While transition to the cloud and digital transformation are continuously reshaping IT, Active Directory (AD) is a still a key component in the environment of almost every organization. The common assumption is that for the foreseeable future most organizations will maintain a mixed on-prem/cloud environment. This introduces a critical security gap because unlike the cloud, AD doesn’t natively support identity protection controls such as MFA, making it alarmingly exposed to an attack that utilizes compromised credentials to access targeted resources. While MFA does exist for local logins and RDP connections, it is absent from key access interfaces such as PsExec, PowerShell, and others that are extensively uses by threat actors in lateral movement and ransomware attacks. Silverfort’s Unified Identity Protection is the first solution that delivers complete MFA protection for Active Directory environments, eliminating the risk of compromised credentials and introducing cloud-level identity protection and MFA for on-prem environments.
A Short MFA Recap – How Does it Work and for what Purpose?
In its simplest form, authentication involves a user providing credentials and an identity provider that checks if the credentials match and based on the result, either allows or denies access to the requested resource. MFA acts as an additional step within this process – following the positive result of the credentials check, the user is required to provide additional proof of his/her identity. In that manner, even if the credentials become compromised, they do not suffice to render access, materially reducing the potential risk of such scenarios.
So What is the Problem with MFA for Active Directory?
Authentication Protocols that don’t Support MFA
