Identity has a once-in-a-decade opportunity to elevate its role and redefine its security criticality within the organization. Not by adding yet another product, but by becoming something fundamentally different: a discipline at the very heart of enterprise security. For IAM practitioners, this is a chance to stop being perceived as a back-office function and instead step into the role of orchestrators and frontline defenders.
“For IAM practitioners, this is a chance to stop being perceived as a back-office function and instead step into the role of orchestrators and frontline defenders.”
Why now? Because the explosion of SaaS, Cloud, and Agentic Software, AI agents, automated services, and high-velocity digital transactions, has completely challenged the status quo. Identities are no longer limited to employees and a few service accounts, they now include ephemeral agents, scripts, workloads, and bots that appear and disappear at machine speed. This proliferation of human and non-human identities poses a new scale and complexity that traditional IAM cannot control. At the same time, it opens a window of opportunity for a required shift in how we design, operate, and secure identity.
And in the background, one fact has not changed: over 80% of today’s attacks are still based on identity compromise. Even the smallest organizations now juggle dozens or hundreds of identities, while large enterprises wrestle with tens or hundreds of thousands. The sheer explosion of identities means no organization can manually trace or control them. That is not just a risk, it is an opportunity to build a new paradigm for securing access.
Identity is no longer “just IT plumbing” or “compliance automation.” It has become the most important building block in securing cloud infrastructure, AI-driven operations, and the future of enterprise trust. This mid-decade is not just another checkpoint in technology evolution. It is the turning point where identity becomes the foundation of modern security.
In this blog, I will explore a brief history of IAM, how it evolved from IT housekeeping to compliance, to security, and use that lens to propose a phased, practical transition to your future role. The goal is to provide both perspective and a strong opinion: it is time for organizations to treat IAM not as an audit tool, but as the frontline of defense for the next five years.
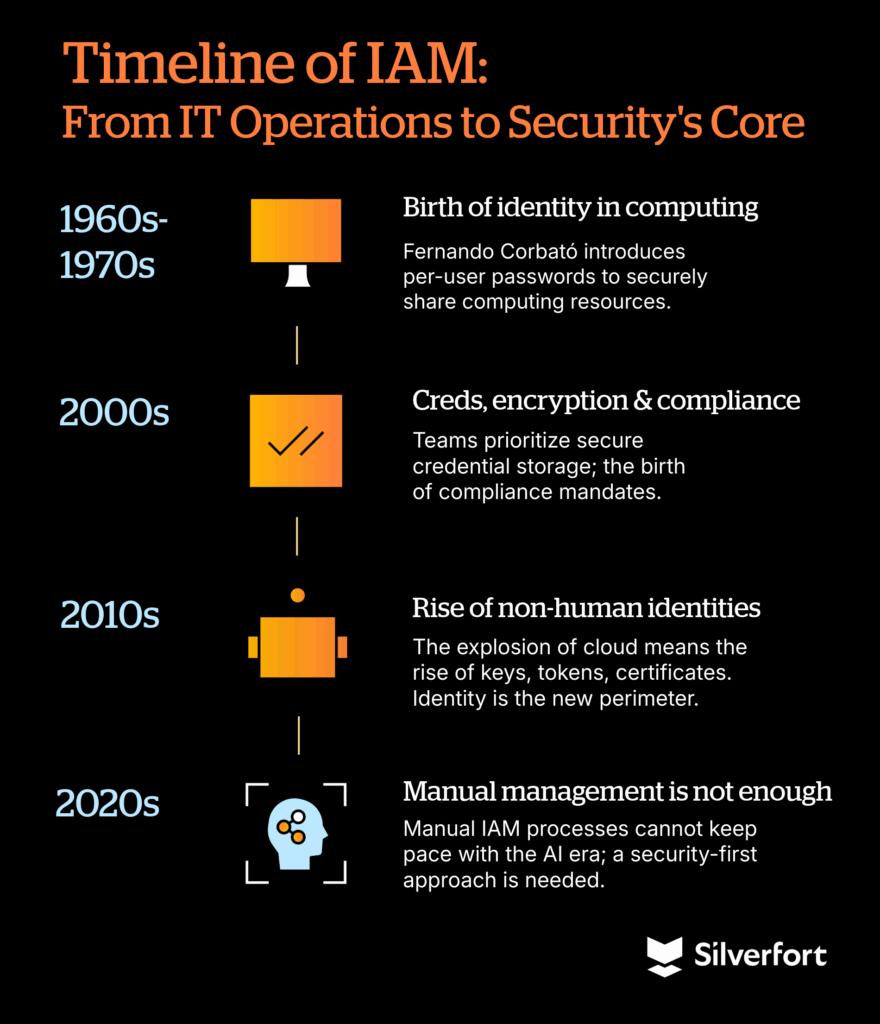
A brief history of IAM: From IT Operations to security’s core
1960s-1970s: The birth of identity in computing
The roots of digital identity trace back to MIT’s Compatible Time-Sharing System (CTSS), led by Fernando Corbató. Corbató introduced the concept of per-user passwords, arguably the first mainstream identity control, so multiple people could share computing resources securely. It was a multi-step innovation: authentication, authorization, and accountability all tied to individual user IDs. This was the spark that later ignited the IAM discipline.
2000s: Credentials, encryption, and compliance takeover
By the early 2000s, enterprises were flooded with credentials: usernames, passwords, PINs, smart cards, physical tokens, and biometric experiments. Encryption became widespread, as did secure credential storage and exchange. This was also the decade of “bring your own credential” (BYOC), contractors, partners, and federated access. At the same time, compliance mandates such as SOX, HIPAA, and PCI pulled IAM into the spotlight. Identity became less about enabling work and more about satisfying auditors. IAM was increasingly measured by its ability to produce evidence: access reviews, segregation-of-duty checks, and governance workflows. In many organizations, governance became more urgent than security.
2010s: Keys, tokens, certificates, and the rise of non-human identities (NHIs)
The cloud era made new types of credentials explode: API keys, OAuth tokens, certificates, and service accounts, credentials that were invisible to most security teams but ran entire infrastructures. This was the birth of the Non-Human Identity (NHI) as a dominant class of identity, often outnumbering humans by 40+:1. At the same time, the collapse of the network perimeter forced security teams to declare: identity is the new perimeter. MFA, SSO, and federated identity became baseline expectations. Yet IAM was still reactive, chasing provisioning cycles and static role models while attackers increasingly targeted these new machine credentials.
“Identity is the new perimeter. MFA, SSO, and federated identity became baseline expectations. Yet IAM was still reactive.”
2020s: Human IAM processes are not enough
Now, in the 2020s, the pendulum has swung back to security-first identity. Human-driven IAM processes—manual approvals, static roles, periodic reviews—can’t keep up with the scale, speed, and complexity of cloud and AI ecosystems. Identities now include AI agents, ephemeral workloads, pipelines, and automated decision-making systems. Security cannot treat identity as a compliance afterthought, nor can teams rely on weak identity capabilities bolted onto foundational endpoint or cloud solutions. IAM must become the frontline. Identity practitioners are now using a single control plane across all their IAM infrastructure for real-time decision-making, context and enforcement.
This urgency is underscored by tectonic market shifts: Palo Alto Networks acquired CyberArk, Microsoft is showering Entra with security-first features, the Identity Threat Detection & Response (ITDR) category has exploded, and asset management itself is increasingly defined in terms of identity rather than hardware or network topology. These shifts confirm a reality: identity is no longer a wire connection, it is the new security fabric.
Why security must evolve into identity-centric security, and why this is the time for IAM people to grow
The old IAM toolbox, manual access approvals, periodic reviews, static roles, and proxy-based enforcement, cannot keep up with the cloud and AI era. IAM is now the connective tissue linking systems, platforms, and data across borders and organizations. It is faster, more dynamic, and in some cases self-operating. Identity today serves both the good guys and the bad guys: the same AI agents that build software can also be weaponized as malware or malicious bots.
This makes IAM professionals the last human-in-the-loop for the new frontier of digital identities. We are in a position to block, exhaust, and push back against attacks before they succeed, while automating the governance and operations around them. If IAM changes in the right way, it will not be a second layer of defense, it will be the frontline of security itself.
