Every non-human identity—in sight and under control
Silverfort continuously discovers, contextualizes, and enforces access policies across all NHIs at scale and without disruption.
- Automatically discover every NHI in your environments.
- Map their activities and establish baselines.
- Enforce control and fence activity.
Every non-human identity—in sight and under control
Silverfort continuously discovers, contextualizes, and enforces access policies across all NHIs at scale and without disruption.
- Automatically discover every NHI in your environments.
- Map their activities and establish baselines.
- Enforce control and fence their activity.
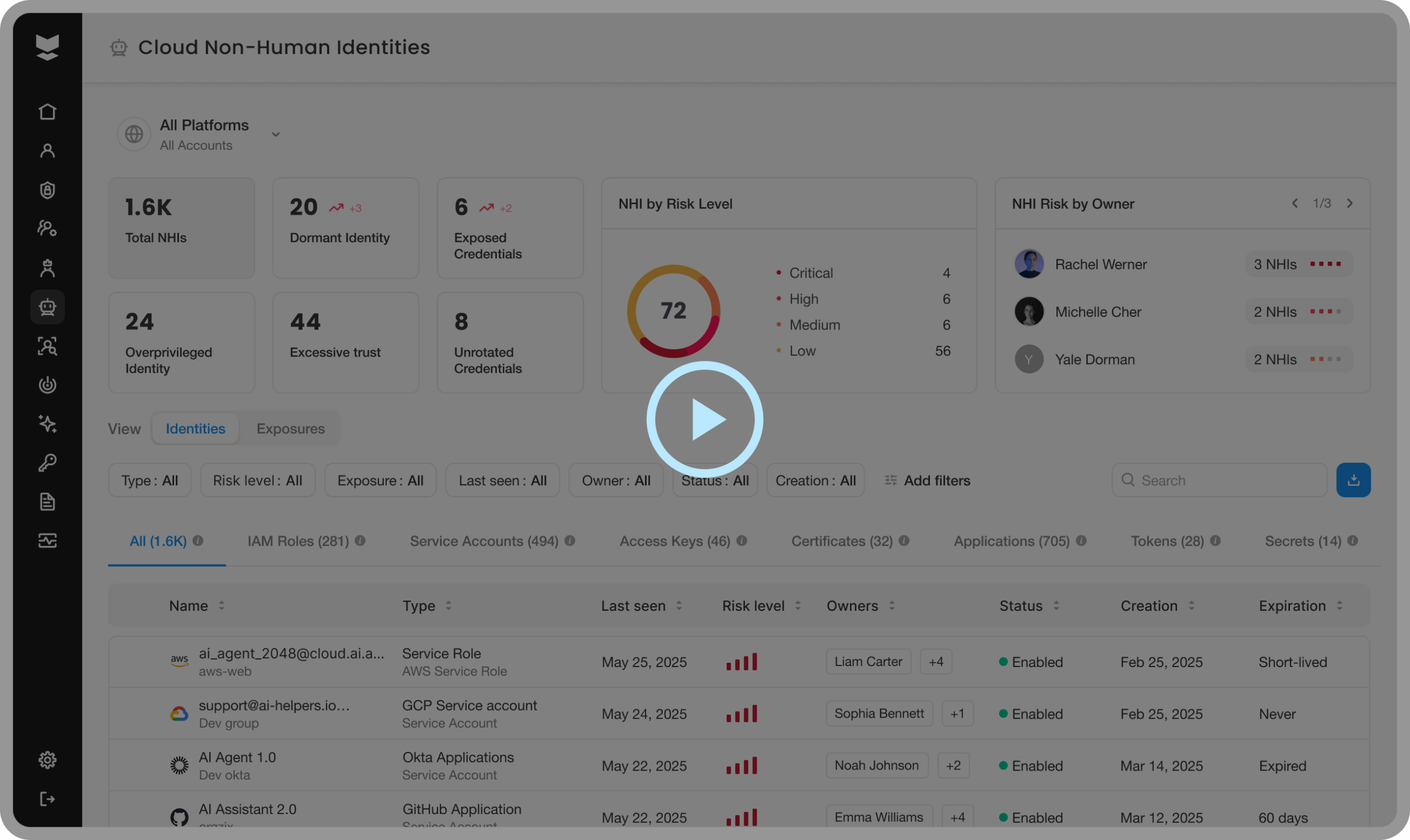
It's easy to underestimate your NHI risk.
