Microsoft has recently disclosed that four zero-day vulnerabilities in Microsoft Exchange Server are actively being exploited in the wild by the Hafnium attack group. Three of these vulnerabilities are operable either in conjunction with an authentication bypass vulnerability or by gaining admin permissions with compromised credentials. This highlights once again that admin access is a critical attack surface that should be closely guarded.
Microsoft released a security update in which these vulnerabilities are fixed. This is by far the most effective protection method and we urge you to install it ASAP. In addition, various security vendors released IOC for their customers to detect if these vulnerabilities are exploited in their environments.
However, this is by no means the last zero-day event, or the last attack targeting admin interfaces. And while both the security update and the released IOCs mitigate the Hafnium threat, there is definitely a need for a proactive protection method that eliminates this attack surface altogether.
Silverfort’s Unified Identity Protection provides such a method, enabling identity and security teams to dramatically reduce attackers’ ability to utilize compromised admin credentials to access, modify or run code on critical servers.
What is the Actual Risk from Hafnium Zero Days?
Exchange servers typically contain sensitive enterprise data and are thus considered a high-value target for attackers. After gaining an initial foothold in the target network, attackers look to obtain privileged access – typically by compromising admin credentials. The unfortunate reality is that despite the multiple security solutions in place, attackers typically succeed in this task.
In this attack Hafnium exploits two types of zero-day vulnerabilities:
- >The Authentication Bypass vulnerability CVE-2021-26855 allows the attacker to authenticate as the exchange server and gain malicious access.
- Code execution and file writing vulnerabilities (CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) enable attackers to execute code and write files to any path on the server. In order to use them the attacker must either exploit CVE-2021-26855 first, or log in with admin credentials.
In this part of the kill chain, the attackers perform what seems to be a legitimate login with legitimate credentials and is therefore a blind spot that neither IAM solutions, nor other security solutions, can efficiently identify as a problem.
Time Protection for Admin Credentials with Silverfort
MFA has been proven to be a powerful control against the malicious use of compromised credentials. By requiring uses to confirm their identity with a second factor, you can prevent attackers from gaining unauthorized access. The problem is that until today, MFA solutions could not be implemented on access interfaces to on-prem servers – including Microsoft’s Exchange Server, regardless if the access is done locally or remote, using RDP or a command line remote access tool.
Fortunately, Silverfort now allows you to enforce this type of protection for administrative access in real time by implementing MFA for Exchange on Premise.
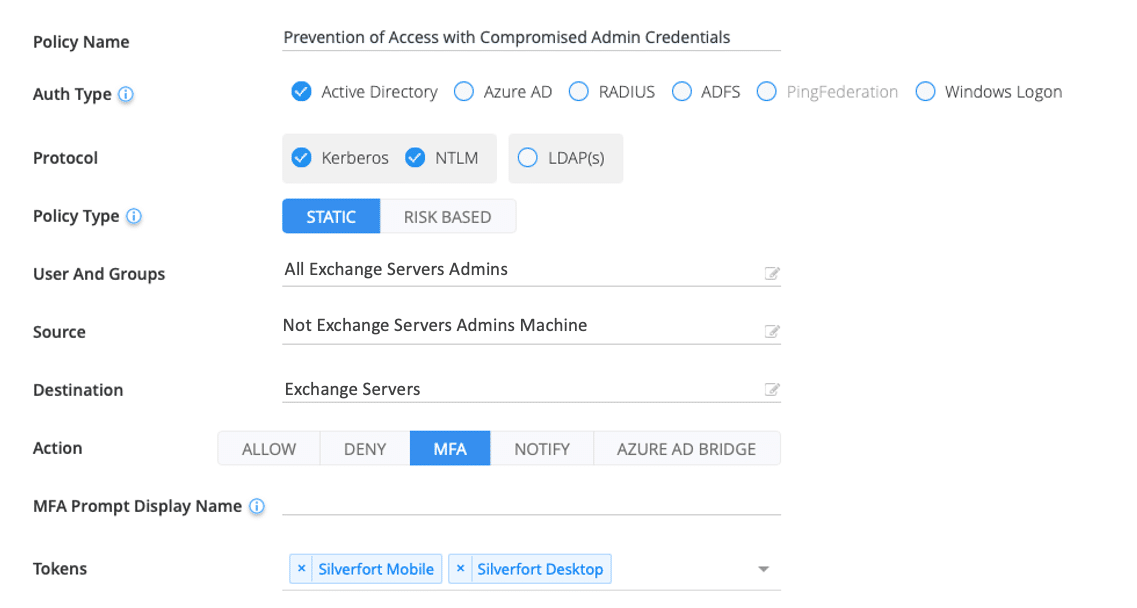
MFA for Administrative Access
The policy requires you to enter:
- The Users: a list of all the accounts with administrative privileges on the Exchange Server
- The Source: every machine that is not part of the Exchange admins machines’ group
- Desired Action: we recommend that MFA be enforced for any access attempt from these source machines to the Exchange Server
Monitoring and Blocking Access of Service Accounts
In many deployments, various service accounts are created for Exchange Servers. These machine-to-machine accounts introduce the same risk associated with human admin accounts, but they cannot be protected by MFA since there is no real person behind them.
Since the behavior of service accounts is highly predictable, Silverfort can automatically identify them and compare their behavior against a baseline to detect any deviation that may indicate a possible compromise. Silverfort then provides policy suggestions that can be easily enabled at any time to block suspicious access, send alerts to your SIEM, write to the log or any combination of the three.
Visibility for Post Breach Analysis
Silverfort generates and provides a full audit trail of admin account activities and the risk level of each access attempt. This visibility is highly useful if you choose not to enforce MFA. While this would not block the malicious access attempt in real time, it would provide actionable insights about any suspicious logins as well as assist in conducting an efficient forensic analysis of prior malicious activity.
Conclusion
Administrative access is one of the most critical attack surfaces in your network and should be protected accordingly. Enforcing MFA on all admin access to sensitive machines in your environment proactively prevents attackers from accessing them for malicious purposes – including the exploitation of CVE-2021-26857, CVE-2021-26858, CVE-2021-27065 Hafnium zero-day vulnerabilities. Silverfort allows you to enforce MFA on any device without installing software agents on each Exchange server and without deploying proxies in your network.
To learn more, schedule a call with one of our experts.