Ransomware has gradually evolved since it was first introduced in 2005. In 2013, ransomware attacks began to target the enterprise workforce rather than personal users, with more than 100k new variants in that year alone – a number that has only risen since.
In 2017, for the first time, WannaCry and NoPetya attacks paired ransomware with automated propagation capabilities, shutting down operations of enterprises worldwide and causing approximately $15B in damages.
Ransomware attacks can be divided into three stages: delivery of the ransomware payload to the target machine, execution of the payload to encrypt or delete data files on the machine, and propagation of the ransomware across multiple machines within the environment, to encrypt their data files as well.
Traditional ransomware attacks operated in one-to-one mode. A compromise of a single machine resulted in data encryption on that machine only. Automated propagation enabled the attacker to exponentially increase their ROI: a compromise of a single machine is now the stepping-stone to compromising all servers and workstations in the environment.
Translating ransomware breakdown to actual damage
It is easily seen that the price of failure rises with each attack stage. The damage caused by a ransomware attack that succeeds in the Delivery and Execution stages is limited to a single or a few infected machines.
Propagation is the X-factor that extends the ransomware damage across wide parts of the targeted organization’s infrastructure. Today, the typical enterprise ransomware protection stack includes security measures against the Delivery and Execution stages. However, most organizations do not have a solution in place for the propagation stage.
This creates a significant security gap – if a ransomware attack bypasses the Delivery and Execution security controls it can propagate uninterrupted across the environment.
Why is propagation a blind spot, and how can it be solved?
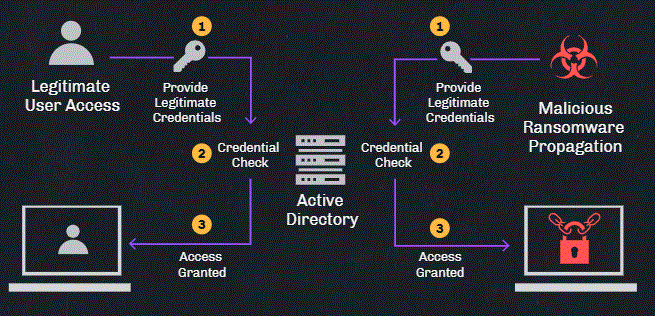
In an enterprise environment, connecting from one machine to another involves the first machine providing Active Directory with a username and password. If these match, Active Directory approves the connection.
Ransomware propagation is carried out by connecting to multiple machines with compromised admin credentials. Since these credentials are valid, Active Directory treats it as a legitimate authentication and grants the ransomware access.
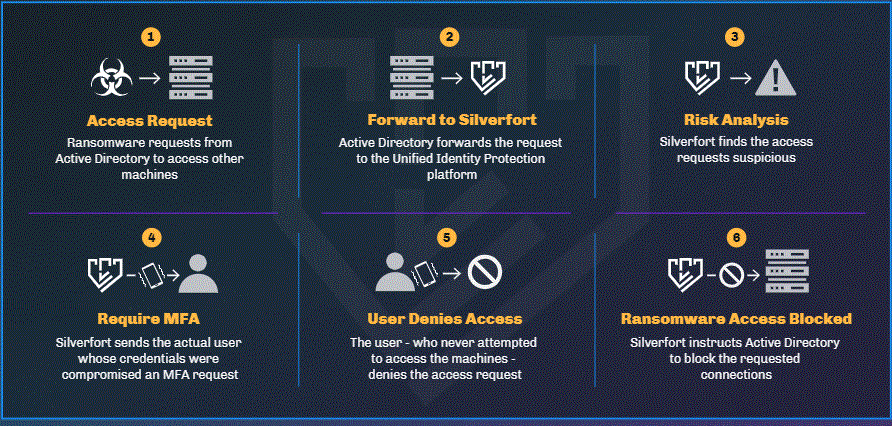
The Silverfort Unified Identity Protection platform integrates with all Identity Providers (IDP) in the environment to perform continuous monitoring, risk analysis, and adaptive access policies on all access attempts, made by all users, to all on-prem and cloud resources. In this way, access to resources is never granted based on credentials alone. Rather, Silverfort’s risk analysis determines whether or not to allow access, augment the authentication with MFA verification, or block the access attempt altogether.
The Silverfort Unified Identity Protection Platform
Silverfort pioneered the first Unified Identity Protection Platform to protect enterprises against identity-based attacks that exploit compromised credentials to access enterprise resources. Using innovative agentless and proxyless technology, Silverfort natively integrates with all existing IAM solutions, to extend secure access controls such as Risk-Based Authentication and MFA across all on-prem and cloud resources.
This includes assets that could never have been protected in this way before, such as homegrown/legacy applications, IT infrastructure, file systems, command-line tools, machine-to-machine access, and more. Silverfort continuously monitors all access attempts by users and service accounts, and analyzes risks in real-time using an AI-based engine to enforce adaptive access policies.
Learn more about how the Silverfort Unified Identity Protection Platform prevents ransomware propagation here.