
5 Ways to Step Up Your AD Hygiene with Silverfort

Active Directory (AD) is the backbone of most organizations’ networks, managing access and authentication for users, devices and applications. While AD provides both users and administrators with central services, its security has not kept pace with growing modern security risks. As a tempting target for threat actors, this is a huge concern for businesses, forcing them to invest time and resources to ensure their AD hygiene is up to par.
Table Of Contents
Maintaining Proper AD Hygiene is Essential
AD hygiene refers to the practices and measures implemented to ensure the cleanliness, organization, and security of an organization’s AD environment. It exists to prevent, detect, and respond to security threats within the AD infrastructure. A properly maintained AD security hygiene program is essential for an organization’s overall security hygiene against identity security threats.
A fundamental aspect of AD hygiene is regular auditing and monitoring, cleaning up outdated or unused accounts, enforcing strong password policies, and monitoring user activities. This involves conducting periodic reviews of AD configurations, user accounts, group memberships, and access permissions to identify any malicious activities or anomalies.
Failure to manage AD effectively can lead to a myriad of identity security risks, with one of the most significant being a lack of visibility into users and their associated risks.
When organizations lack visibility into the types of users in their AD environment and the potential risks they pose, they are unable to effectively assess and mitigate security threats. For example, stale or orphaned accounts, unauthorized access privileges, and other types of risk accounts can go undetected, leaving an organization exposed to identity threats.
Silverfort AD Hygiene Capabilities
Silverfort’s AD hygiene capabilities help organizations proactively manage their user base by automatically discovering all user accounts, service accounts, and other types of users within their AD environment and providing centralized visibility into every authentication and access request.
Organizations gain a unified view of all users, resources, and authentication activities due to Silverfort’s native Active Directory integration, which enables it to log every authentication request.
Furthermore, Silverfort provides a user inventory that displays the types of users and resources in your environment, as well as potential security weaknesses that adversaries may exploit. This enables administrators to identify where their security risks are and how to prioritize their efforts to eliminate these risks.
By gathering actionable insights and taking proactive measures to enhance one’s AD hygiene posture management, Silverfort makes it significantly harder for threat actors to target the organization, thus bolstering its overall resilience against identity threats.
5 Ways Silverfort Can Help You Strengthen Your AD Hygiene Posture Management
1. Detect Shadow Admins
Shadow admins are users who have admin capabilities that you may not be aware of due to ACLs or nested groups.
How does Silverfort detect shadow admins? Silverfort identifies shadow admin accounts based on their privileges and the permissions they have been granted, in both on-prem and cloud environments.
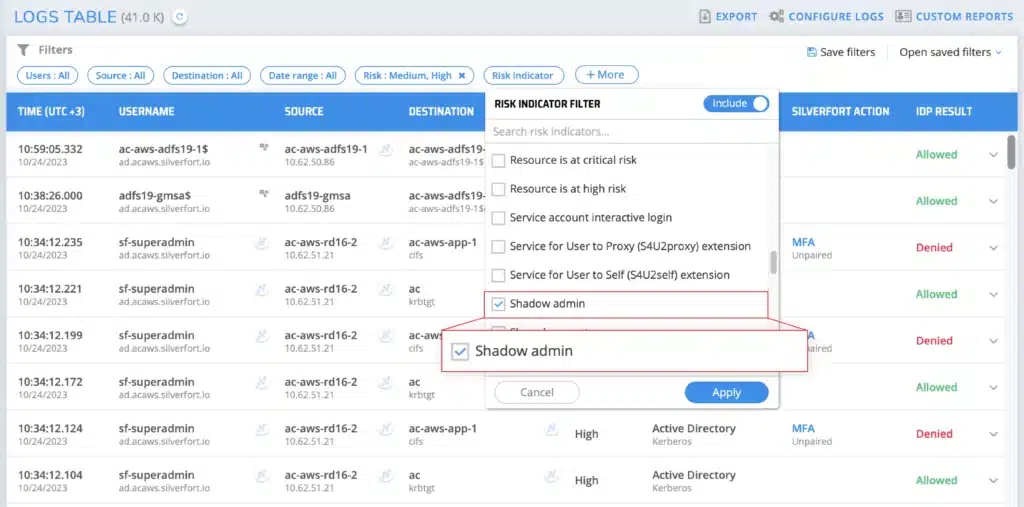
Customer Example: At a Fortune 500 financial company, Silverfort detected 109 new shadow admins created by a single AD misconfiguration. By detecting and removing the privileges of these admin accounts, the customer decreased their attack exposure.
