Identity based attacks make use of user’s compromised credentials for malicious access. They differ from malware-based attacks in that they employ the legitimate authentication process for accessing resources, with no malicious code required.
Some expand the definition and include in it also attack stages that facilitate this unauthorized access, such as credential compromise and privilege escalation.
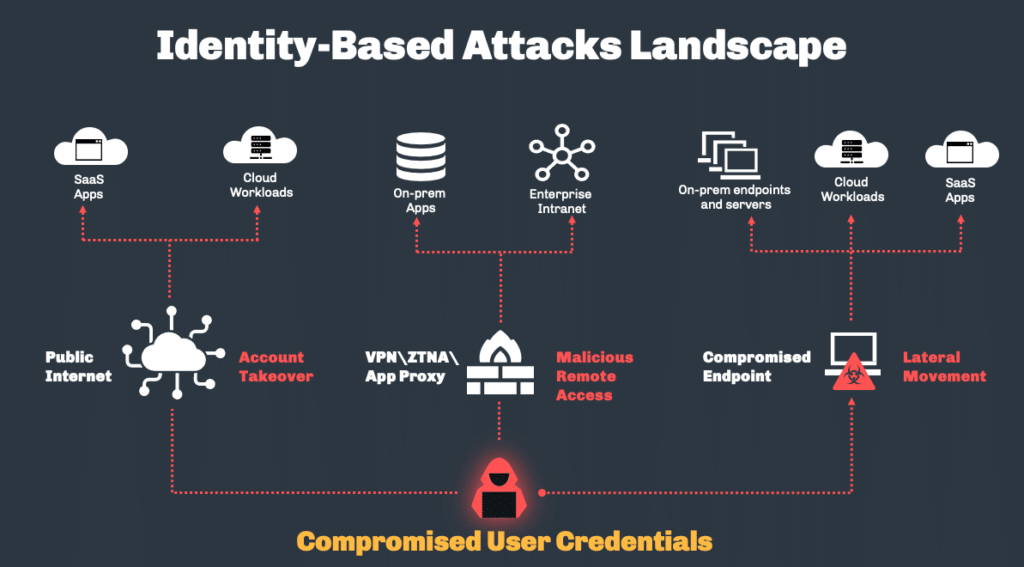
The goal of identity based attacks is to access on-prem and cloud resources by impersonating legitimate users. Once threat actors have stolen login information, they can masquerade as authorized users and gain access to resources. These attacks are difficult to detect since the compromised accounts already have permission to access systems and data.
Identity based attacks continue to grow in sophistication and scale. Organizations must implement strong security controls like multi-factor authentication, employee education, and account monitoring to help reduce risks from these threats. With vigilance and proactive defense, the impact of identity based attacks can be minimized.
Identity-based attacks target individuals by compromising their personal data and digital identities. Hackers employ various techniques/vectors to steal usernames, passwords, social security numbers, and other sensitive information that can then be used to impersonate victims for financial gain or other malicious purposes.
Phishing is a common tactic where attackers send fraudulent emails or text messages posing as a legitimate company or service to trick recipients into providing login credentials, account numbers, or installing malware. Spearphishing targets specific individuals, appearing to come from someone they know. Whaling targets high-profile executives.
Keylogging software secretly tracks the keys pressed on a keyboard, recording usernames, passwords, credit card numbers, and other sensitive data. Keyloggers can be installed by phishing emails, infected external storage devices, or by exploiting software vulnerabilities.
Social engineering aims to manipulate people into divulging confidential information or performing actions that enable system access. Attackers may impersonate IT support staff, claim there is a technical issue that requires account access or trick victims into clicking malicious links by appearing to come from a friend or colleague.
Credential stuffing uses automated tools to test stolen username and password combinations on different websites and services. Billions of compromised credentials from major data breaches are available on the dark web. Hackers employ credential stuffing to find accounts where people reuse the same login information.
As multi factor authentication becomes normalized, biometric spoofing, where attackers falsify biometric data to access privileged accounts, has also emerged as an attack vector.
Identity-based attacks target an individual’s personally identifiable information (PII) and login credentials. These attacks are significant because they can have major impacts on both individuals and organizations.
For individuals, identity theft and account takeovers can lead to financial loss, damaged credit, and compromised personal information. Criminals use stolen identities and accounts to make unauthorized purchases, apply for loans, file fraudulent tax returns, and more.
For organizations, identity-based attacks pose risks to customer data, intellectual property, and financial assets. Hackers frequently target corporate accounts and networks to gain access to sensitive data and funds. Successful attacks can undermine consumer trust and negatively impact a company’s reputation and brand.
Once attackers gain initial access, they will try to move laterally across networks to access additional systems and accounts. They leverage the permissions and trust of the originally compromised account to access more sensitive data and gain greater control. Lateral movement is an advanced technique that often requires stealth to avoid detection.
Regulations like the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA) hold organizations responsible for safeguarding personal data and responding to identity-based attacks. Failure to comply with these regulations can result in significant financial penalties.
Protecting against identity-based attacks requires a multi-pronged approach. Organizations should implement comprehensive security awareness training to educate employees about phishing emails, social engineering tactics, and strong password practices.
Multi-factor authentication (MFA) adds an extra layer of protection for user accounts and systems. When MFA is enabled, users must provide two or more verification methods to log in, such as a password and a security code sent to their mobile device.
MFA adds an extra layer of security, making it difficult for attackers to gain access even if they have the password. It can also mitigate the damage of phishing attacks by requiring a second form of identification that the attacker is less likely to have.
Repeated login attempts (in Brute Force Attacks) are also often thwarted by MFA, as the attacker would need more than just a password to gain access.
Artificial intelligence and machine learning can help detect anomalous login attempts and spot compromised accounts. AI systems analyze huge volumes of data to establish normal behavior patterns for users and systems. They can then flag unusual activity, like logins from unknown devices or locations, excessive failed login attempts, or changes to account information. AI and ML get “smarter” over time by incorporating new data into their models.
In the event of an identity-based attack, an effective incident response plan is critical. The plan should outline steps for securing accounts and systems, investigating the source and scope of the attack, and remediating any damage. It should also include procedures for notifying affected customers or business partners if their data has been compromised. Post-incident reviews help identify areas of improvement for security controls and response strategies.
Continuous monitoring of networks, systems, and user accounts is key to defending against identity theft and account takeover. Monitoring solutions use a combination of log analysis, network traffic inspection, and user behavior analytics to detect threats in real time. When malicious activity is uncovered, security teams receive alerts so they can quickly contain the attack and avoid data loss or system disruption. Regular reviews of access logs, permissions, and user profiles also help ensure that accounts and data are properly secured.
With a robust set of security controls, vigilant monitoring, and adaptive technologies like AI, organizations can strengthen their defenses against the evolving techniques used in identity-based cyber attacks. But constant awareness and education across the workforce are equally important for thwarting social engineering attempts and other scams aimed at stealing login credentials or sensitive data.
As this article has shown, identity-based attacks are a serious threat in today’s digital landscape. By compromising login credentials or spoofing trusted identities, cybercriminals can gain access to sensitive data and systems to launch further attacks.
Identity-based attacks are constantly evolving, but with vigilance, education and adaptive defensive strategies, their impact can be minimized. Continued progress in biometrics, behavior analytics, and other authentication methods may also help curb these threats in the coming years.