Osterman Research’s latest study, “Strengthening Identity Security: Governance, Visibility, and Autonomous Remediation,” reveals a troubling truth: 70% of organizations believe their identity security is ‘mature,’ but 80% admit they lack complete visibility into active identity threats under exploitation. This is the maturity myth: confidence outpacing capability. A lack of industry standards for what identity security is and what it should deliver may be partially to blame for this maturity myth.
This maturity myth is more than a perception problem. It’s a tool problem. It’s a business risk. It’s indicative of an industry at an inflection point. Lack of budgets, resources, and tooling created delays in action and missed opportunities to mature enterprise identity security programs.
Executives are beginning to recognize the urgency: Today, more than 50% of leaders now say identity security is an extremely important cybersecurity priority. What’s changed is the realization that identity compromise is not just an IT issue—it’s a direct driver of ransomware, fraud, compliance failures, and reputational damage.
The Rising Tide of Identity Threats
Why the urgency? Because while internal optics lag, external pressure is rising exponentially. Identity-led threats are intensifying across every industry.
72.1% of identity leaders report that the threat level of identity-related attacks has increased or remained unchanged in the past year. The most significant jumps include AI-powered attacks, ransomware-based attacks, and social engineering of desk staff to reset credentials or MFA factors (up 14.3%).

Over the last 12 months, 60% of identity leaders have seen adversaries become more interested in stealing and abusing compromised credentials, and almost 80% lack visibility into what NHIs/service accounts are actually doing—precisely where attackers hide and pivot. It’s not surprising then that nearly every organization surveyed (93.7%) is concerned about account takeover due to compromised credentials in the next two years.
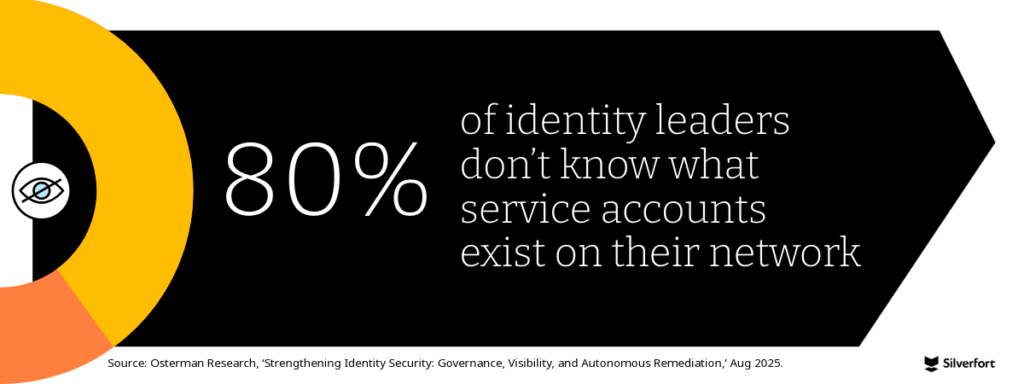
The threat landscape is accelerating—and yet most organizations are struggling to see it clearly.
The Visibility Crisis
Visibility is the foundation of effective identity security, and the research uncovers a major blind spot. More than three-quarters of organizations lack complete visibility into 14 different identity threats and fundamentals, including service account behaviors, historical changes to identity configurations, and whether high-privilege users are even using MFA.
One of the most alarming findings: 4 out of 5 identity leaders don’t have full visibility into three critical risks:
- Service accounts are behaving in unexpected ways.
- Authentication session tokens are used in abnormal locations.
- Compromised employee credentials for sale on the dark web.

