Boost your environment’s resilience with the power of deny.
Protect your identity infrastructure from within. Govern and control users’ access based on their identity with no infrastructure changes with Silverfort’s authentication firewall.


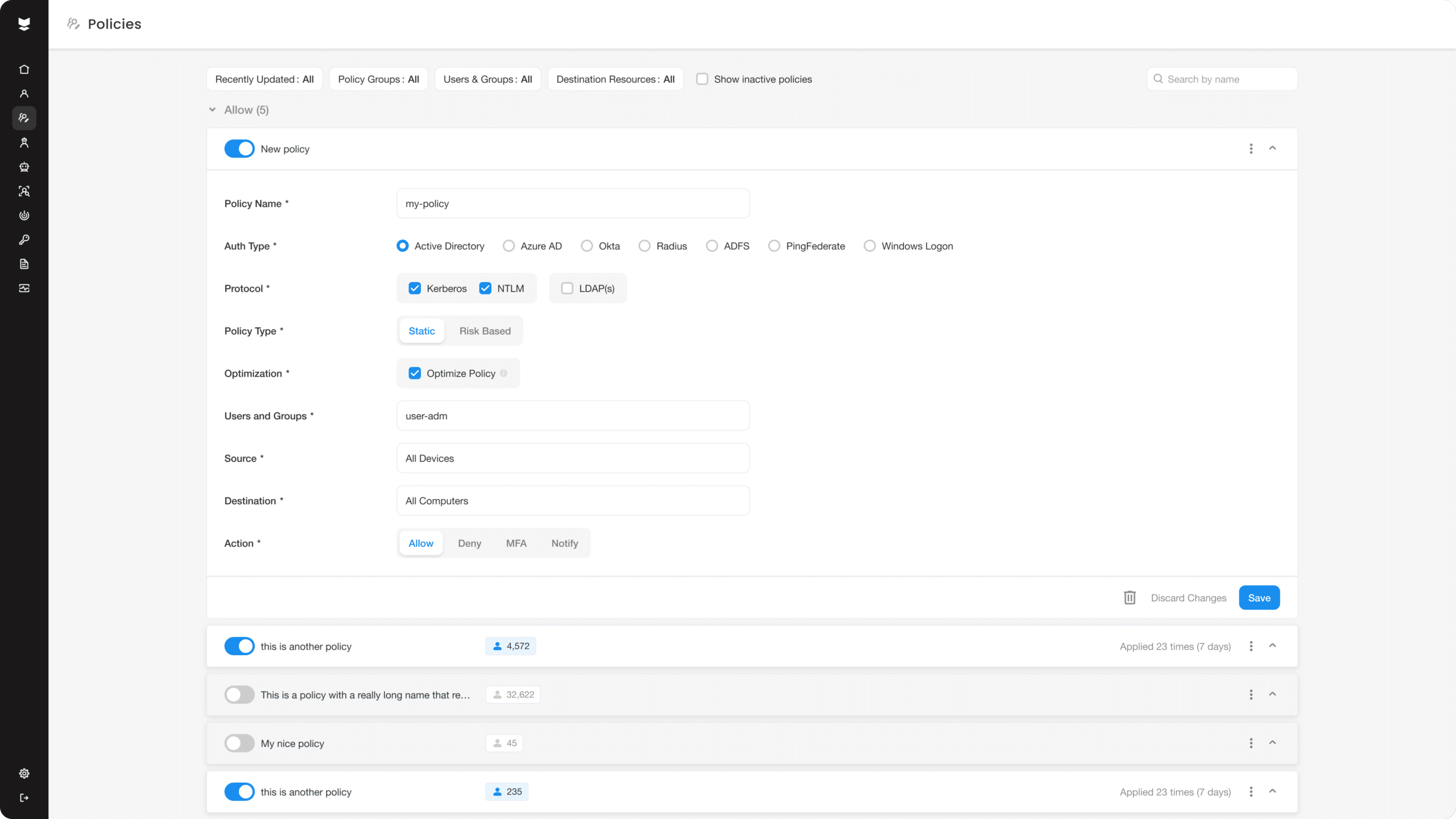
Power up your access controls with our authentication firewall.
Divide your environment into logical access segments with the flexibility to dynamically change it in a single click.
Protect the full scope
Cover the full range of your AD managed resources with access policies across all servers, applications, and IT infrastructure.
Reduce the attack surface
Enhance security posture by blocking access when insecure protocols are used or users have a misconfiguration that puts them at risk of compromise.
Contain active attacks
Freeze all access to some or all of your environment when a breach is detected.
Control access to every resource in a single click.
Protect
Block access based on identity
Secure
Enforce least privilege access policies
Embracing the power of deny to strengthen security posture and mitigate threats.
“Silverfort’s authentication firewall has helped us to apply deny access policies across our organization, which has significantly strengthened our security posture. We’ve been able to effectively mitigate identity threats by ensuring only authenticated users have access to our resources.”
Head of IAM of a leading retail organization
The challenge
The company realized it needed to strengthen its security posture across its entire organization due to the various identity security risks posed by its users when accessing corporate resources. They needed to be able to limit who was allowed to access which resources and systems.
Our solution
With Silverfort, the company has adopted the principle of least privilege by creating group-segmented access policies and applying deny access policies on user groups when needed. Now the company can enforce more strict access controls on each user, resulting in a more powerful security posture for the entire company.
We dared to push identity security further.
Discover what’s possible.
Set up a demo to see the Silverfort Identity Security Platform in action.