Service Account Protection
Discover, monitor and protect service accounts (M2M access) with fully automated visibility, risk analysis and adaptive Zero Trust policies, without requiring password rotation.
Automated Discovery & Monitoring
Gain automatic and comprehensive visibility into all your service accounts and non-human identities, including the ones you’re not aware of, as well as real-time insights into their activity and risk level.
Proactive Threat Prevention
Place a virtual perimeter around your service accounts with ready-to-use Zero Trust access policies tailored to each account’s behavior to prevent threat actors from using them in lateral movement attacks.
No Password Rotation
Protect your service accounts completely and at scale without the operational concerns of unknown dependencies and the breaking of mission-critical processes that comes from password rotation.
Discover all your service accounts
- Automated AI-based discovery of all accounts with machine-like behavior, as well as typical service account attributes and naming conventions.
- Complete visibility into all service accounts and real-time insights into their sources, destinations, authentication protocols, and activity volume.
- Discover accounts that are being shared by both human users and services.
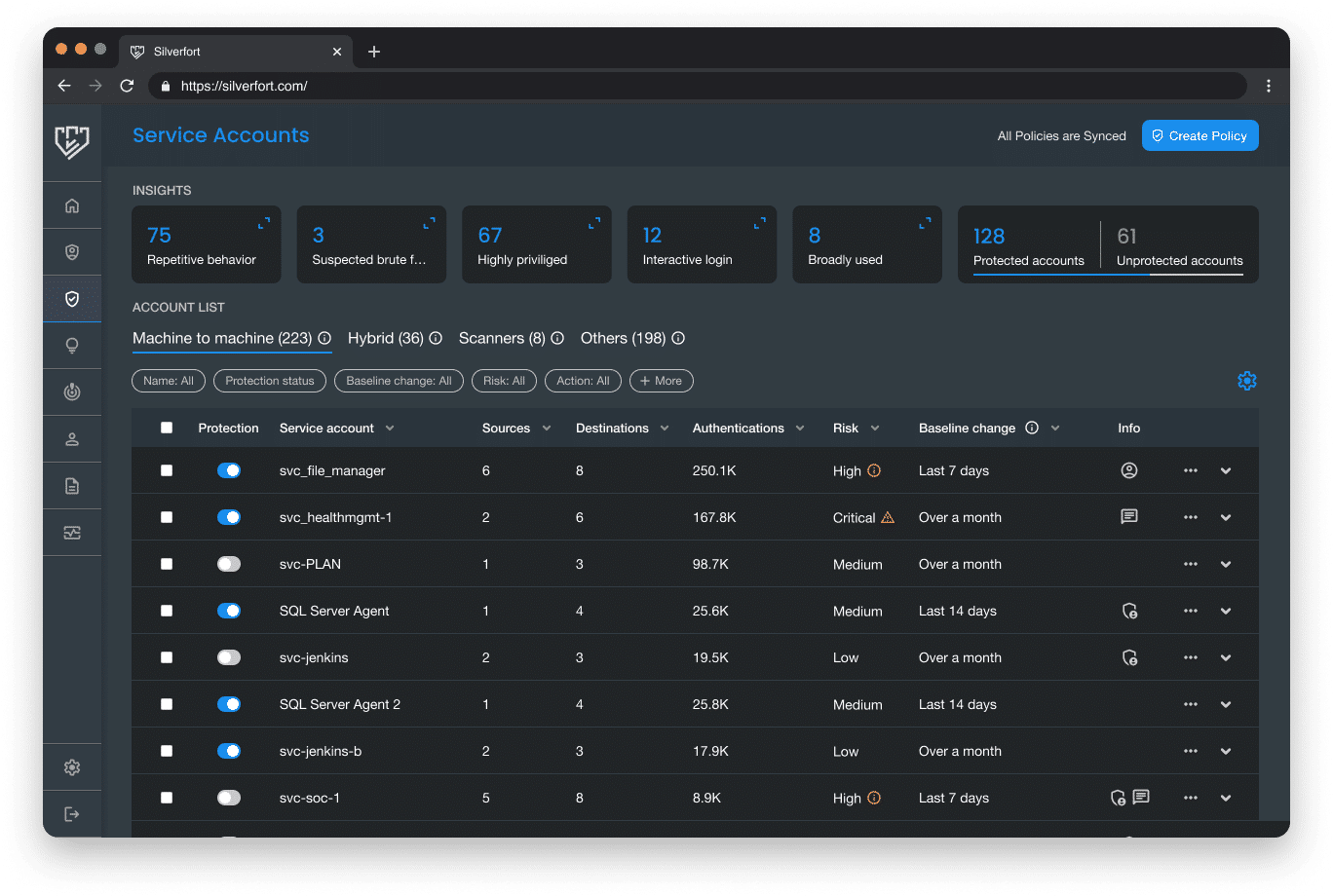
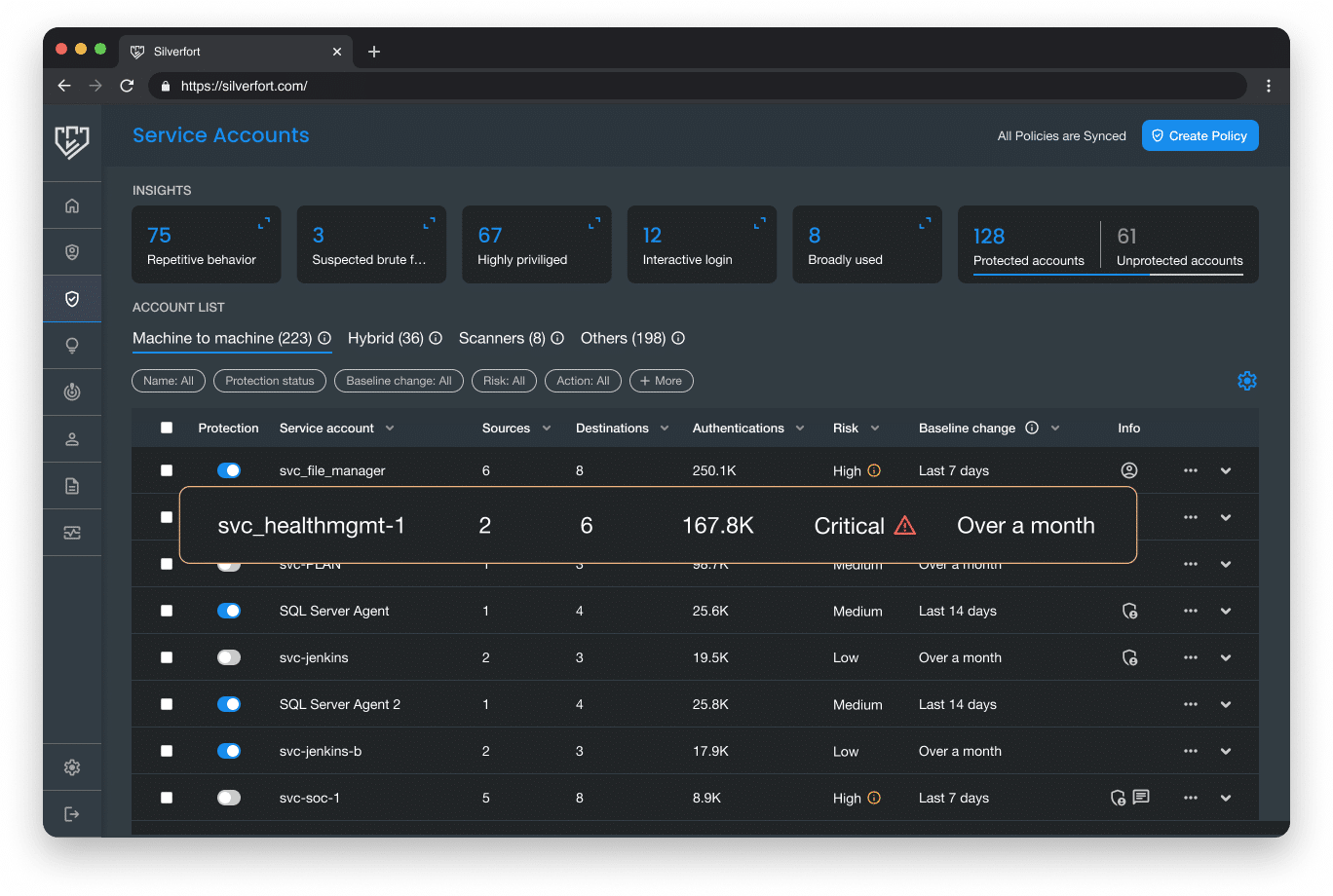
Monitor service account activity and risk
- Monitor service account activity continuously in real time.
- Track the usage patterns, access requests and behavior of each service account, including high-level permissions, broad use, and repetitive behavior.
