The past couple years have brought major changes to cyber insurance policies. Notably, almost all brokers are now requiring multi-factor authentication (MFA) across on-prem and cloud resources. This introduces a severe challenge to small and mid-sized organizations, since standard MFA solutions cannot deliver the required coverage and deploying a PAM solution is typically beyond the scope of their operational capacity and security skillset. The Silverfort Unified Identity Protection platform is the only solution that can consolidate compliance with the full cyber insurance MFA requirements checklist, without requiring agents or proxies, making it an ideal choice for any organization that seeks to purchase or renew its cyber insurance policy.
What is MFA and what are its benefits?
Multi-factor authentication, commonly referred to as MFA, is a security measure that adds an additional layer of protection to the traditional username-password combination. It requires users to provide multiple forms of verification, such as something they know (e.g., a password), something they have (e.g., a mobile device), and something they are (e.g., biometric data).
Implementing MFA offers a wide range of advantages that significantly enhance cybersecurity. Let’s explore these benefits in detail:
- Strengthened Authentication: MFA greatly enhances authentication security. By requiring multiple forms of verification, attackers are considerably more challenged to gain unauthorized access. Even if a password is compromised, the additional factors serve as an additional barrier, to protecting sensitive information.
- Mitigation of Credential-Based Attacks: In the cyber threat landscape, password breaches and credential theft are all too common. MFA plays a crucial role in mitigating such attacks. Even if an attacker obtains user credentials, they would still need the additional factors to successfully complete the authentication process, effectively thwarting unauthorized access attempts.
- Defense against Phishing: Phishing attacks, in which cybercriminals deceive users into divulging their credentials, pose a significant threat. Against such attacks, MFA serves as a powerful defense mechanism. Even if users unknowingly disclose their passwords, the additional authentication factors prevent attackers from progressing further, safeguarding sensitive data.
- Compliance with Regulations: Various industries and government organizations have implemented rigorous data protection regulations. MFA is often mandated as a security measure to comply with these regulations. By implementing MFA, organizations demonstrate their commitment to meeting compliance standards and protecting valuable information from unauthorized access.
- Enhanced User Experience: While prioritizing security measures, user experience is essential. Modern MFA solutions offer seamless and user-friendly experiences. With intuitive interfaces and various authentication methods, such as push notifications or biometrics, the authentication process becomes convenient for users without compromising security.
- Safeguarding Cyber Insurance Policies: MFA plays a vital role in the context of cyber insurance. Insurers recognize the effectiveness of MFA in reducing the risk of cyber incidents. As a result of implementing MFA, organizations demonstrate their proactive approach to strengthening their security posture, which may lead to more favorable insurance terms.
Why do insurers require Multi-Factor Authentication (MFA)?
Organizations are now required by cyber insurers to adopt MFA as a fundamental component of their policies. This requirement is derived from the fact that MFA’s technology is capable of strengthening security, mitigating risks, demonstrating a commitment to security, complying with industry standards, and addressing emerging threats.
Through the mandate of MFA, insurers aim to promote proactive risk management and encourage organizations to adopt robust security measures in order to protect themselves from cyber attacks. Implementing MFA not only aligns with insurers’ risk management strategies but also helps organizations enhance their overall security posture in an increasingly complex cyber landscape.
The Cost of a Cyber Attack vs. The Cost of a Cyber Insurance Policy
Understanding the potential financial impact of a cyberattack and weighing it against the cost of a cyber insurance policy is crucial for making informed decisions.
There are several factors that contribute to the financial consequences of a cyber attack, including:
- Direct Financial Losses: This includes expenses related to system recovery, data restoration, and potential ransom payments. In addition, it encompasses financial losses resulting from business interruptions, including revenue loss or diminished customer trust.
- Legal and Regulatory Consequences: Following a cyberattack, organizations may face legal and regulatory consequences. Including legal defense costs, regulatory fines, penalties, and any potential lawsuits from affected parties.
- Reputational Damage: A cyberattack can severely damage an organization’s reputation, leading to a loss of customer trust and loyalty. Rebuilding a brand’s reputation can be a complicated and costly process, requiring public relations efforts, marketing campaigns, and outreach initiatives to customers.
- Incident Response and Remediation: Organizations must invest in incident response capabilities, forensic investigations, and remediation efforts to identify the attack’s root cause, mitigate further damage, and strengthen security measures. These activities often require specialized expertise and can be financially burdensome.
Simultaneously, the cost of a cyber insurance policy varies based on several factors, including the insured organization’s size, nature, security posture, industry sector, and coverage limits. Other factors that influence policy costs include:
- Risk Assessment: Insurers conduct risk assessments to evaluate an organization’s security gaps to cyber threats. A number of factors are taken into account, including security controls, multifactor authentication, incident response capabilities, and historical breach data. Due to their increased exposure, higher-risk organizations may be subject to higher premiums.
