Find, fix, and fortify every identity weakness everywhere
You can't protect yourself from the risks you can't see. Silverfort uncovers the weaknesses that expose your hybrid environment to identity threats—then helps you mitigate them.
- Find misconfigurations, insecure settings, and exposures
- Resolve them to mitigate your risk and build resilience.
- Scale across your entire hybrid environment.
Find, fix, and fortify every identity weakness everywhere
You can't protect yourself from the risks you can't see. Silverfort uncovers the weaknesses that expose your hybrid environment to identity threats—then helps you mitigate them.
- Find misconfigurations, insecure settings, and exposures
- Resolve them to mitigate your risk and build resilience.
- Scale across your entire hybrid environment.
Identity weaknesses are hiding in plain sight.
Security gaps in identity aren’t exotic—they’re mundane: legacy protocols, misconfigured settings, stale accounts, shadow admins. Attackers exploit them as stepping stones.
Hidden weaknesses everywhere
Misconfigurations in AD, cloud IdPs, legacy authentication modes remain undetected by traditional tools.
Scaling complexity
Hybrid environments with on‑prem and cloud identities introduce gaps at the seams—where attacks often traverse.
Manual remediation fatigue
Security teams are overwhelmed. Patching identity exposures often requires tedious audits, scripts, and guesswork.
Reactive posture is an opportunity for attackers
If posture isn’t continuously assessed and hardened, attackers will find the weak link.
Identity weaknesses are hiding in plain sight.
Security gaps in identity aren’t exotic—they’re mundane: legacy protocols, misconfigured settings, stale accounts, shadow admins. Attackers exploit them as stepping stones.
Hidden weaknesses everywhere
Misconfigurations in AD, cloud IdPs, legacy authentication modes remain undetected by traditional tools.
Scaling complexity
Hybrid environments with on‑prem and cloud identities introduce gaps at the seams - where attacks often traverse.
Manual remediation fatigue
