As enterprises push forward with digital transformation, a new and often overlooked attack surface has emerged: non-human identities (NHIs). NHIs are types of machine identities used by applications, workloads, containers, APIs, IoT devices, and more, and they far outnumber human users and are essential to how modern systems run.
NHIs drive automation and scalability but also introduce new layers of complexity and risks. Traditional identity tools, designed for human users, can’t keep up with the speed and scale of NHIs across hybrid and multi-cloud environments.
Securing these identities requires a strategic shift. Zero Trust offers that shift where identity becomes the new perimeter, and NHIs are governed, verified, and protected just like any human user.
The rise of non-human identities
According to IDC, 95% of all enterprise system-to-system communications are now conducted by NHIs. The proliferation of NHIs is not a coincidence; it’s driven by three major technological shifts.
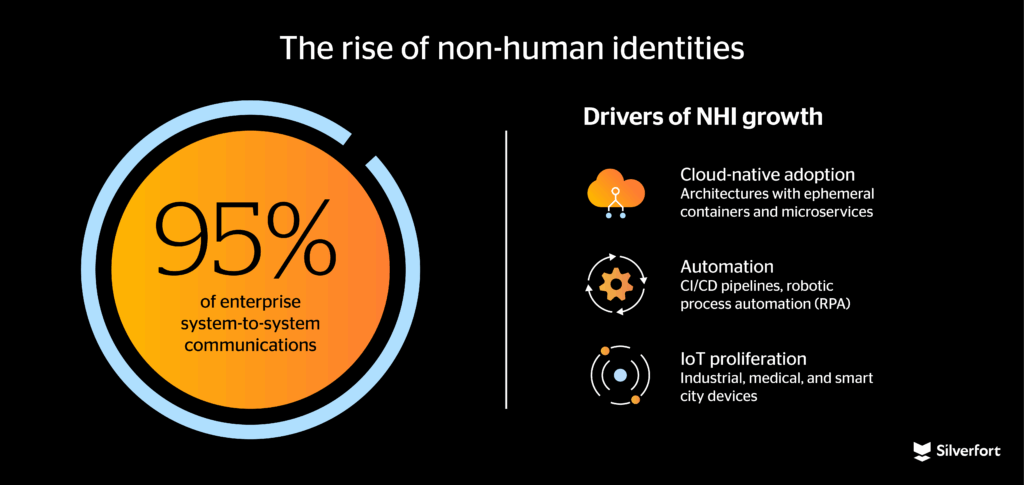
First, enterprises are embracing cloud-native architectures, containerized workloads, and infrastructure as code (IaC). In these environments, NHIs are foundational. Every microservice, serverless function (like AWS Lambda or Azure Functions), or containerized workload needs its own identity to request resources or perform operations. For example, a single Kubernetes cluster might dynamically spin up thousands of pods, each with its own machine identity and scoped access to APIs or databases. These modern architectures dissolve traditional perimeters, making identity the new security boundary. Security must now follow the workload, whether it lives in a public cloud, on-premises, or in a transient container.
Second, organizations are racing to automate repetitive tasks through CI/CD pipelines, robotic process automation (RPA), and AI-driven workflows. These systems depend on NHIs to function. DevOps pipelines use service accounts to fetch code, deploy applications, and run integration tests. Chatbots and AI agents retrieve data via API calls, relying on access tokens and machine credentials. RPA bots log in to ERP systems to process invoices or update records, often with broad access. Each of these interactions is authenticated by a non-human identity and represents a potential attack surface.
Third, the Internet of Things (IoT) revolution has added billions of new endpoints, each one requiring authentication, encryption, and role-based access. Industrial IoT sensors in manufacturing facilities send telemetry to cloud services. Connected medical devices communicate patient data in real time. Smart city infrastructure coordinates lighting, traffic signals, and energy grids. Each device has a machine identity — often poorly secured, rarely rotated, and frequently outliving its original project or use case.
A taxonomy of trust: Types of NHIs
NHIs come in various forms, depending on their use case and environment. Service accounts are widely used by applications and scripts to access databases, cloud resources, or internal systems, and they often have excessive privileges. Machine certificates (such as TLS/SSL certificates) provide encrypted communications and authenticate servers and clients; however, expired or misconfigured certificates can cause catastrophic outages. Cloud-native roles (like AWS IAM roles, Azure Managed Identities, or Google Cloud service accounts) enable workloads to access resources securely. Meanwhile, API keys and tokens allow services to interact in SaaS or third-party integrations.
While these identity credentials are easy to create and deploy, they are hard to monitor and secure. The key challenge is not just managing a few machine identities, but doing so at scale — dynamically and securely across diverse platforms.
Non-human identity security and risks: The silent epidemic
Non-human identities (NHIs) such as service accounts, API keys, and machine-to-machine credentials are vital to modern IT operations, but they often fall outside the scope of traditional IAM and even Zero Trust frameworks. These identities are frequently created programmatically, used briefly, and then forgotten, leaving them unmanaged and vulnerable.
