
Visibility & Risk Analysis
Gain full, real-time visibility into all access attempts across your hybrid environment and AI-driven risk analysis of all users and resources.

Inventory & Auditing
Have operational insights on anything relating to your users, resources and authentication logs at your fingertips at all times.

Full Context
Create reliable, high-precision, and continuously updated behavioral baselines for each user in your environment with Silverfort’s AI-based risk engine.

Threat Detection
Create reliable, high-precision, and continuously updated behavioral baselines for each user in your environment with Silverfort’s AI-based risk engine.
Gain powerful insights into your hybrid network
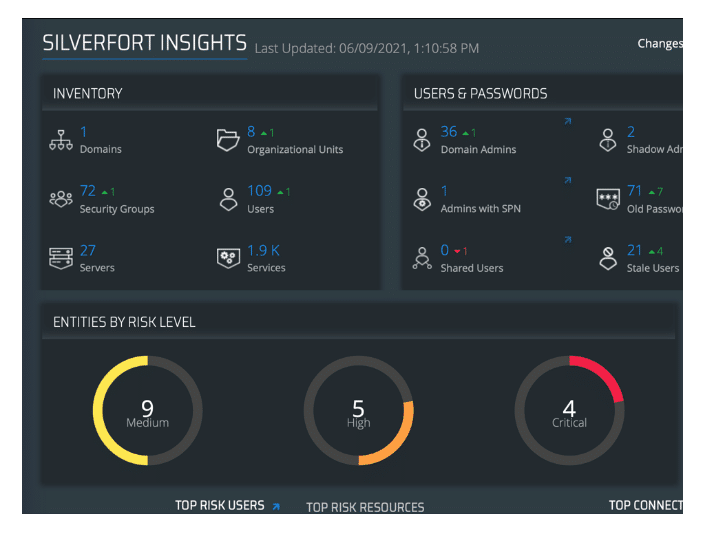
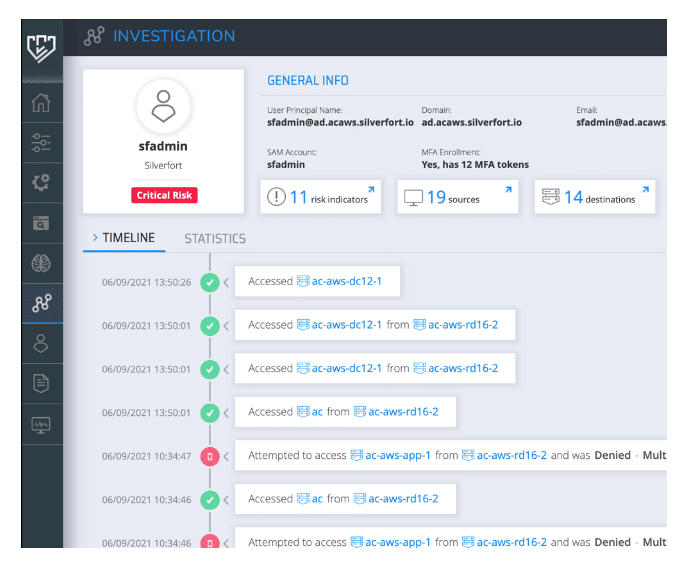
Investigate quickly and efficiently
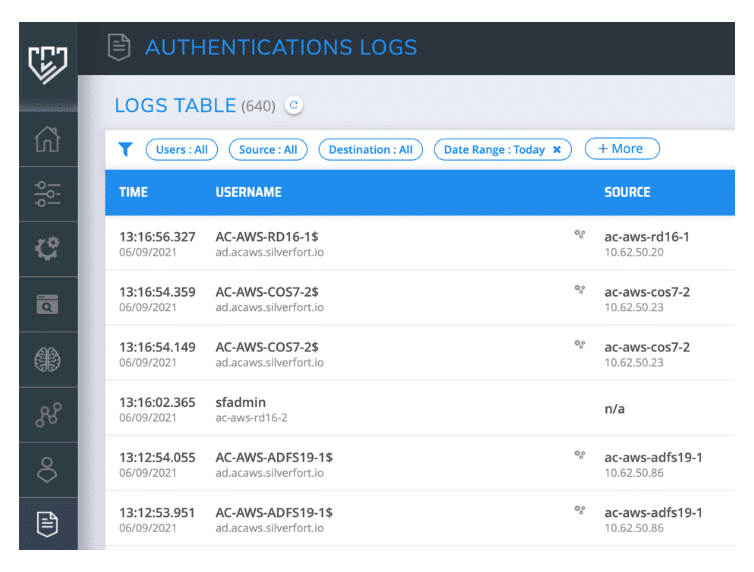
Enrich your SOC with granular access logs
"With Silverfort, we now have continuous visibility and real-time risk analysis into our identity security, which has allowed us to improve our response and mitigation efforts against incoming security threats."
Rusdi Rachim | Senior VP of Corporate Information Security

Customer Challenge
Indosat understood the different identity security risks posed by their users when accessing corporate resources. They needed improved visibility into their users’ logs and how they are being authenticated and identified.
Silverfort Solution
Silverfort enables Indosat to implement continuous monitoring and risk analysis across all users and external contractors. Indosat’s team now has full visibility into what’s normal – and what’s not – for each user account, so they can make informed decisions and take action whenever a risk is detected.
How they rate us:
4.7 – 28 Reviews

We dared to push identity security further.
Discover what’s possible.
Set up a demo to see the Silverfort Identity Security Platform in action.
Frequently Asked Questions
Why is it essential to have real-time visibility and risk analysis?
What are the advantages of implementing visibility and risk analysis on the identity control plane?
Why should organizations continuously perform a risk analysis of user authentications and access attempts?
How is the visibility provided by Silverfort better than the visibility provided by native IAM applications?
An IAM provides granular and comprehensive visibility to the authentications it controls (AD for on-prem, cloud IDP or Federation for SaaS\web apps, etc.). However, no IAM can provide this visibility to authentications controlled by its peers. In today’s hybrid environment, where there are often three or more IAM solutions in parallel, this means that no single IAM can provide centralized visibility into all authentications. Silverfort, on the other hand, integrates with all the different IAMs to aggregate their data and provide a single, consolidated view.
How does Silverfort identify and analyze risks?
Silverfort sees the full authentication trail of each user, both on-prem and in the cloud. This enables Silverfort’s risk engine to create a high-precision behavioral baseline for each user and sense anomalous authentications when they happen. In addition, Silverfort also consumes risk data from other components in the security stack, such as SIEM, XDR, and SOAR, and feeds it to the user’s risk score calculation.


