How Silverfort Overcomes the New Lock Screen Bypass Vulnerability (CVE-2019-9510)

Last week, CERT released an advisory about a Windows vulnerability (CVE-2019-9510) that allows effectively bypassing Multi-Factor Authentication (MFA) to Windows servers. Microsoft was quick to dismiss the vulnerability. But however you look at it, with most MFA solutions, locked remote desktops can be unlocked due to this vulnerability without using MFA, even if MFA is enforced on the server.
CERT said that there is no practical solution to the problem and recommended a few workarounds. In this post, we show how Silverfort can be used to overcome this vulnerability.
Table Of Contents
The Vulnerability Explained
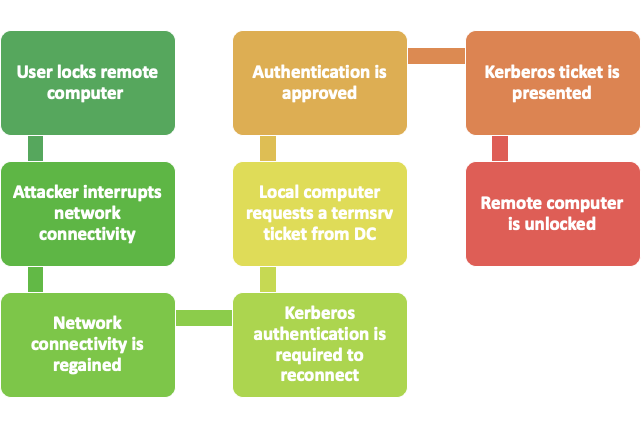
The vulnerability is a result of a new behaviour of the RDP reconnection feature in Windows 10 1803 and Windows Server 2019. If Network Level Authentication (NLA) is enforced, the following sequence of events triggers the vulnerability:
A similar sequence of events will lead to the vulnerability even if NLA is not enforced. The issue with these flows is that the user locked the remote desktop, but the attacker re-opened it without the user entering the password, based only on the Kerberos ticket. This flow remains the same even if an MFA solution is implemented for desktop logon. One would expect the remote desktop to require the user to re-enter their password and provide the second authentication factor to unlock the remote desktop. But this is not the case with the new RDP reconnection behaviour.
The vulnerability has two main effects:
- The user reconnects to the server without re-entering the password.
- If an MFA solution protects Windows logon, rather than the underlying protocols Kerberos and NTLM, the user is not required for MFA to unlock the computer. This affects most MFA solutions.
Easy to Reproduce
To witness the vulnerability with your own eyes, try the following steps:
- Remote desktop to a windows 10 1803
- Lock the remote desktop
- Disconnect the client device from the network
- Reconnect the client device
- You are back in the remote desktop session without reentering your password
Why Silverfort is Unaffected
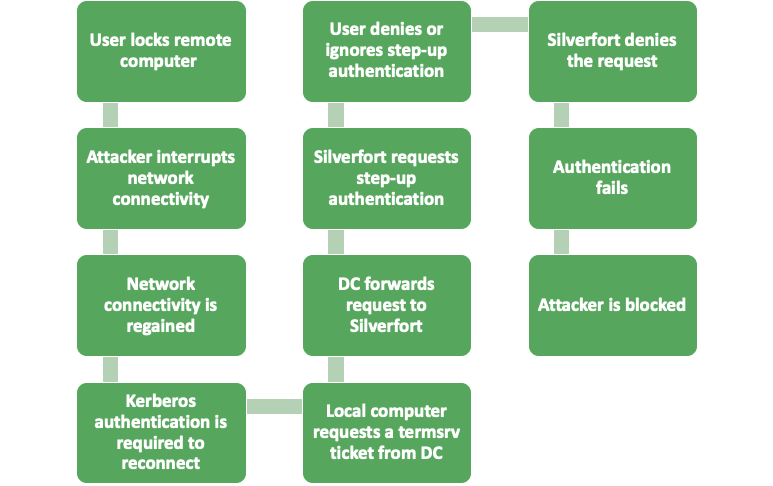
Consider a remote desktop protected by Silverfort. Silverfort can protect any Kerberos service running on the remote desktop, including terminal services (termsrv). A policy in Silverfort can be set to require MFA every time a termsrv ticket is requested to the remote desktop.
Now let’s reconsider the sequence of events that led to the vulnerability, but this time with Silverfort:
By requiring step up authentication for the Kerberos ticket request, in addition to the desktop logon, Silverfort is able to block the attack.
Moral of the Story
This vulnerability shows that it’s not enough to have MFA for one interface of a system. All access points to a system should be protected with MFA to protect it from compromise.
Further reading
Microsoft’s description of the RDP reconnection feature
Microsoft’s response
Yaron Kassner, CTO and Co Founder, Silverfort
Silverfort’s CTO and Co-Founder Yaron Kassner is a cybersecurity and big data technology expert. Before co-founding Silverfort, Yaron served as a big data expert consultant for Cisco. He also developed new capabilities involving big data analytics and machine learning algorithms at Microsoft. Prior to that Yaron served at the 8200 elite cyber unit of the Israel Defense Forces, where he led a reputable R&D team, raised to the rank of Captain, and received a prestigious excellence award. Yaron holds a B.Sc. in Mathematics, Summa Cum Laude, an M.Sc. and Ph.D. in Computer Science from the Technion – Israel Institute of Technology.