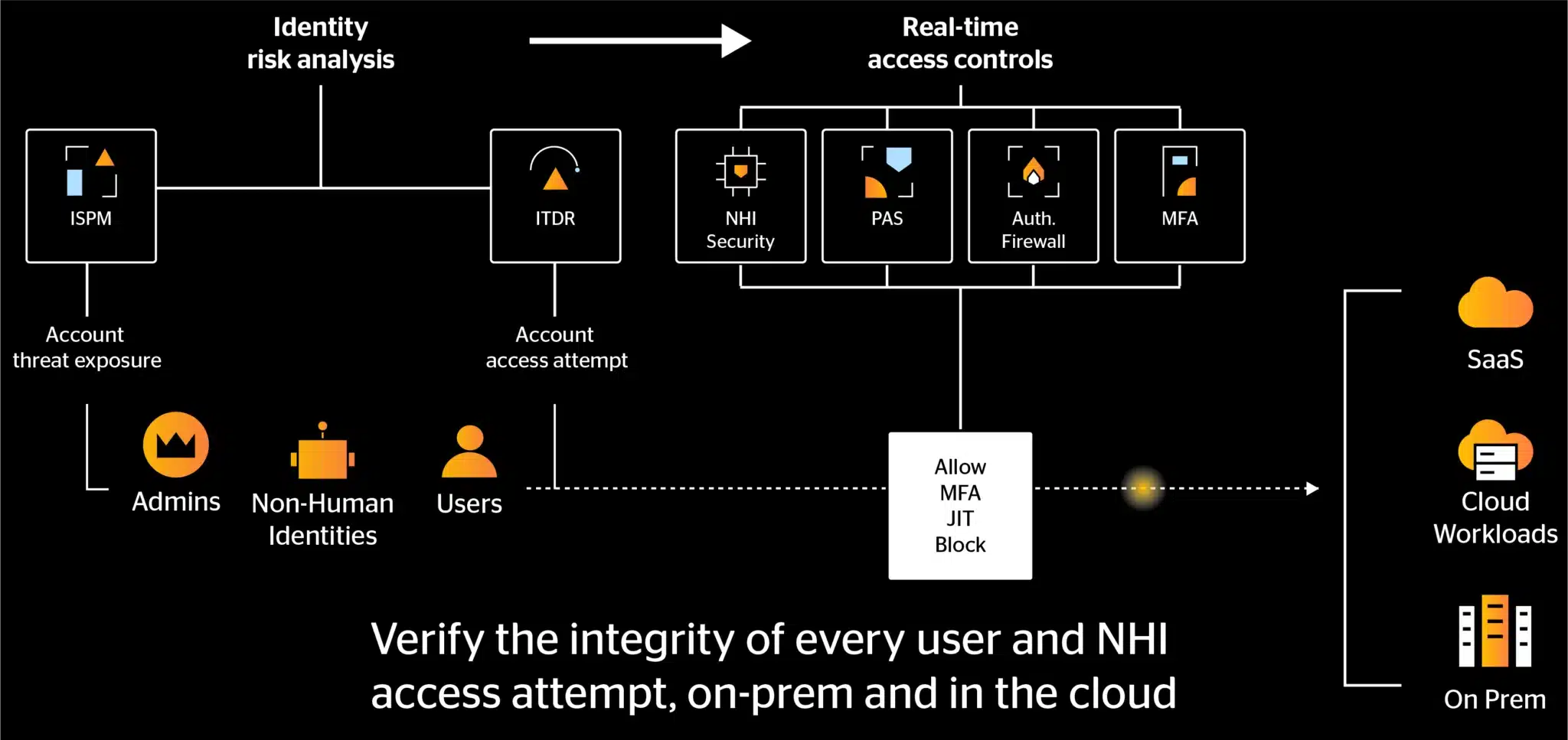
All resources: from legacy on-prem to the cloud.
Proactively reduce the attack surface
Apply identity-based segmentation across your hybrid environment so users can only access the resources they need, reducing blast radius in a compromise scenario.
Extend protection to all resources
View and monitor every user access attempt across your entire identity infrastructure, from on-prem AD to SaaS applications and cloud workloads.
