Identity has changed – in a world where business occurs across systems, time zones, and even between humans and non-humans, “identity” no longer means a single person logging into a single device in a single location. So why are we still approaching identity security as if it’s 2005? There must be a better way: a way that doesn’t consider a disjointed set of IAM, IGA, and PAM solutions the only option, but also considers where visibility, posture, protection, and threat analysis come into play. This is where identity security sits – going beyond authorization and access management and entering the realm of real-time prevention and detection and response.
According to research from the Securing the Identity Attack Surface report, “75% of detections are malware-free (a malware-free attack enables adversaries to operate under the radar and navigate seamlessly across endpoint and cloud domains).” So yes, that saying “Attackers aren’t breaking in, they’re logging in” is true now more than ever, and there’s no turning back.
Yet, while identity management doesn’t equate to identity security, IAM, compliance, and security teams are still in the position of needing to solve the same problems as back when “securing” identities meant governing access for one person, one device, one location. These unchanging challenges include solving how to:
- Gain visibility into all identities, everywhere
- Decrease operational and systems complexity
- Improve processes and communication
- Reduce the likelihood of security incidents (or at least contain them when they do occur)
This is why we’ve created the industry’s first Identity Security RFP checklist, a resource designed for identity, compliance, and security teams to evaluate vendors across six focus areas so they can ask the right questions that lead to selecting comprehensive, best-of-breed solutions.
In this blog, we’ll loosely touch on these six core capabilities every identity security solution should have that, when satisfied, set up your organization for success regardless of environment, company size, or industry.
To jump to the full Identity Security RFP Checklist, click here.
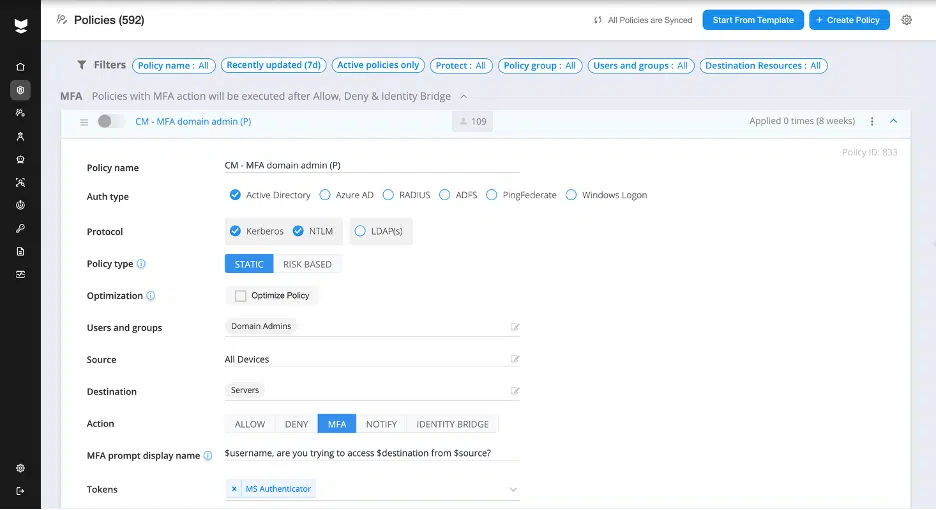
Capability #1: Enable universal Multi-factor Authentication (MFA)
Most MFA solutions weren’t designed to cover everything – leaving behind a trail of unprotected systems, legacy protocols, and unmanaged interfaces. To add further complication, even where MFA is deployed, implementation is often complex – requiring agents or proxies – and managing multiple MFA tools across on-prem and cloud leads to redundant costs and inconsistent user experience.
What organizations really need is universal MFA: the ability to extend protection to any resource, without modifying servers or applications, and without being locked to a single MFA provider.
To get to the root of whether a solution provider offers universal MFA, key questions to ask include:
- Does your solution extend MFA for systems that are more challenging, i.e., command-line tools like PsExec to IT/OT infrastructure and custom apps?