Since the core Active Directory authentication infrastructure was designed and built long before MFA even existed, there is no way to add the MFA step we’ve described earlier to the authentication process. This applies first and foremost to command-line based remote access interfaces such as PsExec, PowerShell PSEnter-Session, WMI. These interfaces are the tool of choice for system admins and helpdesk staff to resolve issues at remote machines – but also for attackers who seek to compromise the network through manual or automated lateral movement.
Reliance on Agents and Proxies = Partial Coverage
RDP stands out as a relatively secure remote authentication alternative since it does support the placing of MFA process within its authentication flow. However, in order to place this protection, one with either must install an MFA agent on each protected server or place a proxy in front of each network segment. This almost always results in partial coverage because agents are never deployed on 100% of the machines and proxies fail to hermetically cover networks that exceed the most basic topology.
Silverfort MFA Protection for Active Directory
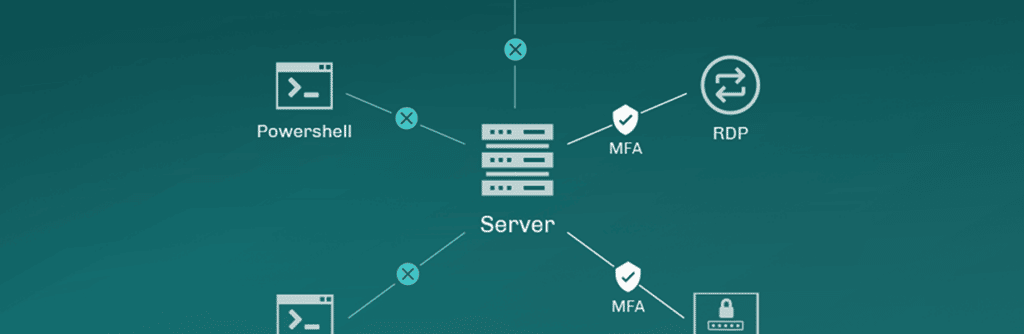
The Silverfort Unified Identity Protection platform delivers end-to-end MFA to Active Directory environments, overcoming the gaps in traditional MFA application. Utilizing agentless and proxyless technology, Silverfort analyzes every Active Directory authentication request and if there is a need, pushes MFA notification to the requesting user. Only after successful verification does Silverfort instruct Active Directory to let the user access the requested resource. This process is completely agnostic to the access method, enabling Silverfort to extend MFA protection across the following:
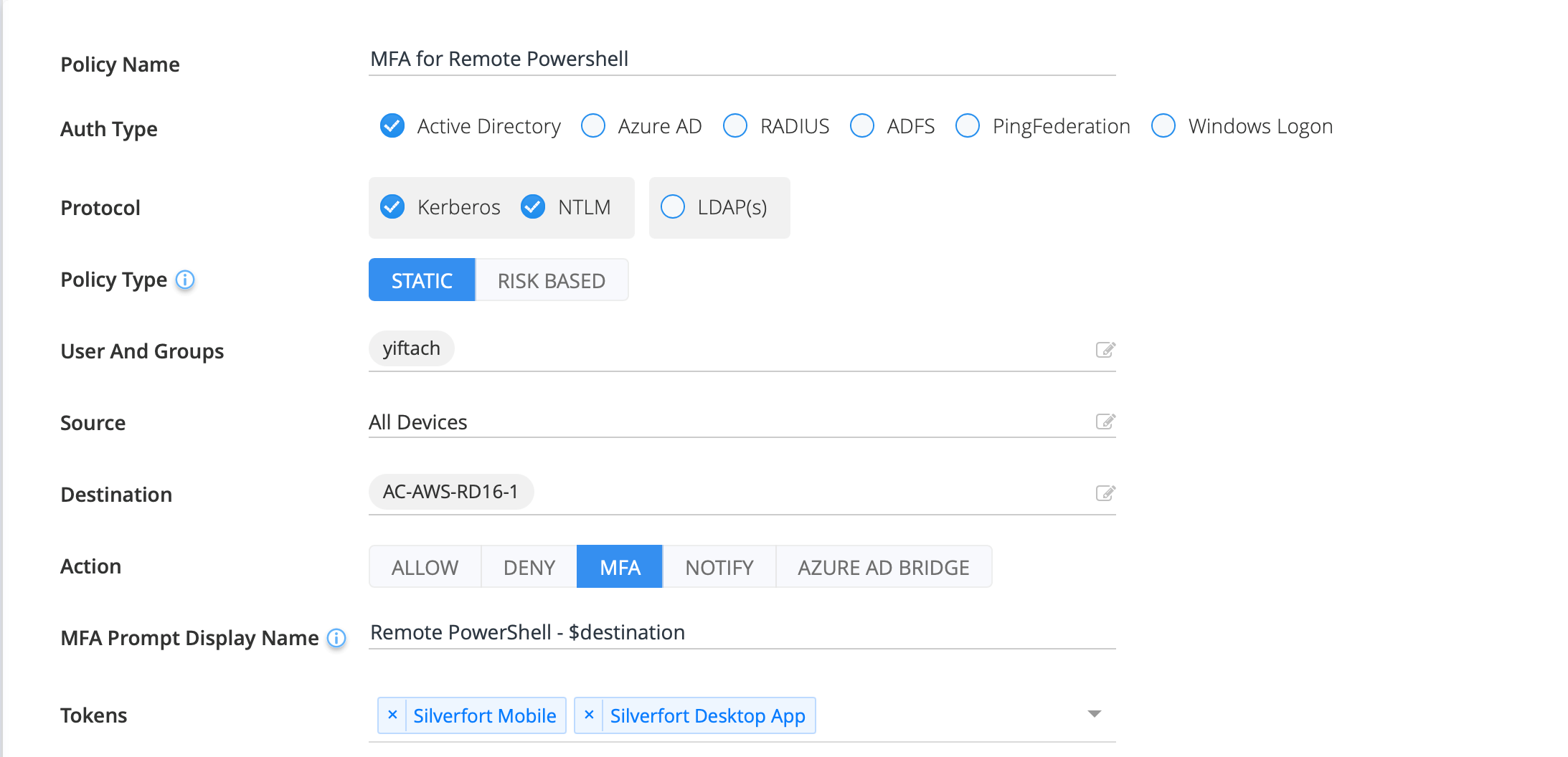
MFA for PowerShell
PowerShell increasingly has become the tool of choice for system administration and includes various cmdlets and utilities for remote access. Unfortunately, its use in cyber attacks has risen in direct proportion. Silverfort enables its users to enforce MFA on PowerShell connections based on either rules or automated discovery of risk indicators.