- Coverage and Limits: The breadth of coverage and policy limits affect the insurance policy cost. The premiums for policies that provide comprehensive coverage, including business interruption, legal expenses, and reputational damage, are generally higher. Higher policy limits also contribute to increased costs.
- Loss History: An organization’s previous history of cyber incidents plays a role in determining policy costs. Organizations with a track record of frequent or severe cyber incidents may face higher premiums due to the perceived higher risk.
- Risk Management Measures: Insurers assess the effectiveness of an organization’s risk management measures, including security controls and incident response protocols. Organizations with robust security practices may be eligible for discounts or lower premiums.
Investing in a cyber insurance policy provides financial protection in the event of a breach. It includes mitigating direct financial losses, legal expenses, and reputational damage. Furthermore, it provides access to resources such as incident response teams and legal expertise, which can be extremely valuable during a cyber crisis. By carefully evaluating the potential financial impact of a cyberattack and considering the costs and benefits of a cyber insurance policy, organizations can make well-informed decisions to protect their interests.
The Cyber Insurance Landscape
While cyber insurance is of course a pivotal element in ensuring your company is able to recover from a cyber attack, an overlooked benefit is that the prerequisites required for cyber insurance compliance can help prevent attacks from occurring in the first place. As a response to the massive 245% uptick in ransomware attacks in 2021 (causing $21 billion in losses in the US alone), cyber insurance companies are taking greater precautions by rolling out a detailed list of new requirements for cyber liability compliance. In particular, a new set of MFA guidelines is now being required by the top cyber insurance providers, using the following MFA form:
The common notion within IT and security teams is that fully complying with this checklist is more than challenging. Let’s take a closer look to understand why.
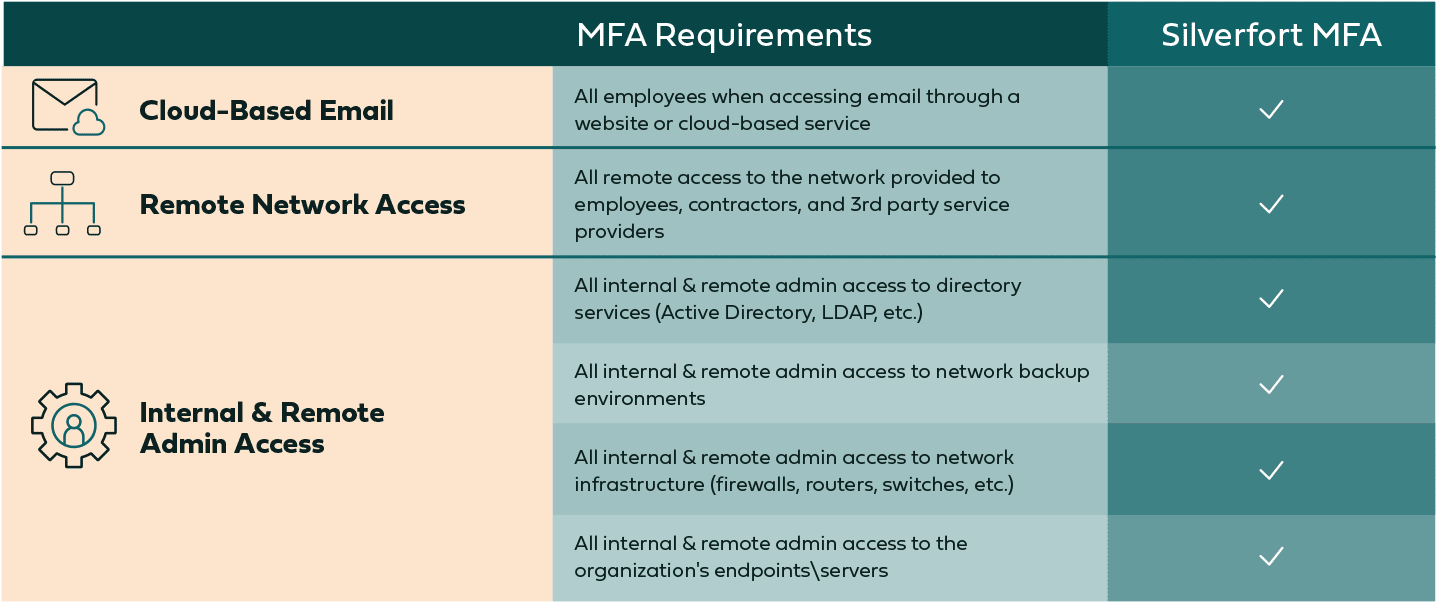
Cyber Insurance Coverage: MFA Checklist
MFA for Office 365 and other Cloud-Based Email – Easy to Find
Most cloud-based email providers, such as Office 365, offer MFA functionality, often as a native component of their product. Even when that’s not the case, adding MFA protection to SaaS or web application is a trivial task.