Service accounts are just the beginning. The non-human identity (NHI) layer spans machine identities, automation scripts, cloud workloads, tokens, keys, and more. These identities operate 24/7, often with persistent, excessive access, and they rarely fall under PAM or MFA protection. Traditional tools can’t discover or control most of them—which is why attackers target them.
Blind spots everywhere
IAM and PAM don’t monitor most non-human access, allowing silent movement across environments.
Too many, too complex
NHIs are often created and decommissioned dynamically, with no central inventory or consistent tagging.
No real enforcement
Without behavioral baselines or policy enforcement, excessive privileges and anomalies go unaddressed.
Your NHI risk is (probably) underestimated.
Service accounts are just the beginning. The non-human identity (NHI) layer spans machine identities, automation scripts, cloud workloads, tokens, keys, and more. These identities operate 24/7, often with persistent, excessive access, and they rarely fall under PAM or MFA protection. Traditional tools can’t discover or control most of them—which is why attackers target them.
Blind spots everywhere
IAM and PAM don’t monitor most non-human access, allowing silent movement across environments.
Too many, too complex
NHIs are often created and decommissioned dynamically, with no central inventory or consistent tagging,
No real enforcement
Without behavioral baselines or policy enforcement, excessive privileges and anomalies go unaddressed.
From invisible identities to visible protection.
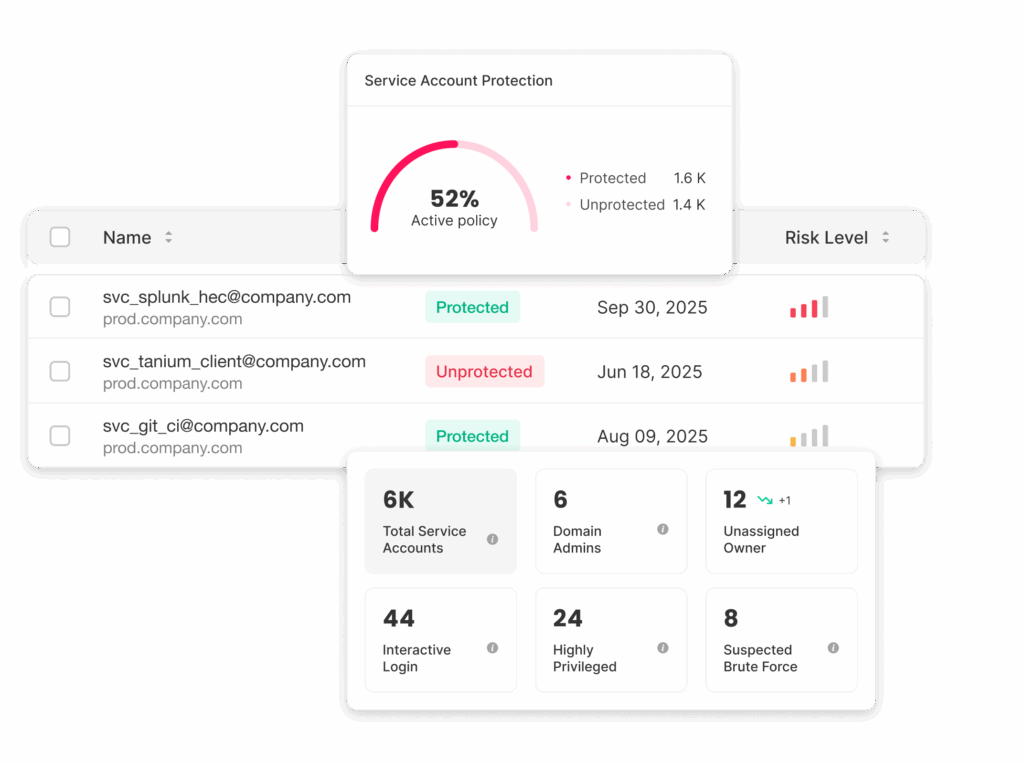
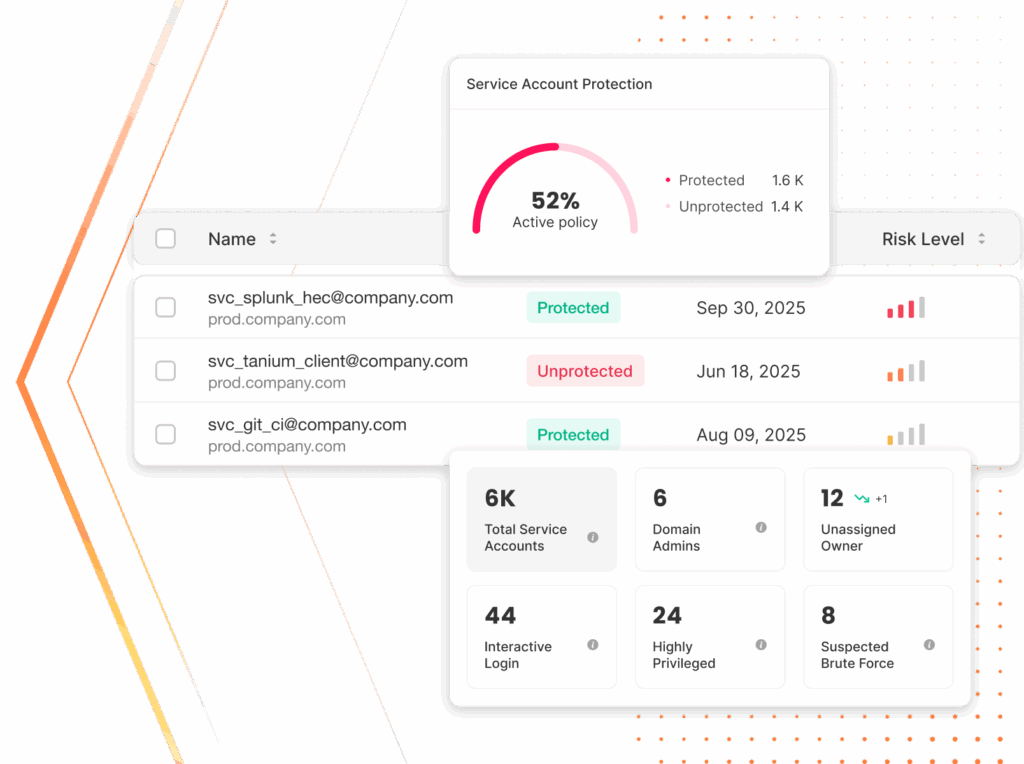
Full NHI control without breaking a thing. Silverfort automatically discovers and secures every service account and NHI—even unmanaged, unknown, or unvaulted ones—without disrupting critical processes or breaking automation.
Automated and complete discovery
Uncover all NHIs and their access behavior. Turn shadow accounts into visible, managed assets by mapping human owners, sources, destinations, privilege levels, and associated risks.
Continuous protection at scale
Enforce adaptive policies and virtual fences for service accounts based on how they actually behave. Lock down access patterns, detect anomalies, and block deviations in real time.
Stronger protection, zero disruption
Achieve lasting confidence in your security for even the most complex environments. Prevent lateral movement, ransomware spread, and privilege misuse while ensuring stability and business agility.
How Silverfort protects service accounts and NHIs at any scale or complexity
From blind spots to full protection—autonomous, continuous, complete.
Discover every NHI
Uncover the full scope of non-human identity activity.
