Identity segmentation is a cyber security model that isolates users based on their job functions and business requirements. An organization can implement tighter controls and monitor over sensitive data and system resources by segmenting user access strategically.
For cybersecurity professionals, understanding identity segmentation concepts and best practices is crucial to reducing risk and protecting an organization’s digital assets. When implemented correctly, identity segmentation reduces the likelihood of data compromise due to compromised credentials or insider threats by restricting lateral movement across the network. It allows security teams to enforce the principle of least privilege and “need to know” access for users and services.
Identity segmentation requires carefully analyzing user behavior and their interactions with different systems and resources to determine appropriate groupings and access levels. While complex to implement, identity segmentation is one of the most effective strategies for limiting the attack surface and hardening defenses. For any organization, identity is the new perimeter – and segmentation is key to controlling access and increasing overall identity security.
The core components of identity segmentation include:
- Attribute analysis: Examining attributes like job role, location, and access permissions to group similar identities. For example, executives can be segmented from contractors.
- Behavioral analysis: Analyzing behavior patterns like login times, resource access, and network activity to group identities with comparable behaviors. Unusual behaviors within a segment may point to compromised accounts or insider threats.
- Risk assessment: Determining the level of risk for each identity segment based on attributes, behaviors, and security policies. Higher-risk segments require stronger controls and monitoring.
- Policy enforcement: Implementing customized access controls, authentication requirements, auditing, and other security policies for each segment based on their risk assessment. Policies are adjusted as risks change.
The Benefits of Implementing Identity Segmentation
Identity segmentation, also known as identity-based segmentation, enhances security by controlling access to resources based on user attributes. It aligns permissions with business needs, reducing an organization’s attack surface.
Granular Control
Identity segmentation provides granular control over user access. Rather than assigning broad permissions based on a user’s role, access is granted based on attributes like department, location, and job function. This minimizes excessive privileges and limits the damage from compromised accounts.
Streamlined Compliance
By aligning access with business needs, identity segmentation simplifies compliance with regulations like GDPR, HIPAA, and PCI DSS. Audits are more efficient since permissions map directly to organizational policies.
Support for Hybrid Environments
In today’s multi-cloud and hybrid IT environments, identity segmentation is crucial. It provides a consistent way to manage access across on-premises and cloud-based resources. The same attributes and policies are applied regardless of where applications and workloads reside.
Improved Reporting
Identity segmentation generates valuable data that can be used for reporting and analysis. By tracking the relationship between user attributes, access, and permissions over time, organizations gain insight into usage patterns and can make data-driven decisions regarding access policies.
How Does Identity Segmentation Work?
Identity segmentation divides identities into groups based on risk factors like access privileges, applications used, and geographic location. This allows organizations to apply security controls tailored to the specific risks of each group.
To implement identity segmentation, organizations first analyze identities and group them based on factors like:
- Job function and access needs (e.g. software engineers vs. HR staff)
- Applications and systems accessed (e.g. those using sensitive databases vs. public websites)
- Geographic location (e.g. headquarters office vs. remote workers)
- Previous security issues (e.g. identities with a history of phishing susceptibility)
Once identities have been segmented, security controls are customized for each group. For example:
- Identities accessing sensitive data may require multi-factor authentication and data encryption
- Remote workers could face additional monitoring and device security checks
- Groups with higher risk are prioritized for security awareness training
A “least privilege” approach is used to grant each segment only the minimum access needed. Access is regularly reviewed and revoked when no longer needed.
Technologies like Identity and Access Management (IAM), Privileged Access Management (PAM) and Zero Trust Network Access (ZTNA) are often used to facilitate identity segmentation. They provide granular control over identity and access policies, allowing tailored rules to be applied for each segment.
When implemented effectively, identity segmentation helps reduce the risk of a breach by minimizing the potential damage. If one segment is compromised, the attack is contained to that group and cannot spread easily to others. This “blast radius” limiting effect makes identity segmentation an important tool for modern cyber defense.
Risks and Challenges of Identity Segmentation
Identity segmentation, or separating user identities into logical groupings, introduces risks that organizations must address to ensure secure access management.
Lack of Governance
Without proper governance, identity segmentation can lead to vulnerabilities. Policies and controls must define who can access which systems and data based on business needs and compliance requirements. If governance is lacking, identities may be improperly segmented or have excessive access, creating opportunities for data breaches or insider threats.
Human Error
Manual processes for assigning users to identity segments are prone to human error. Mistakes like assigning a user to the wrong segment or giving too much access can have serious consequences. Automating identity segmentation where possible and implementing review processes can help minimize risks from human error.
