
Detect and block attackers from accessing resources in your environment by enforcing adaptive MFA protection on PsExec, PowerShell, WMI and other command line interfaces for the first time.

Eliminate attackers’ ability to perform lateral movement by enforcing MFA protection on all command line interfaces, including PsExec, PowerShell, WMI, etc.

Isolate and remediate compromised machines and accounts before an attack spreads by detecting and preventing malicious access attempts in real time.

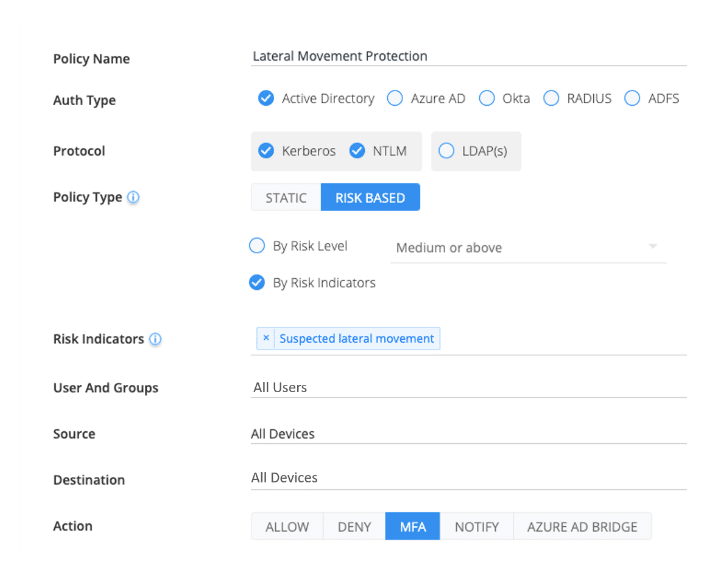
Implement multi-layered protection that combines rule-based policies, capable of anticipating lateral movement activities, with risk-based policies, triggered by anomalous behaviour and techniques.
Silverfort continuously applies AI-based risk analysis to each access attempt to detect any anomalies that indicate lateral movement activity.
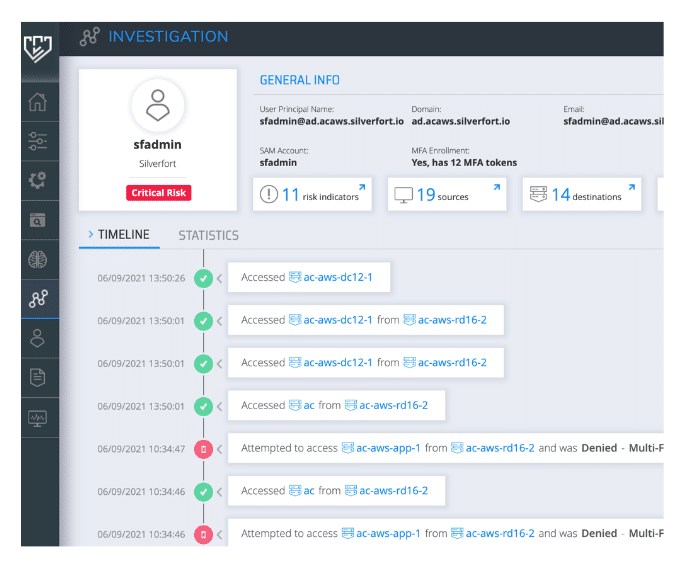
Silverfort eliminates an attacker’s ability to move laterally by applying adaptive MFA policies across all access interfaces including command line tools for the first time.
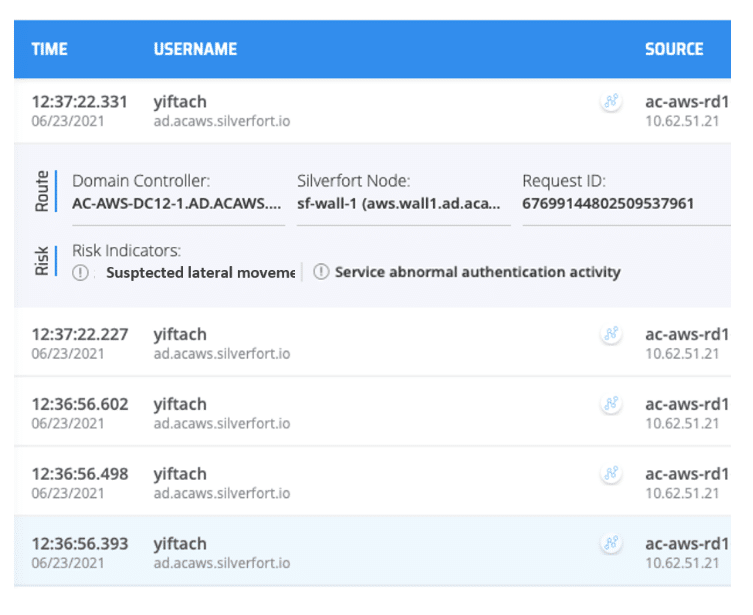
Expedite and optimise incident investigations by viewing the full authentication and access trail of each user and service account with Silverfort’s platform.
Lateral movement is method used by a threat actor to expand their presence within an environment and log into additional machines. The purpose of lateral movement varies depending on the attacker’s motive and objective; for example, they could seek to plant ransomware on as many machines as possible.
Once an attacker has gained an initial foothold on a machine, they will seek to expand their presence within the environment and gain further access to resources using compromised user account credentials. In an enterprise environment (both on-prem and in the cloud), accessing resources requires authentication, hence the close connection between lateral movement and identity protection.
SIEM, EDR, and NDR can assist in reactive alerting of lateral movement attacks that are in full flow. However, only an adaptive policy that triggers MFA or blocks access can deliver real-time protection against lateral movement attacks when they are initiated.
Silverfort is the only identity protection solution that can apply this kind of adaptive policy on any access interface, including the command line access tools like PsExec, PowerShell, and WMI, that threat actors use in lateral movement attacks.
Silverfort analyzes the forwarded access request and enforces MFA authentication where risk is detected. When an attacker attempts to log in to a resource with compromised credentials, the real user will receive an MFA notification asking them to confirm whether they requested access. The true user would deny this, and as a result, the directory would deny access to the attacker.
Yes. Silverfort combines several different methods to disclose lateral movement attacks: