Protect privileged access at scale—instantly and completely.
Secure privileged access beyond the vault with less effort, less cost, and less operational overhead. Discover, classify, and enforce Least Privilege and Just-In-Time (JIT) access policies for all your privileged identities—at scale and within days.
- Find all privileged users—even unknowns.
- Enforce Least Privilege & Just-in-Time (JIT) policies.
- Deploy rapidly across all environments.
Protect privileged access at scale—instantly and completely.
Secure privileged access beyond the vault with less effort, less cost, and less operational overhead. Discover, classify, and enforce Least Privilege and Just-In-Time (JIT) access policies for all your privileged identities—at scale and within days.
- Find all privileged users—even unknowns.
- Enforce Least Privilege & Just-in-Time (JIT) policies.
- Deploy rapidly across all environments.
PAM drains time and budget without closing the gap.
Privileged access now extends far beyond domain admins to service accounts, cloud admins, AI agents, and more—often with standing privileges. Traditional PAM tools were built for compliance, not for securing organizations at this scale. They only protect a fraction of what matters, and too many rollouts stall or never finish at all.
Narrow scope
Traditional PAM only covers a small subset of your most privileged accounts (aka Tier-0), leaving exploitable gaps.
Slow, complex and costly
PAM onboardings drag on for years and drain resources, with low time-to-value.
High friction, low adoption
Vault complexity leads teams to bypass controls and leave gaps behind.
False sense of security
Credentials can be vaulted, but privileges remain, lateral movement goes unchecked, and attack paths stay open.
PAM drains time and budget without closing the gap.
Privileged access now extends far beyond domain admins to service accounts, cloud admins, AI agents, and more—often with standing privileges. Traditional PAM tools were built for compliance, not for securing organizations at this scale. They only protect a fraction of what matters, and too many rollouts stall or never finish at all.
Narrow scope
Traditional PAM only covers a small subset of your most privileged accounts (aka Tier-0), leaving exploitable gaps.
Slow, complex and costly
PAM onboardings drag on for years and drain resources, with low time-to-value.
High friction, low adoption
Vault complexity leads teams to bypass controls and leave gaps behind.
False sense of security
Credentials can be vaulted, but privileges remain, lateral movement goes unchecked, and attack paths stay open.
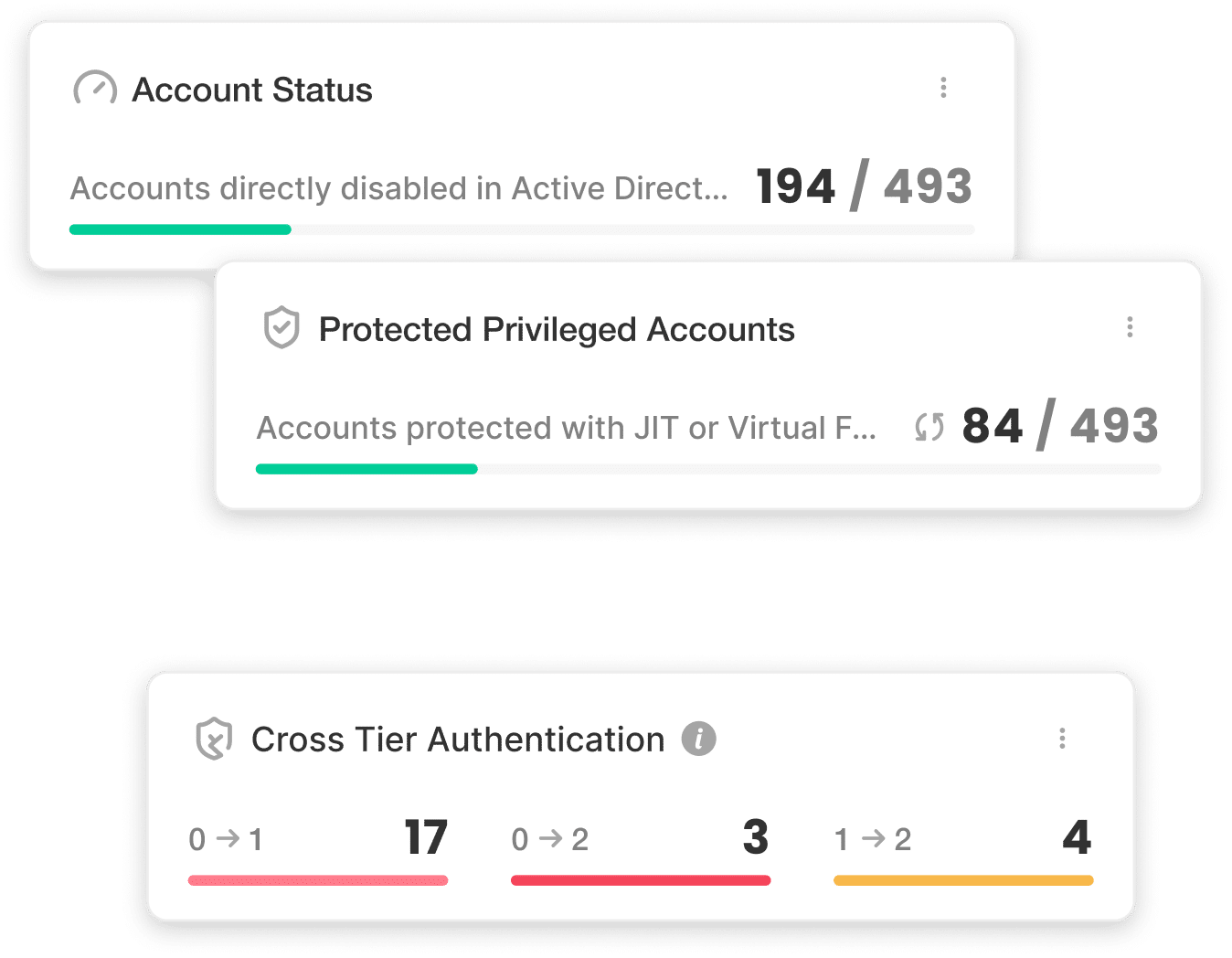
Protect every privileged access with Silverfort Privileged Access Security
