Lateral movement detection is a challenge every cybersecurity researcher is likely familiar with. My team and I faced this challenge a few months ago and, not surprisingly, quickly discovered there is no easy or fast solution to address it.
In this post, I’ll explain the challenge of detecting lateral movement and show you how my team and I significantly improved our ability to detect it with our Lateral Movement Analyzer (LATMA) tool. I’ll discuss the details of this algorithm and explain how it was able to get much better results than others currently available.
If you’re a practitioner, listen up! Because I’m going to share how you can use our new open-source tool to detect lateral movement in your environment.
Understanding Lateral Movement By Examining a Recent Attack
Before discussing the detection of lateral movement, let’s first define exactly what it is. And there’s no better way to do this than by using an example.
A few months ago, hackers from the cybercriminal group Lapsus$ got access to Uber’s systems via a VPN with regular user credentials they acquired using a social engineering technique called “MFA bombing.” The attackers scanned the network to find valuable information and eventually found a PowerShell script that contained admin credentials. They then used this admin’s credentials to log in to a database and expose sensitive company information.
This attack consisted of several steps:
- Getting initial access to Uber’s systems — in this case through social engineering.
- Searching for information and then using it to access other machines in the network and obtain privileged credentials.
- Using these privileged credentials to fulfill a malicious objective — in this case, exposing sensitive information.
Those three steps occur in almost every successful breach. However, only the second step is considered lateral movement since it signals the attackers’ ability to move successfully across an organization’s network. This is the step I’ll focus on.
Understanding the Role Authentication Plays in Lateral Movement
Movement between machines requires authentication. During this phase, the attacker needs to provide credentials to the identity provider, and only after these are verified can they advance to a target machine.
The problem is that normal movement between machines requires authentication as much as malicious movement, and both leave the same traces. This makes distinguishing between normal and malicious movement very hard.
One approach to tacking this is through the detection of anomalies. Taking this approach, however, has its own challenges since many anomalies are actually not malicious. For example, when an employee goes to their IT department for help and the IT person logs in to the computer of the person who asked for assistance, this is an anomaly but obviously not a malicious one.
Sadly, this is why simple anomaly detection algorithms are actually not very useful. This is why my team and I developed the LATMA algorithm that overcomes this obstacle.
The Three Steps to LATMA Detection
Step 1: Build a Graph for Abnormal Authentication Traffic
In this step, LATMA digests the entirety of authentication traffic in the organization and determines which authentications look normal and which appear abnormal. It does this using information about the domain, such as computer/user roles and their expected behavior. Then authentications are then used to build a graph representing the network, where every node represents a computer and every edge represents an authentication.
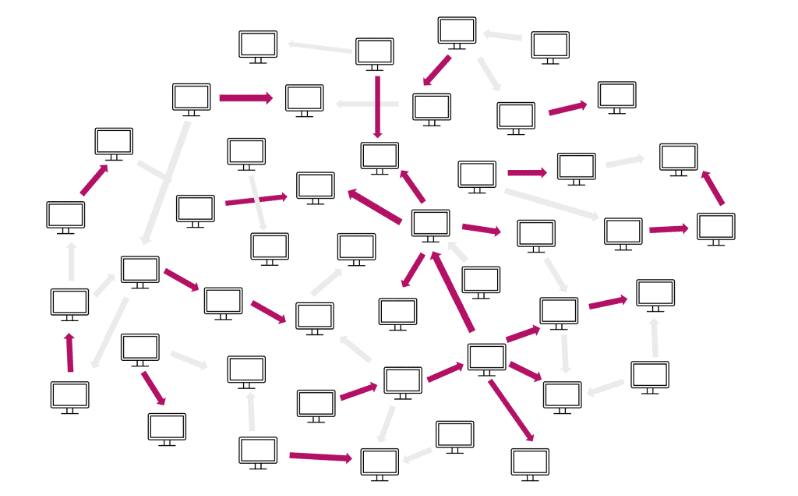
As mentioned previously, though, finding anomalies is not enough to detect lateral movement, so there are several more steps in the process.
Step 2: Finding Patterns of Lateral Movement
In this step, we take the authentication graph from the previous step as input and search for lateral movement patterns. These patterns are associated with different types of malicious intent.
