Silverfort
THE IDENTITY UNDERGROUND REPORT
The most common identity security gaps that lead to compromise
Your defenses are sky high – but underground you’re exposed.
We noticed a gap in cybersecurity research. Most threat reports available today go into great detail about malware, threat actors, and attack kill chains, but they include very little data on the identity gaps and weaknesses that play a part in almost every cyber attack. We decided to change that.
The Identity Underground is the first attempt to map out the most critical identity security weaknesses that lead to credential theft, privilege escalation or lateral movement — both on-prem and in the cloud. They aren’t vulnerabilities or attacks in themselves, but rather inherent weaknesses in identity infrastructure regularly used by threat actors in their attacks. As such, we decided to call these gaps Identity Threat Exposures (ITEs).
The data in this report is gathered from hundreds of live production environments. Our hope is that the Identity Underground can help identity and security teams benchmark their security programs and empower them to make informed decisions on where to invest in identity security.

Did you know?
of all users are service accounts with high access privileges and low visibility.
of user accounts are stale and do not perform any activity.
of admin accounts are configured to have unconstrained delegation
Identity Threat Exposures (ITEs) open your organization up to attack
The Identity Underground maps out the most critical ITEs that allow attackers to access credentials, escalate privileges and move laterally, both on-prem and in the cloud. We have classified them into four categories: Password Exposers, Privilege Escalators, Lateral Movers and Protection Dodgers. ITEs are hard to eliminate and can result from a misconfiguration, malpractice, legacy identity infrastructure, or even built-in features. They are behind the steep increase in credential theft and lateral movement, a feature of nearly every attack. ITEs in this report are proven to be prevalent, impactful, and available for attackers to exploit. While there are multiple ITEs of different types, we’ve only included those that introduce a risk every organization is likely to experience.

Password Exposers
Allows attackers to move laterally undetected.
Related MITRE ATT&CK Technique: Privilege escalation
Examples:
- NTLM authentication
- NTLMv1 authentication
- Admins with SPN

Privilege Escalators
Allows attackers to move laterally undetected.
Related MITRE ATT&CK Technique: Privilege escalation
Examples:
- Shadow admins
- Unconstrained delegation

Lateral Movers
Enables attackers to escalate existing access privileges.
Related MITRE ATT&CK Technique: Lateral movement
Examples:
- Service accounts
- Prolific users

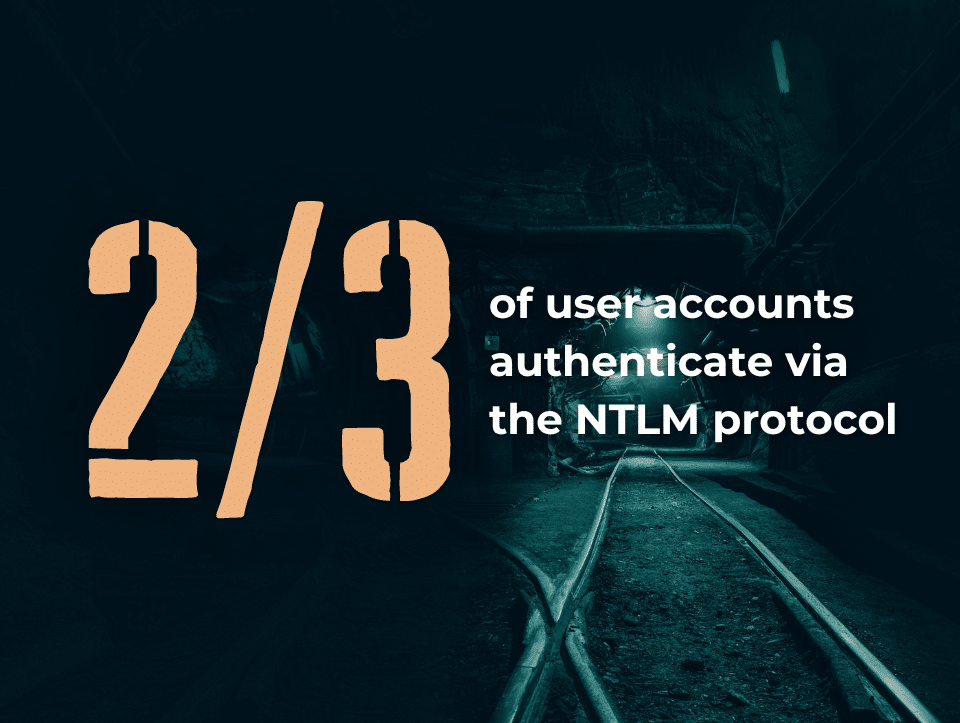
Easily cracked with brute-force attacks, NTLM authentication is a prime target for attackers looking to steal credentials and move deeper into an environment.
Recent research by Proofpoint security shows threat actor TA577 stealing NTLM authentication information to obtain passwords. This is another example of a Password Exposer ITE.

