The Silverfort Identity Security Platform
Secure every dimension of identity.
Leave no one behind. Discover and protect all identities: workforce users, privileged users, third parties, non-human and machine identities, and AI agents—across all environments.
Silverfort connects to your entire IAM infrastructure and secures it from within.
Our platform uses Runtime Access Protection (RAP) technology to seamlessly integrate with your entire IAM infrastructure, delivering end-to-end visibility and inline protection to every identity, everywhere. No more user disruptions. No more system modifications.
All identities
Cover them all: workforce users, privileged users, third parties, non-human and machine identities and AI agents.
All environments
Apply security controls to every corner of your infrastructure: on-prem, OT, hybrid, cloud and multi-cloud.
All resources
Extend protection to every resource, from legacy systems and command-line tools to modern cloud workloads and SaaS apps.
All you need
From complete visibility to exposures and threat analysis. and security controls enforcement in real time—we cover it all.
Runtime Access Protection (RAP)
Operating from within the IAM infrastructure, we see and protect every authentication—so you can finally have peace of mind.
Operating from within the IAM infrastructure, we see and protect every authentication—so you can finally have peace of mind.
Operating from within the IAM infrastructure, we see and protect every authentication—so you can finally have peace of mind.
Operating from within the IAM infrastructure, we see and protect every authentication—so you can finally have peace of mind.
Operating from within the IAM infrastructure, we see and protect every authentication—so you can finally have peace of mind.

The Silverfort Identity Security Platform
Discover exposures, analyze threats and enforce security controls in real time with Runtime Access Protection (RAP).
Explore the Silverfort Identity Security Platform
Finally, the identity security platform you deserve. End-to-end visibility and protection when it matters most.
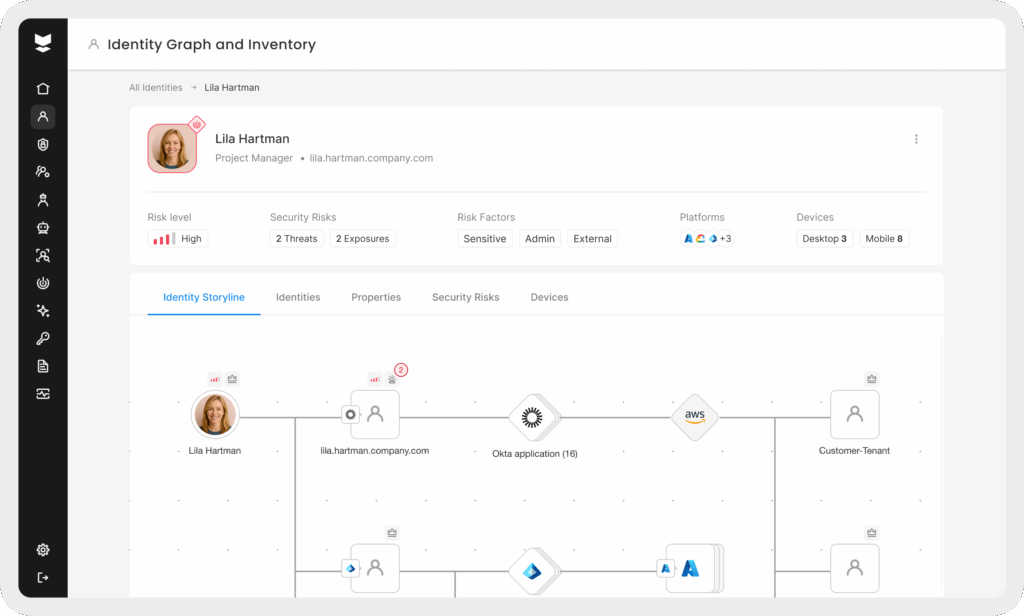
Stop identity threats without slowing the business.
Stop identity threats in real time
Smart decision-making based on context and risk analysis.
Enforce unified policies everywhere
One flexible, granular control layer for security & compliance.
Deploy fast, get value faster
Easy implementation and onboarding with proven ROI.
No disruptions and overhead
No proxies, no app changes, no user friction or workflow modifications.
Scale without limits
Designed to support any user, system, or environment, at any size or scope.
Complete visibility
Across your entire environment from legacy to cloud.
Complete visibility
Deploy fast, get value faster
Stop identity threats — in real time
Enforce unified policies everywhere
No disruptions and overhead
How can we help you boost security while cutting costs?
Cost saving & efficiency
Fix compliance gaps early
Stay audit-ready and avoid costly surprises.
Lower cyber insurance premiums
Meet insurer requirements and cut coverage costs.
Consolidate tools, simplify ops
Fewer point solutions, faster rollouts, smoother ops.
Modernize without ripping and replacing
Bring legacy systems & AD to today’s standards.
Reduce overhead with one platform
Streamline management, free up security resources.
Resize and reduce unnecessary resources
Identify and decommission unused resources and licenses.
Improve Active Directory hygiene
Reduce the load on AD by 20-40% with authentication hygiene.
Accelerated security
Reduce security risks
Protect critical systems and data with Zero Trust architecture.
Secure complex environments
Support cloud migration, M&A, and other strategic IT moves.
Resolve red team findings
Close security gaps and show measurable progress.
Enable safe AI adoption
Use AI tools and agents securely with the right guardrails.
Stop and contain attacks
Block lateral movement, contain breaches, and prevent attacker re-entry.