Full privilege coverage. Zero manual effort. Live in days. Operating from within your IAM layer, our patented technology discovers, classifies, and protects privileged accounts end-to-end. Silverfort PAS delivers full, efficient protection for every privileged access in real time.
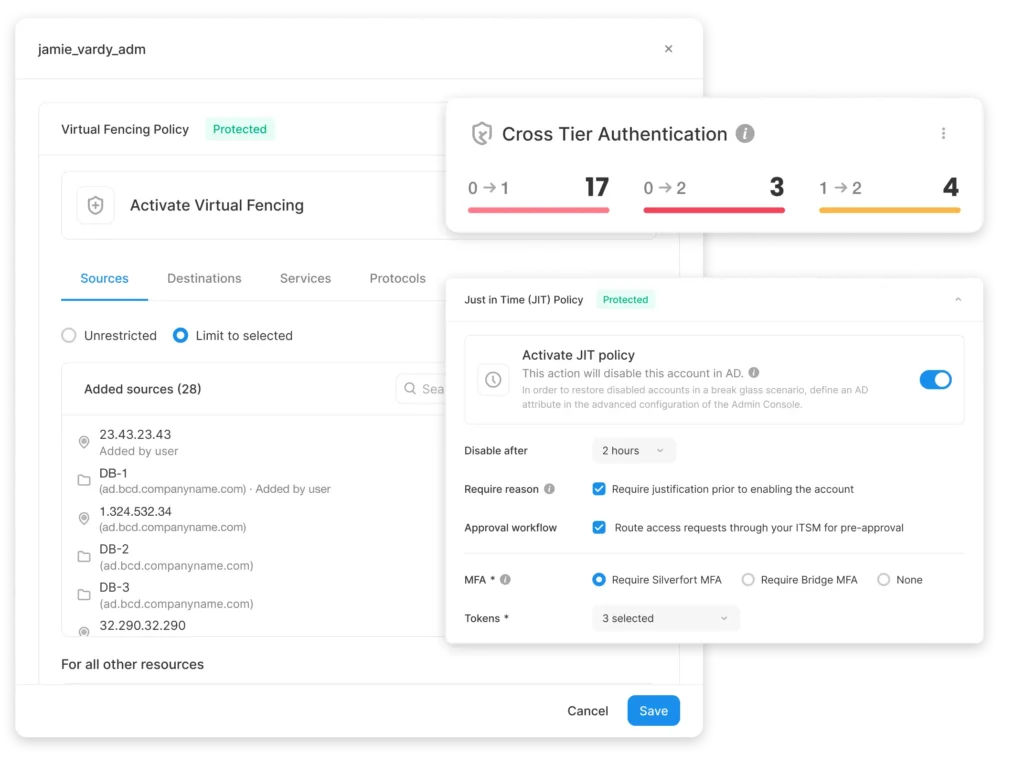
Automated discovery & controls
Continuously map all privileged accounts based on real access behavior and grant access rights only when and to what’s necessary.
Continuous protection at scale
Extend virtual fencing, least privilege, and Just-in-Time (JIT) access to every privileged identity, with unified real-time enforcement.
Rapid deployment, unlock ROI
Deploy rapidly and seamlessly into existing environments with capped expenses, accelerating ROI and time-to-value.
We've got you covered, whether a vault exists or not
Silverfort's Privileged Access Security is at the heart of our Vaultless PAM offering, designed to build resilience directly into your environment. With the full Silverfort platform, you get scalable protection and measurable risk reduction across all privileged identities.
Already invested in traditional PAM?
Silverfort helps you complete and extend the PAM journey.
Not yet started your PAM journey?
Silverfort delivers full protection without the operational headaches PAM usually brings.

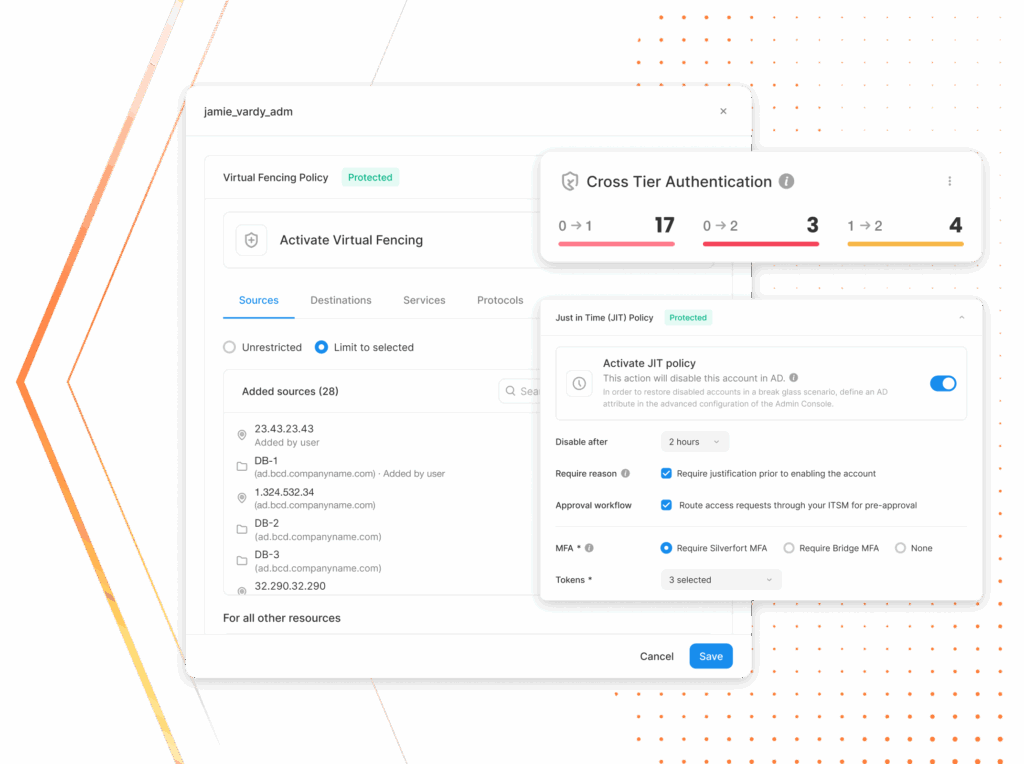
How Silverfort scales privileged access protection across the entire organization
From frustration to full control—easy, fast, and complete.
