Modern enterprise IT environments are highly diverse and include many different assets, from legacy IT infrastructure to modern cloud workloads. This drives the need for multiple IAM products, each covering a different environment – on-prem, cloud, secure remote access and others. These IAM solutions work in different silos, and provide different protection capabilities for different assets, creating both a management and security problem. In terms of Identity Protection, the problem is more severe. Cloud-native and modern web apps can be protected by Entra ID (formerly Azure AD) Conditional Access, Risk Based Authentication and MFA that effectively prevent 99% of identity-based attacks. However, on-prem enterprise resources – IT infrastructure, homegrown apps, command line access tools, databases, file shares etc. – aren’t natively supported by both the SSO and the Identity Protection measures of Entra ID (formerly Azure AD). This creates a critical security gap that has not been addressed – until today.
For the first time, Silverfort customers can simplify and optimize their Identity Protection by consolidating it in Entra ID (formerly Azure AD) for all their on-prem and multi-cloud resources. Entra ID (formerly Azure AD) Conditional Access, Risk Based Authentication and Microsoft Authenticator MFA solutions for Active Directory are now fully applicable to core enterprise resources that they never supported before, including IT infrastructure, legacy homegrown apps, command line access tools and many others. By this, Silverfort enables enterprises to apply best-of-breed Identity Protection across all resources and access attempts.
The Three-Step Journey Towards Entra ID (formerly Azure AD) Hybrid IAM Consolidation
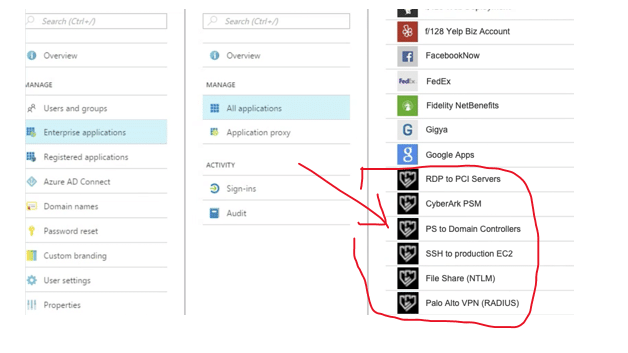
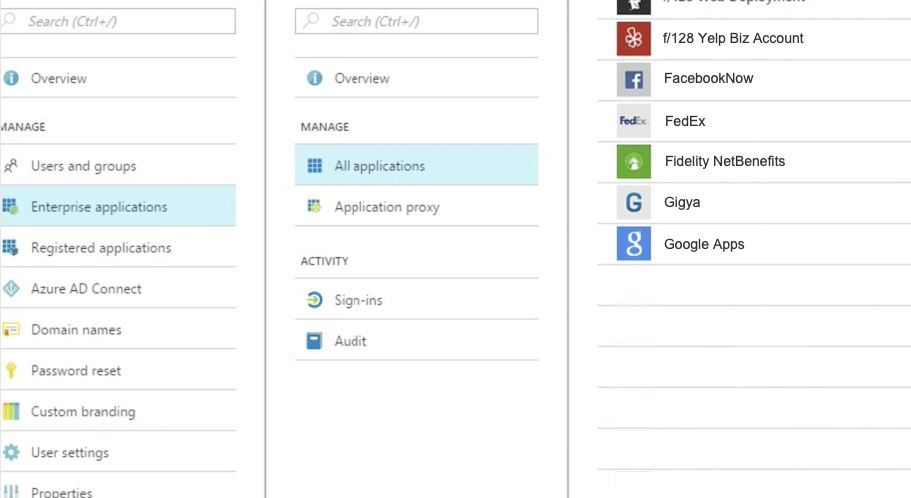
Silverfort seamlessly enables enterprises to bridge their managed apps and resources into Entra ID (formerly Azure AD) as if they were SAML-based applications. Once bridged, these resources appear in Entra ID (formerly Azure AD) Console similar to any app that natively supports Azure AD management and can be subject to Azure AD access policies.