Security teams are overwhelmed. Patching identity exposures often requires tedious audits, scripts, and guesswork.
Reactive posture is an opportunity for attackers
If posture isn’t continuously assessed and hardened, attackers will find the weak link.
From passive monitoring to proactive resilience
Intelligent posture management that completes your identity defense stack.
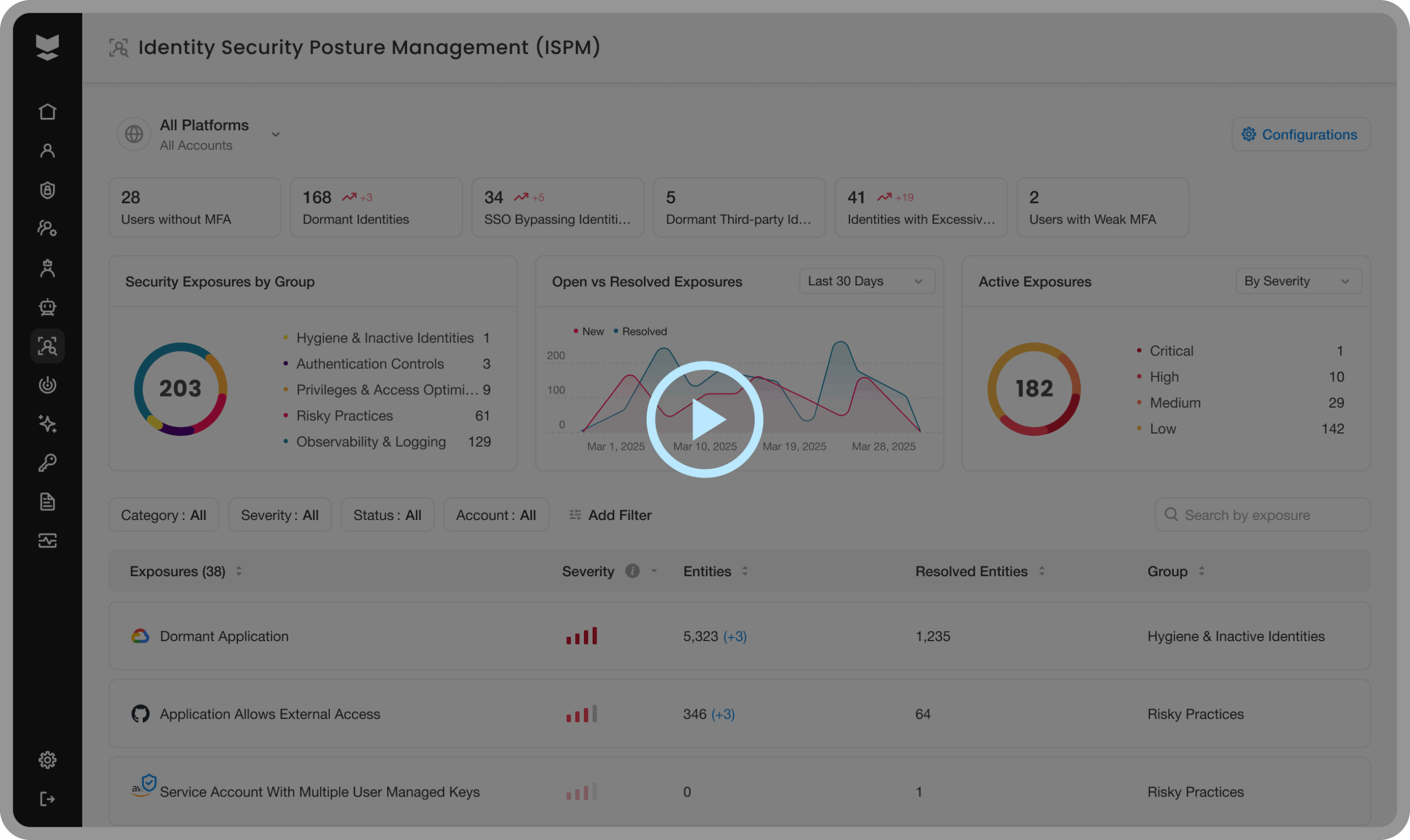
Comprehensive identity gap discovery
Automatically detect risks and exposures (misconfigurations, legacy settings, insecure protocols and more) across on-prem, cloud and hybrid environments.
Prioritized risk insights & recommendations
Evaluate exposures to guide remediation focus and get expert recommendations for mitigating associated risks.
Continuous posture hardening
Monitor, track, and evaluate your identity security posture as your environment evolves.
Critical ISPM challenges we solve every day
Mitigate risk from legacy protocols
Identify and resolve exposure caused by legacy authentication protocols (e.g. NTLMv1 usage, weak LDAP)
Eliminate shadow admins
Detect and remove unintentional admin privileges and shadow admin accounts
Spot stale and orphaned accounts
Improve hygiene and reduce attack surface by identifying stale and orphaned accounts
Continuous risk scoring
Prioritize remediation of critical exposures with continuous risk scoring
Take action against risk
Enforce MFA or authentication firewall rules where identity risk is too high
Critical ISPM challenges we solve every day
Mitigate risk from legacy protocols
Identify and resolve exposure caused by legacy authentication protocols (e.g. NTLMv1 usage, weak LDAP)
Eliminate shadow admins
Detect and remove unintentional admin privileges and shadow admin accounts
Spot stale and orphaned accounts
Improve hygiene and reduce attack surface by identifying stale and orphaned accounts
Continuous risk scoring
Prioritize remediation of critical exposures with continuous risk scoring
Take action against risk
Enforce MFA or authentication firewall rules where identity risk is too high
How Silverfort elevates your identity security posture.
