As cyber threats evolve, organizations must constantly adapt their identity security strategies to stay protected. One of the most significant elements of modern security strategies is network segmentation, which involves the division of a network into smaller, isolated segments to limit unauthorized access to sensitive resources.
As network segmentation is well-known and implemented by most organizations, the rise of identity threats presents a more modern approach to segmentation from the identity control plane.
A further extension of this concept is identity segmentation, which focuses on the identity and attributes of the users, devices, and applications. This approach enables organizations to apply granular access controls to specific identities, improving their overall security posture and protection against unauthorized access.
In this blog, we will explore the difference between network segmentation and identity segmentation. We will also explore how identity segmentation is the key to implementing a true Zero Trust strategy.
The Evolution of Network Segmentation
Network segmentation is a security approach that isolates segments in the enterprise network to reduce the attack surface. Network segmentation works best in the “castle and moat” enterprise environment, securing all exposure points in the environment. This approach has been heavily implemented since the early 2000s by security and IT teams.
While this approach has proven effective in most network security strategies, the evolving nature of cyber threats highlights gaps in network segmentation.
Network segmentation access policies are typically defined by firewall rules or VLANs, which tend to be static and dependent on network traffic. These static policies are dependent on the device and not the user’s access requirements, often granting broad access to users based on their location within the network. Attackers increasingly target user identities, exploiting compromised credentials to gain unauthorized access.
The approach does not adapt to the dynamic nature of modern work environments, where users access resources from a variety of devices and locations. Network segmentation fails to provide the granular control required to secure identities effectively.
Identity Segmentation Boosts Identity Security Posture
Identity segmentation is the approach to security that involves managing and controlling access based on user identities, roles, and attributes. Instead of relying on rigid network boundaries such as IP access lists and firewall rules, identity segmentation divides the network not just from a physical or geographical standpoint, but also from the perspective of the identity control plane.
This is done by segmenting an environment based on the identity and attributes of users, devices, and applications. By doing so, organizations can implement granular access controls, ensuring users only have access to the resources necessary for their roles.
Network Segmentation vs Identity Segmentation
Network segmentation involves dividing a network into different segments to enhance security and control. Traditional network segmentation relies on factors like IP addresses, VLANs, and physical separation to create these segments. While effective at limiting the impact of a breach within the network, network segmentation often falls short in addressing the dynamic and evolving nature of user identities.
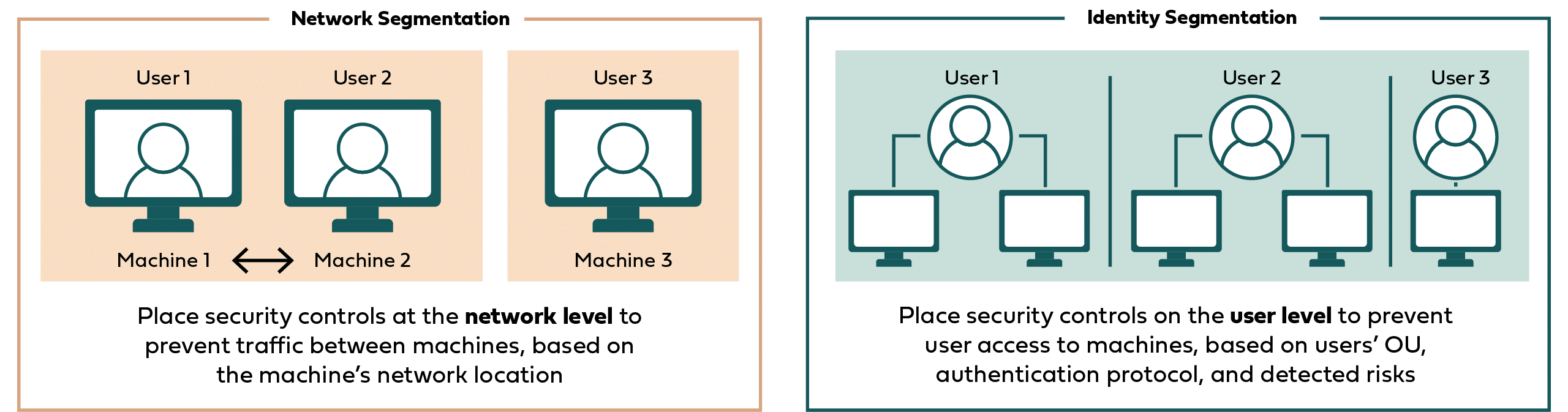
On the other hand, identity segmentation shifts the focus to user identities. This approach aligns with modern security threats where users are the primary targets and threats often exploit compromised credentials. Identity segmentation involves creating access controls based on user attributes, roles, and behavior, so users can only access the resources necessary for their roles, irrespective of their network location.
The primary difference lies in their focus: network segmentation emphasizes securing pathways and infrastructure, while identity segmentation centers on safeguarding individual user identities. Network segmentation tends to rely on static policies based on network structure, whereas identity segmentation involves dynamic and context-aware access controls based on user attributes. Identity segmentation is particularly effective in countering identity-based threats, which have become increasingly prevalent in the cybersecurity landscape.
Adapting to the Zero Trust Architecture
To implement a Zero Trust architecture, all organizations must protect their identities, devices, networks, applications, and workloads, as well as data. It is important to note that while many organizations have successfully implemented a few principles of the Zero Trust model, most still need to strengthen their identity security posture management.
Strong identity management and protection enables organizations to respond more rapidly and precisely when a potential threat arises. IT teams can better track and alert on any identity threats that come up, prompting proactive measures to stop potential unauthorized access attempts.
To construct a complete Zero Trust architecture across your environments, identity management and identity protection must be the core components. This will enable you to manage and protect all aspects of identity effectively, which is essential for safeguarding all types of assets, including those that are on-prem.