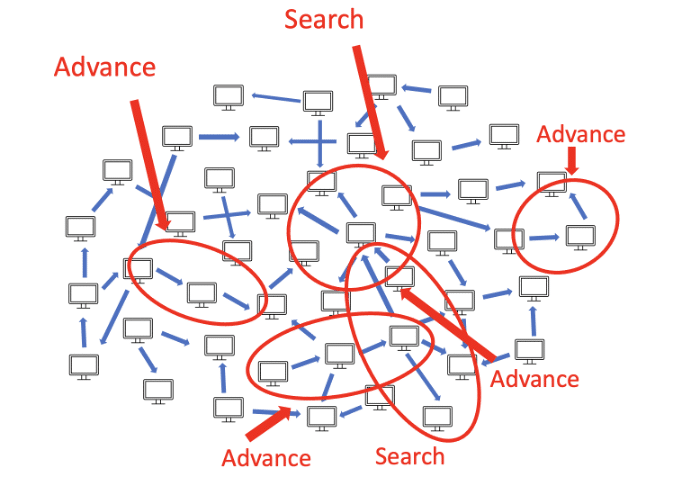
We classify the patterns into three categories:
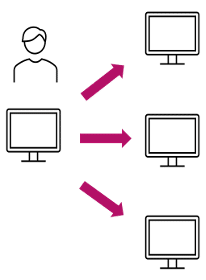
Search patterns – Before attackers perform any movement, they will likely search for a good target to advance to. The pattern is: many authentications from a single source (representing the attacker’s current location) to multiple servers.
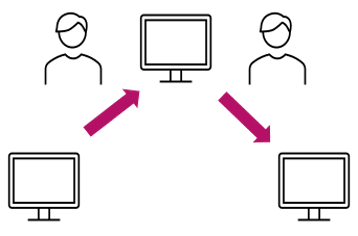
Advance patterns – These represent the attackers’ movement between different network assets. The attackers might steal credentials along the way and then use them to advance.
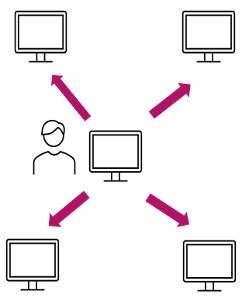
Act patterns – Usually these occur towards the end of the breach when the attackers have started to fulfill their malicious objectives. These patterns are often characterized by massive automatic access to multiple machines at once in order to steal information or run malware.
Step 3: Alerting
LATMA generates an alert when at least two of these patterns happen in sequence. For example, if the attacker searches for a target machine to advance to and then successfully advances to it, the algorithm generates an alert.
In the example, the attack could have been stopped before the acting pattern, because the algorithm generates an alert if it detects an acting pattern connecting to another pattern. Acting patterns usually mean that the attacker has already fulfilled their objectives. In this case, the output of the algorithm can help with the investigation.
Introducing LATMA: the Lateral Movement Analyzer Tool
As part of our research, we developed a free tool that implements LATMA’s logic and outputs a detailed report of all suspicious movements in the environment. The tool consists of two modules:
Logs Collector – This module collects authentication traffic from the Active Directory (AD) environment. It gathers the logs from the domain controllers and endpoints, focusing only on interactive Kerberos and NTLM authentications. This module is open-source and can be found here: https://github.com/silverfort-open-source/latma