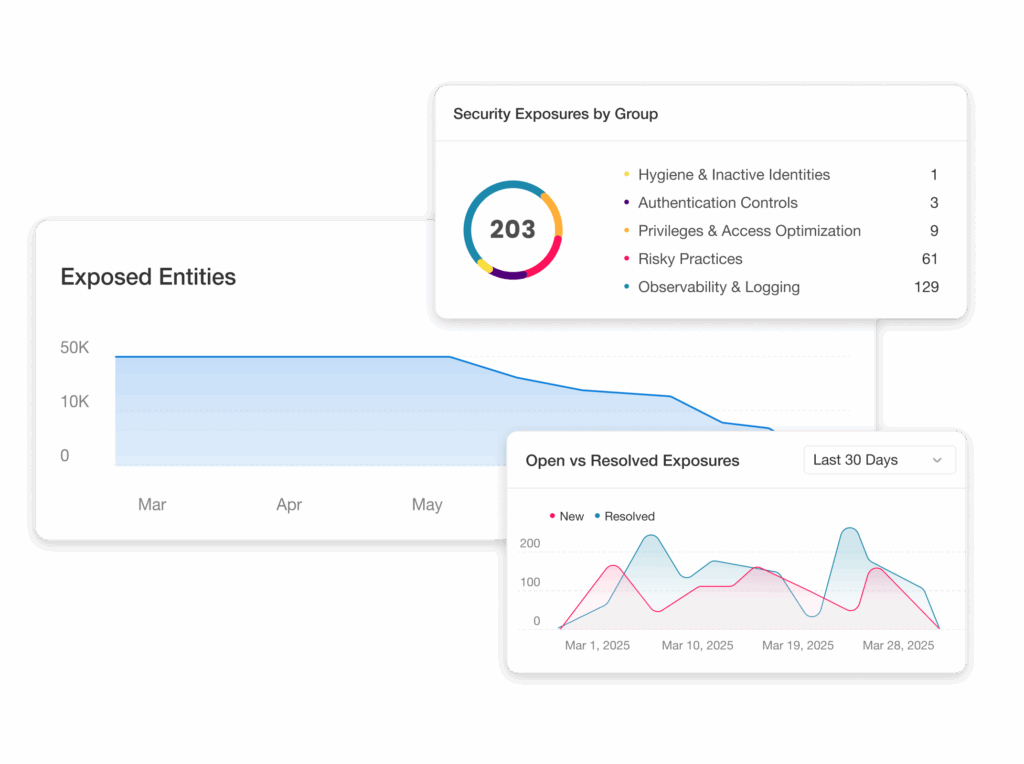
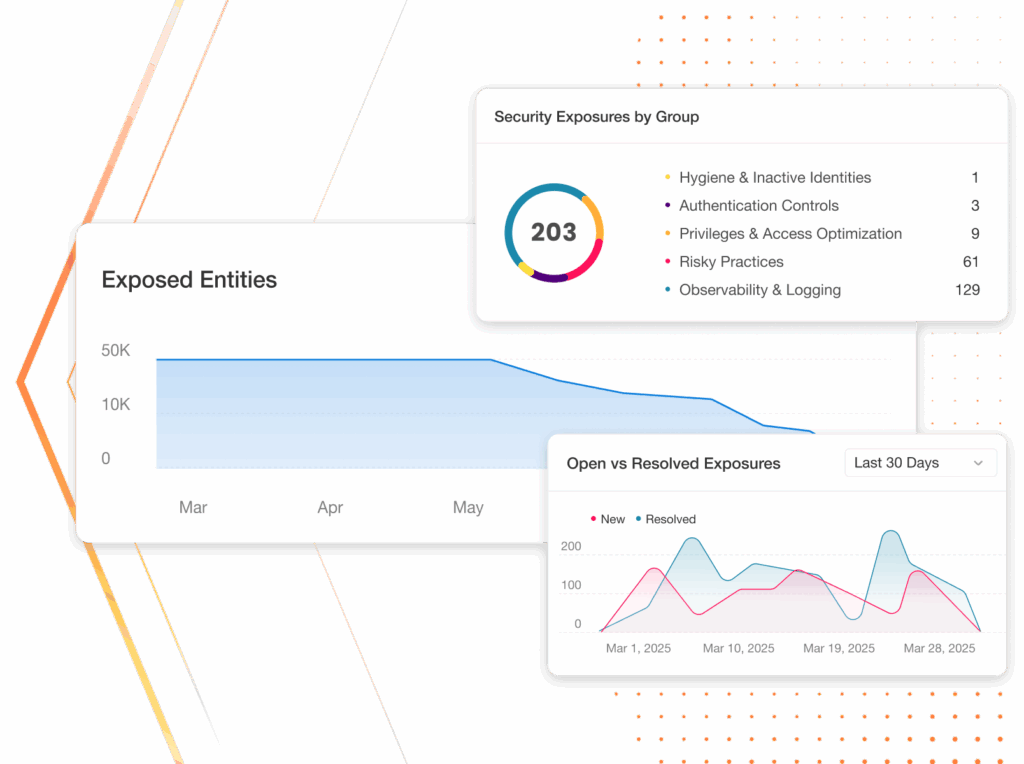
Discover all exposure points
Informed by a holistic view of your systems and infrastructure, Silverfort reveals misconfigurations, legacy protocols, shadow admins, stale accounts, sync issues, and more across all environments.