NIST SP 800-207 emphasizes the need to eliminate long-lived credentials in favor of short-lived, automatically expiring ones. This reduces the risk of credential theft by narrowing the attack window and ensures NHIs follow the same rigorous access controls as human users.
Unfortunately, credential hygiene remains a critical weakness—and attackers are exploiting it:
- In the 2022 Twitter breach, hardcoded API keys were exposed in a public repo.
- An expired SSL certificate triggered a major Microsoft Exchange outage in 2021.
- In the SolarWinds attack, over-privileged machine accounts enabled lateral movement and data theft.
The stakes are high. Many reported cloud breaches involve compromised NHIs—often due to exposed API tokens or unmanaged service accounts. As NHIs continue to proliferate, securing and managing them is no longer optional—it’s mission-critical.
Adding to the challenge is fragmentation. IAM tools like Active Directory were designed for humans, not machines. Different environments (e.g., Kubernetes, CI/CD pipelines, IoT) manage NHIs in isolation, creating silos, inconsistent enforcement, and audit fatigue.
To address these risks, organizations must start treating NHIs as first-class identities with full lifecycle management, strong access controls, and visibility across environments all aligned to Zero Trust principles.
Why Zero Trust is essential for non-human identity security
The Zero Trust model, which asserts “never trust, always verify,” is well-suited to the dynamic nature of non-human identities. Unlike old perimeter-based security models, Zero Trust assumes breach by default and validates every access request—whether from a human user or a machine. Most Zero Trust implementations today, however, focus on human-centric measures: multi-factor authentication, single sign-on identity providers like Okta or Azure AD, and endpoint security agents on user devices.
Non-human identities often bypass these human-focused controls. A service account, for example, might have persistent access to critical systems with no MFA or behavioural analytics monitoring its use. An API key embedded in code can grant access indefinitely without triggering any alerts. These blind spots are exactly what attackers seek to exploit, allowing them to operate undetected using stolen or misused machine credentials.
Roadmap: Operationalizing Zero Trust for non-human identities
Securing NHIs under a Zero Trust framework requires a clear operational roadmap. Organizations should approach this systematically, covering everything from visibility to enforcement:
First, gain complete visibility into the machine identity landscape. You can’t protect what you don’t know exists, so inventory all NHIs across cloud and on-premises environments and map out where and how they interact.
Next, establish ownership and governance for machine identities. Every NHI should have a designated owner or team responsible for it. Define lifecycle policies for these identities — for example, automatically deactivate or rotate credentials after a period of inactivity — and enforce those policies consistently.
Modernize authentication for non-humans. Passwords and other static credentials should be phased out in favor of stronger mechanisms. Employ certificate-based or token-based authentication for services and APIs. Embracing standards like SPIFFE (Secure Production Identity Framework For Everyone) can help ensure consistent workload identity management across platforms.
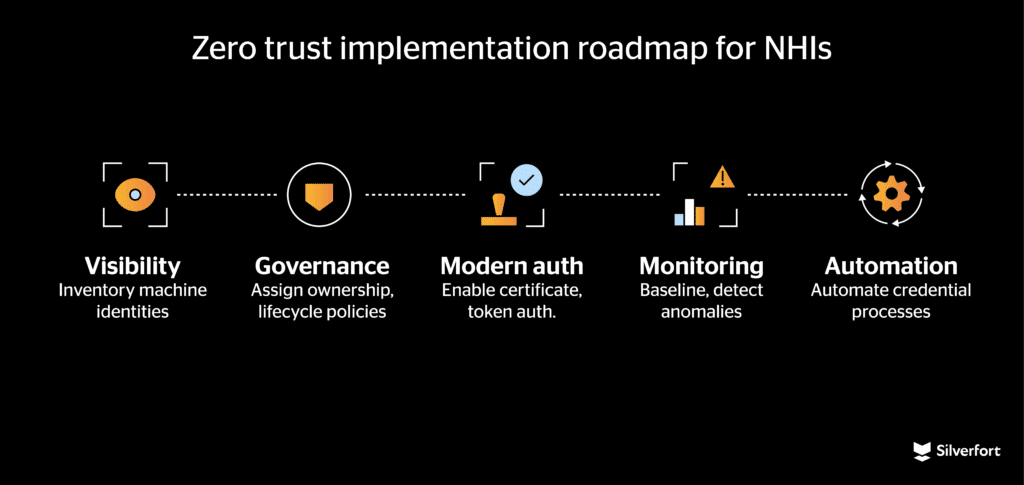
Integrate monitoring into security operations. Feed machine identity logs and access events into your Security Information and Event Management (SIEM) and User and Entity Behavior Analytics (UEBA) tools. Baseline normal behavior for service accounts and certificates and enable anomaly detection to flag unusual usage patterns in real time.
Finally, automate the machine identity lifecycle. The issuance, rotation, and revocation of credentials should be built into CI/CD pipelines and automated workflows. By integrating identity management into development pipelines, organizations eliminate manual errors and ensure that security keeps up with the speed of deployment.
