The traditional domain-joined world of Active Directory (AD) has collided with the explosion of cloud services, SaaS apps, non-human identities (NHIs), and autonomous AI agents, creating a vast – yet often invisible – attack surface.
What used to be a well-patched castle of Kerberos tickets is now an AI-driven jungle of token sprawl, over-provisioned service accounts, and lateral movement at machine speed.
But the truth is, even as what constitutes “identity” keeps evolving, many organizations still grapple with fundamental challenges that have existed since the early 2000s. That’s right, I’m talking about legacy Active Directory.
While CISOs moved on to conversations about secure AI adoption with the rest of the C-Suite, the CIO and IAM teams continued to quietly operate in the background – focusing on how to support business needs and collaboration capabilities that exist regardless of what kind of infrastructure keeps the company humming along.
IAM != Identity Security
There’s a clear misconception that how IAM operates present-day is the best (or only) approach to folding in security when it comes to identity, and now is the time to get the CIO and CISO on the same page.
Provisioning access does not equate to controlling the risk that access brings with it. This is where identity and security collide, and it begs the question: “Hey CISO, are you comfortable with your CIO’s Active Directory strategy in the AI era?”
I’ll give an example: Does the IAM team sync on-prem AD to Entra ID? Jane Doe in marketing changes her password, which now in addition to being stored on-prem, has been replicated and stored in the cloud. Data processing and security look different on-prem versus in the cloud, so the infrastructure team just expanded the organization’s attack surface while doing the jobs they are, in fact, supposed to be doing.
In the rest of this post, we’ll explore the evolution of identity risk, why a specific identity security strategy needs to be a collaborative effort between the IT and security teams, and how to take actionable steps to establish shared goals while maintaining compliance.
Identity is now the #1 attack surface
Active Directory was never designed with AI in mind. We had centralized trust, Kerberos authentication, and Group Policy easily defined because of a limited perimeter. Identities were mostly human, and privilege escalation followed predictable lateral paths (e.g. pass-the-hash). Security followed a clear model: GPO hardening, Tier 0 networks, and golden ticket defenses.
But then came cloud and hybrid transformation…
The perimeter dissolved. Hybrid became the norm, as organizations still maintained on-prem AD for business-critical applications and compliance mandates while extending identities into Entra ID or Okta. The easy availability of SaaS applications meant shadow IT was more prevalent than ever before, and many identities now proliferate outside the SOC’s view.
Fast-forward to non-human identities and agentic AI. NHIs like service accounts and API keys now outnumber human identities by at least 50:1, while AI agents are granted access to files, financial systems, calendars, and codebases – leaving behind new tokens, credentials, and logs.
The end result? Your AD is now just one spoke in a hub of disconnected, over-permissioned systems. Identity risk is now dynamic, so you can’t rely on static role-based models. Breaches like SolarWinds exploit federated identity and SAML token forgery, exposing the truth that identities are often persistent, over-permissioned, and poorly governed.
Instead of approaching “identity” as a pure access management play, you need continuous security evaluation.
“Your AD is now just one spoke in a hub of disconnected, over-permissioned systems.” -Eric Haller, Advisor
What’s changed in the risk landscape?
With AI and digital transformation, identity utilization changes. It becomes federated (cloud), and it also becomes impersonated (AI), so the problems of achieving visibility and establishing control become harder to solve. This landscape means communication and strategy need to change, too; the IAM team responsible for provisioning infrastructure needs to be in lock step with the security team securing that infrastructure, and vice versa. There is no in-between anymore.
Below are the north star goals that must be shared because of this new reality:
- Maintain an identity inventory
- Use the Principle of Least Privilege
- Configure systems from an identity-first perspective
Guidance on putting the north star goals in place and their respective action items
Let’s get specific on what these north star goals look like and why they matter.
Step 1: Know and classify the identities that exist
Gartner has started calling this “Identity Inventory and Visibility and Intelligence Platforms (IVIP),” but it’s just a fancy way of saying that both the identity and security teams should be able to say which identities exist, what types of identities they are, and how those identities interact with the systems around them. A real-world example would be that the identity team provisions access to a certain folder in SharePoint, and the security team has visibility into that identity’s existence and permissions. Based on their knowledge of security best practices, the security manager can provide least-privilege recommendations after seeing the full picture of an identity’s access in the organization. The security leader could also provide key context into what other gaps exist or what other access the account could have beyond the intended provisioning. This presents a validation and risk assessment opportunity that typically falls to the wayside, especially as the number of identities in an organization keeps increasing. Again, this is only possible when we know what identities exist and their relationships in the entire hybrid environment.
