As cyberattacks continue to escalate in frequency and intensity, so do the stakes for both cyber insurance providers and their clients. To address this rapidly growing threat, brokers have raised the requirements that clients must now meet in order to acquire or renew a comprehensive policy. But these more stringent requirements are proving a challenge for many companies, especially when it comes to complying with the cyber insurance multi-factor authentication (MFA) checklist.
The watchword for underwriters today is “MFA everywhere,” but traditional MFA solutions can’t actually protect every resource within the modern hybrid enterprise – especially legacy systems – leaving open arcane attack vectors that cyber criminals are increasingly exploiting. Fortunately, there are solutions that providers can suggest to clients so they can enforce MFA across their entire organization. This post examines those solutions and proposes next steps both entities can take to prevent attacks and thus reduce the number of claims, decrease premiums, and improve overall security.
Understanding the Urgency for Cyber Insurance Compliance
The rapid rise of ransomware attacks has created soaring demand for cyber insurance policies to protect companies against financial loss, reputational damage, and legal exposure. But according to a 2021 report from the U.S. Government Accountability Office, less than half of surveyed organizations actually meet the current requirements for cybersecurity insurance, with small and medium businesses facing the biggest compliance challenges.
Meanwhile, cyber insurance claims have increased tenfold since 2016, with 2022 registering a 62% year-over-year increase in ransomware complaints over 2021 according to the FBI’s Internet Crime Complaint Center. As a result, insurance providers have tightened policy requirements (for example, regularly including 40-page attestation forms) and raised premiums to mitigate against the increased risk — in some cases declining to offer coverage at all.
The upshot is that cyber insurance vendors now require companies to implement more rigorous security protocols in order to be eligible for policies, with a primary focus on enforcing MFA across the entire enterprise. However, this is easier said than done, as many admin interfaces and legacy applications do not natively support MFA. Furthermore, cyber attackers have found ways to circumvent traditional MFA systems by compromising low-level system admin interfaces such as PsExec, PowerShell, Windows Management Instrumentation (WMI), and Remote Desktop Protocol (RDP) in order to steal credentials and propagate ransomware.
The Essence of the Problem
Cybersecurity insurance providers and companies today face a conundrum: To limit risk, brokers are now requiring every corporate system to have additional authentication procedures in place before they issue a policy; but meeting that requirement appears to be unattainable, as traditional MFA solutions can’t protect many of the legacy systems that organizations still rely on. This, in turn, means organizations can’t purchase the policy they need (and that insurers are eager to sell).
As a workaround, some companies are resorting to solutions like installing server or endpoint agents, implementing network changes such as proxies, or even making code changes to the individual legacy applications themselves.
Finding the Solution
But to make meaningful headway on this issue, it’s actually insurers who can take important steps to alleviate the impasse – first, by helping clients ask several key questions:
- Is your infrastructure hybrid (i.e., both on-premises and cloud)?
- Do you use common access interfaces such as PowerShell, PsExec, or MSI?
- How extensive and distributed is your network?
- Do you already have MFA tools in place you need to integrate?
Secondly, brokers can recommend solutions that follow established cybersecurity best practices. For example, those that:
- Cover phishing-resistant methods, such as FIDO and PKI-based MFA
- Don’t require costly implementation, since a fast deployment means clients can easily renew an existing cyber insurance policy
- Offer identity protection across both on-prem and cloud resources
- Cover hybrid networks
- Are comprehensive and standalone
Furthermore, they can champion those solutions that make use of important recent innovations, including:
- Agentless and proxyless technology to extend MFA to any resource and access interface across a hybrid environment — including legacy and homegrown applications, command-line access tools, industrial and healthcare systems, file shares, and databases.
- Technology that can deliver unified authentication and access policies across environments, assets, and user types.
- Risk engines that continuously analyze both human and entity-based requests.
- Systems that don’t disrupt the user experience by triaging MFA requests and elevating sensitive and high-risk situations.
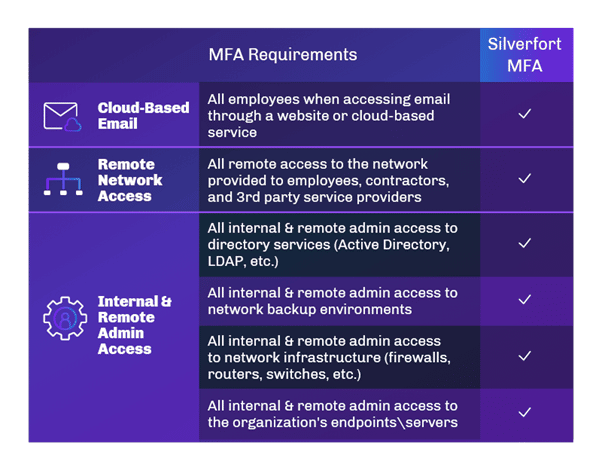
The Silverfort Unified Identity Protection platform meets all of the above criteria, thus presenting a compelling option that brokers can leverage to help clients comply with the new MFA for cyber insurance requirements, such as the ability to apply protocols to legacy applications and command-line access tools. Here’s the full cyber insurance coverage checklist:
As well, Silverfort offers a dedicated program to incentivize insurance brokers to grow their business. This is divided into three partner pillars:
- Recommendations – Expedited access for clients to Silverfort experts.
- Referrals – Fees or rebates for each client enrolled.
- Resellers – Incentives for packaging Silverfort with Endpoint Detection and Response (EDR) solutions, email phishing tools, or other security systems that help clients meet enhanced cybersecurity requirements.
By guiding clients to a comprehensive solution that can truly offer seamless MFA protection across an organization’s tech stack, cybersecurity insurance companies can reduce risk – both for themselves and their clients – while accelerating revenue at the same time.
Learn more about Silverfort’s Cyber Insurance solution by reading our eBook.