- Does your solution eliminate the need for agents or proxies with real-time or inline enforcement?
- Can your solution provide MFA for all AD authentications, including NTLM, Kerberos, LDAP and LDAPS?
- Does your solution extend Entra ID conditional access to AD-managed resources?
- Does your solution integrate with Okta MFA?
Capability #2: Enforce least privilege access
Once an attacker gains a foothold in systems, there’s often no way to stop lateral movement or privilege escalation without impacting core systems. Worse yet, most detection tools trigger only after the damage is done.
What’s needed is inline enforcement at the point of authentication – deep within the identity infrastructure – so access can be blocked or challenged before a session is ever established. You need to be able to inspect every login attempt and continuously assess risk to enforce policy before a session ever begins.
To get to the root of whether a solution provider enables your team to enforce least privilege access, key questions to ask include:
- Does your solution have runtime access protection, offering preemptive, inline security controls at the authentication layer?
- Can your solution prevent lateral movement and ransomware propagation as it’s happening?
- Can your solution prevent PAM bypass by admins that log in directly to resources?
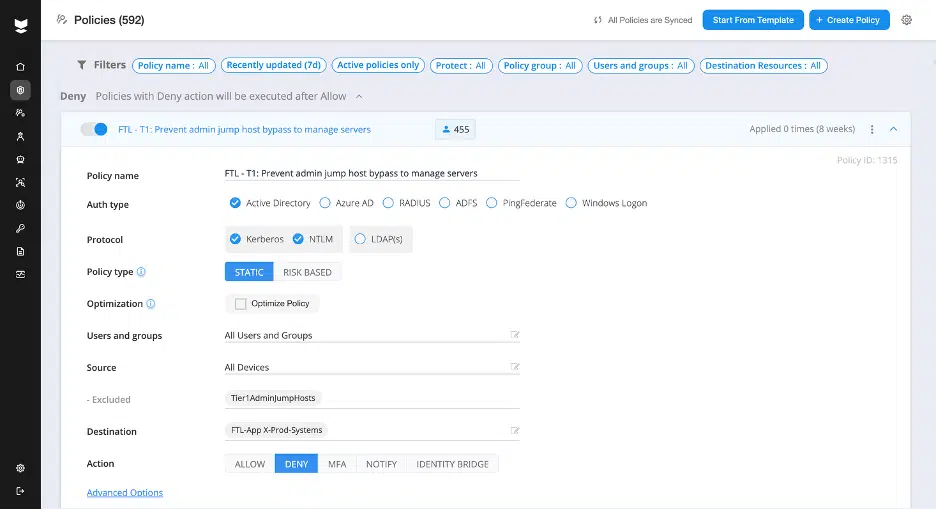
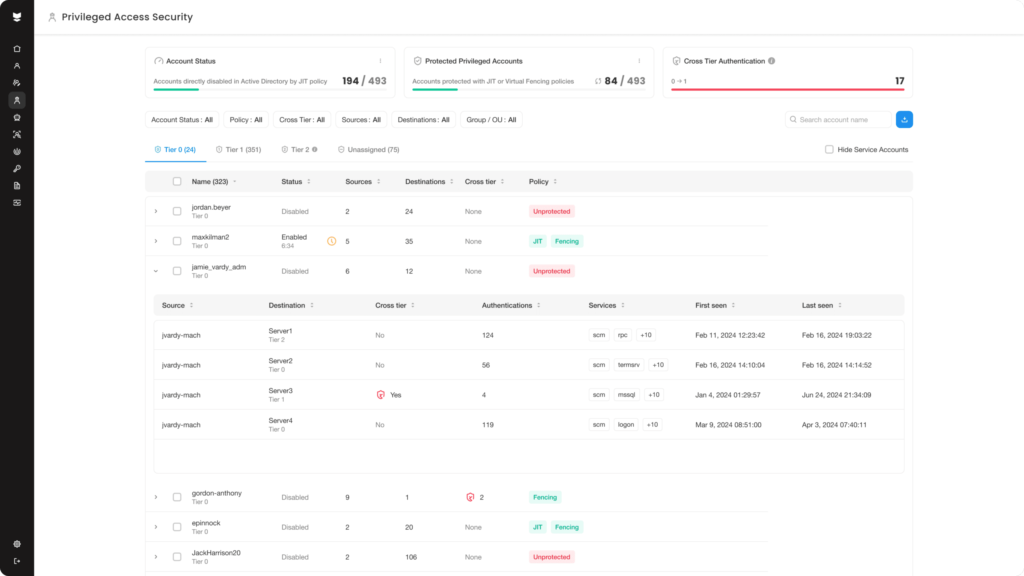
Capability #3: Protect privileged users and accounts
Privileged accounts continue to be one of the most abused entry points in breaches and insider threats. As Chief Identity Security Advisor (EMEA) Rob Ainscough notes in his webinar “Winning the Privileged Access Battle: From Firefighting to Field Control,” security teams typically turn to Privileged Access Management (PAM) solutions to prevent privileged account abuse. However, PAM solutions are difficult to scale, hard to ensure comprehensive coverage (especially where non-human identities such as service accounts are concerned), and it can take months or years just to protect a single account.
What organizations need is an approach that reduces overhead, eliminates blind spots, and enforces least privilege dynamically. To get to the root of whether a solution provider protects privileged users and accounts, key questions to ask include:
- Can your solution discover unknown privileged accounts?
- Can your solution enforce least privilege access by restricting where accounts can be used through virtual fencing?
- How does your solution prevent abuse of privileged accounts without disrupting legitimate workflows?
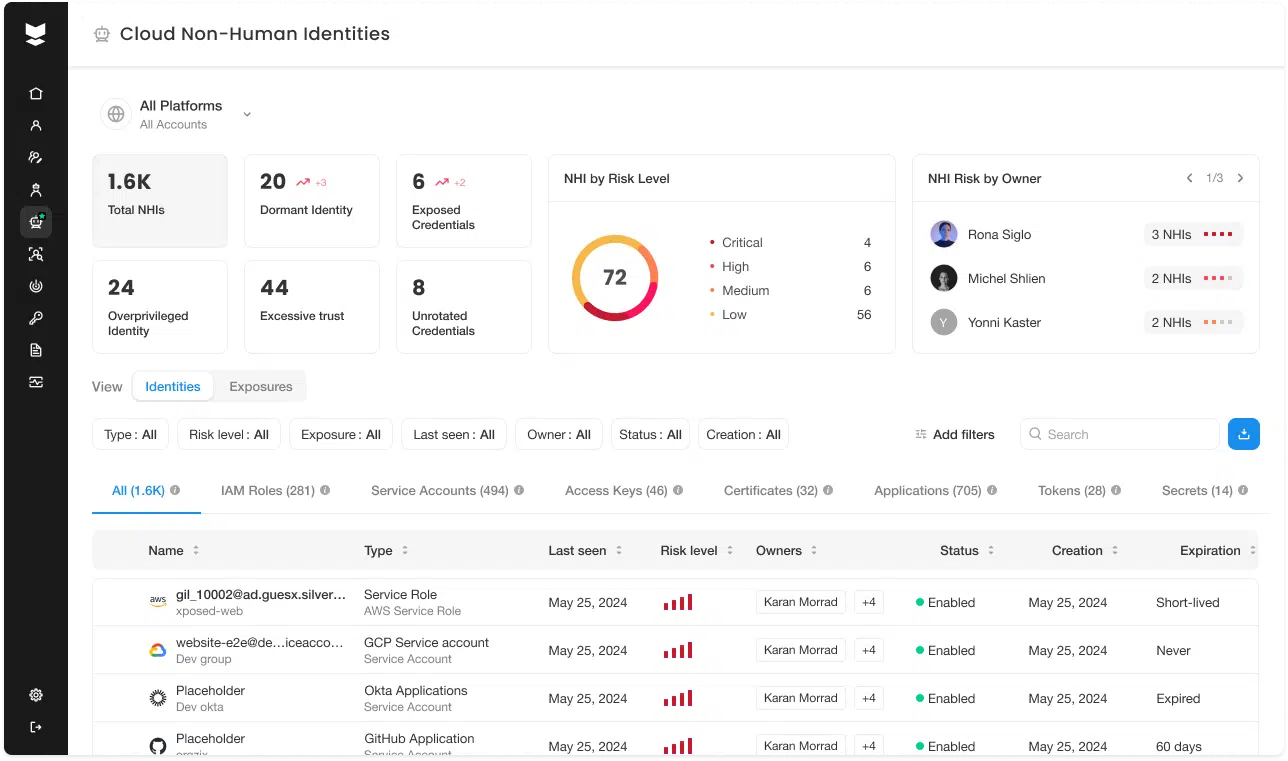
Capability #4: Discover, classify, and secure non-human identities such as service accounts
Non-human identities (NHIs) like service accounts and API keys outnumber human users by at least 50:1, and this divide continues to grow. Yet these identities often operate in the shadows. They’re difficult to discover, lack clear ownership, and are frequently granted excessive privileges.
Modern identity security solutions need to provide complete visibility, active control, and scalable automation to manage NHIs at scale throughout their entire lifecycle – whether in the cloud or on-prem.
To get to the root of whether a solution provider secures every NHI across cloud and on-prem, key questions to ask include:
- Can your solution automatically discover and classify the following types of NHIs or programmable access credentials?
- On-premises AD Service Accounts
- OAuth or Access Tokens
- API Keys
- Certificates
- Cloud IAM Roles
- Service Principals
- Cryptographic Keys
- Can your solution view every authentication request that goes across Active Directory?
- Does your solution automate protection of machine identities at scale using APIs, smart policy engines, and integrations such as CMDB or ticketing systems?
- Can your solution provide identification and inventory of service accounts?
- Can your solution facilitate the onboarding of service accounts to PAM?
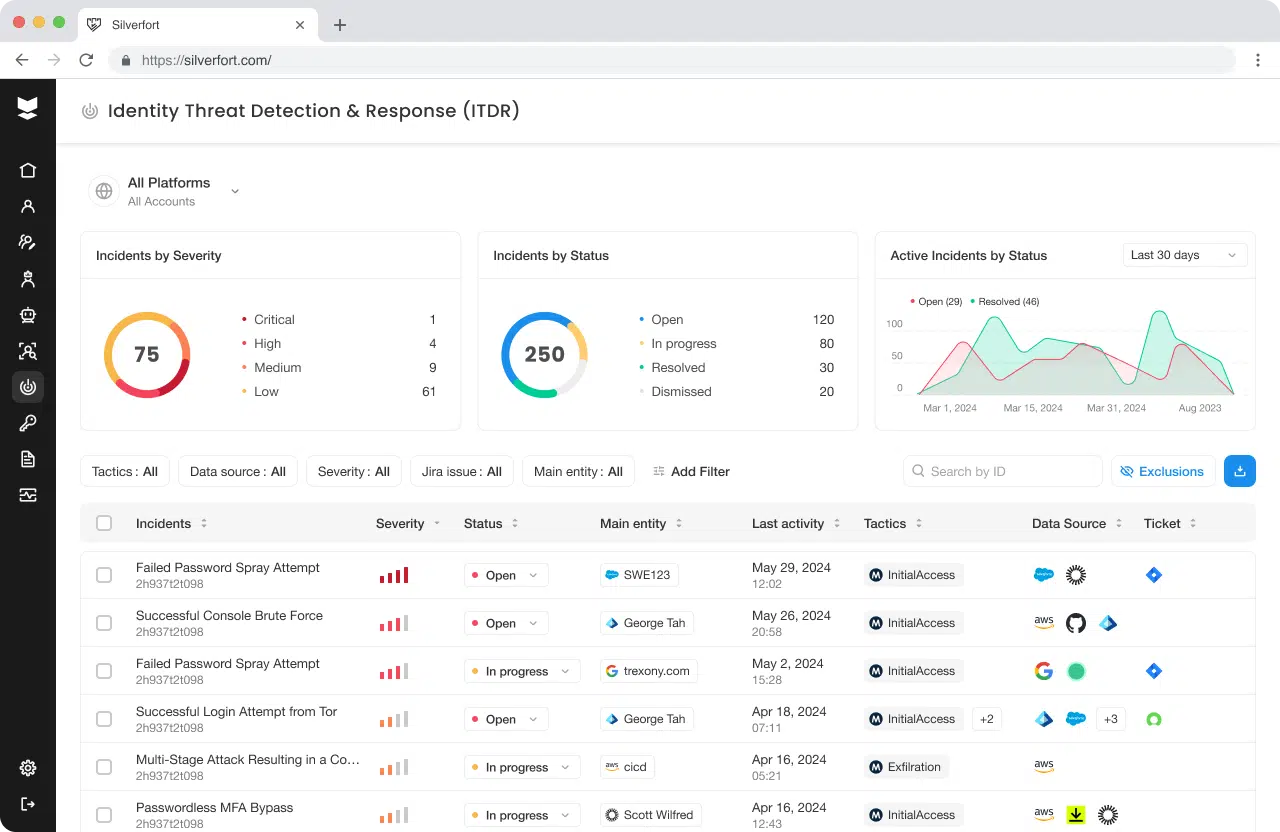
Capability #5: Detect and block credential abuse, stop lateral movement, reduce false positives, and activate real-time response
According to the 2024 Verizon Data Breach Investigations Report, over 80% of breaches involve stolen or compromised credentials. Yet most detection and response tools weren’t built with identity in mind. Additionally, with traditional SIEM platforms it’s difficult to scale detections centered around identity, making it hard for SOC and IR teams to keep pace with evolving threats. Meanwhile, EDRs, XDRs, and CDRs only look at one piece of the puzzle, rather than offering a full picture of threats in the environment.
To close those gaps, organizations need ITDR solutions that are identity-native and proactive. The right platform can identify threats at the heart of many large-scale breaches: lateral movement, privilege escalation, and suspicious access patterns.
To get to the root of whether a solution provider can detect and respond to identity-driven threats in real time, key questions to ask include:
- Does your solution deliver advanced identity-aware threat detection that inspects every access attempt across on-prem and cloud resources?
- Can your solution go beyond passive detection to enable inline, real-time responses to malicious behavior?
- Does your solution stop attackers with step-up authentication, access blocking, or forced re-authentication? And can it do so without halting user productivity?
- If a breach occurs, can your solution contain the attack and ensure it doesn’t spread to additional resources?
