As ransomware attacks continue to skyrocket, both in frequency and intensity, underwriters of cyber insurance policies have been dramatically tightening their requirements in order to stem financial losses. Over the past three years, for example, the number of claims related to cyberattacks has doubled, with insurance companies posting a record-high 72% cyber loss ratio in 2020. Meanwhile, ransomware attacks rose 105 percent last year, up to 623.3 million attacks globally, with the average payout now costing $570,000.
In response, insurers have been revamping their cyber insurance policies to be much more specific about which security controls must be in place. The first major change came last year, when companies began mandating that multi-factor authentication (MFA) controls be enforceable across numerous systems in the environment, including cloud-based email, remote network access, as well as admin access to directory services, backup environments, and network infrastructure.
Recently, underwriters have gone one step further, with many of them also requiring that all privileged accounts be protected. This post examines why insurance companies are now focused on these accounts in general and specifically on a subset of privileged accounts: service accounts.
The Link Between Ransomware Attacks and Service Accounts
Threat actors have increasingly been using a particularly stealthy tactic to move freely across an environment: lateral movement. Lateral movement is the stage of an attack that comes after initial access, where attackers make use of compromised user credentials to access as many machines as possible in order to maximize the attack’s payoff by encrypting multiple machines simultaneously.
Successful ransomware attacks often make use of a compromised service account, which is a non-human account used for machine-to-machine (M2M) communication that performs a critical process (such as a network scan or a software update) repeatedly and automatically. These accounts are very attractive targets for attackers since they are usually highly privileged, with admin-level access to numerous systems.
Several recent high-profile cyberattacks, in fact, have involved a compromised service account, including the SolarWinds Hack of 2021 and the Uber Breach earlier this year.
Security Challenges of Service Accounts
Service accounts are especially vulnerable to compromise for two important reasons. First, they often have low visibility, since there is no diagnostic tool that can discover them and monitor their behavior. Second, service accounts are typically excluded from password rotation as they are often embedded within scripts. The upshot is that once one of these accounts is compromised, an attacker will be able to move around an environment undetected and for an unlimited amount of time.
This is exactly why insurers are concerned about service accounts have recently started requiring companies to conduct inventories as well as put in place specific security measures to prevent attackers from using them for malicious access.
The New Requirements to Obtain a Cyber Insurance Policy
Among the requirements companies must now meet are the following:
- There is an inventory of all privileged service accounts, updated at least quarterly – including what each service account is used for and why it requires domain admin entitlements
- Service accounts are tiered so that different accounts are used to interact with workstations, servers, and authentication servers
- Service accounts are configured using the principle of least privilege and to deny interactive logins
- There is a process in place to regularly review the requirements for each privileged service account to verify it still requires permissions that it has
- There are steps being taken to mitigate any exposure the service accounts’ configuration creates that could result in credential harvesting
- Specific monitoring rules are in place for service accounts to alert the Security Operations Center (SOC) of any abnormal behavior
These requirements present serious challenges to companies seeking a new (or looking to renew an existing) cyber insurance policy. As mentioned, there is no utility that can generate a report of all current service accounts, which means organizations may find it impossible to produce an accurate count of them and demonstrate a full accounting of their behavior.
But even for companies with up-to-date records, configuring specific policies to monitor all service account behavior would be extremely labor-intensive and a huge drain on IT resources. Furthermore, putting steps in place to protect service accounts from compromise is complicated at best, since rotating the passwords of service accounts can break critical processes.
How Silverfort Enables Companies to Meet the Service Account Requirements
Fortunately, the Silverfort Unified Identity Protection platform was developed to address exactly these issues – and can help companies meet the cyber insurance requirements for service accounts.
Silverfort gives companies the ability to automatically discover and secure all service accounts in the environment via an AI-engine that detects any account that displays repetitive, machine-like behavior. Once detected, Silverfort can then continuously monitor those accounts and all the places they authenticate to, providing security teams with real-time insights into their activity and level of risk.
Silverfort also comes with ready-to-use access policies tailored to each service account based on its specific pattern of behavior, with any deviation immediately detected and resulting in either blocked access or an alert sent to the SOC team – thus preventing threat actors from using them in lateral movement attacks.
In addition to rule-based policies, adaptive risk-based policies can be easily created to activate as the risk level of an account increases. This level of granular protection means that service accounts can be fully protected without rotating passwords, which can break mission-critical processes.
Here is a summary of the capabilities Silverfort provides around service accounts:
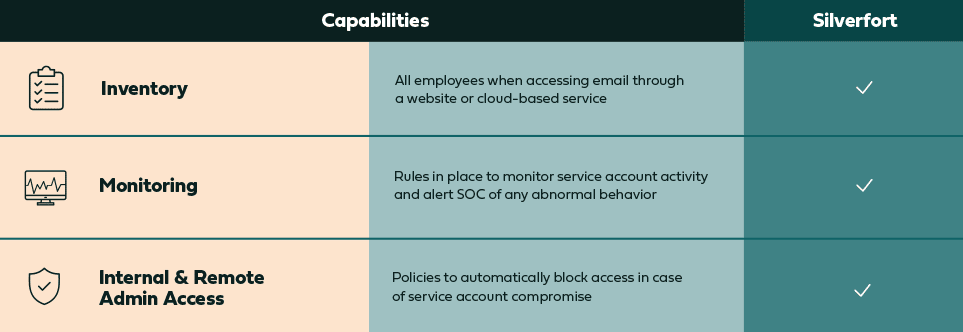
With Silverfort in place, organizations will find meeting the new requirements around service accounts to be painless and straightforward, allowing them to qualify for a cyber insurance policy and regain peace of mind. To learn more, request a demo here.