Whether you’re securing your endpoints, cloud, or network, visibility is a prerequisite. Identity should be treated like any other piece of critical IT infrastructure, and protected the same way—if not even more so. When attackers use valid—but stolen—credentials, traditional defenses are often insufficient, making visibility even more important.
Service accounts, AI agents, unknown NHIs...
you have it, we see it.
Legacy, ‘Reactive’ Prevention Models Fail in New AI Agent & NHI Age
The study also found that the top barriers to stopping identity threats are manual processes and lack of automated remediation. Nearly 80% of organizations cannot monitor what their service accounts are doing, and more than half cannot quickly detect when employee credentials appear for sale on dark web forums.
Manual investigations take too long in an era where AI-powered attacks can move in milliseconds. Relying on human reaction times against machine-driven threats is a losing battle.
Meanwhile, the C-suite is Paying Attention
At the leadership level, importance is soaring. Today, 84% cite identity security as a clear cybersecurity priority. When we drill down further, the data is even more encouraging: A majority of executives (51%) award identity security the highest rating, denoting it as ‘extremely important.’ That’s nearly double the 28% from 2023. That figure is anticipated to continue rising at a similar pace: By 2027, it’s expected to reach 66%.
The sentiment represents a clear signal that robust identity security is now viewed as business-critical, not optional. That growing executive focus sets the mandate: leaders want measurable progress. They are budgeting for it, and boards are now funding the catch-up.
Among organizations already using identity security technologies, two investment patterns will dominate the next 12 months.
The most common pattern is high priority investment colliding with high required investment—a sign of gaps large enough to demand urgent spend. This is the ‘close the gap’ phase.
The other clear investment priority signals a ‘doubling down’ approach. Organizations are identifying the highest priority identity security categories with lower incremental investment requirements, opting instead to strengthen capabilities already in place.
Together, the data paints a market in motion.
True Identity Security Market Emerges, Standard Definition Begins to Form
Non-human identities (NHIs) are the epicenter. As AI agents and service accounts proliferate, many teams still don’t fully understand which NHIs exist or what they’re doing, and nearly 80% lack visibility into service account behavior—a combustible mix given NHIs’ scale and privilege. That’s why NHI and service-account protection show up as top-priority investments for the next year—even when the spend required is high.

As the identity security market evolves from a compliance checklist to a strategic risk mitigation strategy, we’re seeing that what ‘mature’ means varies.
If traditional maturity was ‘we have IAM, MFA, and some logging,’ the new bar is higher. Osterman’s benchmark points to a gold-standard triad—continuous visibility, risk scoring, and autonomous response. 70% of organizations don’t meet this standard.

That’s the definition of a market-wide opportunity—and risk. Without layered identity security, organizations are left exposed to the very attacks that are most likely to succeed.
Side note: Silverfort can help here too.
Identity Security Mimicking the Endpoint and Cloud Security Solution Evolution
Digital Identity is increasingly complex, and the identity security industry must evolve to keep pace—much as we’ve seen other security solution market segments evolve before us.
Endpoint security evolved from security as a feature to dedicated point solutions with the introduction of products like Antivirus and EDR, before CrowdStrike emerged as a platform to protect entities holistically. Cloud security took a similar evolutionary journey: it began as local features from each cloud provider, moved into dedicated point solutions like container security and CSPM, before its inevitable platformization, as seen with Wiz.
Identity security is on a similar journey—moving from identity security as a local feature from each IAM provider to dedicated point solution offerings, such as MFA, PAM, and NHI. Today, it’s time to move into the third phase and begin protecting identities holistically.
The path to resilience requires honest assessment and action. Identity and Access Management (IAM) remains essential, but it is no longer sufficient.
The Path Forward
The maturity myth is not irreversible. With the right investments, organizations can move beyond labels to build true identity resilience. Prioritizing these capabilities moves organizations from a false sense of maturity to measurable resilience:
1. See everything you authenticate—human and non-human—across cloud and legacy. Most organizations still can’t inventory or monitor NHIs/service accounts with confidence, yet these identities now outnumber humans and are central to how work actually happens. Prioritize discovery and behavior baselining for service accounts, tokens, API keys, and emerging AI agents to detect “unexpected” actions before they escalate into incidents.
2. Don’t rely on IAM alone—establish an independent identity security control plane. IAM verifies and grants access; identity security protects identities against misuse and lateral movement. The data show organizations overestimate maturity when they equate IAM features with end-to-end protection. A unified layer that spans IDPs, directories, SaaS, and on-prem is now table stakes for consistent policy, detection, and recovery.
Need help getting end-to-end identity security?
We wrote the playbook — and we built the platform.
3. Shift left from clean-up to preemptive enforcement. Autonomous remediation should happen during the authentication moment (or even earlier), not hours into an investigation. Think step-up auth based on risk, hard blocks on abnormal geographies or protocols, ring-fencing service accounts to their intended scope, and automatic rollback of malicious identity configuration changes. That’s how you neutralize leaked credentials and stop lateral movement in real time.
For security leaders and communicators, the bottom line is simple: the C-suite is paying attention, the market is signaling its intent (in terms of priority and budget), and adversaries are exploiting gaps that we can measure. The organizations that close the visibility gap, debunk the ‘maturity myth,’ and operationalize autonomous, preemptive controls will be the ones that finally make ‘mature’ mean something.
Report
Download the full report today
See how your identity security peers are tackling top concerns and where they plan to invest to achieve their goals in 2025 and beyond.