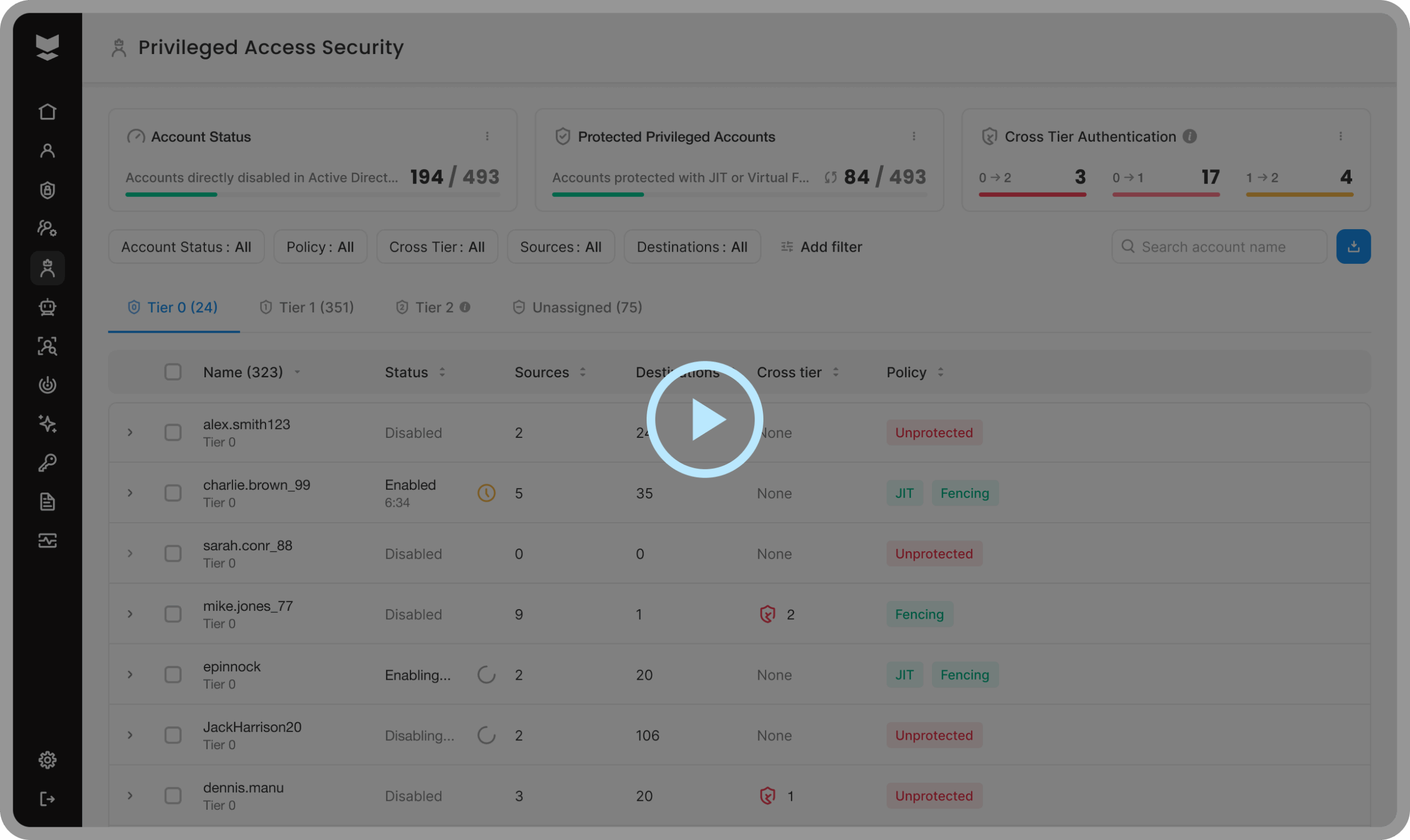
Discover every privileged identity
Expose the entire scope of privileges—not just what PAM knows about.