- High-precision anomaly detection which alerts of any deviation from the service account’s standard behavior.
Analyze all service account activity
- Assess the risk of every authentication attempt and detect any suspicious behaviors or anomalies.
- Utilize enriched contextual data and risk scoring for each service account.
- Provide SOC teams with logs and actionable insights into overall service account activity.
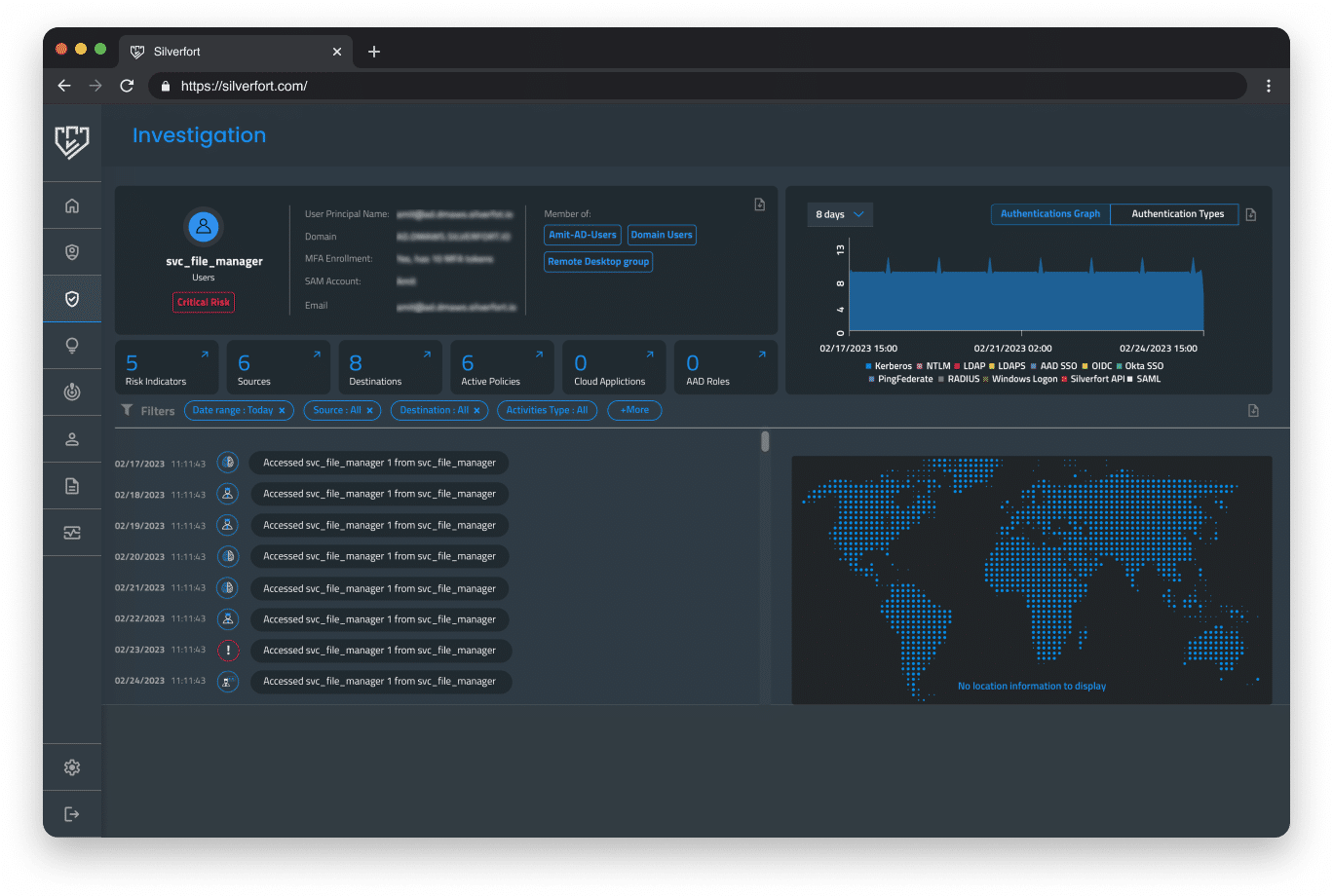
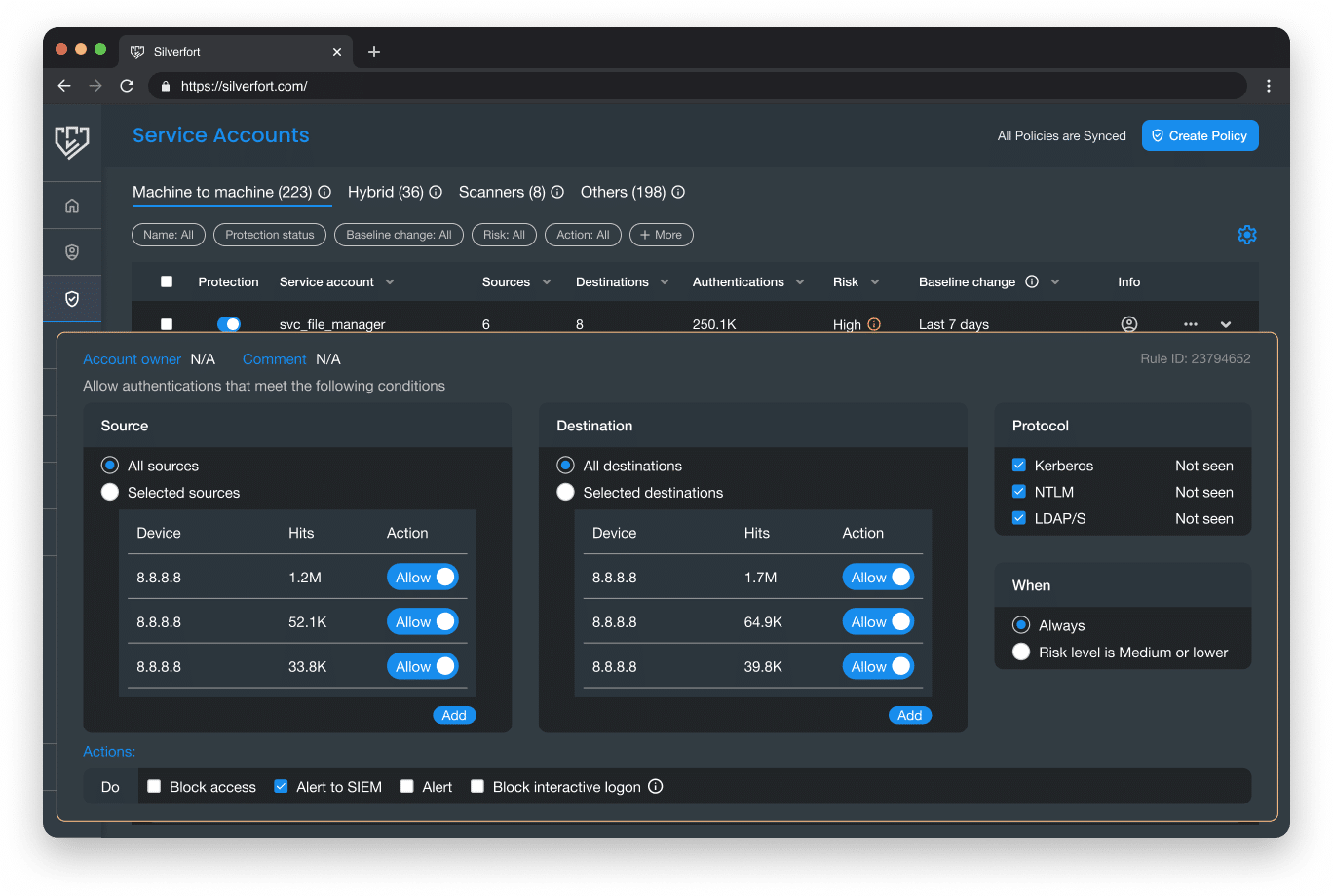
Evaluate service account policies
- Silverfort automatically suggests a tailor-made policy for each service account based on its behavioral pattern.
- Build out custom policies to fine-tune and adjust protection as needed.
- Customers can start with alerting mode and gradually advance to full protection.
"Service accounts are a security nightmare because you can’t put MFA on them. Silverfort was able to protect what no one else can, including our service accounts. Of the security tools that we use, Silverfort has a very high return on investment."
Tom Parker | VP of IT & CISO

Customer Challenge
Kayak struggled to find a solution that could extend identity security controls over their entire environment, particularly their critical applications that use LDAP and their service accounts.
Silverfort Solution
Silverfort enabled Kayak to put real-time protection on service accounts by enforcing policies that block any access that deviated from normal behavior. Because of this, even if attackers could compromise the credentials of their service accounts, they would not be able to use them for malicious access.
How they rate us:
4.7 – 28 Reviews