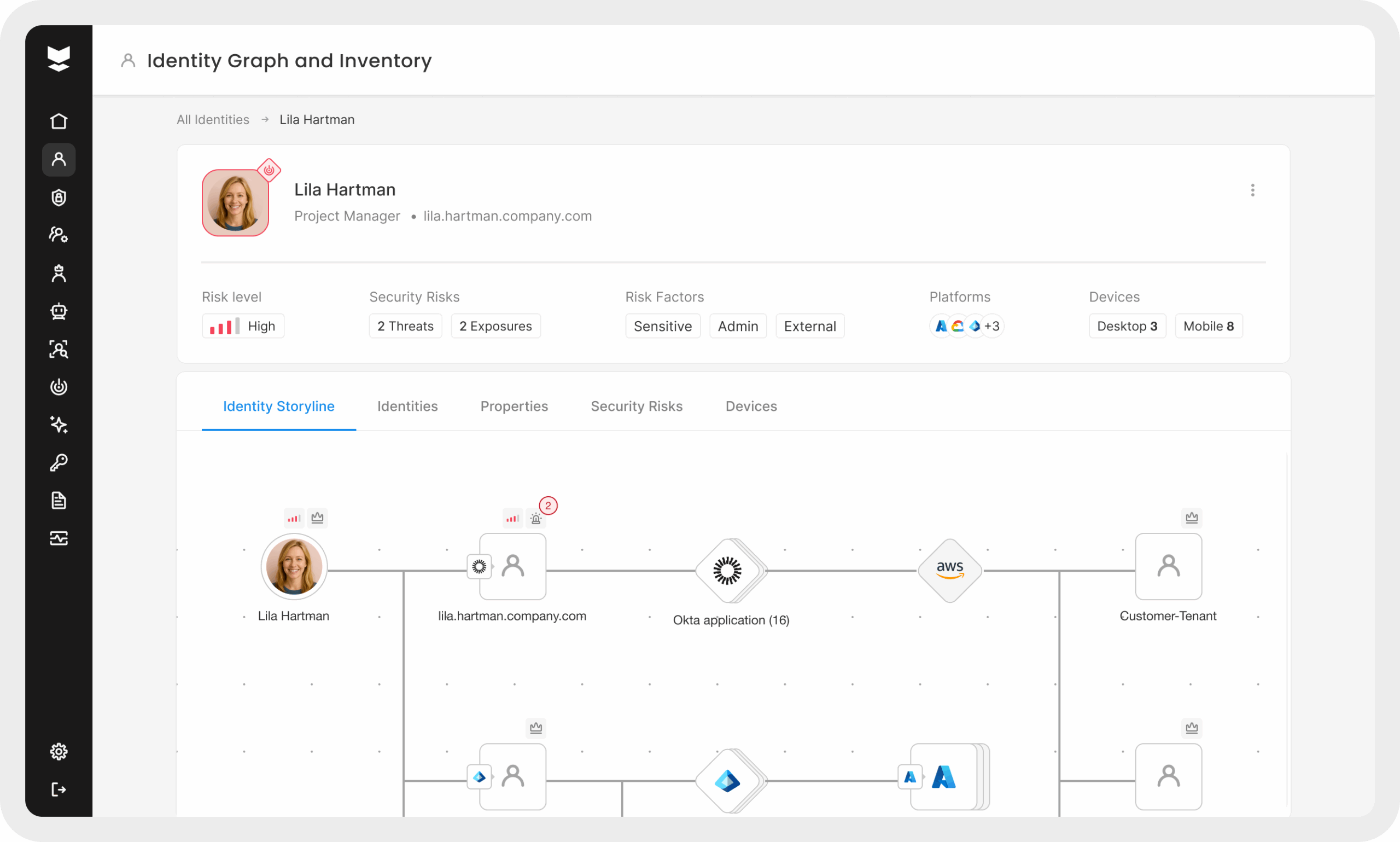
Step 2: Prioritize all privileged identities (not just the ones PAM knows about)
Chances are your organization uses a Privileged Access Management (PAM) solution. The problem with that is PAM is only as good as the identities it has in its system. It’s important to identify and tier all privileged accounts based on actual authentication activity. This will help you map the risks across the entire environment and empower the security team to implement Just-in-Time (JIT) access controls. The IAM team can support here by providing additional context on each privileged identity and ensuring strong ownership and documentation. Another benefit is the ability to inform a more robust SOC alert engineering strategy based on the level of detail shared.
Step 3: Strengthen the underlying security hygiene
A more secure environment is also an easier one to manage and provision. For example, that Ops team contractor who ended work 6 months ago? They’re still in the system. Continuous monitoring helps “clean up” what exists and why in the overall identity inventory, making it easier for both the security team to shrink the attack surface and the identity team to manage the systems and applications in use. Taking it a step further, the two departments can work together to apply risk-based conditional access policies and isolate scopes, further streamlining synergy with SIEM/SOAR pipelines that flag unusual activity. This is one of the most important considerations for establishing shared outcomes between IAM and security teams – with the CIO and CISO working together, automated prevention tactics like closing the contractor’s access, can be deployed prior to abuse.
A feasible action plan to work from shared objectives
After establishing your north stars, it’s time to get the CIO, CISO, and their respective IAM and security teams in a room talking to one another. These are the topics to go over together that will: a) confirm measurable outcomes and b) identify the communication and project gaps that need closing:
- Map your crown jewel systems and who (or what) accesses them
- Identify the top 10 riskiest identities based on privilege, usage, and sprawl
- Develop SOAR playbooks to monitor key identity lifecycle events, such as latent access termination (or the like)
- Partner on alert engineering (and enrichment/context flows) to improve SOC visibility into account abuse – this leverages IAM’s knowledge of intended users (versus security’s view of actual users) to improve protections
- Establish communication processes when incidents missed in detection (security) and caused by control failure (IT) that open the door for control improvements (IAM) and security coverage
- Start using behavioral-based MFA, identity-first threat detection, and fine-grained logging
If you control identity, you control the kill chain
In a world of automation and AI where Active Directory still powers business continuity and productivity all the same, identity is the new endpoint, the new perimeter, and the new key to the kingdom. If you can’t see it, segment it, and secure it – a feat that takes both IAM and security working from shared behaviors and goals – you’ve already lost.
Let’s get serious about next-gen identity defense, because the next breach won’t be a brute-force attack – it’ll be an autonomous AI agent with an old API key.
To get started on building shared outcomes and projects between IAM and security teams, start by building your identity inventory to illuminate what’s really going on in your environment.

