Ransomware attacks rank high among enterprises’ cybersecurity concerns. The common practice today is to protect against the delivery and execution stages of these attacks. However, nearly all enterprises lack the ability to proactively prevent the automated propagation of ransomware payload that has managed to bypass the delivery and execution protection. Since this propagation is the difference between a single infected endpoint and a mass enterprise lockdown, lacking the ability to prevent this is a critical security gap. Silverfort’s Unified Identity Protection platform delivers the only solution today that can utilize MFA to effectively prevent automated ransomware propagation, never allowing the malicious payload to expand beyond the initially infected machine.
Automated Propagation is the X Factor in Ransomware Attacks
Ransomware attacks transformed from a nuisance to a critical risk in 2017, when the WannaCry and NotPetya attacks wreaked havoc among enterprises across the globe, with overall estimated damages of close to $15B. These attacks were the first to couple an encryption payload with automated propagation. In this manner, social engineering a single enterprise worker to open a weaponized email resulted in data encryption of not only this worker’s endpoint alone, but all other machines in the enterprise environment. This new reality forced enterprise security decision makers to reprioritize their security needs, pushing enterprise ransomware protection to the top of their list.
Ransomware Attack Anatomy: Delivery, Execution, Propagation
Ransomware attacks comprise the following consecutive stages:
Delivery Protection – Checked
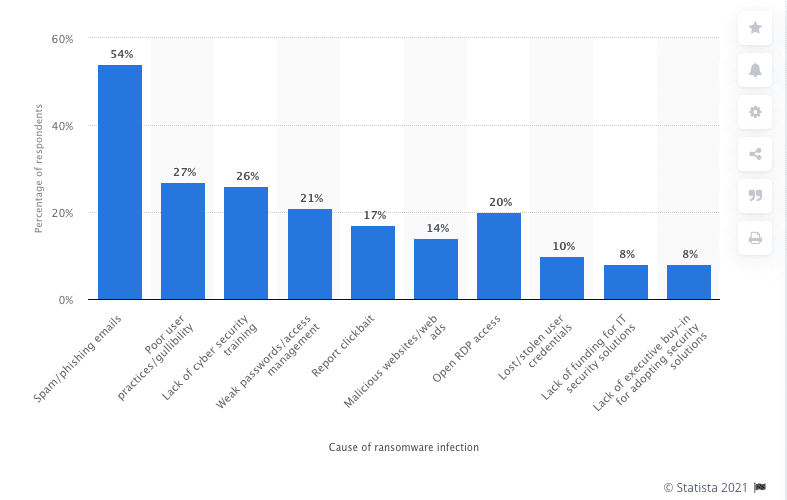
The purpose of the delivery stage is to place the ransomware payload on the target’s machine. There are various methods for attackers to achieve this with weaponized phishing emails, compromised RDP access, and watering holes leading the list. The table below, taken from Statista website, shows a more detailed distribution of delivery vectors:
Protection against ransomware delivery is carried out by email security gateways that scan emails to detect and remove risky content prior to user interaction, endpoint protection platforms that prevent the download of potential malware, and MFA on RDP connections which prevents attackers’ ability to connect with compromised credentials.
Execution Protection – Checked
The Execution stage is when the ransomware payload that was successfully delivered to the workstation or server starts running with the intent to encrypt the data files on the machine.
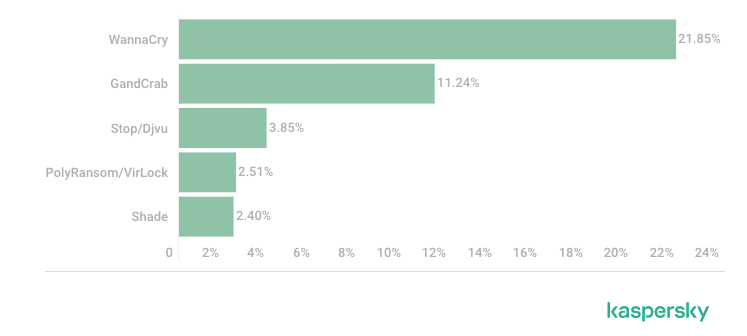
This table, assembled by Kaspersky Labs, shows the top-performing ransomware families:
Enterprises protect against the Execution stage by deploying Endpoint Protection Platforms (EPP) on their workstations and servers. The EPP aims to terminate the execution of any process that detects as ransomware, preventing the malicious encryption altogether.
Propagation Protection – The Blind Spot!
The propagation stage is where the ransomware payload is copied to many other machines in the enterprise environment via malicious authentication with compromised credentials. One of the most vulnerable attack surfaces are shared folders. In an enterprise environment every user has access to at least some of them, paving the way for ransomware to propagate.
As we have explained before, this is the stage where the mass damage is caused. However, this stage today is a blind spot in enterprises’ security posture. There is no security solution today that is capable of preventing automated ransomware propagation in real time. In practice, it means that if a ransomware variant succeeds in bypassing the Delivery and Execution security measures – and a certain percentage if these variants always do – it can propagate within the enterprise environment, encrypting any machine it can reach. And while EPPs are getting better at protecting against new strains of malware, threat actors are crafting more evasive and stealthy payloads – making such bypass a high-probability scenario.
What is the Challenge in Protecting Against Automated Ransomware Propagation?
To better understand the root cause of this security gap, let’s examine how automated ransomware propagation works.
