The Pay2Key attacks have targeted leading enterprises in the past couple of months with various ransomware, extortion and data theft attacks. These attacks did not feature any noticeable innovation on the offensive side. However, they do offer insight into the fact that threat actors are increasingly targeting modern enterprises with compromised credentials – not only for the Initial Access stage, but also for lateral movement. The important role that compromised credentials play in today’s attacks poses a critical challenge to security teams. This article analyzes two sample Pay2Key attacks, presents three actionable insights for enterprise security decision makers, and explains how Silverfort’s Unified Identity Protection platform can address this new reality, in which user identities have become a primary attack surface.
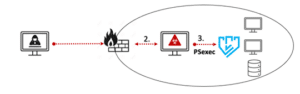
Pay2Key Attack – Example #1: RDP and Automated Ransomware Propagation
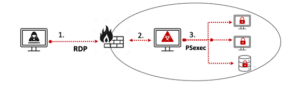
This attack was disclosed on November 8th 2020, by Check Point . The attackers attempted to execute a mass ransomware campaign. To achieve that, they altered the traditional weaponized email vector, often used for gaining initial access, to a more efficient technique – remote connection utilizing compromised RDP credentials. Once establishing a connection with a machine within the targeted environment, they configured this machine as a pivotproxy to deliver the ransomware payload to other machines in the network. The actual propagation was done by using the PSexec automation capability that enabled the ransomware to spread across the entire network within a single hour.
-
- Initial Access via compromised RDP credentials
- Persistence via configuration of compromised machine as C2C server
- Lateral Movement via Psexec
Diagram 1: Pay2Key Attack Example #1
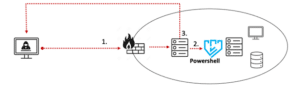
Pay2Key Attack Example #2: Supply Chain RDP and Manual Lateral Movement
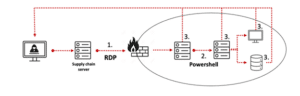
A different attack took place in the beginning of December 2020, and featured similar tactic for gaining Initial Access: like in the previous example, compromised RDP credentials were used to access a server of a 3rd party contractor that could connect to the target environment. From there, the attack followed a standard Lateral Movement process, with the attackers compromising additional credentials as they advanced, and using them to log in to other production servers with Powershell. Eventually, the attackers managed to exfiltrate significant volumes of sensitive data and used it to extort their victim while threatening to leaking the data to the public.
- Initial Access via supply chain server with compromised RDP credentials
- Lateral Movement via Powershell scripts
- Persistence and Data Exfiltration via backdoor on each compromised server
Diagram 2: Pay2Key Attack Example #2
Security Insight 1 – Compromised Credentials are now Extensively Used for the Initial Access Stage
By default, the immediate association of the ‘Initial Access’ stage of the attack, is the use of malware and exploits. While in many cases this is still true, it’s important to note that Compromised Credentials are taking an increasingly bigger role in this process. Verizon’s 2020 DBIR states that using compromised credentials has topped exploits and backdoor malware as the hackers’ preferred infection vector:
‘…Malware has been on a consistent and steady decline as a percentage of breaches over the last five years. Why is this? Has malware just gone out of fashion like poofy hair and common courtesy? No, we think that other attack types such as hacking and social breaches benefit from the theft of credentials…’
Security Insight 2 – Lateral Movement is a Compromised Credentials Problem
Malware authors put in hard work in their strive to make their attack vector appear as legitimate behavior to avoid detection. Unfortunately for the defending side, that isn’t needed for the Lateral Movement stage. Once an attacker has successfully compromised user account credentials, the malicious login looks 100% legitimate, giving them direct access to additional machines. In terms of a ransomware protection strategy, it means that the key to protect against Lateral Movement should be found in the field of secure authentication – i.e., MFA and Conditional Access policies – tools that have been proven effective against the use of compromised credentials. However, these tools are not the common practice of enterprises’ security teams today.
Security Insight 3 – Compromised Credentials Are The New Identity Attack Surface
The new enterprise IT environment features hybrid on-prem and cloud networks, and needs to support massive remote access to enterprise resources (a growing need driven by Covid19). User account identities play a key role in accessing resources in this environment. This hasn’t gone unnoticed by attackers who are relentlessly pursuing your user account credentials – regardless if these are credentials for an on-prem file server or a- SaaS application of remote access VPN. It is time to acknowledge that Identities are becoming a critical attack surface and that Identity Protection is needed more than ever.
Silverfort Unified Identity Protection Platform
Silverfort is the first Unified Identity Protection that consolidates security controls across corporate networks and cloud environments to block identity-based attacks. Using an innovative agentless and proxyless technology Silverfort applies continuous monitoring, risk analysis and adaptive access policy on every authentication of every user account to any resource, on-prem or in the cloud In the context of the Pay2Key attacks, they targeted the RDP and windows admin tools such as PSexec and Powershell. If it were possible to enforce MFA on Powershell and these other access methods, the attacks would have failed completely. Well guess what? – it’s now possible.
Silverfort vs Pay2Key Attacks
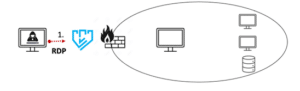
To recap, the ‘Initial Access’ stage of this attack started with using compromised RDP credentials. Silverfort enforces MFA for RDP connections to ensure legitimate access, so, because the attackers can’t authenticate with the 2nd factor, it would have blocked the attack’s Initial Access stage and the attackers would have never penetrated the perimeter.
- Initial Access via compromised RDP credentials is blocked by Silverfor MFA policy on RDP connections
Diagram 3: Pay2Key Attack Example #1 Initial Access Protection
It’s always important to apply additional defenses, in case the attackers are persistent and resourceful enough to succeed with another Initial Access technique.
In that case, Silverfort would block the next stage of Lateral Movement, by enforcing MFA on the PSexec remote authentications (on which the automated ransomware propagation relied):
- Initial Access established
- Persistence via configuration of compromised machine as C2C server
- Lateral Movement via Psexec is blocked by Silverfort MFA policy on PSexec
Diagram 4: Pay2Key Attack Example #1 Lateral Movement Protection
In a similar manner, Silverfort would have prevented both the Initial Access and Lateral Movement stages of the Pay2Key attack example #2. The RDP part is identical, so let’s move to the part in which we consider that the attacker did manage somehow to establish a footprint on one machine within the environment. There are some aspects in the Lateral Movement part that are worth focusing on:
- Initial Access established
- Lateral Movement via Powershell scripts is blocked by Silverfort MFA policy on Powershell Remoting
- Persistence and Data Exfiltration via backdoor – only on the initially accessed server
Diagram 5: Pay2Key Attack Example #2 Lateral Movement Protection
In this case Silverfort prevents the Lateral Movement by applying MFA on remote Powershell connections, ensuring only legitimate valid users are executing it and limiting the attack to the single machine that was initially compromised.
Final Thoughts
As we’ve stated in the beginning of this article, the Pay2Key attacks are not unique in any manner. But it is exactly the lack of uniqueness that should raise a flag to security teams worldwide – the common attacks, rather than the unique ones are the ones that are likely to target your environment and it is imperative to protect against them. In today’s enterprise Identities are the keys to the kingdom’s crown jewels. Silverfort Unified Identity Protection platform is the first to provides your users’ identities the protection they really need.
Learn more on Silverfort here