Microsoft’s recent research spotlights a dangerous post-exploitation technique called Golden dMSA. This new attack method abuses SYSTEM-level access on domain controllers to execute persistent payloads, including ransomware that targets the core of Active Directory. By hijacking delegated Managed Service Accounts (dMSAs), attackers can gain access without needing to compromise traditional credentials.
Originally introduced in Windows Server 2025, delegated Managed Service Accounts (dMSAs) are a major advancement in service account security. While static password-based accounts remain susceptible to Kerberoasting attacks, dMSAs shift the authentication model by binding access directly to verified machines in Active Directory (AD).
This machine-centric approach eliminates credential theft by tying access to device identity rather than user-managed passwords, ensuring that only explicitly authorized machines can leverage the account. However, when abused in post-exploitation scenarios, dMSAs can be used by attackers to execute malicious code from within trusted high-privilege infrastructures.
In this blog, we will break down how the Golden dMSA attack flow works, why it poses multiple risks, and how organizations can secure machine identities before attackers do.
What is Golden dMSA?
Golden dMSA is a post-exploitation technique that allows attackers to gain long-term access in Active Directory (AD) environments by generating valid passwords for delegated Managed Service Accounts (dMSAs) and group Managed Service Accounts (gMSAs).
This method becomes viable after the attacker has already gained privileged access, such as Domain Admin or SYSTEM-level permissions on a domain controller. From there, they can take advantage of a flaw in the way these service account passwords are generated. The process includes predictable, time-based elements with limited variability, making it easy to reverse-engineer and reproduce the correct passwords.
Attackers can then generate credentials offline and impersonate critical service accounts across the domain, bypassing normal security controls and password rotation mechanisms.
How a Golden dMSA attack unfolds
A Golden dMSA attack typically begins after an attacker gains a foothold in the environment and escalates privileges. From there, the method enables covert persistence and extensive lateral movement across Active Directory.
This is how the typical golden dMSA attack occurs:
1. Initial access and privilege escalation
The attacker compromises a system within the domain and escalates to Domain Admin or SYSTEM-level access on a domain controller, often through phishing, credential theft, or exploiting misconfigurations.
2. Extraction of the KDS root key
With privileged access, the attacker extracts the Key Distribution Services (KDS) root key, a critical cryptographic secret used by Active Directory to generate passwords for managed service accounts.
3. Service account enumeration
The attacker identifies delegated Managed Service Accounts (dMSAs), and group Managed Service Accounts (gMSAs) across the forest. This typically involves querying for account names and associated identifiers using LDAP or other directory tools.
4. Offline password generation
Due to a weakness in the password generation algorithm, the attacker can brute-force the values and generate valid passwords using tools like Golden dMSA, without triggering alerts.
5. Post-exploit impact: SYSTEM-level ransomware deployment
With credentials for service accounts in hand, the attacker can reenter the domain controller and operate with SYSTEM-level privileges. From here, they can:
- Tamper with core processes like LSASS (e.g., for further credential dumping or injection).
- Deploy ransomware from a central, high-trust machine with domain-wide access.
- Move laterally to other systems and infrastructure.
This stage of the attack is crucial because ransomware executed from a domain controller typically includes broad domain trust and can spread rapidly. Most EDR solutions have limited visibility into SYSTEM-level operations, especially on domain controllers. To make matters worse, service account activity often goes undetected by standard security solutions.
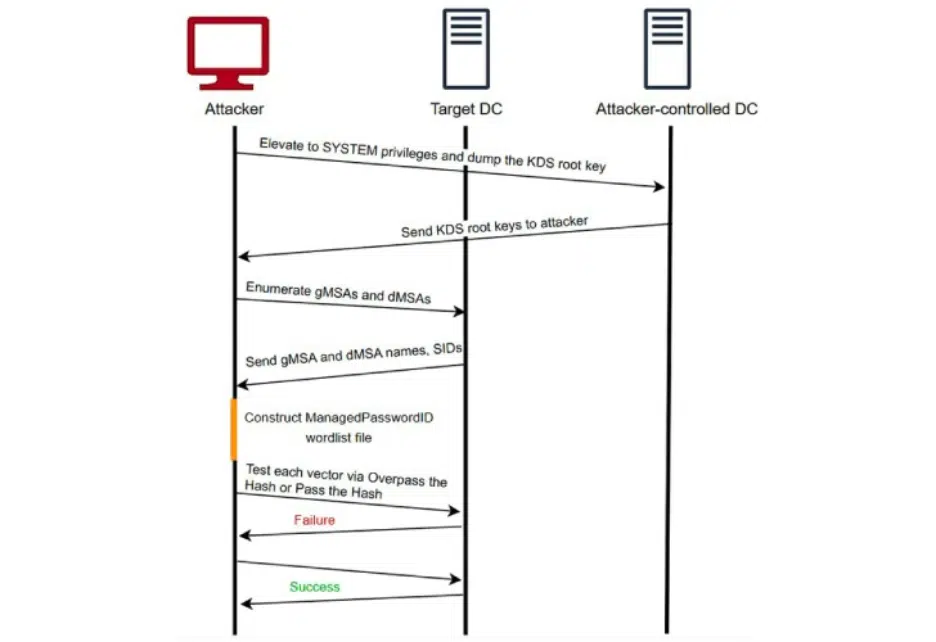
How Golden dMSA bypasses traditional security solutions
Golden dMSA is particularly dangerous not because it breaks in, but because of what it can do after gaining access. Due to it being a post-exploitation technique, by the time it is exploited by the targeted domain controller, most security solutions are already out of scope.
Detection becomes especially difficult because attackers operate using legitimate credentials and elevated privileges. Once the attacker gains SYSTEM-level access, common security tools like EDR and antivirus struggle to provide visibility or enforce controls in those privileged contexts.
Lateral movement also comes into play as it blends in with normal admin activity, making it hard to differentiate malicious actions from routine domain operations. Since no malware or exploits are necessarily involved at this stage, signature-based or behavior-based detection systems may not trigger alerts at all.
In short, once attackers are inside the perimeter and leveraging Golden dMSA, the usual security layers offer little resistance, making early detection and privilege boundary hardening critical.
Silverfort’s Golden dMSA prevention approach
Even in post-exploitation scenarios like Golden dMSA where traditional security tools often fall short, Silverfort protects direct and indirect access to domain controllers with MFA and strict real-time access policy enforcements that actively stop attackers from progressing inside the environment.
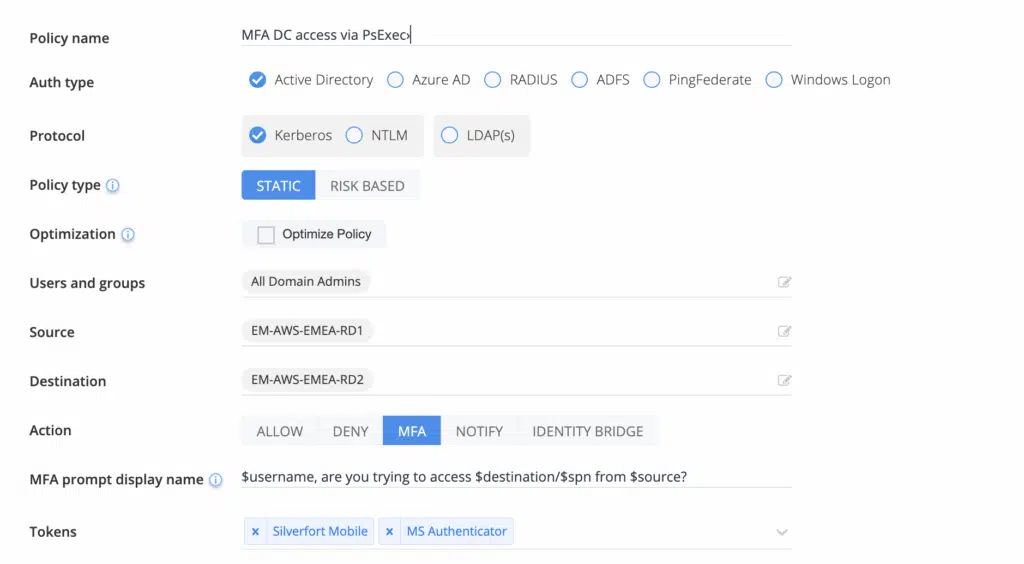
Enforcing MFA for admin access to domain controllers
Silverfort enables organizations to enforce MFA on any access attempt to domain controllers, including:
- Remote Desktop Protocol (RDP) sessions
- PsExec executions
- SMB file share access
By enforcing MFA at traditionally unprotected access points such as RDP and PsExec, Silverfort has the capability to require users to verify their identity with MFA, which can help prevent an attacker from moving laterally across an environment. This disrupts the attacker’s ability to leverage Golden dMSA-generated credentials for privileged access, effectively halting progression even after initial compromise.