2. Reducing NTLMv1 Usage
NTLMv1 is inherently insecure due to its use of weak encryption (DES) to encrypt the session key. This encryption type can be easily broken, and the user’s password can be extracted.
How does Silverfort detect NTLMv1? Silverfort monitors all authentications processed by Active Directory without using event logs. It identifies which devices are sending NTLMv1 authentication requests and sends alerts to the logs screen inside the Silverfort platform.
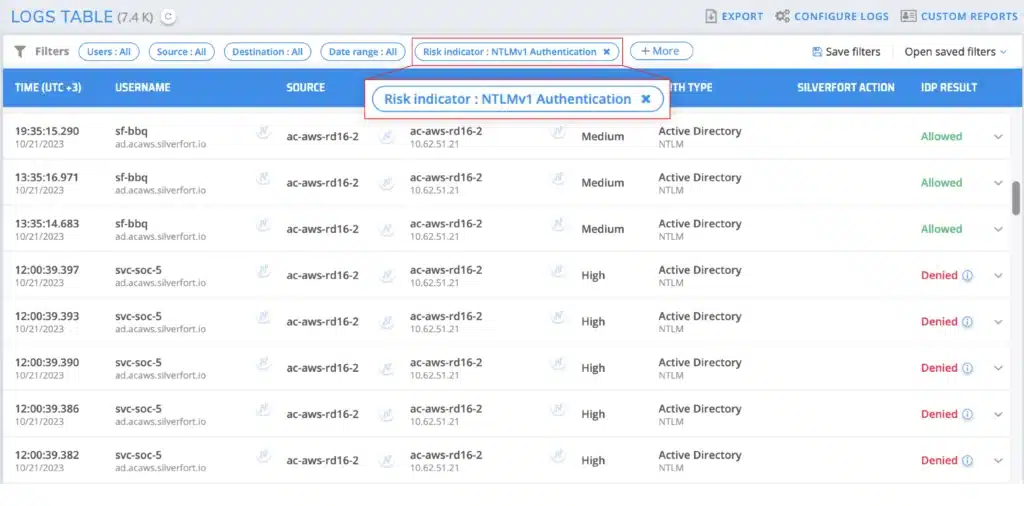
Customer Example: In a leading global manufacturer’s environment, Silverfort discovered that around 5-8% of admin users still authenticate with NTLMv1 protocol, which was exposing their user passwords to compromise. Weekly reports are now sent to the team so they can reduce and ultimately eliminate the use of NTLMv1.
3. Discover Stale Users
Stale users are accounts that have not been used for a while; for example, former employees’ accounts that have not been disabled. Certain types of stale accounts are difficult to identify unless you are able to monitor their authentication activity. As an example, identifying service accounts is difficult since their information is not available natively.
How does Silverfort detect stale users? Silverfort automatically identifies and discovers stale users based on a lack of user activity data and information gathered from logs and other sources.
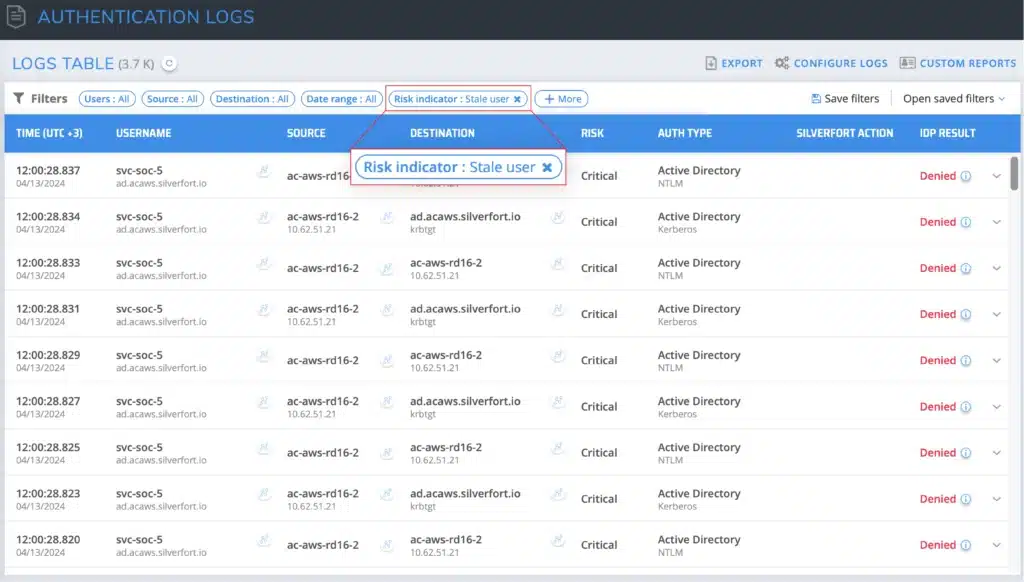
Customer Example: At a leading US retail company, Silverfort detected that 13% of user accounts were stale users who had not performed any recent activity. This helped the company to clean up its Active Directory by disabling/removing the unused accounts, which ultimately helped decrease licensing and minimize costs.
