Silverfort Protection Against CVE-2023-23397 Outlook Zero Day

In the latest Patch Tuesday, Microsoft released a patch for CVE-2023-23397 Zero Day in Outlook, which was reported to be exploited in the wild. Exploitation of this vulnerability enables an adversary to grab NTLM hashes (equivalent to user credentials) from the targeted machine and use them for malicious access to other machines in the environment. All this would take place as soon as a crafted email is downloaded to the machine’s inbox without any need of interaction from victim’s side. Microsoft has rated the severity of this vulnerability ‘critical’ and traced its exploitation to a Russian APT group targeting a limited number of organizations in government, transportation, energy, and military sectors in Europe. In this article we provide a brief analysis of CVE-2023-23397 and show how Silverfort’s Unified Identity Protection platform can mitigate its exploitation’s impact with a simple policy that enforces MFA on NTLM authentications.
Table Of Contents
CVE-2023-23397 High-Level Analysis
Description of the Targeted Outlook Component
CVE-2023-23397 is an Elevation of Privilege vulnerability in Outlook Client for Windows. It abuses an antique attribute that still exists that enables a customized alert sound of a scheduled appointment. According to Microsoft’s documentation the attribute ‘PidLidReminderFileParameter’ accepts a full path of a sound file. This field supports the Universal Naming Convention (UNC) path to access remote files and folders using the standard network file-sharing protocol SMB. When the appointment is overdue, it triggers the customized sound and forces Outlook to reach the remote file.
Where is the Vulnerability in this Component?
The problem with this behavior is that during the creation of the SMB session, an NTLM authentication is made to the remote server. Snatching the session can allow an adversary to perform an NTLM Relay attack against another service on behalf of the victim, or alternatively bruteforce the NTLM hash and achieve the user’s password.
So, first and foremost, we strongly recommend upgrading all Outlook clients for Windows to its latest version.
CVE-2023-23397 Risk: Credential Theft Without User Interaction Required
The unique concern regarding this vulnerability is that it can be triggered without any user interaction at the moment the Outlook client receives the malicious appointment. This is because the faulty attribute is triggered in case the appointment is overdue. This dramatically sets it apart from any vulnerability that requires interaction such as opening an attachment or clicking a link. The entire exploitation process takes place in the background, providing the adversary the ability to access resources on the user’s behalf.
The common security stack in today’s organization lacks the ability to detect and prevent in real-time lateral movement attacks that employ NTLM relay. This makes CVE-2023-23397 an immediate threat that must be addressed.
Silverfort Mitigation to Exploitation of CVE-2023-23397
Silverfort’s Unified Identity Protection platform can protect against the exploitation of CVE-2023-23397. While Silverfort won’t prevent the exploitation itself it would deprive the adversary’s ability to utilize the stolen hash for malicious access, with a simple MFA policy.
Silverfort performs continuous, real-time monitoring, risk analysis and policy enforcement for all authentications in the AD environment. As such, it can identify NTLM authentications and leverage this identification to trigger MFA verification.
Recommended Policy to Protect Against Potential NTLM Relay Attacks
We recommend the following:
1. Configure an NTLM policy for any server that is exposed to the internet. As an additional precaution measure, you can also include sensitive resources that aren’t exposed to the Internet, since this vulnerability can also be applied from inside the network.
2. Apply MFA policy for non-NTLM authentication protocols, as there are variants of how the vulnerability can be exploited where the password can be brute forced, providing the attacker the ability to use it with other authentication protocols as well.
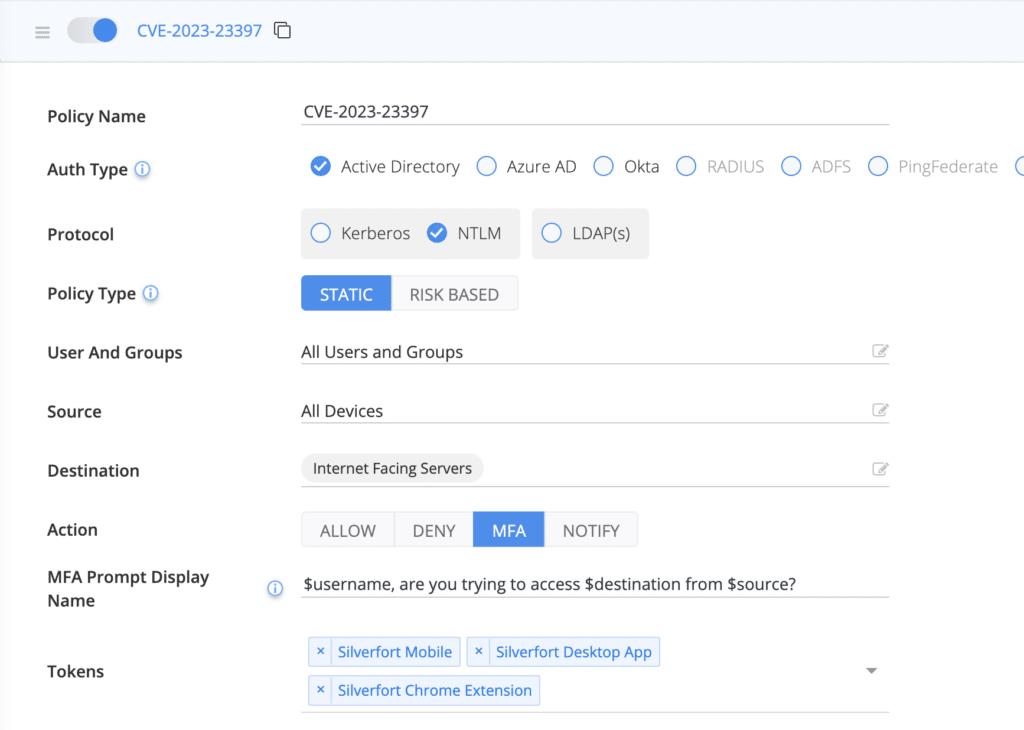
If you find the ability to protect NTLM and other AD protocols with MFA, feel free to reach out and request a demo or visit our website.