The path to full identity protection consolidation in Entra ID (formerly Azure AD) includes three steps:
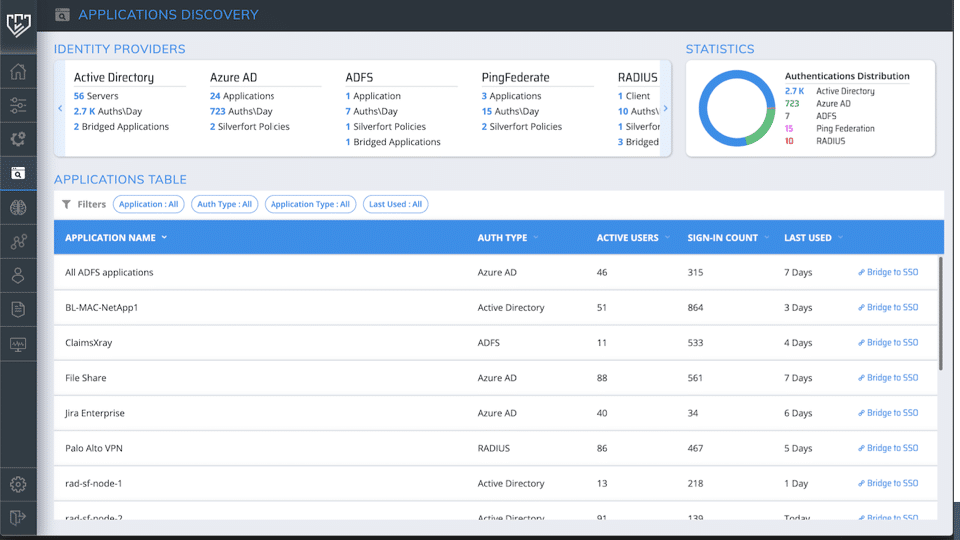
Step #1: Discovery of All Applications and Resources
The initial stage is to discover all the resources and applications in the on-prem and multi-cloud environment. Automating this process is a huge time saver for large enterprises that would need to identify hundreds, if not thousands of applications in their on-prem and cloud environments. Silverfort automatically discovers of all these resources and applications, identifying those that natively support Entra ID (formerly Azure AD) SSO and those that don’t.
Step #2: Migration of Supported Apps into Entra ID (formerly Azure AD)
To accelerate and optimize the migration process for SAML-based apps that are natively supported by Entra ID (formerly Azure AD), Silverfort provides actionable operational insights about application usage and dependencies. These insights help organizations prioritize the migration process based on business and operational needs.
Step #3: Bridging unsupported apps into Entra ID (formerly Azure AD)
For resources and applications that are not natively supported by Entra ID (formerly Azure AD), Silverfort enables organizations to connect them to Entra ID (formerly Azure AD). The bridged apps appear in the Entra ID (formerly Azure AD) console with a Silverfort icon. Now it is possible to apply authentication and access policies on these applications from the Entra ID (formerly Azure AD) console.
What is the User Experience Post Hybrid IAM Consolidation?
After completing the bridging process and the configuration of authentication and access polices, any resource access attempt is monitored and protected.