4. Disable Admins with SPN
Having a Service Principal Name (SPN) associated with an admin account can expose it to a Kerberoasting attack, where an attacker requests the Kerberos ticket and obtains a payload encrypted by the user’s password hash. Attackers can then brute force this payload to expose the credentials and compromise the account.
How does Silverfort detect Admins with SPN? Silverfort detects these types of accounts by monitoring authentication events involving Service Principal Names (SPNs) within the network. It utilizes behavioral analytics and user behavior profiling to identify deviations from normal patterns, such as unusual access requests or privilege escalation attempts associated with admin privileges.
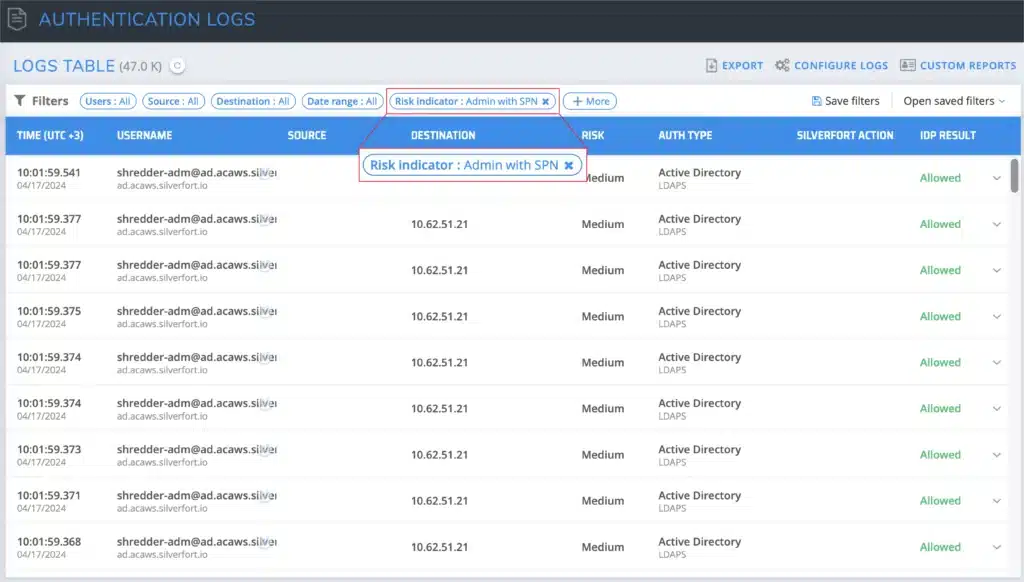
Customer Example: In a large healthcare provider’s AD environment, Silverfort discovered 8 admins with SPN that the customer was not aware of. This helped the customer to limit their exposure to potential Kerberoasting attacks and decrease their attack surface exposure.
5. Removing PrintNightmare
PrintNightmare is a critical security vulnerability affecting Windows’ Print Spooler service that allows remote code execution and could lead to unauthorized access or system compromise.
How does Silverfort detect bad authentications from patched Print Spooler services? Silverfort detects PrintNightmare by analyzing authentication events and abnormal service behavior and triggering alerts for further investigation and mitigation. Microsoft explains how to fully mitigate PrintNightmare but with Silverfort you can completely skip the problematic network packet capture as it will alert on all the bad Print Spooler authentications.
Customer Example: A large US school district detected PrintNightmare in their environment thanks to Silverfort. With Silverfort they fixed this issue and reduced the number of unnecessary authentications in their environment by about 70%.
Real-Time Visibility and Actionable Insights is Critical for AD Hygiene
To maintain proper Active Directory hygiene and strengthen identity security posture management within organizations, it is crucial to have end-to-end visibility and actionable insights into all your users and resources. By having all the insights into your AD user base, you can take proactive steps to ensure that your user base is not opening the door to identity threats. This will strengthen your overall identity security posture management (ISPM)
By investing the resources to step up your AD hygiene you will ensure its cleanliness and security is up to date to prevent your AD environment from being compromised and used as a gateway for attackers to gain unauthorized access to sensitive data.
Looking to strengthen your AD hygiene and gain complete visibility across your environment? Reach out to one of our experts here.