Eliminate threat exposures
Identify and resolve any weaknesses and excessive trust within your hybrid environment that expose your users to compromise and your resources to malicious access.
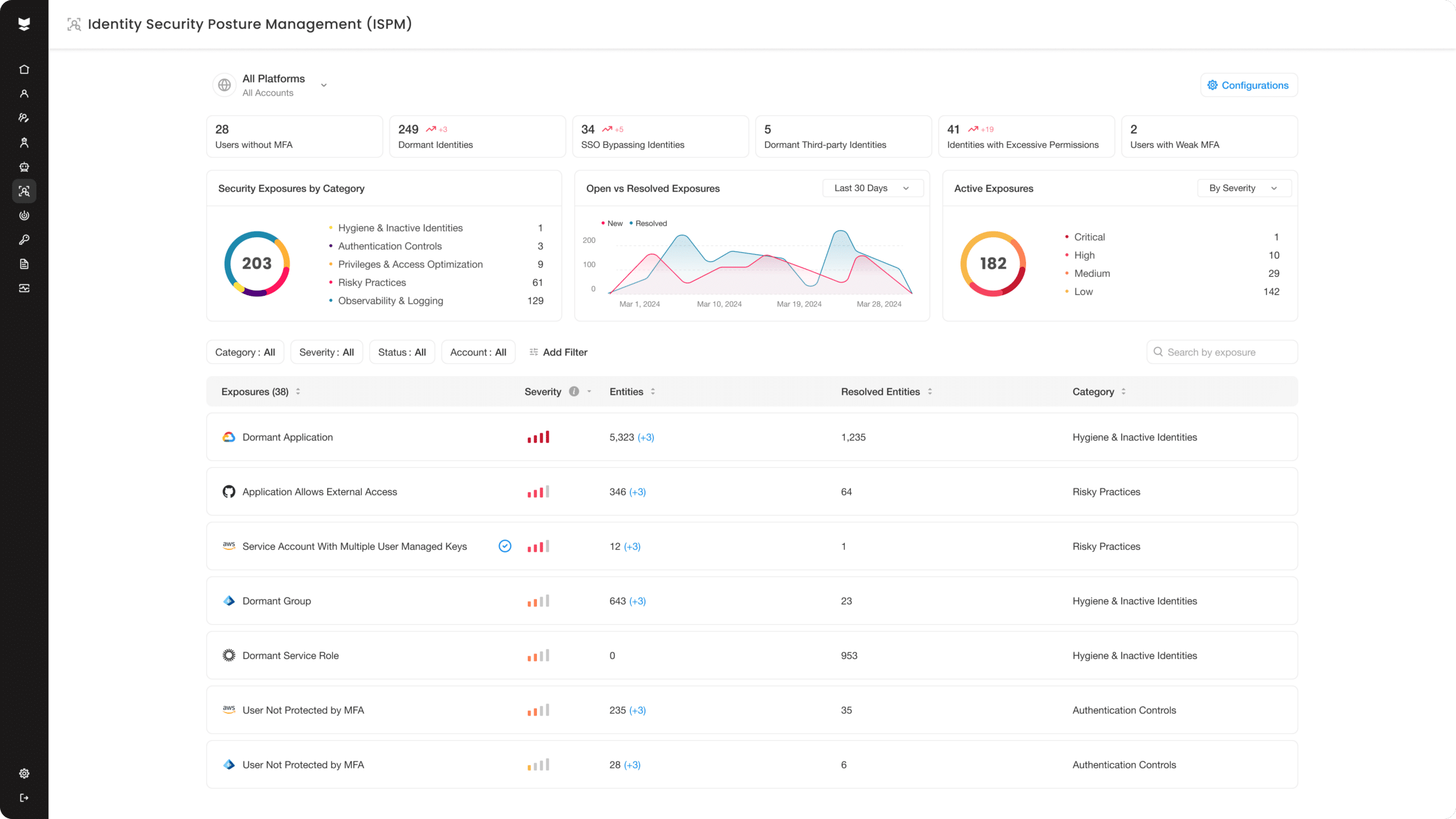

We dared to push identity security further.
Discover what’s possible.
Set up a demo to see the Silverfort Identity Security Platform in action.