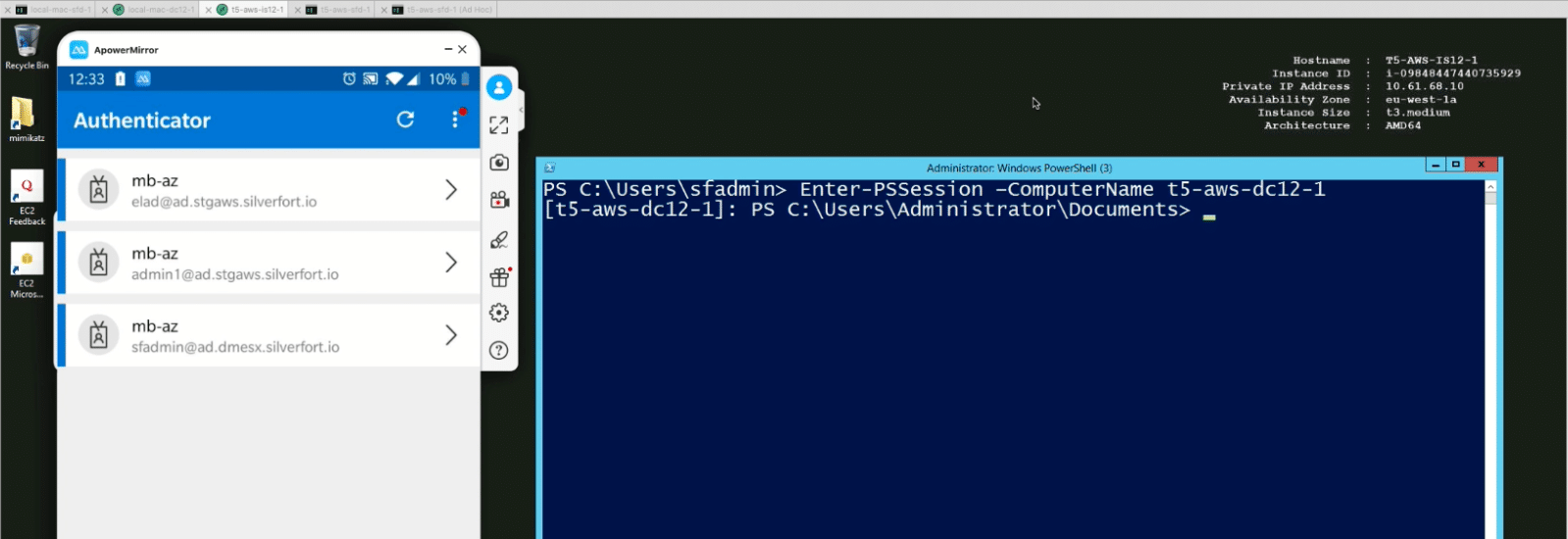
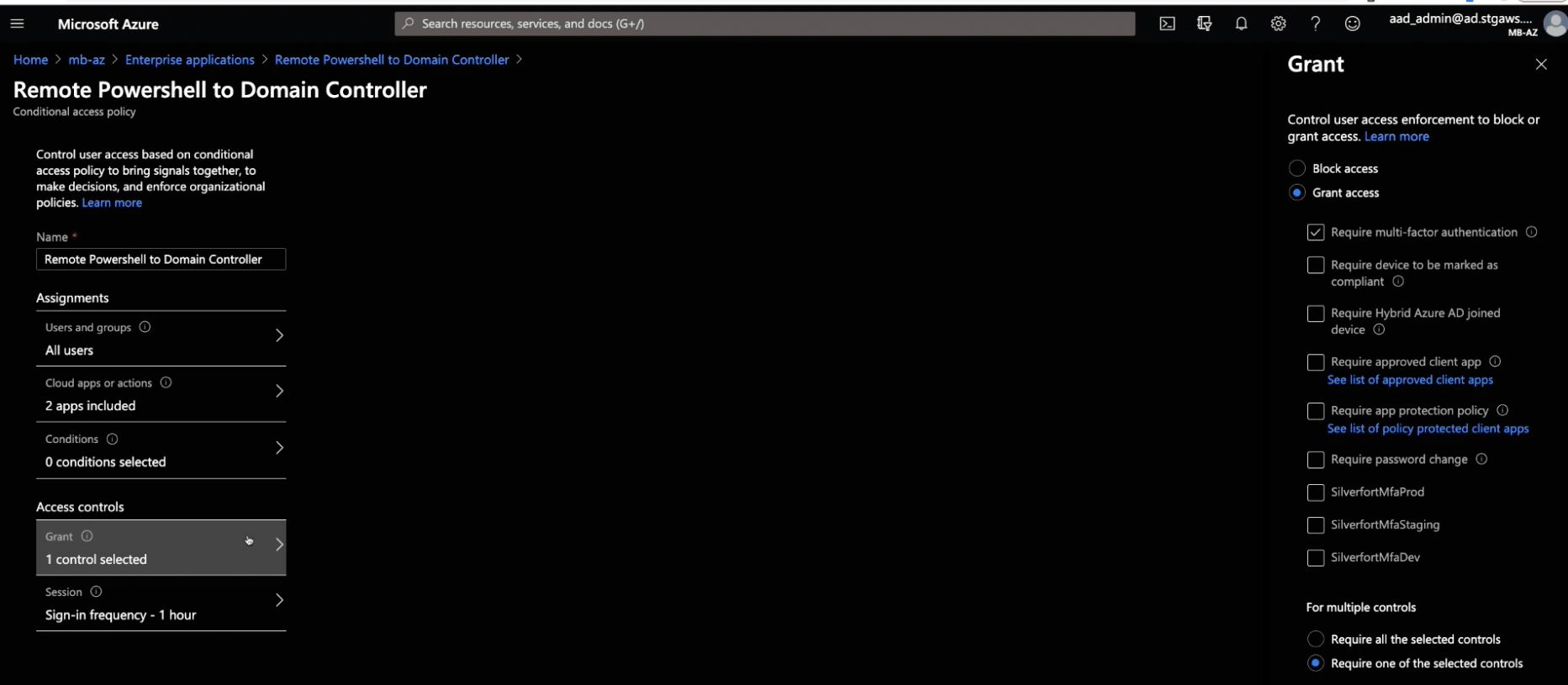
For example, you can now enforce an MFA policy on Remote Powershell.
First you will configure a policy that requires MFA when accessing a remote Domain Controller with Powershell:
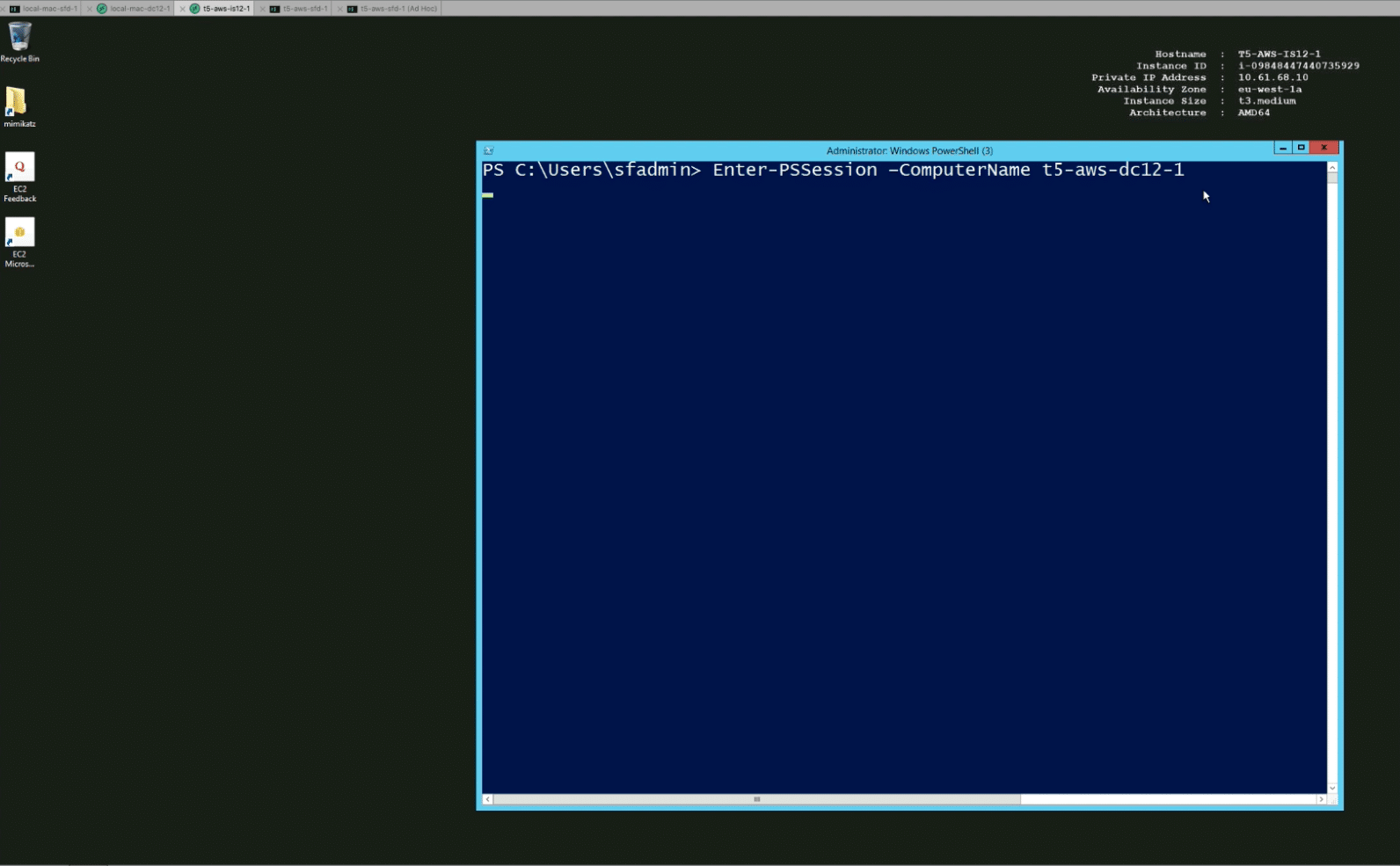
From the user’s perspective, the user will access just as before, by entering a Powershell command, DC name and user credentials:
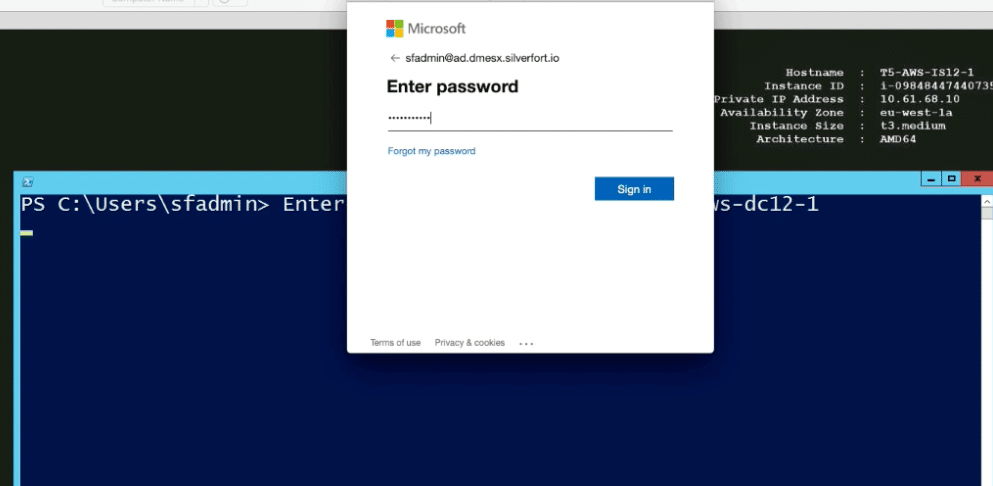
However, with the Entra ID (formerly Azure AD) policy enforced, instead of immediately getting access to the DC, the user is prompted with a Microsoft login pop-up:
And again, based on the policy, the user receives an MFA notification to his or her cell phone.