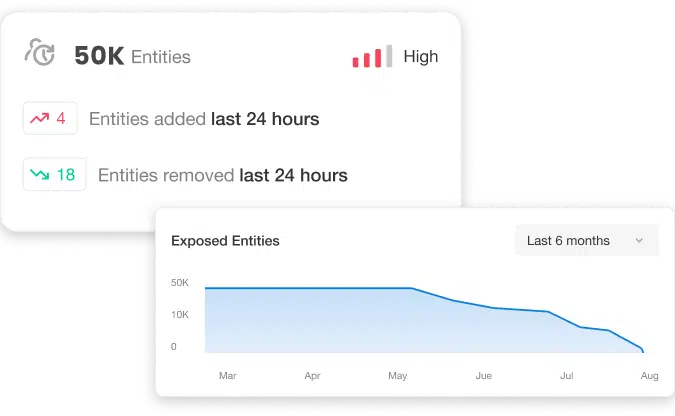

Assess and score threat exposure
Mitigate effectively
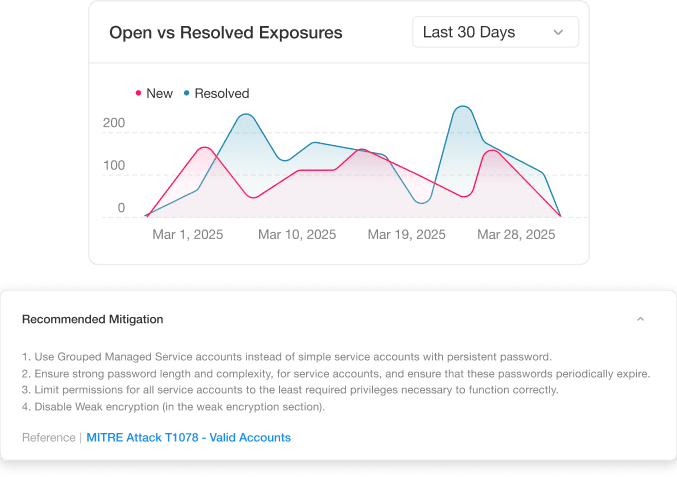
Take action with clear guidance and automated playbooks. Silverfort translates findings into specific steps—from disabling risky protocols and removing shadow admins to enforcing MFA and tightening permissions—so you can close gaps quickly without guesswork or disruption.
How Silverfort elevates your identity security posture.
Discover all exposure points
Informed by a holistic view of your systems and infrastructure, Silverfort reveals misconfigurations, legacy protocols, shadow admins, stale accounts, sync issues, and more across all environments.

Assess and score threat exposure
Silverfort applies a scoring model based on probability and business impact. This ranking helps you focus on exposures that matter most (not just the noisy ones).

Mitigate effectively
Take action with clear guidance and automated playbooks. Silverfort translates findings into specific steps—from disabling risky protocols and removing shadow admins to enforcing MFA and tightening permissions—so you can close gaps quickly without guesswork or disruption.

With the help of Silverfort, we were able to fill a critical gap in our identity security which we were experiencing, which was key for our overall security posture.
Katie McMillan | Information Security Manager

With the help of Silverfort, we were able to fill a critical gap in our identity security which we were experiencing, which was key for our overall security posture.
Katie McMillan | Information Security Manager

Why Silverfort is different
Don't just find your weaknesses. Fix them. Silverfort ISPM combines posture with power.
Complete coverage
Across cloud, on-prem, hybrid and AI agents
Low-touch rollout
That scales across all identities and environments
Inline enforcement with patented RAP technology
Enabling virtual fencing to block threats instantly
Adaptive policies and enforcement
Based on real-time identity behavior
Non-intrusive protection
With minimal operational impact
Traditional tools
Posture-only startups
Discovery depth
- Static config snapshots only
- Mostly cloud-centric, partial view
Full coverage & continuous discovery
On-prem, cloud & hybrid; configs, real users & NHIs
Risk prioritization
- Manual rules, noisy alerts
- Basic scoring, black-box ML
Enriched impact & probability model
Model enriched with identity context & threat insights
Mitigation
- Advisory only, manual fixes
- Remediation playbooks
Actionable recommendations
Automated playbooks and inline enforcement
Sustainability
- Mostly periodic scans
- Varies from periodic scans to continuous analysis
Continuous and scalable
Continuous posture analysis and monitoring, hardening and drift detection
Operational safety
- Risk of breaks and mis-fixes
- Varies
Guided mitigation
Minimal disruption and safe fallback