Protect every access point—no exceptions.
When we say universal, we mean it. Extend MFA to every resource, including legacy apps, homegrown systems, command-line tools, and OT infrastructure—without modifying them.
- No agents, no app changes, no system modifications.
- Complete MFA protection across your hybrid environment.
- Protect resources that don’t natively support MFA.

Protect every access point—no exceptions.
When we say universal, we mean it. Extend MFA to every resource, including legacy apps, homegrown systems, command-line tools, and OT infrastructure—without modifying them.
- No agents, no app changes, no system modifications.
- Complete MFA protection across your hybrid environment.
- Protect resources that don’t natively support MFA.

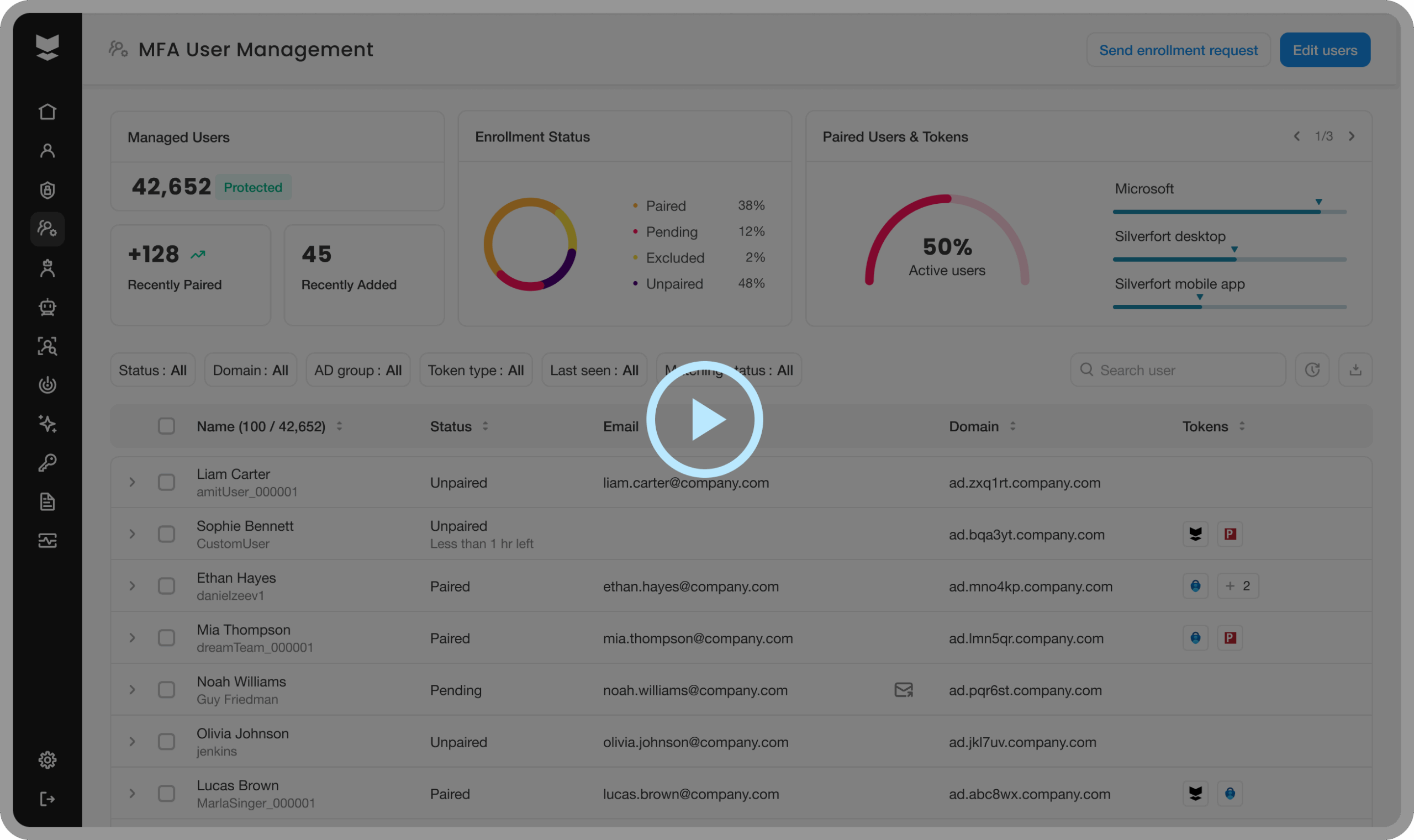
Your MFA coverage is (probably) incomplete.
Most MFA solutions only cover modern systems and apps. But in enterprise environments, there are still legacy apps, command-line tools, OT systems, and on‑prem targets that MFA can’t reach. MFA gaps are risk magnets. Attackers shift to weak or unprotected systems to bypass controls.
Unprotected legacy and homegrown apps
Retrofitting MFA often requires changes, rebuilding, agents, or deep integration, which may break workflows.
Fragmented MFA islands
Different MFA systems per tool or silo create inconsistent security.
No adaptive, risk-based MFA
Static rules fail to respond to user context or risky behavior.
High effort and disruption risk
Static rules fail to respond to user context or risky behavior.
Your MFA coverage is (probably) incomplete.
Most MFA solutions only cover modern systems and apps. But in enterprise environments, there are still legacy apps, command-line tools, OT systems, and on‑prem targets that MFA can’t reach. MFA gaps are risk magnets. Attackers shift to weak or unprotected systems to bypass controls.
Unprotected legacy and homegrown apps
Retrofitting MFA often requires changes, rebuilding, agents, or deep integration, which may break workflows.
Fragmented MFA islands
Different MFA systems per tool or silo create inconsistent security.
No adaptive, risk-based MFA
Static rules fail to respond to user context or risky behavior.
High effort and disruption risk
Static rules fail to respond to user context or risky behavior.
From partial coverage to universal enforcement.
Complete MFA, no compromise. Silverfort extends MFA to every identity and system—even where it was never possible before—without disrupting users or breaking workflows.
Full MFA reach
Silverfort protects the unprotectable, including all AD resources regardless of the system, interface or protocol.
Zero code changes
No need to modify your servers or apps thanks to our patented Runtime Access Protection (RAP) technology.
Adapt to your MFA stack
Consolidate—or complement—your existing MFA solutions for cost saving and better user experience.
Critical multi-factor authentication challenges we solve every day.
Apply MFA everywhere
Enforce MFA for legacy, custom, homegrown, and on‑prem applications that don’t natively support it
Close gaps across your identity stack
Unify MFA controls across cloud, on-prem, hybrid, and OT environments.
Comply with MFA requirements
Meet MFA mandates for compliance, cyber insurance, and audit requirements without complex integrations.
Prioritize MFA rollouts
Reduce exposure and drive adoption without the implementation headaches.
Trigger MFA adaptively
Trigger MFA based on anomalous behavior, location, device risk, or asset sensitivity.
Prevent access bypass
And evil-twin tactics by centrally enforcing MFA for all paths.
Preserve automation and workflow continuity
Protect admin interfaces, command-line tools, and orchestration without breaking them.
Critical multi-factor authentication challenges we solve every day.
Apply MFA everywhere
Enforce MFA for legacy, custom, homegrown, and on‑prem applications that don’t natively support it
Close gaps across your identity stack
Unify MFA controls across cloud, on-prem, hybrid, and OT environments.
Comply with MFA requirements
Meet MFA mandates for compliance, cyber insurance, and audit requirements without complex integrations.
Prioritize MFA rollouts
Reduce exposure and drive adoption without the implementation headaches.
Trigger MFA adaptively
Trigger MFA based on anomalous behavior, location, device risk, or asset sensitivity.
Prevent access bypass
And evil-twin tactics by centrally enforcing MFA for all paths.
Preserve automation and workflow continuity
Protect admin interfaces, command-line tools, and orchestration without breaking them.
How Silverfort makes MFA truly universal
From patchwork to pervasive—adaptive, context-driven, and friction-free.
Enforce MFA everywhere
Protect all resources and access interfaces.
Extend MFA to every AD-managed authentication: Kerberos, NTLM, and LDAP flows. Protect resources and access interfaces that don’t natively support MFA without modifying them.
- Homegrown applications
- Legacy systems
- Admin access tools
- File systems and databases
- VPN
- IT infrastructure
- Desktop login
- RDP & SSH
- SaaS applications
- VDI & Citrix