“Identity today serves both the good guys and the bad guys: the same AI agents that build software can also be weaponized as malware or malicious bots.”
Redefining the identity team’s role
This transformation requires reimagining how IAM teams work. The IAM function is no longer just about provisioning users or enabling SSO, it is about becoming the human orchestrators and frontline defenders of security. IAM teams connect the organization, enable business through privileges and credentials, and, more importantly, orchestrate context-based access decisions at scale. They are security’s partner as identity becomes the frontline.
Think of your IAM controls as “little agents” embedded in every privilege you grant. Those agents must dynamically tweak and adapt each access decision in a just-in-time, context-aware motion. This is where the IAM team’s role becomes strategic: building, operating, and refining these agents as part of a security fabric that scales with the enterprise.
As I will elaborate in his upcoming articles, IAM must evolve into a discipline of orchestration, where the IAM professional is not only an enabler of access, but also a defender who ensures every use of access is continuously evaluated, contextually enforced, and secured in real time.
A 6-step guide to elevating identity into security’s frontline
(0) Clear your mind and task list: Automate everything you can, now. Automate access reviews, compliance work, rightsizing of permissions, and initial access grants. This work is already a commodity, your focus should be elsewhere. Look for platforms that integrate governance automation and remove manual audit drudgery from your daily work.
(1) Make your control plane: Make all your controls work together. No more silos. Add a layer of correlation and orchestration across all human and machine accounts. Every root entity, user, machine, software, or agent, should have a clear access storyline and behavioral profile, automatically built from the moment it is created. A real-time access graph per identity is no longer optional. Seek technologies that unify identities across hybrid cloud, DevOps, and SaaS, producing continuous access mapping and control.
(2) Complete the controls: Touch the untouchable. Make sure you have the right controls around AI, DevOps pipelines, IOT, ICS, cloud workloads, and emerging agentic systems. Non-human identities are already the majority, secure them as first-class citizens. Adopt tools that extend IAM visibility beyond users to endpoints, workloads, APIs, and infrastructure.
(3) Make context matter for every single transaction decision: Marry (1) and (2) to create context, behavioral, privileges, posture, and risk, that feeds your control systems. Every access request should be contextual, not just credential-based. Start with advanced static rules, then move toward risk-based or AI-assisted decisions. Look for identity security that natively integrates context into their decision engines.
(4) Become the human-in-the-loop of automated dynamic access: Once the platform is in place to automate day-to-day tasks, your role shifts to making the hard calls, edge cases, anomalies, and true access security decisions where human judgment is irreplaceable. Choose technologies that trigger humans only for outliers, freeing your time for strategic decision-making.
(5) Build your place at the security crisis table: IAM must sit at the crisis panel during breaches, not in the back office. You are a decision-maker, a reality reader, and a leader when breaches unfold. This is how IAM becomes truly security-first. Invest in platforms that feed IAM signals directly into incident response and SOC workflows.
The (near) future is identity-first: Get ready now
We are living in the most exciting and consequential time for IAM professionals. With 80% of attacks rooted in identity, and with cloud and AI reshaping the digital landscape, IAM is now the frontline of enterprise defense.
Now you have to decide: will you be an early adopter, leading the charge and reshaping how IAM secures your enterprise, or will you wait until the change fully happens and then scramble to adapt?
The mid-2020s through 2030 will be remembered as the decade when identity professionals finally took their rightful place on the frontlines. And if we get this right, IAM will not just protect our enterprises, it will shape the future of secure digital trust.
We will post different articles and reviews about each of these six steps in future blogs and podcasts. Stay tuned, and get ready to lead this new era.
References
– MIT and Fernando Corbató, origin of passwords: [MIT News]
– Sonrai Security – History of Identity
– Palo Alto Networks acquisition of CyberArk (2024): [SecurityWeek Reports]
– Microsoft Entra roadmap: Microsoft Security Blog
– Identity Threat Detection & Response (ITDR) growth: [Gartner – 2023-identity-threat-detection-and-response-gartner]