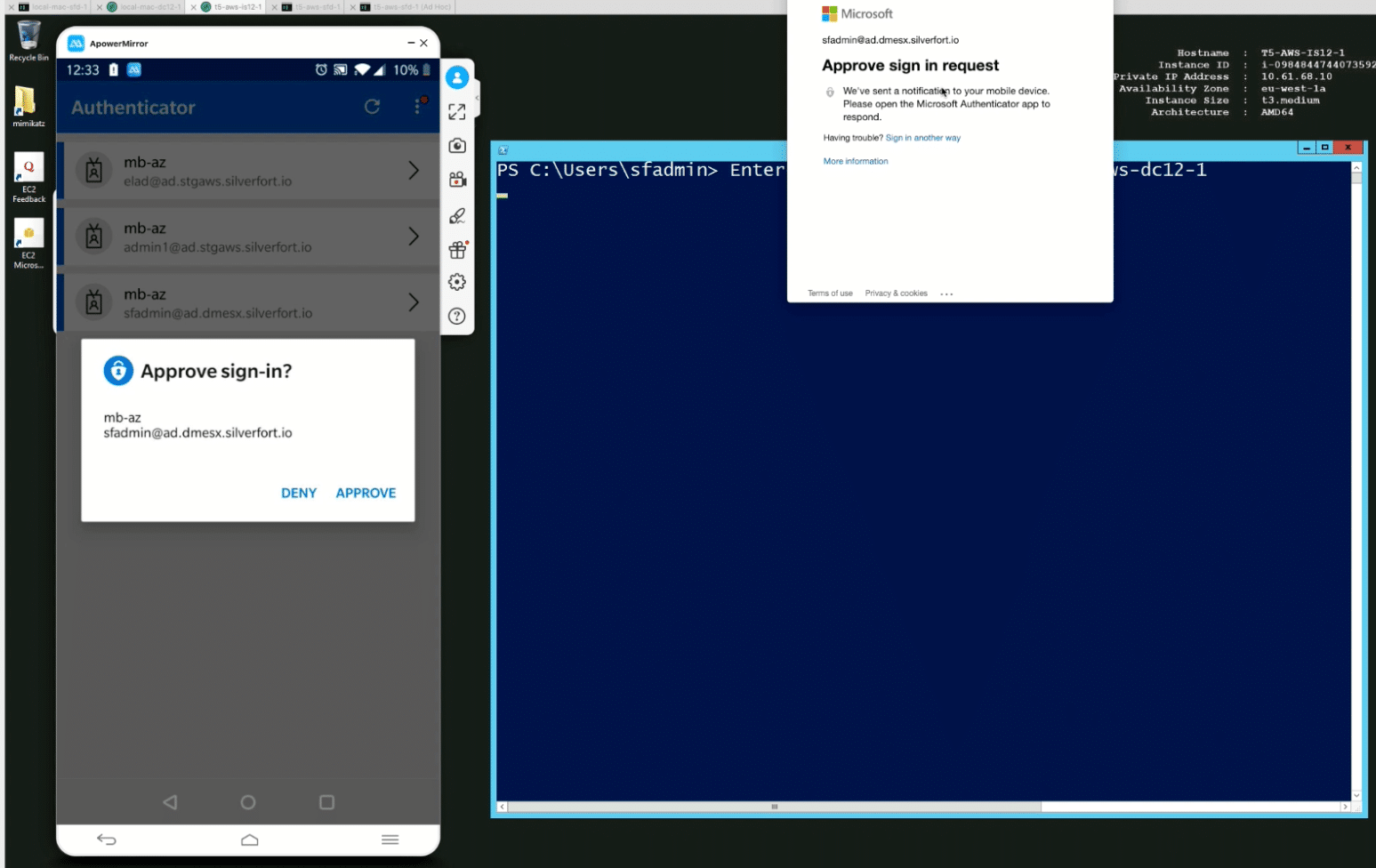
Only after sign-in approval can the user access the Domain Controller.
Want to see more?
Watch this short demo recording to see how this would look like:
Final words
Today, access and authentication to resources that cannot be managed in Entra ID (formerly Azure AD) need to be managed by other IAM solutions – Active Directory, ZTNA solution, VPN, local database etc. This creates both management and security challenges.
Silverfort’s agentless and proxyless technology seamlessly enables enterprises to bridge their managed apps and resources into Entra ID (formerly Azure AD) as if they were SAML-based applications. By consolidating all resources and applications into the Entra ID (formerly Azure AD) Console, authentication and access to any asset can be managed as if it were natively supported by Entra ID (formerly Azure AD) and subject to Entra ID (formerly Azure AD) access policies – as simple as that.
Hybrid IAM Consolidation is about simplifying and optimizing your Identity Protection by consolidating it into a single interface. It is a key component in enhancing the security posture of your enterprise and gaining resilience against attacks that utilize compromised credentials to access your on-prem and cloud resources.