We have the patient-zero endpoint where the ransomware payload was initially executed. In order to propagate to other machines in the environment, the malware will use compromised credentials and perform a standard authentication – providing the other machine a valid (yet compromised) username and credentials. While this activity is 100% malicious within its context, in essence it is identical to any legitimate authentication in the environment. There is no way for the Identity Provider – Active Directory in this case – to identify this malicious context and it will approve the connection.
So here is the blind spot in ransomware protection – on the one hand, no security product can block authentications in real time, and on the other, the only product that can do it – the Identity Provider – doesn’t have the ability to discern between legitimate authentications and malicious ones.
This is where Silverfort Unified Identity Protection platform comes into play.
The Solution: Unified Identity Protection Platform
Silverfort has pioneered the first purpose-built Unified Identity Protection platform that proactively prevents attacks that utilize compromised credentials to access enterprise resources. Silverfort utilizes innovative, agentless technology to natively integrate with the Identity Providers in the enterprise environment to apply continuous monitoring, risk analysis and access policy enforcement on each and every access attempt to any on-prem and cloud resource. In this way, Silverfort extends Risk Based Authentication and MFA to resources and access interfaces that could have never been protected before – including Active Directory command line remote access interfaces upon which automated ransomware propagation relies.
So How Does Silverfort Deliver Real Time Protection Against Automated Ransomware Propagation?
As we’ve explained earlier, automated propagation utilizes authentication with compromised credentials to spread in the targeted environment with a special inclination towards shared folders. Let’s understand how Silverfort addresses this risk:
Continuous Monitoring
Silverfort continuously analyzes user accounts’ authentications and access attempts, building up a high-precision behavior profile of both users’ and machines’ normal activities.
Risk Analysis
In the case of automated propagation, there will be multiple simultaneous login attempts originating from a single machine and user account. Silverfort’s risk engine will immediately identity this anomalous behavior and increase both the user account’s and machine’s risk score.
Access Policy Enforcement
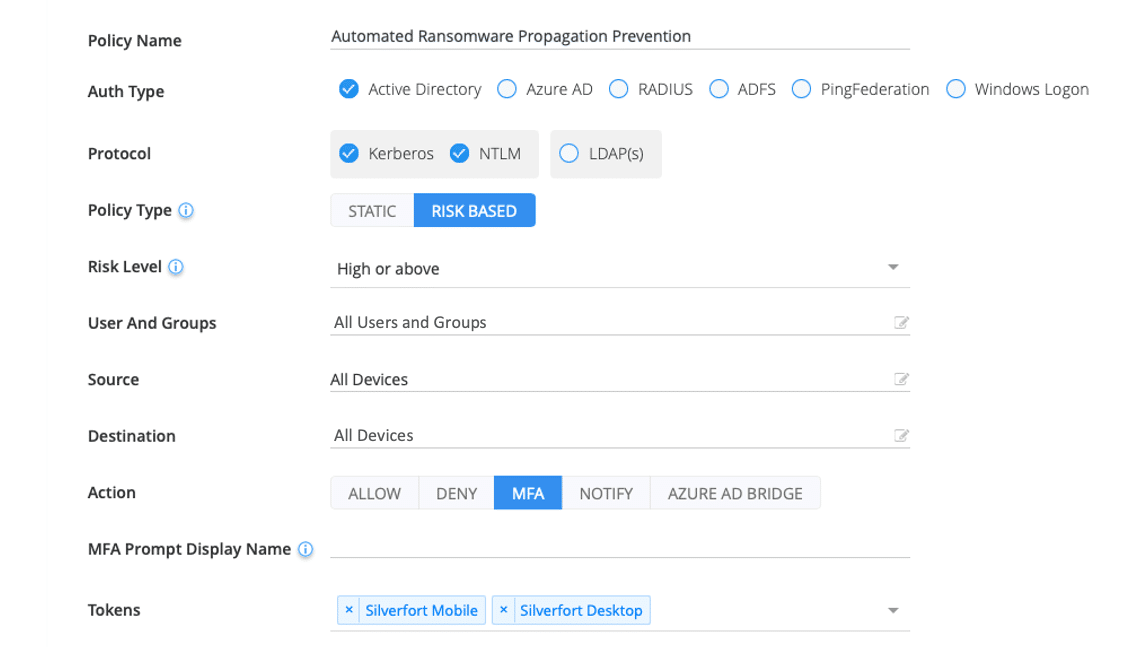
Silverfort enables users to create access policies that utilize its real-time risk score to trigger a protective action – stepping up authentication with MFA or even blocking the access altogether. The policy against automated ransomware propagation would require MFA wherever a user account’s risk score is either ‘High’ or ‘Critical’, and would apply to all access interfaces – Powershell, CMD and CIFS, which is the dedicated protocol for providing shared access to network folders.
With this policy enabled, whenever the ransomware attempts to expand to another machine, the connection would not be permitted without MFA verification of the actual users whose credentials were compromised. Effectively, it means that the propagation would be prevented, and the attack would be contained to the single, patient-zero endpoint.
Conclusion: It Takes a Dedicated Identity Protection Approach to Prevent Automated Propagation
Automated propagation is the most lethal component in ransomware attacks and is the key game changer in the risk they introduce to enterprises today. With Silverfort’s Unified Identity Protection platform you can finally have this critical blind spot covered and checked, materially increasing your enterprise’s resilience to attempted ransomware attacks.