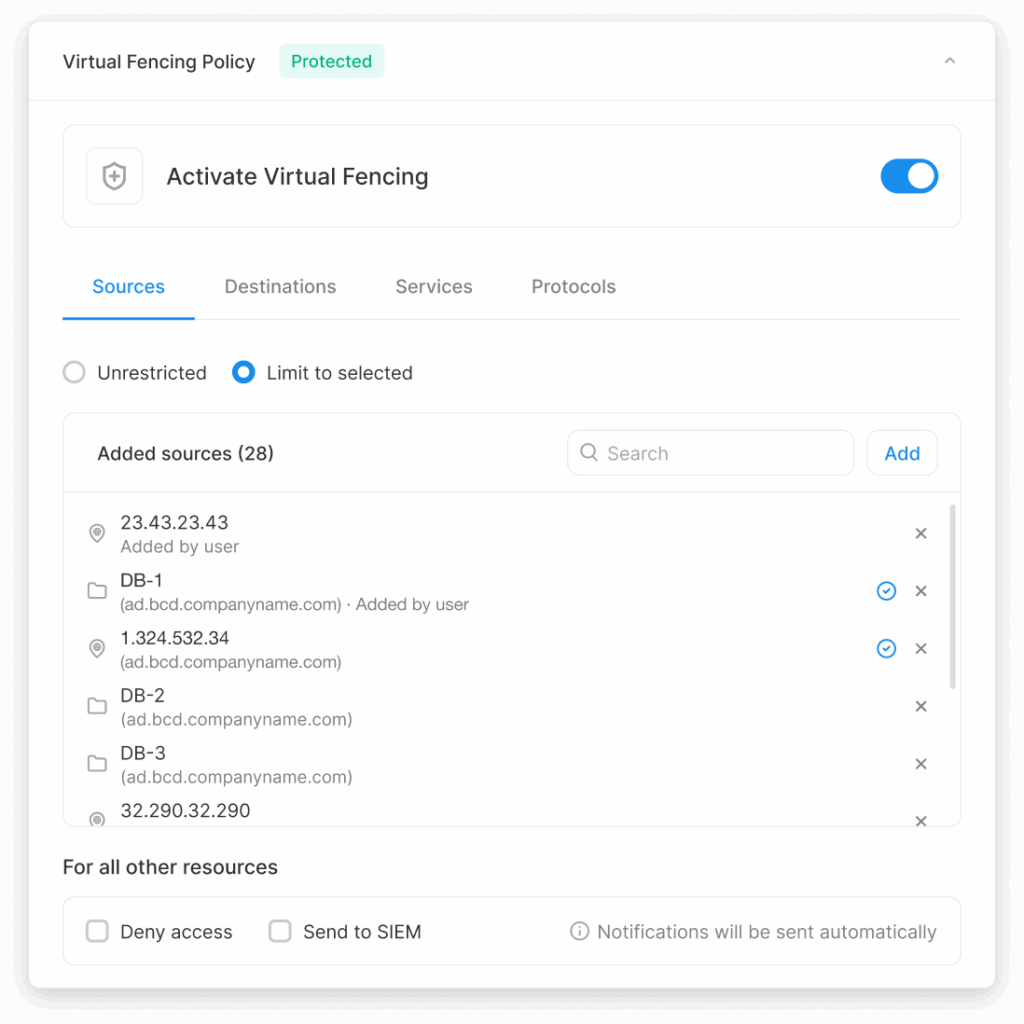
Protect with virtual fencing
Make privilege usable only where it’s safe.
