
Enforce adaptive policies based on real-time risk analysis across all users, systems and environments without requiring agents or proxies, and respond to detected threats and anomalies with MFA and real-time prevention
Apply real-time analysis on each access request based on the full context of the user’s authentication activity, to detect behavioral anomalies and malicious patterns such as brute force attacks, Pass the Hash, Pass the Ticket, impossible travel and many more.

Configure access policies that leverage Silverfort’s risk scoring to trigger proactive security controls, preventing suspicious users from accessing resources by applying MFA or blocking access.

Leverage Silverfort’s end-to-end integration with the IdPs in your hybrid environment so your access policies span across all human users and service accounts, all access interfaces, and all on-prem and cloud resources.
Silverfort policies trigger protective actions such as MFA and block access when risk is detected, so legitimate users can seamlessly authenticate and only suspicious ones are required to verify their identities.
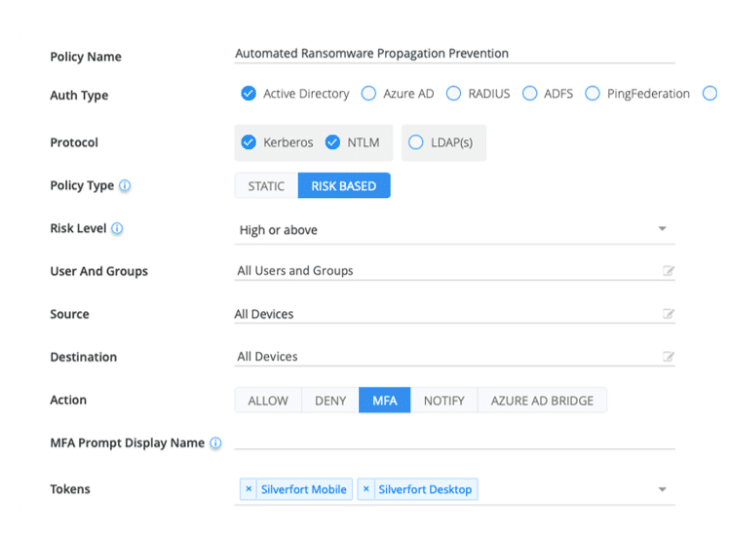
Silverfort lets you build policies that trigger MFA or block access upon detection of specific risks which you determine when configuring the policy, enabling you to pay special attention to attacks that your environment is likely to experience.
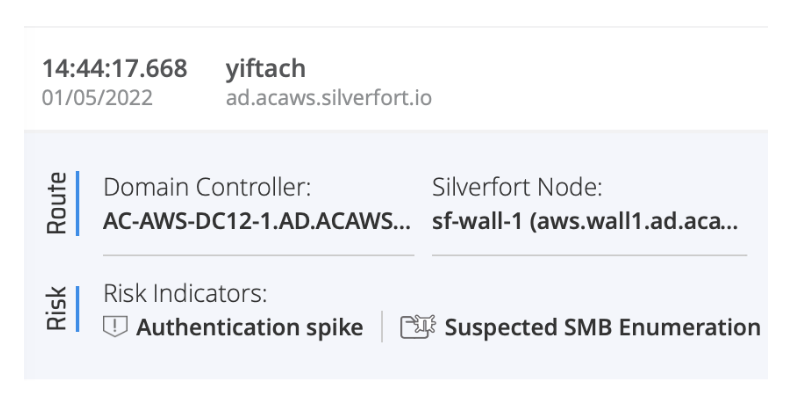
Silverfort integrates with the core components in your security stack, such as XDR, SIEM and SOAR, for both mutual exchange of users’ and machines’ risk data, as well as incorporate MFA and Access Block in automated response playbooks.
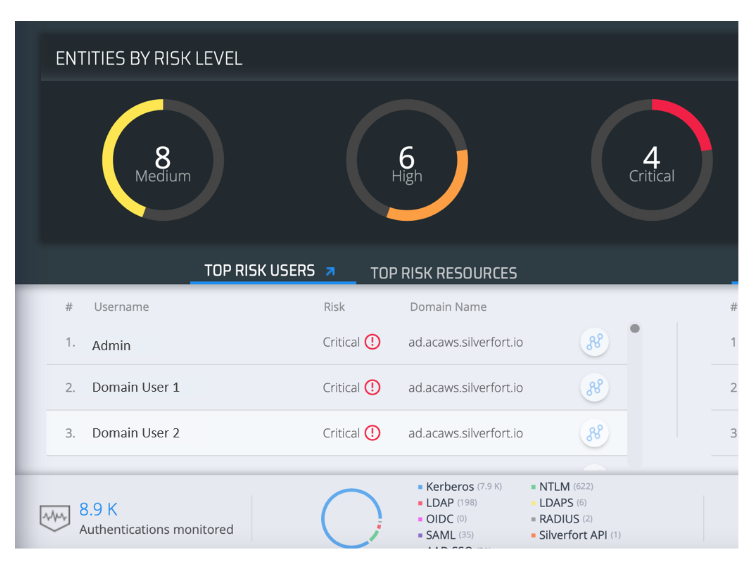
The bank understood that compromised credentials could be used to access sensitive environments which control identity and access. They wanted to enhance their identity security with different risked-based authentication methods to improve their security posture and visibility into user authentication requests.
With Silverfort, the bank’s security team configured a set of adaptive access policies for all of its users and service accounts. These covered all on-prem and cloud resources to protect against a wide range of identity threats such as account takeover, malicious remote connections, lateral movement and ransomware spread.