Analyzer Module – This module inputs the logs from the collector and outputs a detailed report containing the patterns that LATMA found, how they’re connected, and who performed them and when. It also visualizes the findings in a GIF. This module is free and can be found here: https://www.silverfort.com/resources/tools/lateral-movement-analyzer-tool-beta/
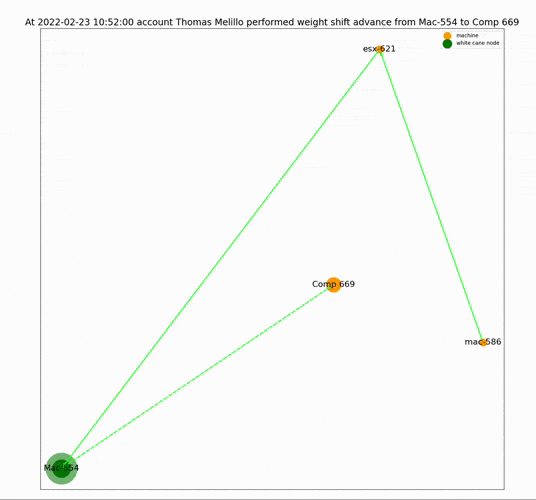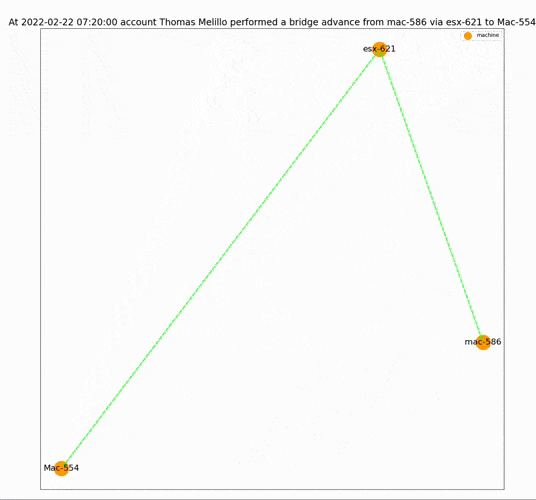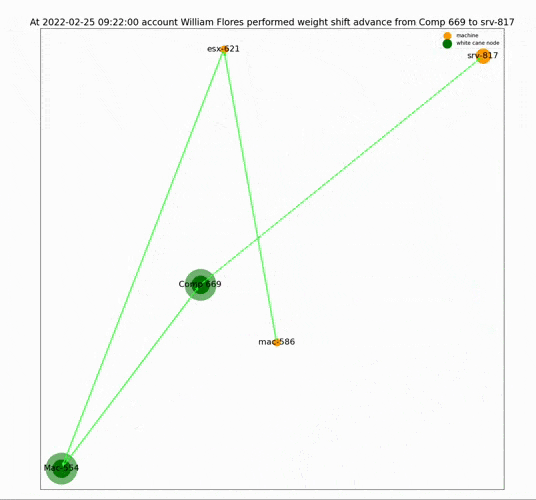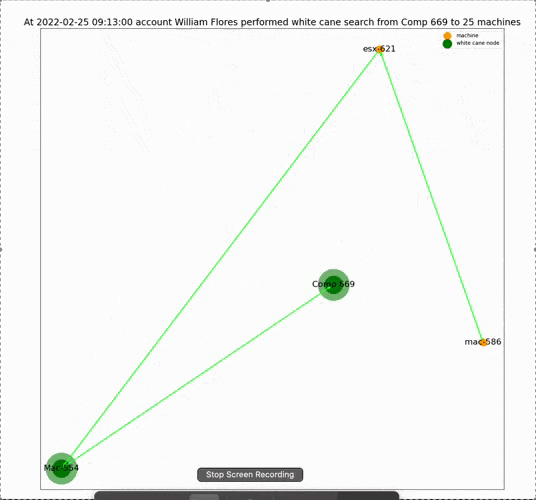
One of the advantages of this tool is that the results are readable and clear. Because sometimes the hardest part in dealing with an alert is not just knowing that it happened but convincing your team that it was not a false alarm. LATMA’s straightforward output helps address this issue.
Watch this full demo of LATMA, from 16:54 – 30:44
The Proof of LATMA Is in the Results
If you’ve read this far, I hope you’re convinced that this algorithm and tool have value. So I also want to show you that it is extremely accurate.
As part of my job at Silverfort, I get to see authentication traffic from hundreds of different environments, and you might be surprised to learn that many of them are targeted by lateral movement attempts. We know this because either our customer discovered this or Silverfort’s platform alerted us to it. That makes this data good for validation, training algorithms, and testing hypotheses.
We ran LATMA on dozens of data sets from different environments. The bottom line is that it detected 95% of lateral movements and generated a false alarm approximately once every three days — almost 30 times better than other existing algorithms!
Future Work: Where We’re Going With This
The work on the algorithm helped me and my team better understand and model lateral movement attacks. It also made me realize that, despite the significant improvement, there is still a long way to go. Attack surfaces are evolving quickly and attackers have more and more opportunities to take advantage of this, for example by moving from an on-prem environment to the cloud and vice-versa. So a potential enhancement to this algorithm would include logs and events from cloud environments and detection for a lateral movement that crosses platforms.
So tuned for more news around LATMA and be sure to let us know your feedback about this tool.