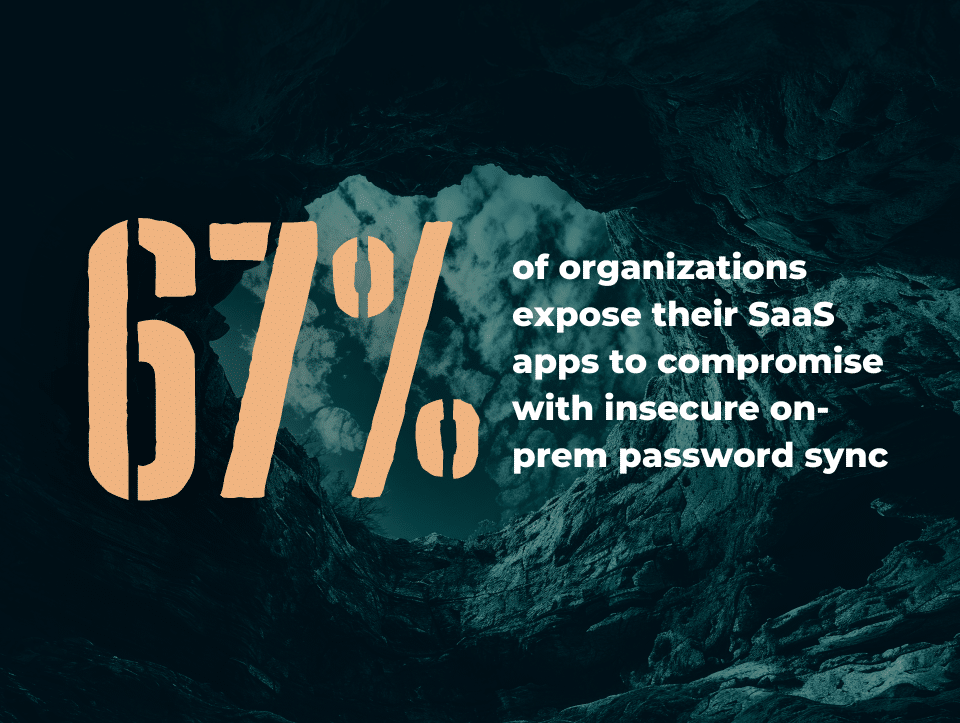
It’s common practice for Active Directory (AD) to sync user hashes to the cloud IdP so users can access SaaS apps with the same credentials as on-prem resources.
By syncing user passwords in this way, organizations inadvertently migrate on-prem identity weaknesses to the cloud and create a Password Exposer ITE. Attackers, including the Alphv BlackCat ransomware group, are known to hack cloud environments from on-prem settings.


A single misconfiguration in an Active Directory account spawns 109 new shadow admins on average.
Shadow admins are user accounts with the power to reset passwords or manipulate accounts in other ways. Considered Privilege Escalators, attackers use Shadow Admins to change settings, permissions and give themselves more access to machines as they move deeper into an environment.

Almost a third of all user accounts are highly privileged service accounts.
Service accounts are used for machine-to-machine communication, and are identities that have a lot of access and privileges. Attackers target service accounts, as they are often overlooked by security teams. Only 20% of companies are highly confident that they have visibility into every service account and can protect them. We consider unknown service accounts Lateral Mover ITEs.

What you can do today to protect your organization
Identity remains an insidious part of nearly every attack. An underground world of Identity Threat Exposures contributes to an organization’s identity attack surface. The good news is that there are actions you can take today to eliminate these ITEs and bolster your identity security.
01
Know where you’re exposed and eliminate risk where possible
Gain visibility into the ITEs in your environment, follow Microsoft’s best practices and weed out any ITEs that result from malpractices or misconfigurations.
02
Contain and monitor existing risks
For ITEs that cannot be eliminated, such as service accounts or the use of NTLM, monitor these accounts closely for any sign of compromise.
03
Take preventative measures
Apply identity segmentation rules or MFA policies to protect user accounts and enforce access policies on your service accounts.
04
Connect the identity and security teams
Combine the areas of expertise of your identity and security teams to prioritize and implement fixes against ITEs.