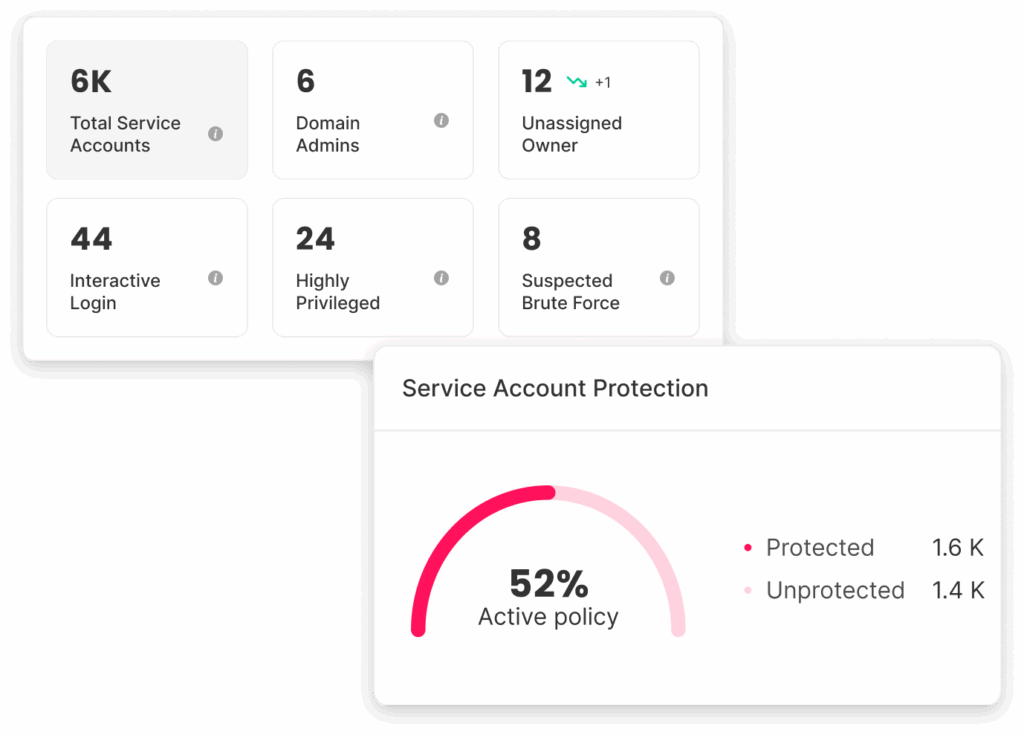
Silverfort continuously discovers and maps all AD service accounts and cloud NHIs, delivering granular visibility and insights into their activities, risk indicators, and usage patterns based on real access telemetry.
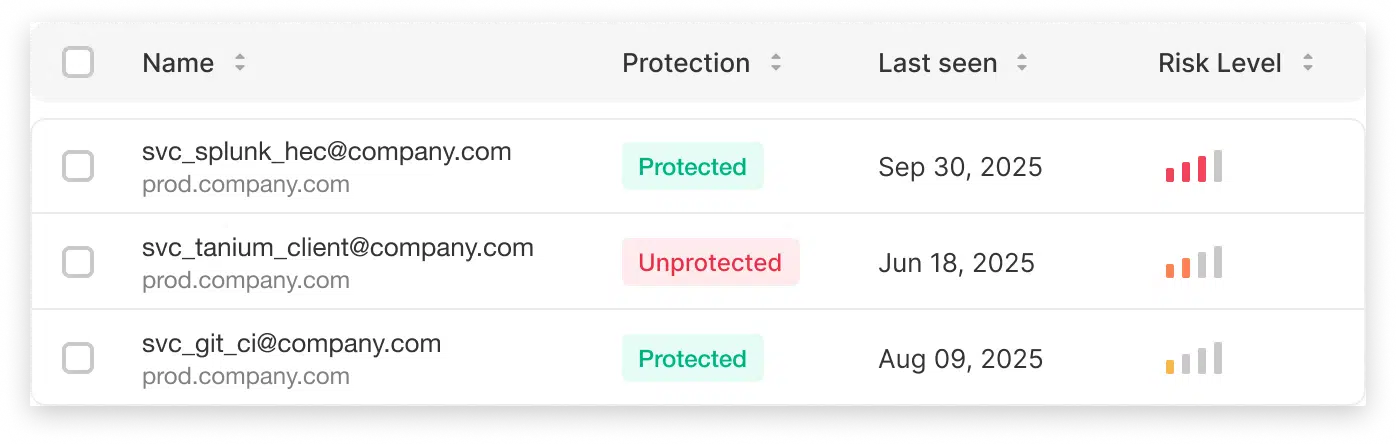
Understand and control behavior
Baseline every service account’s behavior.
Silverfort automatically builds a behavioral baseline for each service account, learning its usual access paths, privileges, and frequency of activity. It scores predictability and detects anomalies such as new hosts, unusual destinations, or sudden privilege elevation. During this learning phase, policies run in “alert only” mode, offering visibility without disrupting critical automations. This creates a behavioral fingerprint for every service account, enabling precise, context-aware protection.