MFA protection on direct Windows logins to domain controllers
Silverfort provides the ability to enforce MFA on all interactive logins to domain controllers, including:
- Local console logins
- Remote Desktop Protocol (RDP) sessions
- Any direct login using valid domain credentials
By enforcing MFA at these critical access points, Silverfort prevents unauthorized access to domain controllers even if attackers possess valid credentials. This capability is especially important in scenarios involving credential-based attacks like Golden Ticket, Pass-the-Hash, or lateral movement. Requiring MFA at the moment of login disrupts the attack chain early, turning domain controllers from high-risk targets into secure endpoints.

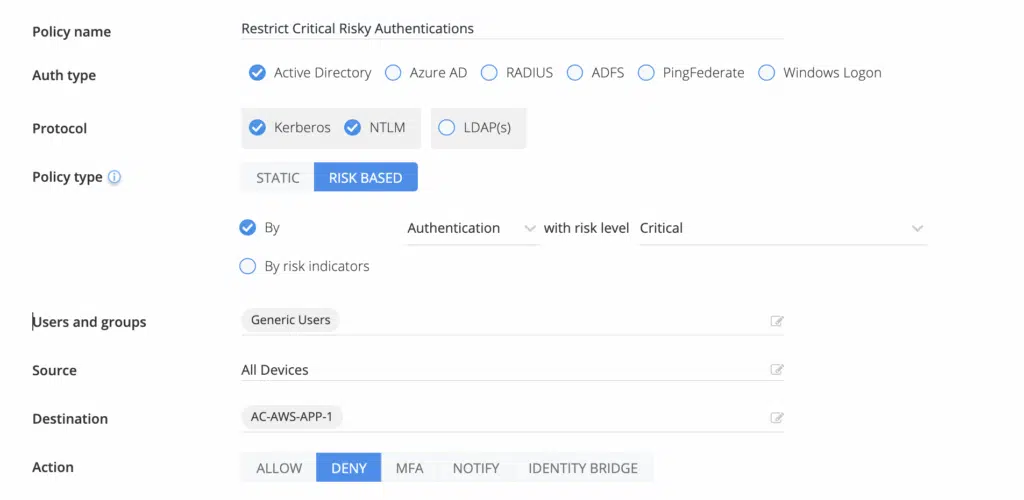
Real-time access enforcement
Silverfort performs real-time analysis of authentication traffic across the environment, correlating signals from user identity, device posture, access protocol, and behavioral patterns. This enables precise enforcement decisions at the identity layer, allowing you to:
- Block unauthorized or misused access paths to critical systems like domain controllers, even if valid credentials are used.
- Detects tool-based anomalies such as unexpected use of PsExec, PowerShell, or other lateral movement utilities by analyzing deviations from known admin behavior baselines.
- Disrupt lateral movement early by enforcing access policies that adapt to risk context, preventing escalation before attackers reach sensitive targets.
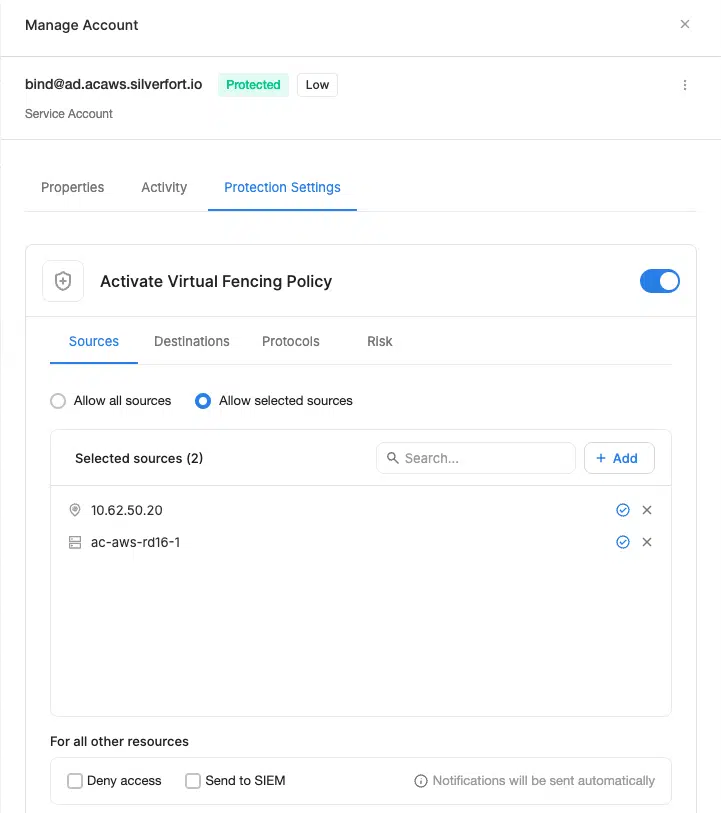
Virtual fencing to stop lateral movement
Silverfort can apply virtual fencing capabilities not just for users, but also for non-human identities. These policies establish explicit access boundaries, restricting movement based on the identity type (user or service account), its role, and contextual factors such as source system, access method, and protocol.
Unlike traditional network segmentation, which lacks visibility into identity context, Silverfort enforces policy at the authentication layer. This enables real-time enforcement that blocks credential-based movement, even when attackers are using legitimate credentials or SYSTEM-level privileges.
Silverfort’s approach ensures:
- Human users are only able to access the systems and workloads explicitly assigned to them, eliminating blanket access between domain-joined machines.
- Service accounts including dMSAs, gMSAs, and other non-human identities, are governed by virtual fencing protection policies that define which machines, services, or apps they are allowed to interact with. Any unauthorized service-to-service access attempts are denied outright.
- Lateral movement, whether through interactive tools (RDP, PsExec) or automated processes (scheduled tasks, service start-ups), is evaluated in real time and blocked unless it aligns with predefined policy.
By enforcing these controls in identity and authentication flows, Silverfort eliminates blind spots where service accounts and privileged users traditionally move unchecked, reducing lateral movement risk even in fully-compromised privileged environments.
Stopping lateral movement starts at the authentication layer
Golden dMSA is a reminder that no perimeter is inherently secure and that attackers will compromise when provided with the opportunity. The real challenge is what happens next, especially when they reach domain controllers with SYSTEM-level access.
That is why real-time identity enforcement needs to be at the forefront to ensure protection. To defend against post-exploit techniques, organizations need to apply security controls at the authentication layer, not just the endpoint or network.
Silverfort makes this possible. By enforcing least privilege, monitoring authentication in real time, and controlling both user and service account access, Silverfort prevents lateral movement and service abuse—even when credentials are legitimate.
Learn how to defend against Golden dMSA and other identity-based attacks by scheduling a call with one of our identity security experts.