Embedding Zero Trust into machine identity management
Protecting NHIs requires embedding Zero Trust principles throughout the machine identity lifecycle. This begins with recognizing machine identities as first-class entities in your IAM program, just like human users. Secure them with strong, cryptographic authentication methods — such as mutual TLS certificates for services, established workload identity standards, or time-limited API tokens — rather than shared passwords or static keys.
Zero Trust architecture also means combining certificate-based machine identities with context-aware access decisions. In practice, that could involve checking the context of a request (origin, time, workload type) before granting access, not just the credential. Decentralized identity issuance frameworks, which dynamically issue and validate certificates or tokens for workloads, can help establish trust across distributed and cloud environments on the fly.
To reduce risk, static credentials must be phased out in favor of short-lived, tightly scoped ones. Secrets management systems should issue ephemeral credentials that expire quickly, and secure identity federation can provide temporary access tokens for external or hybrid services when needed. Additionally, enforcing Zero Standing Privileges (ZSP) ensures that NHIs receive access only when necessary and only to the resources required for their task. In other words, machine identities shouldn’t have more privileges than needed, nor should they be left enabled when not in use.
Micro-segmentation is another critical Zero Trust control for NHIs. By enforcing granular network boundaries around workloads and services, it contains potential compromises and prevents attackers from moving laterally to other systems if a single machine identity is breached.
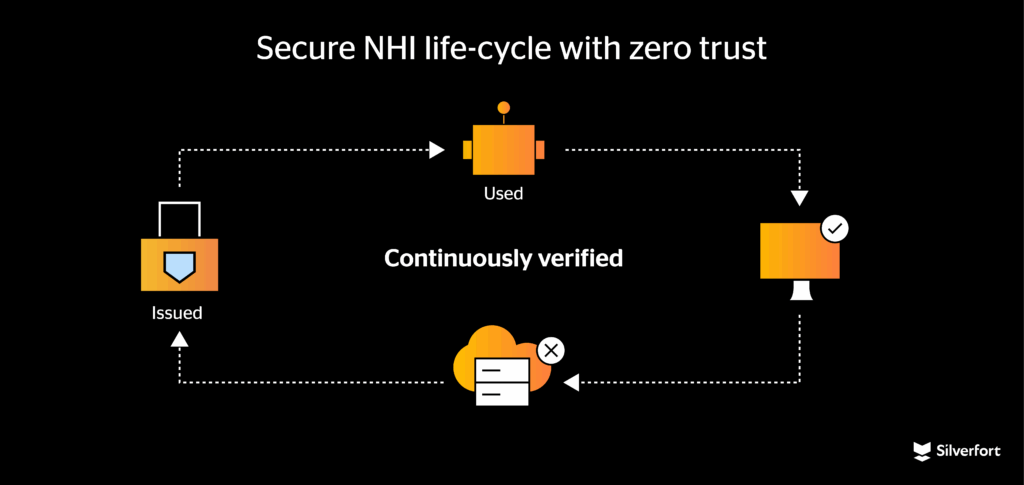
Meanwhile, continuous monitoring and behavioural analytics are essential for detecting anomalous NHI activity. Unusual access patterns — for instance, a normally dormant service account suddenly attempting to read large amounts of sensitive data — should trigger automatic responses. Those responses might include revoking the suspicious credentials, isolating the workload, or other real-time countermeasures based on risk signals. Modern Zero Trust solutions support this kind of adaptive, risk-based policy enforcement to ensure that even when machine identities behave unexpectedly, the system can respond immediately to mitigate harm.
Business case: Why non-human identity security matters now
Securing non-human identities (NHIs) is no longer just an IT concern; it’s a business-critical priority. With machine identities now vastly outnumbering human users, any gap in managing them can open the door to breaches, data loss, and operational disruption.
By moving away from long-lived credentials and enforcing continuous verification, companies can sharply reduce attack surfaces and limit the damage of potential intrusions.
But the benefits go far beyond security:
- Compliance becomes simpler, with stronger identity governance and reduced audit overhead.
- Uptime improves by automating routine tasks like certificate renewal, avoiding costly outages caused by expired credentials.
- Innovation accelerates, as unified identity governance eliminates friction across teams, systems, and environments.
In short, getting NHI security right protects the business from risk, boosts operational resilience, and enables faster, safer innovation.
The future of identity security: Unified, continuous, contextual
As experts suggest machine identities now outnumber human identities anywhere from 50:1 to 100:1 — and continue to grow exponentially — they are no longer a mere footnote in cybersecurity; they have become the front line. The future of identity security lies in unified platforms that can continuously authenticate and govern every interaction, whether it’s a person logging in or a microservice calling an API. Identity is no longer static; it’s dynamic, contextual, and foundational to security.
We are witnessing a paradigm shift. The age of NHIs is here, and with it comes both unprecedented opportunity and new risks. Organizations that elevate machine identities to strategic assets and adopt Zero Trust as their guiding principle won’t just be more secure — they’ll be more agile, more compliant, and better prepared for whatever comes next.