Enforce inline, real-time policies—without breaking automation
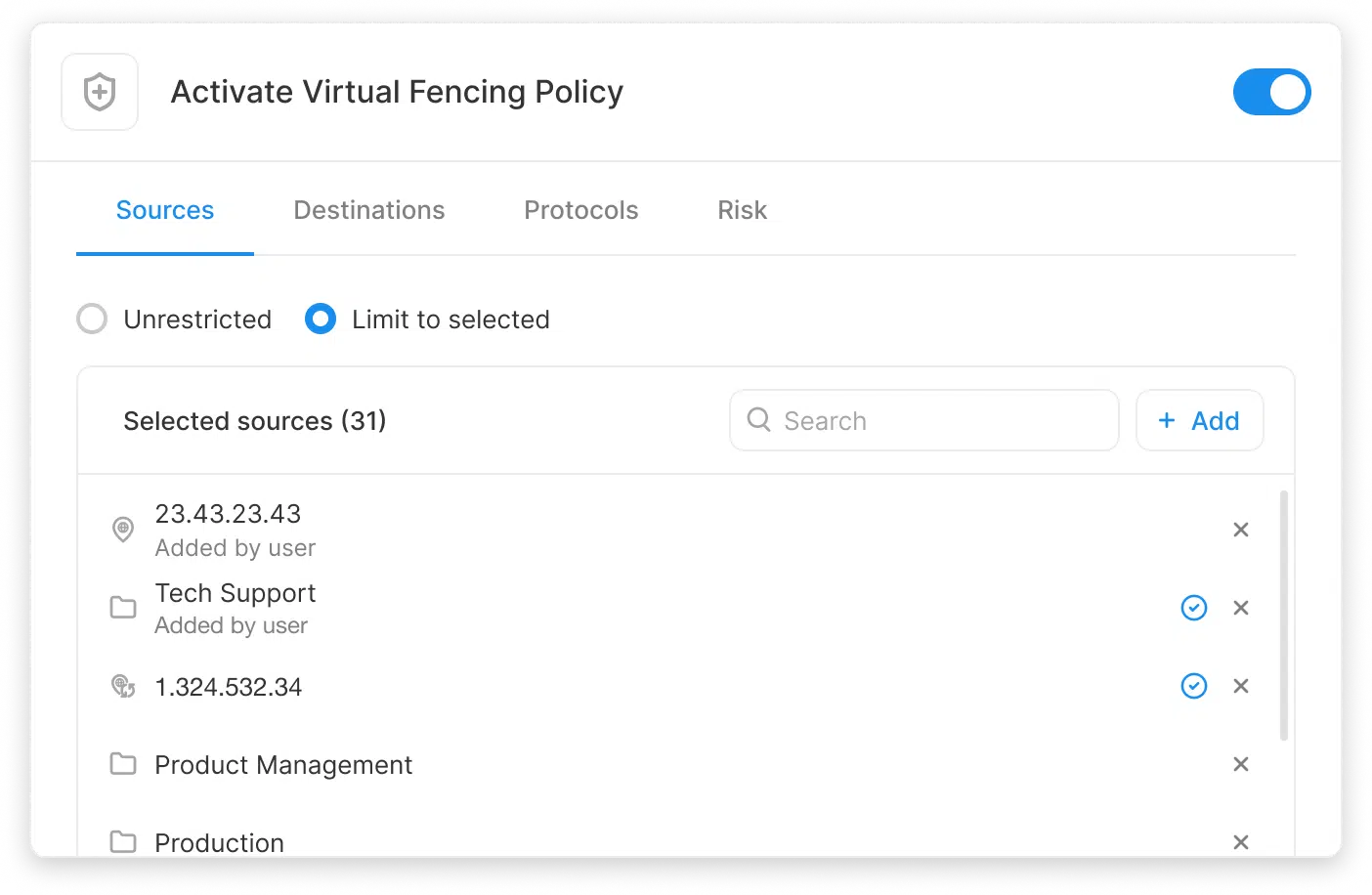
Apply virtual fences and adaptive policies to block compromise.
Once baselines mature, Silverfort enforces adaptive policies that lock down activity and permit only expected behavior for each service account. These real-time controls act like virtual fences, automatically blocking abnormal activity—such as unexpected source or destination, or lateral movement attempts—without disrupting legitimate processes. Least Privilege can become dynamic and self-adjusting, keeping automation safe while preventing misuse, ransomware spread, and privilege abuse.
