Ping Identity and Silverfort have joined forces to introduce a new approach of Identity-centric Zero Trust security that enables Zero Trust access, offering both higher granularity in terms of risk analysis as well as relatively rapid and seamless implementation that does not require any IT infrastructure changes. This new offering accelerates your Zero Trust journey with policies that can be configured within minutes, enabling Ping Identity and Silverfort customers to materially increase the defenses of their hybrid cloud environments and reduce the risks of a cyberattack.
What is Identity-Centric Zero Trust?
Today’s enterprise environment includes multiple resources including physical servers, SaaS apps, cloud workloads, file shares, on-prem applications, etc. Identity-centric Zero Trust ensures the following criteria are met:
- All users are by default not trusted until they are properly authenticated.
- Once authenticated, user accounts are only authorized for the resource they requested access for.
- Authentication and authorization is continuous. Their risk is constantly being assessed in the background and their risk score/profile is being adjusted accordingly.
For example, let’s assume that a remote user has connected remotely by authenticating to the enterprise VPN. Once inside the internal environment this user now attempts to access a file server. Identity-centric Zero Trust would evaluate this new access request and determine if it is allowed and would never assume that this user account is trusted based solely on their VPN access.
Better Together: Ping Identity & Silverfort
Ping Identity delivers intelligent identity solutions for the enterprise. We enable companies to achieve Identity-centric Zero Trust security and more personalized, streamlined user experiences. The PingOne Cloud Platform provides customers, workforce, and partners with access to cloud, mobile, SaaS and on-premises applications across the hybrid enterprise. Over 60% of the Fortune 100 choose us for our identity expertise, open standards, and partnerships with companies including Microsoft and Amazon. We provide flexible identity solutions that accelerate digital business initiatives, delight customers, and secure the enterprise through multi-factor authentication, single sign-on, access management, intelligent API security, directory, and data governance capabilities. For more information, visit www.pingidentity.com.
The Silverfort Unified Identity Protection platform utilizes its agentless technology for continuous monitoring, risk analysis and secure access policies on all other resources in the enterprise environment, including core assets that could never have been protected by MFA before, such as legacy homegrown applications, on-prem servers, command line access interfaces and more.
Together, Ping Identity and Silverfort provide real-time visibility and control over all authentications and access requests across every type of resource in enterprise environments. We provide the foundations for Identity-centric Zero Trust at scale and a major prerequisite for Zero Trust maturity – complete coverage of every user access to every resource.
Details of the Integration
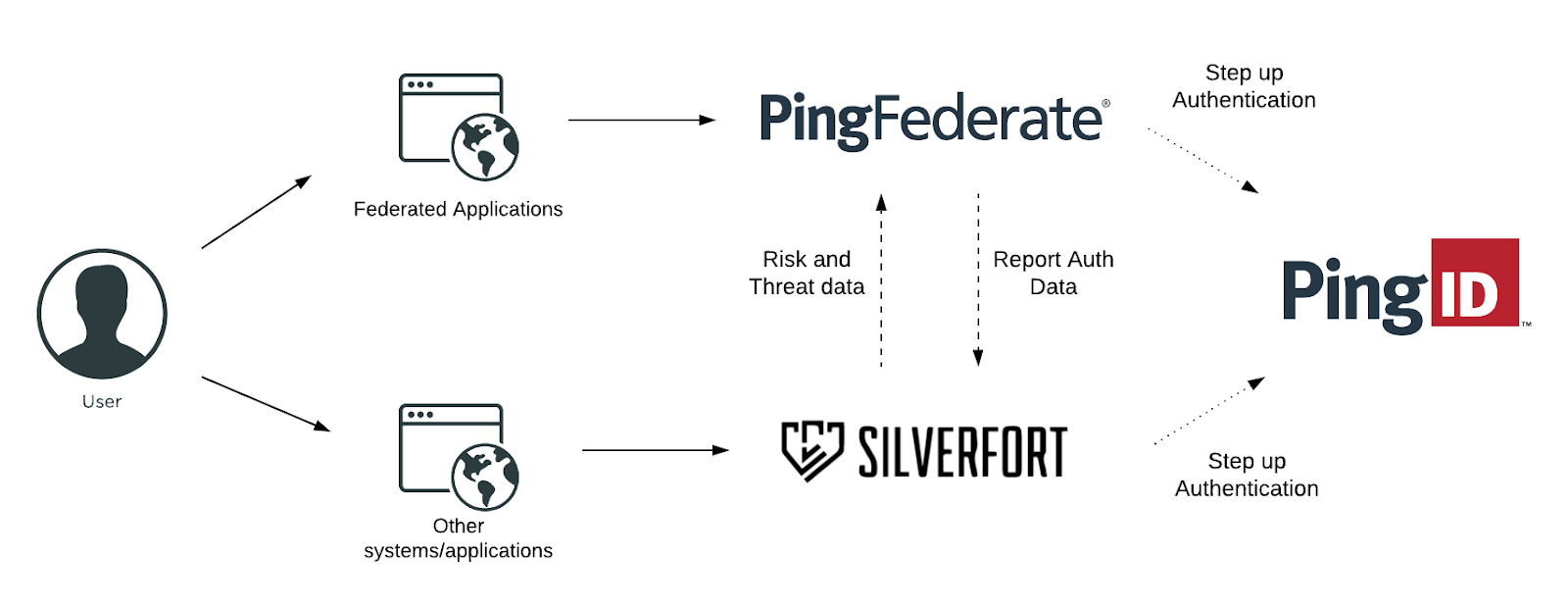
Ping Identity streamlines all access requests to federated applications to Silverfort. This feed provides Silverfort’s risk engine with the full data of every user’s authentication and access attempt activity both on-prem and in the cloud. This data enables the risk engine to perform high-precision risk analysis to reveal the true context of each access attempt and determine whether to grant access, require MFA or deny it altogether.
This is the complete Identity-centric Zero Trust flow delivered by Ping Identity and Silverfort:
- Continuous Monitoring: monitors all access requests, made by all user accounts to any type of on-prem or cloud resource, and creates a comprehensive audit trail.
- Risk Analysis: covers all individual access attempts, assesses the probability of a compromised attempt, based on analysis of the user behavior, the audit trail, and various contextual parameters.
- Enforcement of Real Time Access Policy: based on the calculated risk score and predefined policy access can either be granted, denied, or require step up authentication via MFA.
The Business Value of the Integration
Together, Ping Identity and Silverfort’s integration delivers the following benefits to the business:
- Simple and Easy Deployment: no infrastructure changes and related downtime are required. All the Zero Trust access policies are delivered by Silverfort on top of the existing identity infrastructure.
- High granularity: focus on the user versus the network ensures risk analysis is granular and carried out on every resource access request.
- Improved ability to detect anomalies and threats: By definition, an attacker’s movement within the enterprise environment is anomalous in comparison to legitimate users. Performing security checks for each resource access increases the likelihood to detect and prevent malicious activity.
Want to learn more?
- Schedule a demo with one of our experts
- Silverfort + Ping partnership page
- Ping Integration Directory listing