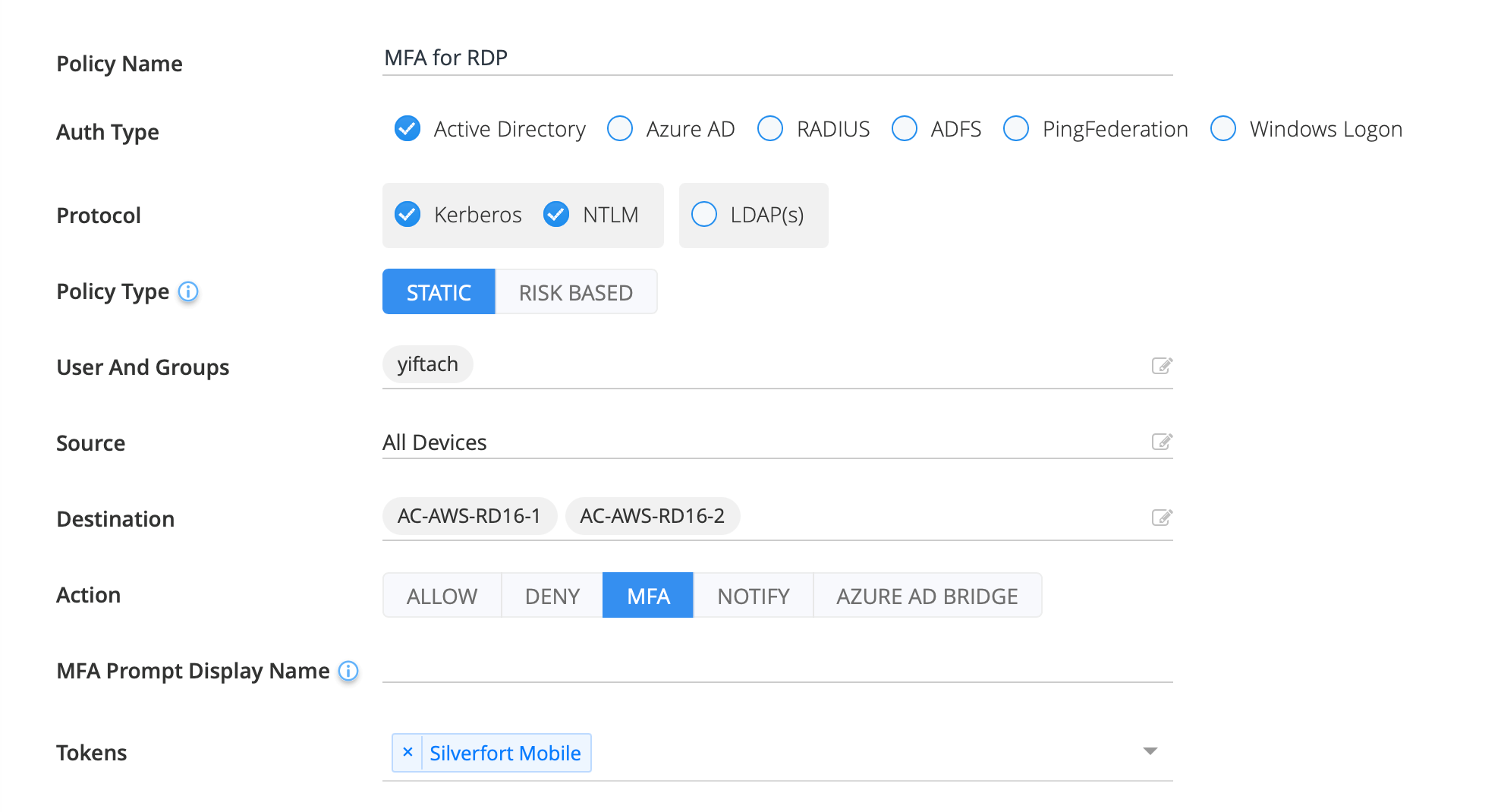
MFA for RDP
Unlike its peers, RDP is not command-line based but enables direct interaction with the remote machines’ GUI. This expands its usage to a large portion of the non-technical members of organizations, especially in the COVID remote workforce era. While traditional MFA can be applied to RDP it is subject to the limitations of proxies and agents that we’ve described earlier, resulting almost always in partial coverage that leaves a gap for attackers to take advantage of.
As opposed to this, Silverfort’s agentless and proxyless technology seamlessly enforces MFA on RDP connections in the environment to render end-to-end security.
Cool, But Can Silverfort Deliver MFA to Other Access Methods in Active Directory Environments?
The concept is simple – if the resource authenticates to Active Directory, Silverfort can enforce MFA. As simple as that. This holds true regardless of the access methods. We’ve dedicated space to PowerShell, MFA for PsExec and RDP since they are extremely common, but the same protection logic applies equally to any existing or future authentication vector that passes through Active Directory – WMI, database connections, on-prem application or any other.
It is Time to Realize that MFA Protection for Active Directory is a Must
Active Directory is here to stay. Cyberattacks thrive on the historic absence of active identity protection for Active Directory environment that in practice means that if your user accounts’ credentials get compromised, it’s game over. The good news is that we don’t have to accept this anymore – Silverfort makes MFA for Active Directory accessible, comprehensive and easy to deploy, making your organization resilient to cyberattacks as never before.
Learn more about Silverfort: