— By Jonathan Nativ, Sales Director, APAC, Silverfort —
In the game of chess, the king is the most important piece. Once your opponent gets your king, the game is over. Yet the king is a relatively vulnerable piece, and it’s protected by stronger ones like rooks, bishops and of course – the queen.
In the IT world, Privileged Access Management (PAM) (many times referred to as a Password Vault) is the ‘King’ because it stores the keys to the kingdom – the credentials of the most important and sensitive users in the organization (privileged users) and many times it is used as the entry point into the organization for external users.
Therefore, adversaries will do all they can in order to compromise it.
What is a PAM Solution and Why is it Important to Protect?
The PAM solution is a centralized repository where all the sensitive credentials are stored and managed. This includes:
1. Domain Administrator credentials
2. Database credentials
3. Cloud infrastructure credentials and access keys
4. Firewall passwords
5. Corporate Social Media Accounts
6. Many more
One key thing to note about PAM solutions is that once implemented it becomes the single most sensitive system in the network, as it contains all the credentials of the most privileged users.
According to Gartner, securing privileged accounts in an organization is a top priority security project these days. This is due to the fact that compromised credentials were used in more than 80% of data breaches. When attackers gain access to the network the first thing they are going to look for are privileged credentials. These credentials will allow them to access high value assets, move laterally in the network and install malicious software.
What if one of your system administrators (that uses the PAM solution) falls victim to a Phishing Attack and their personal credentials are stolen? If those credentials allow access to the PAM solution, the attacker now has access to all the credentials, that have been conveniently stored in one central location.
If an adversary gains access to the PAM solution he or she literally gains unlimited access to any sensitive system in the network. Adding Multi-Factor Authentication (MFA) provides a critical layer of security against the use of stolen user credentials. For that reason, PAM vendors highly recommend to always implement an MFA solution together with the PAM solution.
So How Should I Protect my King?
In a recent paper published by Deloitte, PAM and MFA are ranked as the 2 top identity initiatives for enterprises, with equal importance. These two important initiatives go hand in hand – putting all your sensitive passwords in one place doesn’t make much sense if attackers could easily access it with yet another password. Once the PAM solution is protected with MFA, even if an attacker gets stolen credentials of a system administrator, the attacker will not be able to access the PAM solution. This is because an additional factor of authentication (like a token or approval through a mobile application) is required from the user before access will be granted.
When selecting and implementing an MFA solution, it is key to make sure that all the interfaces to the PAM solution are protected by MFA – not just the front door. This may be easier said than done.
Let me explain:
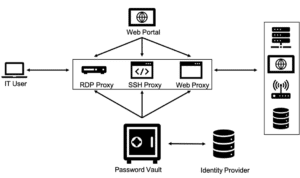
Most PAM solutions have several interfaces, including:
1. Web Portal Access – used for credential retrieval as well as administrative tasks
2. Proxy Access – used by system administrators to connect to systems using vaulted credentials (this is the preferred method by system administrators as it is more transparent).
3. API Access – used for automated tasks and service accounts

[picture caption] The image above shows a basic high level architecture of a typical PAM solution.
Here Comes the Queen
To offer real protection, an MFA solution must provide a way to secure each interface into the PAM system.
Without protecting all the interfaces, you are leaving a vulnerability in the system that will allow an attacker to get in.
In many cases MFA is not implemented on all the PAM interfaces due to the complex integration requirements. In most cases MFA implementations require agents or proxies as well as changes to the network architecture. As PAM solutions are often delivered as a “black box” appliance, it’s not possible to install agents or make changes to the code.
MFA solutions that are based on RADIUS are complex to implement and provide bad user experience due to that fact that One Time Passwords (OTP) are needed to be typed for each session that is opened (keep in mind that administrators might open countless sessions every day – so it becomes a nuisance).
Silverfort’s agentless and proxy-less solution enables MFA on all PAM interfaces without the need to make complex changes to the system or the environment. Thanks to Silverfort’s agentless architecture it is also possible to protect all the interfaces to the PAM solution, including the web interface, GUI client, API and Proxies, without the need to perform MFA again and again for each session.
When choosing an MFA vendor, it is also important to take into consideration the end user experience.
IT administrators (that use privileged accounts) are usually very sensitive to changes in their workflow. They are also using the PAM solution multiple times in the span of an hour, so any inconvenience can have major impact on productivity.
In most cases the users are storing the credentials for the PAM Solution in their browsers or connection managers to make their life easier.
Other aspects that should be considered when choosing an MFA provider for a PAM solution:
1. Changes to current workflows
2. Ability to open multiple sessions at the same time without multiple MFA challenges
3. Easy-to-use MFA options such as soft tokens and mobile MFA apps
4. Ability to trigger MFA only once within a given time frame
5. Risk-based MFA that considers user behavior and context
Silverfort’s risk-based authentication solution is flexible and enables it to provide a balance between security and user experience by allowing users to authenticate with MFA only once in a while, while keeping them secured all the time. This, together with the adaptive risk-based approach, makes it an ideal MFA solution for a PAM implementation.
Final Words
PAM is a critical security layer for organizations. PAM projects require a significant amount of time and recourses. Does it make sense to go through all the trouble to lock the door but leave the window open?
MFA should be added to protect your PAM solution from day one. It should be considered an integral part of the PAM solution and be used to secure access through all routes and interfaces in order to protect the most important assets in your network.