Silverfort research finds threat actors could attack new Microsoft cloud authentication protocol to steal or forge cloud tickets and carry out lateral movement
Summary
Silver Ticket and Pass the Ticket (PTT) are infamous legacy on-prem Kerberos attacks used to perform Lateral Movement in Active Directory. Marking another step towards the cloud, Microsoft recently made Azure AD Kerberos, their cloud-based implementation of the Kerberos protocol, generally available. Azure AD Kerberos enables authentication to cloud resources without having to use an on-premises Active Directory. Microsoft made security enhancements to this cloud variant of Kerberos; however, the attacks lie in the underlying logic of how the protocol operates, so fixing them would require Kerberos to be significantly re-engineered. It is not simply a case of patching flawed code.
We’ve developed two variants of Pass the Ticket and Silver Ticket which work for Azure AD Kerberos. We named them Bounce the Ticket and Silver Iodide. These attacks expose infrastructure hosted by Azure, such as servers and storage, to malicious access.
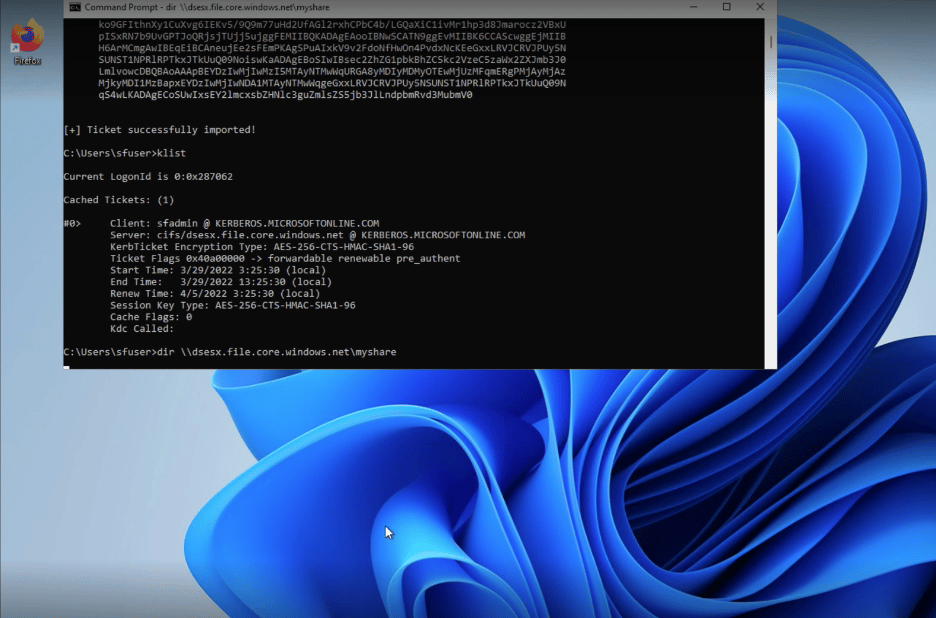
You can read the full technical analysis in this white paper.
In accordance with responsible disclosure, both techniques were shared with Microsoft’s MSRC team prior to publication. We’d like to share our appreciation for the time and effort the company took to assess our research.
As there is no specific fix, Silverfort urges enterprises to perform the following mitigations:
- Review and monitor for any changes to Azure Access Control (IAM) and the share’s access control permissions to validate that only authorized users have permissions for the Microsoft.ClassicStorage/storageAccounts/listKeys/action – Kerberos key extraction operation.
- To avoid the Bounce the Ticket attack, reduce the number of computers allowed to hold cloud TGTs to the minimum required. You can do that by restricting the “Allow retrieving the Azure AD Kerberos Ticket Granting Ticket during logon” group policy to security groups that use Azure AD Kerberos.