How Silverfort protects service accounts and NHIs at any scale or complexity
From blind spots to full protection—autonomous, continuous, complete.
Discover every NHI
Uncover the full scope of non-human identity activity.
Silverfort continuously discovers and maps all AD service accounts and cloud NHIs for granular visibility and insights into their activities, risk indicators, and usage patterns.

Understand and control behavior
Baseline every service account’s behavior.
Silverfort automatically builds a behavioral baseline for each service account, learning its usual access paths, privileges, and frequency of activity. It scores predictability and detects anomalies such as new hosts, unusual destinations, or sudden privilege elevation. During this learning phase, policies run in “alert only” mode, offering visibility without disrupting critical automations. This creates a behavioral fingerprint for every service account, enabling precise, context-aware protection.

Enforce inline, real-time policies—without breaking automation
Apply virtual fences and adaptive policies to block compromise.
Once baselines mature, Silverfort enforces adaptive policies that lock down activity and permit only expected behavior for each service account. These real-time controls act like virtual fences, automatically blocking abnormal activity—such as unexpected source or destination, or lateral movement attempts—without disrupting legitimate processes. Least Privilege can become dynamic and self-adjusting, keeping automation safe while preventing misuse, ransomware spread, and privilege abuse.

Service accounts are a security nightmare because you can’t put MFA on them. Silverfort was able to protect what no one else can. Of the security tools that we use, Silverfort has a very high return on investment.

Tom Parker
VP of IT & CISO, Kayak
Service accounts are a security nightmare because you can’t put MFA on them. Silverfort was able to protect what no one else can. Of the security tools that we use, Silverfort has a very high return on investment.

Tom Parker
VP of IT & CISO, Kayak
Critical NHI challenges we solve every day
Automatically discover every non-human identity
Including unmanaged and unvaulted service accounts, tokens, and workloads.
Eliminate blind spots in your identity perimeter
With full visibility into non-human access across on-prem, cloud, hybrid, and AI-powered systems.
Prioritize remediation efforts
Such as risk-based context for every NHI to build a remediation strategy that minimizes your attack surface and aligns with your security and operational needs.
Detect and stop abnormal activity
Like privilege escalation or lateral movement, with real-time behavioral enforcement.
Prevent abuse of over-privileged accounts
By enforcing Least Privilege and Just-in-Time access without changing how services run.
Secure automation and DevOps processes
Without disrupting workflows, breaking scripts, or halting services.
Critical NHI challenges we solve every day
Automatically discover every non-human identity
Including unmanaged and unvaulted service accounts, tokens, and workloads.
Eliminate blind spots in your identity perimeter
With full visibility into non-human access across on-prem, cloud, hybrid, and AI-powered systems.
Prioritize remediation efforts
Such as risk-based context for every NHI to build a remediation strategy that minimizes your attack surface and aligns with your security and operational needs.
Detect and stop abnormal activity
Like privilege escalation or lateral movement, with real-time behavioral enforcement.
Prevent abuse of over-privileged accounts
By enforcing Least Privilege and Just-in-Time access without changing how services run.
Secure automation and DevOps processes
Without disrupting workflows, breaking scripts, or halting services.
Why Silverfort is different
Traditional IAM and PAM weren’t designed for modern NHI risk. Silverfort closes that gap.
Complete coverage
Across cloud, on-prem, hybrid and AI agents
Low-touch rollout
That scales across all identities and environments
Inline enforcement with patented RAP technology
Enabling virtual fencing to block threats instantly
Adaptive policies and enforcement
Based on real-time identity behavior
Non-intrusive protection
With minimal operational impact
Traditional tools
NHI-focused startups
Coverage
- Siloed and partial
- Cloud and SaaS focused
Complete coverage
Across cloud, on-prem, hybrid and AI agents
Scalability
- Manual setup, brittle rules
- Mostly auto-discovery, some tuning required
Low-touch rollout
That scales across all identities and environments
Real-time protection
- Static policies, alert-based, no real-time protection
- Detection-first, remediation later
Inline enforcement
With patented RAP technology, enabling virtual fencing to block threats instantly
Behavior awareness
- Predefined, static rules
- Reactive anomaly detection
Adaptive policies & enforcement
Based on real-time identity behavior
Disruption risk
- High (breaks workflows)
- Varies
Non-intrusive protection
Minimal operational impact