Kerberos delegation was originally designed as a security enhancement- a way to enable applications to authenticate securely on behalf of users when accessing resources. Impersonation as part of authentication isn’t inherently bad; it’s actually an elegant answer to a long-standing problem: how to let applications access resources only when they genuinely need to, while limiting the scope of data they can reach. For example, a front-end service acting on behalf of a user to call a backend API reflects a legitimate and well-controlled use of this mechanism.
As enterprise environments evolved, this approach became a standard for how applications interact with resources. Kerberos delegation introduced a structured and secure way for services to extend user access only where necessary, maintaining authentication integrity across complex systems. But by shifting where trust resides, it also expanded the landscape itself, creating more areas for researchers to explore potential weaknesses and for adversaries to interfere, manipulate, or abuse trust in new ways.
Abuse of Kerberos delegation can therefore be dangerous if it falls into the wrong hands… like what if an attacker finds a way to insert themselves into the delegation path and impersonate the user to access sensitive resources? Or another step further, what if the threat actor figures out a way to impersonate a different, maybe more privileged, user than intended?
This is the story behind Silverfort’s newest research, and what our team is going to present at Black Hat EU in London.
Black Hat Europe 2025 session
You Win Some, You CheckSum: A Kerberos Delegation Vulnerability
December 10, 2:30 PM
As part of responsible disclosure, our research team reported the Kerberos constrained delegation vulnerability to Microsoft, and today they’ve issued an update as part of Patch Tuesday, where it received a CVSS score of 7.5. Using Man-in-the-Middle technique, this flaw allowed us to impersonate arbitrary users and ultimately gain control over the entire domain.
In this blog, we’ll share information on what was uncovered and why it matters. For the technical details, a comprehensive demo, and details on how to mitigate, come to Eliran’s talk at Black Hat EU. If you can’t make it, you can watch the video on-demand after December 10th—we’ll add the link to this blog.
Why CVE-2025-60704 matters
Kerberos is a multi-layered protocol and can be complex to understand at first; it involves multiple message exchanges, encrypted tickets, and session keys. Delegation adds another layer to the complexity, with several models available: unconstrained, constrained, and resource-based (RBCD). This helps extend trust boundaries across services. One last layer adding to the complexity is that Kerberos delegation can also interplay with other authentication types. The main purpose of Kerberos is for an application to authenticate a user.
Delegation will always be an important consideration in cybersecurity for one main reason: the ability to impersonate a user’s identity is an attractive target for attackers. It doesn’t matter if your organization is cloud-native or if you have mission-critical apps exclusively built on legacy architectures. The concept remains the same: an application acting on behalf of a user’s identity can be powerful if abused.
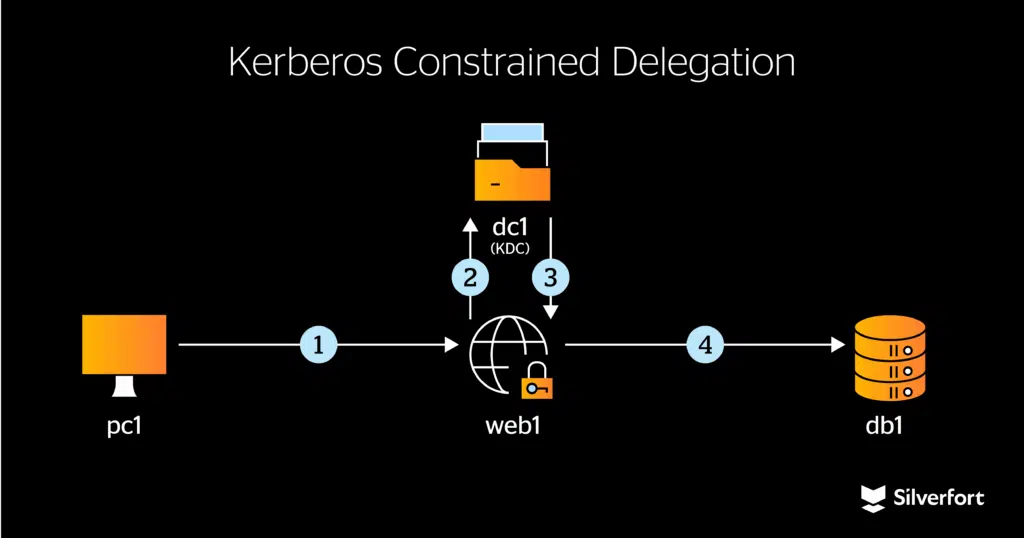
As our team began researching, we looked for ways to bypass the security mechanisms of the Kerberos delegation protocol. That’s when something interesting emerged: in Kerberos Constrained Delegation (KCD), the protocol had some mechanisms that allowed us to not only impersonate a user we gained access to, but also escalate privileges and more. We would elaborate—but that’s saved for the talk.
The impact of CVE-2025-60704 if exploited
We often think of identity threats as being related to gaining access to the targeted identity (whether human or non-human like a service account) and then seeing what’s possible using that identity’s permissions. Rarely do we think in terms of gaining access, then being able to switch who we become to someone else entirely.
The impact of this is clear: any organization using Active Directory, with the Kerberos delegation capability turned on, is impacted. This means thousands of companies around the world are affected by this vulnerability. Because Kerberos delegation is a feature within Active Directory, an attacker requires initial access to an environment with compromised credentials. Once the vulnerability is exploited, the attackers could escalate privileges and move laterally to other machines in an organization. Worse, they could also gain the ability to impersonate anyone in the company, unlocking untold access or even becoming a domain admin.
Exploiting CVE-2025-60704 would be part of their long game, stealing IP or personal data, impersonation, ransomware, and more.
Mitigating CVE-2025-60704
Kerberos has been trusted for decades as the backbone of enterprise authentication. However, even the most well-architected security protocols can be quietly undermined and exploited. So, what should security teams do?
For any company using Active Directory, we recommend they patch this vulnerability as soon as possible. If patching isn’t an option for the time being, set up an alert in your ITDR solution to monitor all Kerberos Constrained Delegation. We’ll offer more detailed mitigations at Black Hat.
Meet me at Black Hat EU in London
If you’re attending Black Hat in London, we’ll take you through it all:
- Where the research started, and how our research team stumbled upon the CVE.
- How a mechanism designed to make your infrastructure more secure expands your attack surface.
- Protocol behavior, trust assumptions, and some light reverse engineering of Windows internals that helped us trace the flaw down to its root.
- Mitigation strategies and how to better protect environments relying on Kerberos delegation.
We’re excited for Black Hat in December and the chance to deep dive into explaining the ins and outs of Kerberos delegation, and why it signals the need for a renewed focus on impersonation’s impact on identity security. For those who can’t make it to BlackHat Europe, we’ll add an on-demand video of the talk to this blog after December 10th.
Interested in staying in touch and keeping up with our research? Connect with the presenter on LinkedIn to follow for more.
More information about Eliran Partush, Silverfort Security Researcher
Eliran is a security researcher and IT specialist on the Silverfort Research Team with a specific interest in network and authentication protocols, especially Kerberos. He loves challenges like CTFs and diving into deep protocol study. He has an extensive background as a network and system engineer at Cisco for 10+ years and has always enjoyed taking systems apart and putting them back together again.