MFA for VPN Access – Easy to Find
For VPN connections, adding MFA is quite simple. If the VPN provider itself doesn’t have an MFA option, any LDAP or RADIUS-enabled VPN can have MFA added via a 3rd party provider.
MFA for all Remote and Internal Admin Access – Problematic
Here is where complying with the requirements becomes more complicated. While standard MFA solutions can cover some of these use cases, none can cover all of them. Let’s explore each of these sub-requirements:
MFA for AD, MFA for PowerShell, MFA for PsExec – Partial Availability Only
Industry-leading MFA solutions deliver only partial protection for remote access to on-prem directory services. While there are available MFA products for RDP access, none can cover command line tools such as PsExec, PowerShell, or WMI, creating a critical gap in both actual protection as well as complying with the cyber security insurance requirements.
MFA for all Network Backup Environments – Partial Availability Only
Dedicated backup solutions, whether in the form of virtual appliances or cloud storage, typically support MFA. However, if the backup environment is in an on-prem server it is subject to the same limitations we’ve just described – in fact, there have been various ransomware attacks lately in which these servers themselves were hit and encrypted.
MFA for Access to Network Infrastructure (routers, switches, firewall, etc.) – Partial Availability Only
In the case of routers and switches, the question is whether they can interface with RADIUS/TACACS+ – if so, adding MFA is rather simple. However, if your infrastructure doesn’t support these interfaces then it’s too bad – it might be time for an upgrade. Regarding firewalls, most modern firewalls also support the addition of MFA to the authentication process so there should be no problem here.
MFA for Active Directory-Managed Endpoints/Servers – Partial Availability Only
The problem here is similar to the one with MFA for directory services – there is no available solution that can enforce MFA on Active Directory-managed endpoints and servers. There is the single exception of RDP and local login, but no such protection exists to the command line remote access tools we’ve outlined above.
PAM Solutions are Out-of-Scope for Small to Midsized Organizations
It may be that the drive behind the new MFA checklist was to push organizations to adopt a Privileged Access Management (PAM), assuming this approach would raise their protection level and increase their resilience against cyberattacks.
However, when surveyed about reasons they don’t use PAM in their organizations, IT and cybersecurity analysts most commonly pointed out the heavy burden entailed in PAM’s cost of implementation, maintenance and ongoing operation. In other words – PAM is out of scope for small to mid-sized enterprises. So, while in theory PAM could have delivered the protection insurers seek for their insured customers, it’s not a practical cyberattack insurance solution in real life.
Silverfort: The Catch-All MFA Solution
While standard MFA solutions are able to cover some of the use cases required by cyber insurance, none can protect all of them. Since insurers themselves state ransomware as one of their top concerns, we’ll use it to demonstrate this claim – ransomware propagates in attacked networks by utilizing command line tools like PsExec, Powershell and others. No other MFA solution can cover these access interfaces.
The Silverfort Unified Identity Protection platform is the only solution that enforces MFA from the backend of identity providers rather than by agents or proxies on the individual resources. In practice this means that Silverfort can protect with MFA any user account that authenticates to an on-prem or cloud directory in the environment.
Not only does Silverfort protect internal and remote admin access in the on-prem environment (which no other solution does), but it also enables customers to consolidate all their MFA protections in a single solution, making it a natural answer to cybersecurity compliance standards.
Bottom Line: MFA Authentication Across All Your Resources Will Make You More Secure
We get it – cyber security insurance renewals are always frustrating, and especially now that providers have added so many new requirements for compliance. Between deciphering the vague wording of these prerequisites, finding solutions to protect every company asset with MFA, and getting users on board with large scale changes, it’s no small ordeal – especially in the short timeframes given by cyber liability providers.
On the other hand, these changes signal a substantial shift towards a future where enterprises are much better prepared against cyberattacks. Implementing MFA across all resources in the organization is a huge step towards a better security posture. And it doesn’t have to be painful – Silverfort makes the process of extending your current MFA solutions to cover all resources in your organization quick and straightforward. To learn more, request a demo here.
Not sure yet? Here are some more helpful resources:
- Re-evaluate Your MFA
- Agentless MFA
- Prevent Automated Propagation of Ransomware Attacks
- Lateral Movement Protection
What’s it like to go with Silverfort for your cyber insurance renewal? Hugh Christiansen of High Touch Technologies explains: