Service Accounts Likely Played a Key Role in the SunBurst Attack

***** By Gal Sadeh, Lead Data Scientist, Silverfort *****
Research we have conducted at Silverfort Labs indicates that service accounts likely played a key role in the ability of the SolarWinds attackers ability to move laterally within the victim’s environment. This should serve as a wakeup call for enterprise security stakeholders. Service accounts are a vulnerable and sensitive attack surface that must be protected, in order to harden an organization’s overall security posture. The Silverfort Unified Identity Protection platform protects service accounts as part of its holistic protection of all accounts in the hybrid network. This article includes both a technical analysis of SolarWinds service account behavioral patterns, as well as a demonstration of how Silverfort access policies could have protected against an attack scenario that uses these accounts for lateral movement and access to enterprise resources.
Table Of Contents
Modeling the SolarWinds Service Accounts Behavior
In order to protect against lateral movement based on service account credential theft, it is important to first understand the normal behavior of service accounts. This allows us to distinguish between the expected behavioral patterns and patterns that characterize attackers. For example, the SolarWinds service account normally does not use the remote desktop protocol (RDP) to authenticate to other machines. Any use of that protocol by that service account would be a red flag.
For this purpose, we analyzed authentication data as well as findings from controlled attack simulations and studied three types of service accounts SolarWinds uses to scan networks and access additional machines. In the attack scenarios we examined, these accounts can be used as the primary method for lateral movement. Given the relative ease of using them for this purpose, it is likely they were exploited to carry out the SunBurst attacks as well.
Let’s start by understanding the standard behavior for service account. The graphs in this section show a SolarWinds server as the middle node with edges connecting it to various machines in the network.
Note – The actual names of the accounts are configured by the users in each specific environment. We’ve thus given each type a descriptive name based on its authentication behavior.
Service Account Type 1: RPCSS scanner
- Activity: Scans the network with RPCSS service to remotely control other machines in the network. RPCSS allows the user to do almost anything on the remote machine including the ability to execute code
- Authentication protocol: Kerberos
- Service Principal Names (SPNs):Cifs, DNS, RPCSS, HOST, KRBTGT and LDAP.
- Predictability: High
- Behavior sample:
Diagram 1: RPCSS Scanner service account activity pattern
Service Account Type 2: General Scanner
- Activity: Scans the network with various protocols and when possible uses RPCSS to get access to elevated permissions on a remote machine. Occasionally, this type of service account uses NTLM.
- Authentication protocols: NTLM, Kerberos
- SPNs: RPCSS, HOST, KRBTGT and LDAP
- Predictability: Medium. While part of the activity is repetitive in terms of time and accessed machines, there are many activities that cannot be mapped to a deterministic pattern.
- Behavior sample:

Diagram 2:General Scanner service account activity pattern
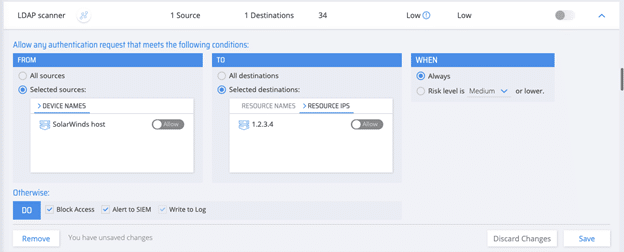
Service Account Type #3: LDAP Scanner
- Activity: Performs LDAP query every 12 hours to track changes in the AD.
- Authentication protocol: LDAP
- Predictability: High
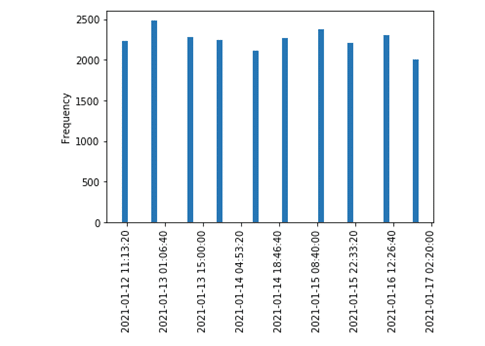
- Behavior sample:
-
Diagram 3:LDAP Scanner service account activity pattern
More detailed activity breakdown of this service account is presented here:
Diagram 4: LDAP Scanner service account detailed activity breakdown
Silverfort Protection against SunBurst Service Accounts Compromise
Silverfort’s Unified Identity Protection Platform uses dedicated access policies to prevent the use of compromised SolarWinds service accounts for lateral movement. The guideline in creating the policies was to capture the standard behavior of the accounts, and block and alert any detected deviation. Such deviations, as slight as they may be, are required from the attacker’s side, and blocking prohibiting them would enable the organization to react to the threat in time and thwart the attack.
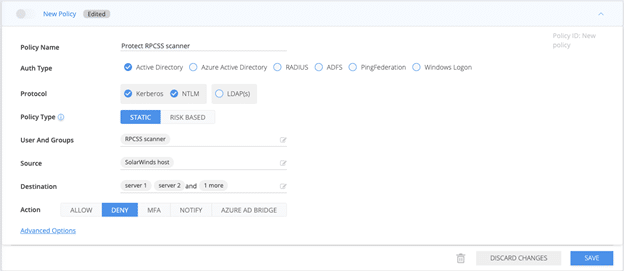
Service Account Type #1: RPCSS scanner
This service account’s standard behavior is to authenticate only with Kerberos. A Silverfort access policy that prevents this account from performing NTLM authentication would prevent it from being abused for lateral movement. You also should make sure the scanner authenticates only with the permitted Kerberos SPNs to the known set of servers. In the policy below these are represented in the server names in the Destination field. Note that while NTLM is blocked altogether, the Kerberos part of the policy is more granular and applies only to the SPN that are not part of the account normal access list (see diagram 7)
-
Diagram 5:Silverfort ‘RPCSS Scanner’ protection policy
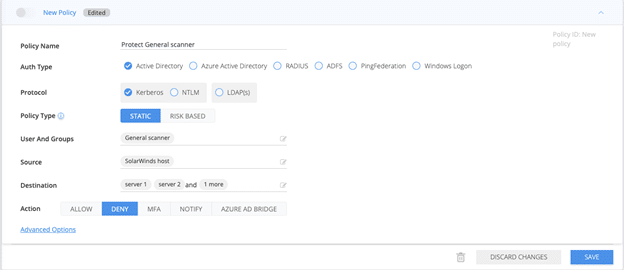
Service Account Type #2: General Scanner
This type of service account features unpredictable behavior, posing a greater protection challenge. However, what is predictable is the machine this account normally accesses. A policy that limits this account’s access to only these machines would eliminate the risk of it being used to access other sensitive resources:
Diagram 6:Silverfort ‘General Scanner’ protection policy
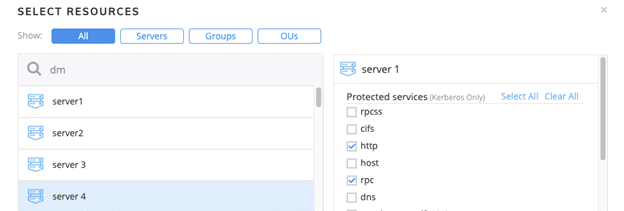
For both of the policies above, choose only the relevant SPN each scanner uses, for example:
-
Diagram 7: Silverfort granular Kerberos services protection for RPCSS and General Access policies
Service Account Type #3: LDAP Scanner
Service accounts of this type have a highly predictable behavior – performing LDAP queries every 12 hours to a distinct set of machines. A policy that limits the target resource of these accounts to this set of machines, and allows these accounts to authenticate with LDAP only, would eliminate the risk of lateral movement that they introduce.
Diagram 8: Silverfort ‘LDAP Scanner’ protection policy
Final Thoughts
In today’s threat landscape, protection against the use of compromised credentials to access sensitive resources is often a missing link in the security stack of most enterprises. The SunBurst attack demonstrates once again that this lack of protection creates a critical risk exposure. Silverfort Unified Identity Protection platform is purpose-built to confront and win against the rising threat that identity attacks introduce to your enterprise.
- Learn more about Silverfort Service Account Protection here.

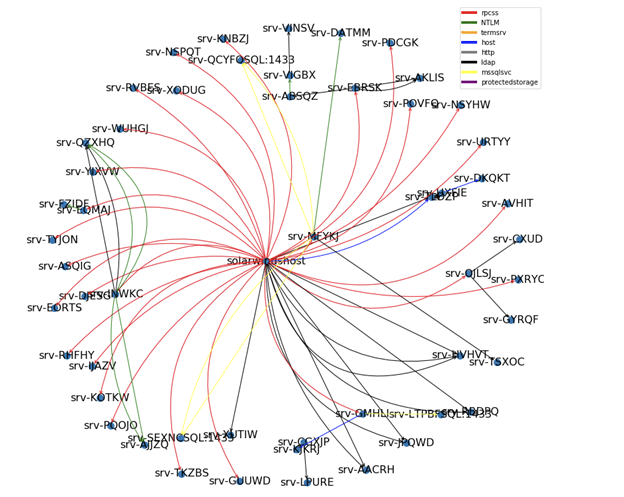 Diagram 1: RPCSS Scanner service account activity pattern
Diagram 1: RPCSS Scanner service account activity pattern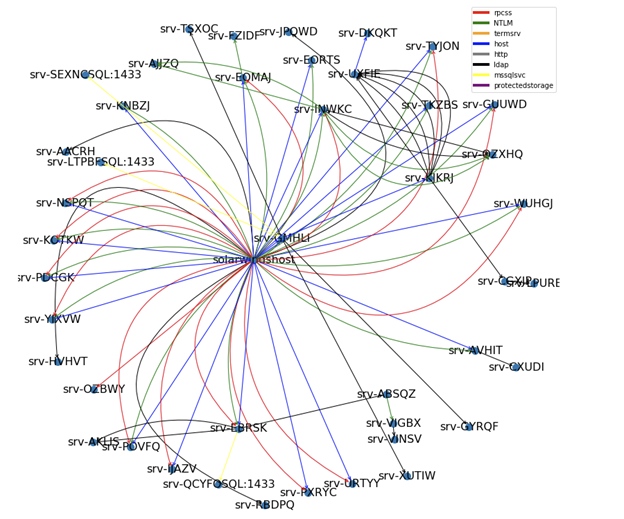
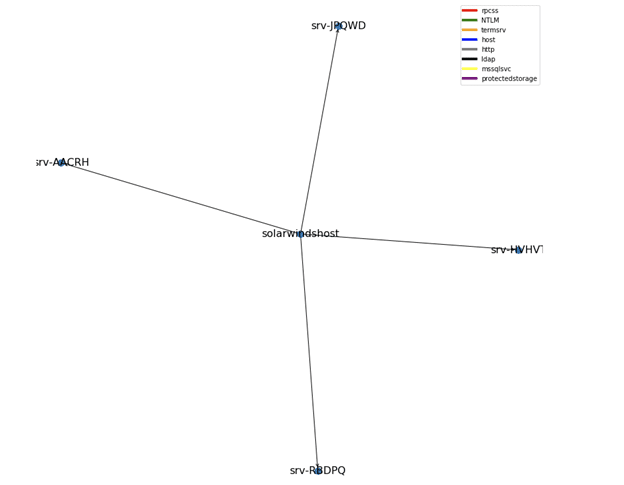 Diagram 3:LDAP Scanner service account activity pattern
Diagram 3:LDAP Scanner service account activity pattern