Conflicting Controls
If controls for different identity segments conflict or overlap, users may end up with unintended access. For example, if a user belongs to two segments with different levels of access for the same system, the access level that provides greater permissions may take precedence. Organizations must evaluate how controls for different segments interact to ensure secure access.
Lack of Visibility
Without a comprehensive view of how identities are segmented and managed, organizations cannot properly assess and address risks. They need visibility into which users belong to which segments, how access is controlled for each segment, how segments inherit access from one another, and more. Gaining this visibility is key to governance, auditing, and risk mitigation.
Network Segmentation vs Identity Segmentation
Network segmentation involves dividing a network into different segments to enhance security and control. Traditional network segmentation relies on factors like IP addresses, VLANs, and physical separation to create these segments. While effective at limiting the impact of a breach within the network, network segmentation often falls short in addressing the dynamic and evolving nature of user identities.
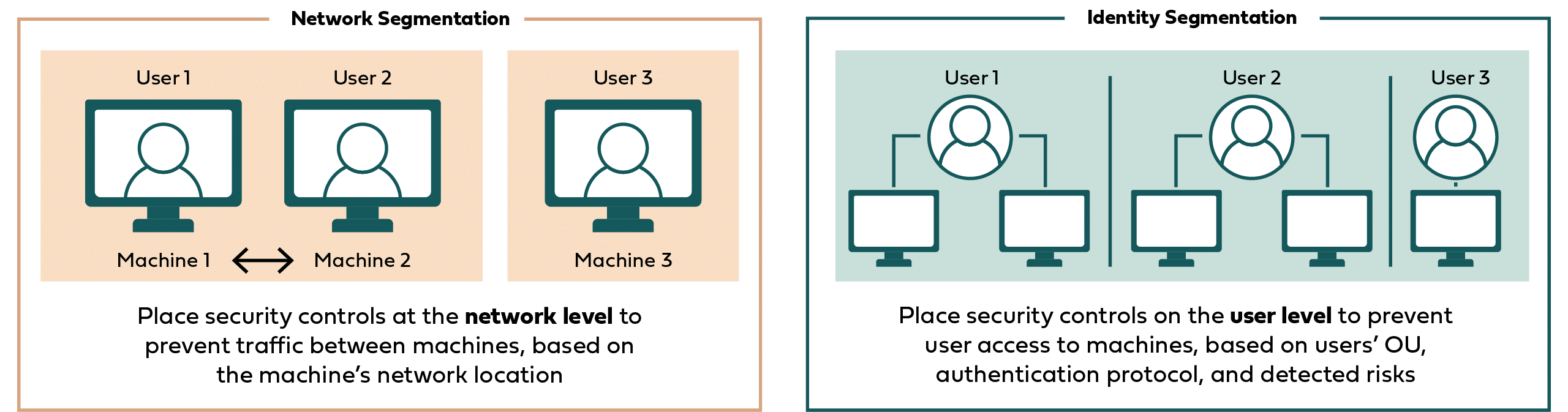
On the other hand, identity segmentation shifts the focus to user identities. This approach aligns with modern security threats where users are the primary targets and threats often exploit compromised credentials. Identity segmentation involves creating access controls based on user attributes, roles, and behavior, so users can only access the resources necessary for their roles, irrespective of their network location.
The primary difference lies in their focus: network segmentation emphasizes securing pathways and infrastructure, while identity segmentation centers on safeguarding individual user identities. Network segmentation tends to rely on static policies based on network structure, whereas identity segmentation involves dynamic and context-aware access controls based on user attributes. Identity segmentation is particularly effective in countering identity-based threats, which have become increasingly prevalent in the cybersecurity landscape.
How does identity segmentation improve security?
Identity segmentation improves security by enabling targeted protection of sensitive resources. Rather than a one-size-fits-all approach, controls can be tailored to the specific risks of each segment. For example, identities with access to customer data may have stricter controls than those used by front-office staff. Segmentation also simplifies compliance by mapping controls directly to data access requirements for each role.
Conclusion
Identity segmentation is an important cybersecurity concept that allows organizations to isolate sensitive and privileged accounts. By applying the principle of least privilege and limiting access to only authorized individuals, companies can reduce their risk exposure and ensure compliance.
Though implementing identity segmentation requires time and resources, the long-term benefits to data security and privacy are well worth the investment. With the increasing complexity of IT infrastructure and the constant threat of breaches, identity segmentation will continue to be a best practice that organizations tend to.