Limit access only to its intended purpose—by source, protocol, or destination to stop misuse, privilege escalation, and lateral movement in real time.
Eliminate standing privilege and attack paths
Mitigate risks across your entire environment—even in places PAM can't reach.
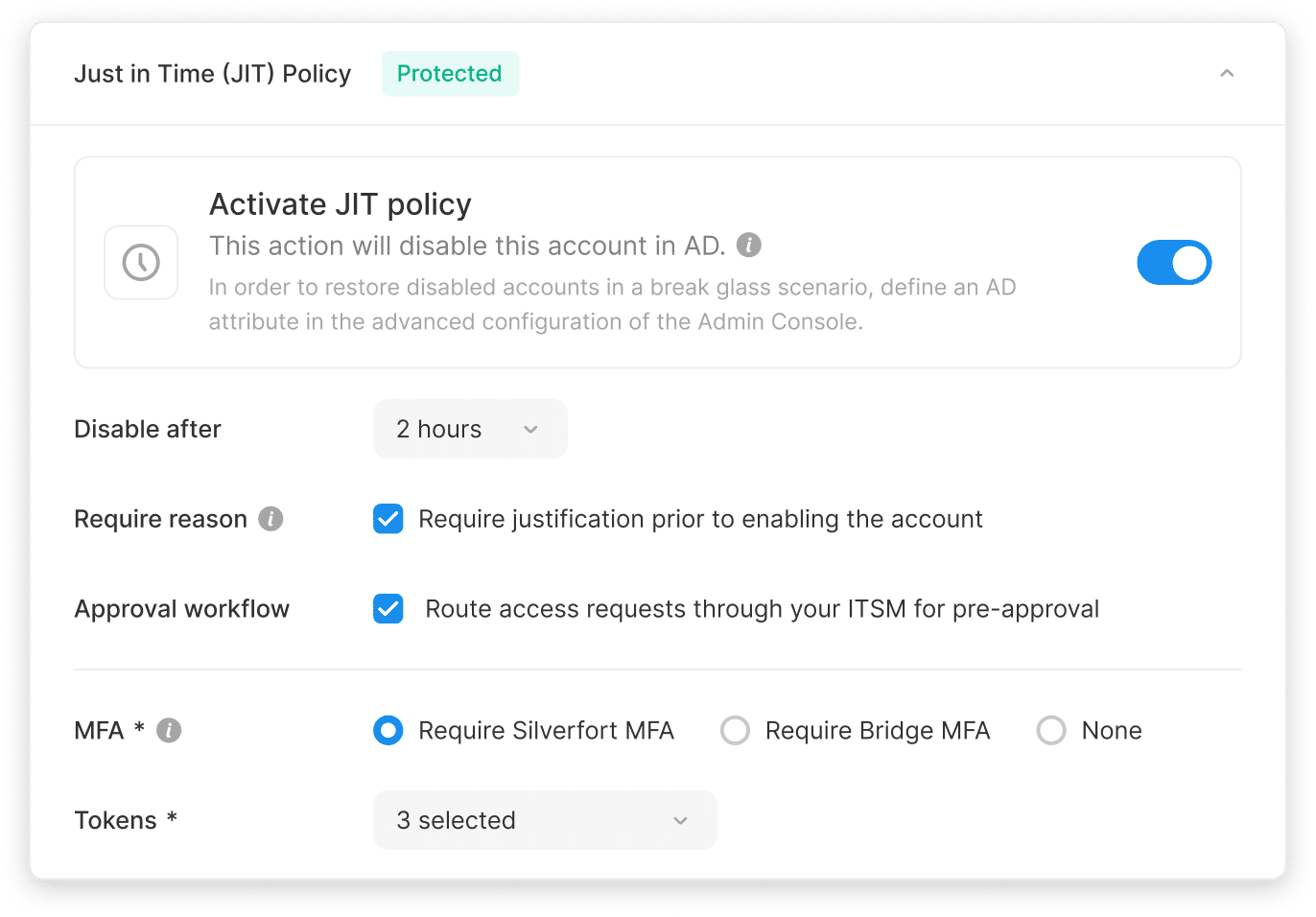
Enforce Just-in-Time (JIT) and least privilege access policies thanks to Silverfort’s unique inline technology, and achieve Zero Standing Privileges (ZSP). Remove persistent access and block hidden escalation paths. Frictionlessly and at scale, without deploying vaults or proxies.
