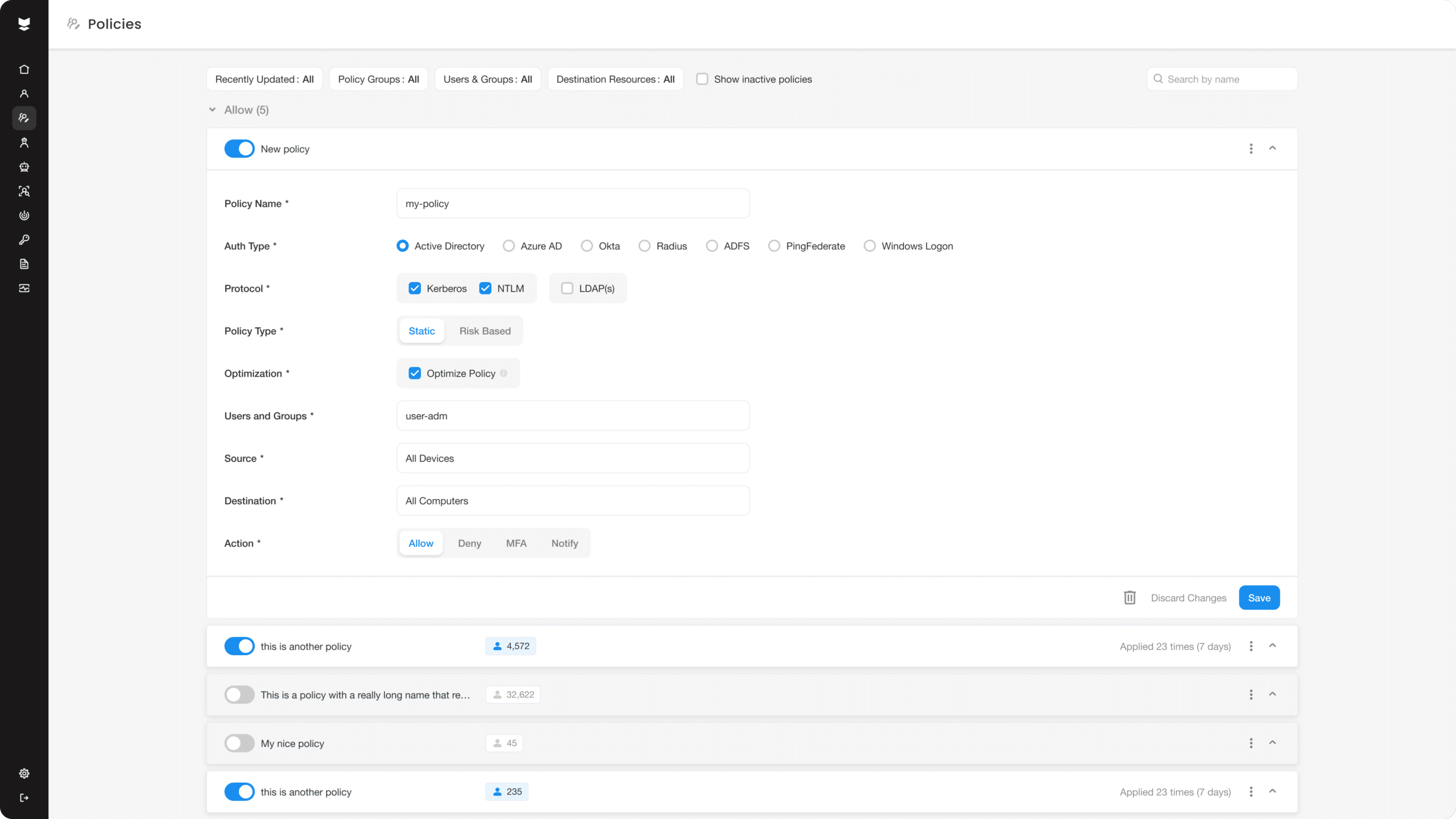
Secure access for the most complex networks with Silverfort’s cutting-edge MFA for Juniper.
Silverfort is the next-generation solution for multi-factor authentication (MFA) for Juniper. We offer a unique agentless solution that extends secure access to any sensitive resource, including those on-premises, in the cloud, and across hybrid environments. Our platform enables granular access controls and policy enforcement, as well as a seamless user experience across all applications. With Silverfort, you can easily integrate MFA into your existing infrastructure to reduce risk while improving security posture. Get started today with Silverfort’s MFA for Juniper.