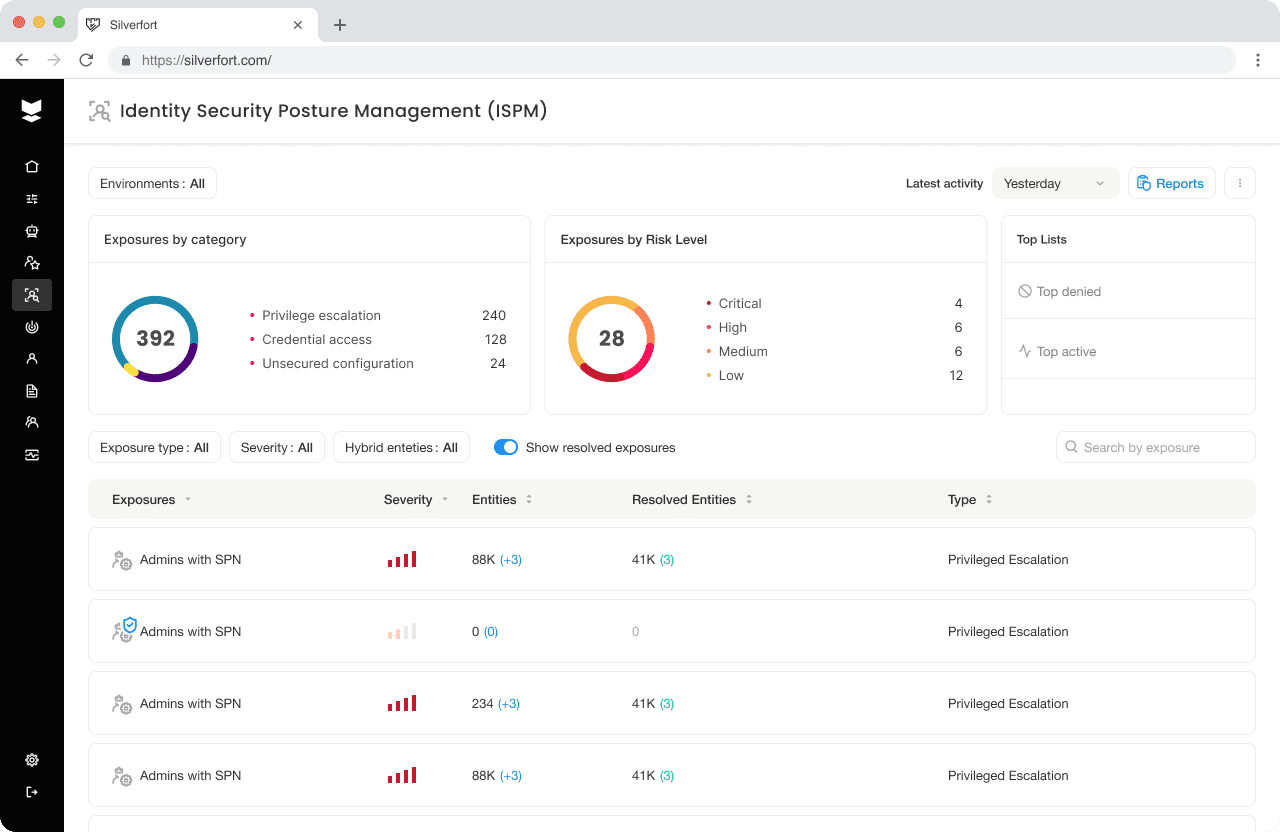
Capability #6: Improve identity security posture, proactively discover risks, and remediate weaknesses across hybrid environments
Weak points in the identity infrastructure – such as misconfigurations, outdated protocols, and excessive privileges – often go unnoticed until it’s too late, leading to account takeovers, lateral movement, and failed audits. Mapping and remediating risks at scale requires centralized visibility, comprehensive protection, and measurable results to improve and maintain identity hygiene.
To get to the root of whether a solution provider offers comprehensive identity security posture management (ISPM), key questions to ask include:
- Can your solution provide a prioritized inventory of identity weaknesses within the organization?
- Can your solution identify exposures associated with user activity and authentication requests, such as legacy protocols?
- How do you identify service accounts that are dormant or no longer in use?
- Can your platform detect users who are not in Domain Admins or other obvious groups, but still have admin-level permissions (shadow admins)?
Download the Identity Security RFP Checklist
These questions are a small sample of what’s available in the full checklist – download it today to see the entire list for each of the six capabilities. The best part is that we also made the checklist interactive for you to customize it based on your team’s needs; once you download, you’ll have the option to get the list of questions in either a Google Sheet or Microsoft Excel format (whatever you prefer!).
It’s time to make identity security your strategic advantage. Based on our identity security experts’ curated list of questions to ask vendors, you’ll leave conversations with vendors with a clear picture of how you can connect the dots, make informed decisions, and stay ahead of threats.
Interested in seeing how Silverfort satisfies the capabilities within the Identity Security RFP Checklist? Browse our platform now.