How Silverfort solves one of the biggest identity security challenges
From frustration to full control—efficient, continuous and complete
Discover every privileged identity
Expose the entire scope of privileges—not just what PAM knows about.

Protect with virtual fencing
Make privilege usable only where it’s safe.
Limit access only to its intended purpose—by source, protocol, or destination to stop misuse, privilege escalation, and lateral movement in real time.

Eliminate standing privilege and attack paths
Mitigate risks across your entire environment—even in places PAM can't reach.

Critical privileged access challenges we solve every day
Lock down privileged access at scale
Including unmanaged users and service accounts that PAM can’t see.
Enforce JIT and least privileged access
For domain admins during critical operations.
Stop privilege escalation and lateral movement
Virtually fencing all sensitive tiers to stop attackers in their tracks.
Eliminate standing privilege enterprise-wide
Across on-prem, cloud, and hybrid environments without slowing operations.
Meet regulatory requirements for privileged access
Enforce audit-ready controls to comply with industry standards and frameworks.
Critical privileged access challenges we solve every day
Lock down privileged access at scale
Including unmanaged users and service accounts that PAM can’t see.
Enforce JIT and least privileged access
For domain admins during critical operations.
Stop privilege escalation and lateral movement
Virtually fencing all sensitive tiers to stop attackers in their tracks.
Eliminate standing privilege enterprise-wide
Across on-prem, cloud, and hybrid environments without slowing operations.
Meet regulatory requirements for privileged access
Enforce audit-ready controls to comply with industry standards and frameworks.
How Silverfort Privileged Access Security maps, fences, and protects all privileged identities instantly.
Why Silverfort is different
Traditional PAM doesn’t cut it anymore. Silverfort closes the gaps it leaves behind.
Beyond the vault
Every privileged access secured, automatically and continuously.
Complete coverage
Human users, service accounts, and AI agents.
All tiers
Protection across every privileged level at scale.
No frictions or delays
Fast, simple, cost-effective rollout with high ROI.
Inline enforcement
Every privileged access request validated in real time.
Traditional PAM
Account coverage
- Only secures some privileged accounts, mostly tier-0
Every privileged access, at any sensitivity and any tier, secured, automatically and continuously
Identity types
- Focuses mainly on human users (domain and cloud admins)
Complete coverage: human users, service accounts, and AI agents
Tier scope
- Limited to Tier-0 domain admins
All tiers; protection across every privileged level at scale
Deployment
- Heavy deployments, very slow rollout
No frictions or delays—fast, simple, cost-effective rollout with high ROI
Access enforcement
- Focus on credential vaulting and session brokering/proxying
Adaptive access policies and inline enforcement at runtime; every privileged access request validated in real time
License utilization and ROI
- Low utilization due to operational complexity and selective onboarding of accounts
Broad coverage drives full utilization, faster time to value, and measurable cost reduction