Apply real-time risk policies
Minimize your attack surface and block attacks.
Replace, extend, or consolidate your existing MFA solution
Your environment, your choice.

How Silverfort makes MFA truly universal
From patchwork to pervasive—adaptive, context-driven, and friction-free.
Enforce MFA everywhere
Protect all resources and access interfaces.
Extend MFA to every AD-managed authentication: Kerberos, NTLM, and LDAP flows. Protect resources and access interfaces that don’t natively support MFA without modifying them.
- Homegrown applications
- Legacy systems
- Admin access tools
- File systems and databases
- VPN
- IT infrastructure
- Desktop login
- RDP & SSH
- SaaS applications
- VDI & Citrix

Apply real-time risk policy
Minimize your attack surface and block attacks.
Silverfort combines static rules and risk-based signals (user, device, behavior, asset) to dynamically trigger MFA when it matters, based on Silverfort’s ISPM insights or detected threats by ITDR, in response to changes in users’ and resources’ risk levels.

Replace, extend, or consolidate your existing MFA solution
Your environment, your choice.

Why Silverfort is different
Silverfort extends MFA anywhere to protect the unprotected.
Every access point
Legacy, CLI, OT systems & more.
Real-time, risk-adaptive MFA
Decisions based on user context & detection signals.
No app changes, no agents
Seamless layering.
Unified MFA plane
Across your entire identity ecosystem.
Full coverage
No alternate routes for attackers.
Low-touch rollout
Across hybrid and multi-cloud environments.
Powered by ISPM & ITDR
MFA triggered by ISPM insights and ITDR detections.
Traditional MFA
Coverage
- Only covers apps/systems with built-in MFA support
Every access point
Legacy, CLI, OT systems, and more
Policy intelligence
- Static rules, no context
Real-time, risk-adaptive decisions
Based on user context & detection signals
Deployment effort
- Intrusive changes, agent installs, rewrites or rebuilds
No app changes, no agents
Seamless layering
Architecture
- MFA silos per tool
Unified MFA plane
Across your entire identity ecosystem
Attack surface
- Attackers bypass via unprotected paths
Full coverage
No alternate routes for attackers
Scalability
- Manual integrations, brittle configurations
Low-touch rollout
Across hybrid & multi-cloud environments
Threat response
- Limited or disconnected from detection
Powered by ISPM & ITDR
MFA triggered by ISPM insights & ITDR detections