I sat down with Abbas Kudrati, APAC Chief Identity Security Advisor at Silverfort, to discuss the most pressing identity security trends shaping 2025 and what C-suite leaders need to know to protect their organizations.
Your new lecture title “It’s the identity, stupid” grabs attention immediately. What inspired this?
Abbas: Well, I borrowed from James Carville’s famous 1992 Clinton campaign message, but with a cybersecurity twist. The reality is that in today’s world, identity isn’t just one component of security, it’s the fundamental pillar. Your firewall isn’t your first line of defense anymore; your identity infrastructure is. Organizations that haven’t grasped this are fighting today’s battles with yesterday’s weapons.
What has changed in the security landscape that has made identity so central?
Everything has been turned inside out. The internet is the new network, the cloud is the new data center, and identity is the new perimeter. Any device can be a work device now, and effectively, every company has become an IAM company whether they realize it or not.
What’s particularly concerning is that non-human identities now outnumber human identities by 25-50 times. In 2010, humans dominated the identity landscape. By 2020, non-human identities were 10x more numerous, and by 2025, with GenAI, LLMs, and copilots, they’re projected to be 50x more numerous. That’s a massive attack surface that most organizations aren’t securing properly.
Your research highlights significant concerns about non-human identities. Why should executives care about this specifically?
Because it’s a ticking time bomb. According to Cloud Security Alliance research, only 15% of organizations feel highly confident in preventing NHI attacks, while 69% are concerned about them. Only 20% have formal processes for offboarding and revoking API keys, and even fewer rotate them regularly.
The most alarming part? Service accounts, which often hold extensive privileges, frequently lack robust visibility. If these machine identities are compromised through configuration files or code repositories, it can lead to extensive business disruption.
As organizations harden user policies, attackers are increasingly targeting applications instead. The problem? Applications can’t use MFA or remember credentials like humans can, and developers often want all the privileges they can get. It’s a perfect storm.
Gartner recently named managing machine identities as one of the top cybersecurity trends for 2025. What’s driving this focus?
Reality is catching up with the threat landscape. The OWASP Top 10 Non-Human Identity Risks for 2025 highlights critical issues like improper offboarding, secret leakage, vulnerable third-party NHIs, and overprivileged NHIs.
As more companies adopt Zero Trust principles, attackers are evolving their strategies. Rather than trying to circumvent identity infrastructure, they’re working to subvert it. This requires breaking down the traditional walls between identity and security teams, something many organizations still struggle with.
Let’s discuss AI’s role in identity security. How is it changing the landscape?
It’s a double-edged sword. Forward-thinking organizations are leveraging AI to transform identity operations, from discovering hidden entitlements to predicting risks and optimizing access policies. This represents a fundamental shift from reactive to predictive security.
But AI is also empowering attackers. We’re seeing increasingly sophisticated automation of identity-based attacks, particularly in permission mining and lateral movement. After gaining initial access, threat actors can now systematically explore and exploit identity permissions, especially in cloud environments, often finding subtle paths to higher privileges that might not trigger alerts.
What are the most significant identity-based threats in 2025?
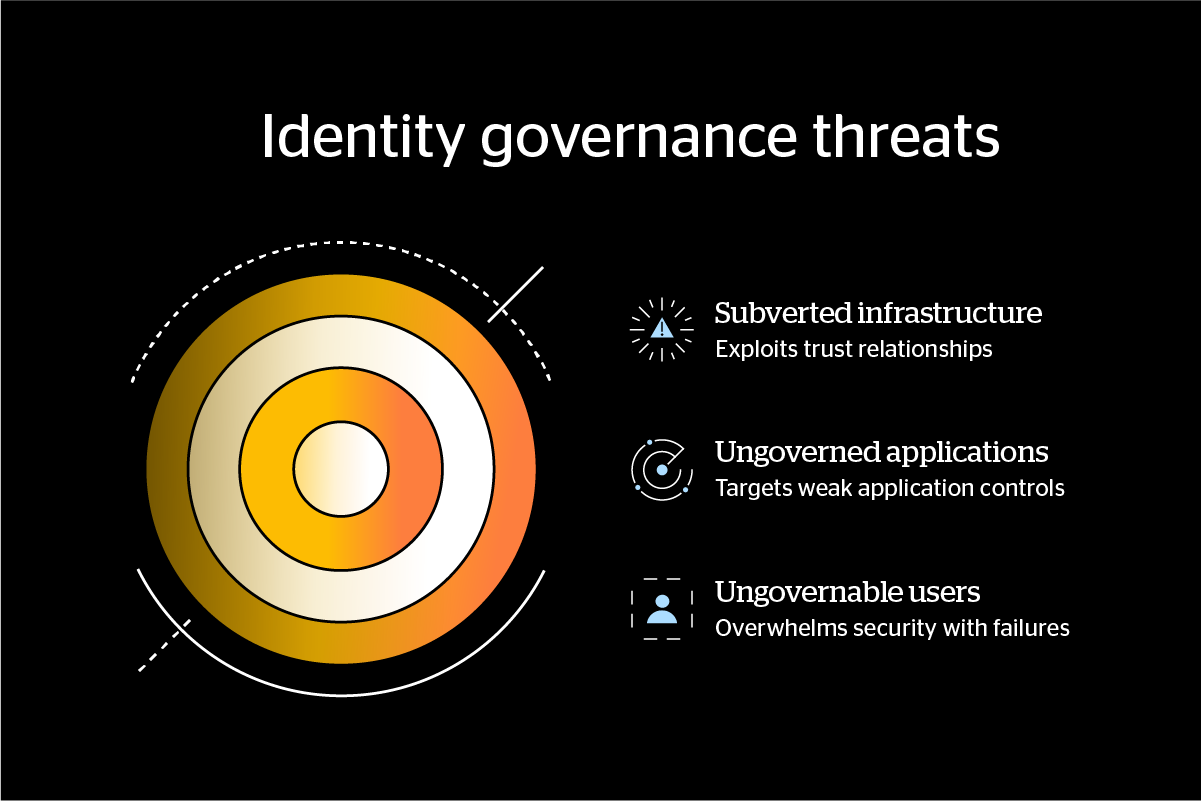
I categorize them into three main threats:
First, “Ungovernable Users“. The reality is that users can’t be trained to deal with sophisticated attacks like session-cookie theft, adversary-in-the-middle phishing, or MFA fatigue. The high frequency of user failures overwhelms SOC resources. Organizations need to make security flows failure-proof.
Second, “Ungoverned Applications”. As organizations harden user policies and infrastructure, attackers shift to applications. The strategy here needs to be strict application controls, compliance checks, and credential scanning in real time.
Third, “Subverted Infrastructure“. As Zero Trust adoption increases, attackers are working to subvert rather than circumvent identity infrastructure, exploiting trust relationships between identity providers and service providers.
You’ve developed a strategic matrix for identity security investments. Can you explain how executives should approach this prioritization?
The Identity Security Matrix helps executives allocate resources across four strategic priorities. Zero Trust Architecture and AI Integration offer the highest strategic value, though they differ in implementation complexity. Zero Trust Architecture provides high strategic value with relatively low implementation challenges, while AI Integration is just as important but requires more complex implementation.
Industry Consolidation, while complex to navigate, carries lower strategic weight for most organizations. Workforce Challenges require ongoing attention but shouldn’t divert resources from more critical initiatives.

What practical steps should C-suite leaders take to strengthen their identity security posture?
Six critical actions:
- First, implement strategic access controls, especially Just-In-Time access for sensitive operations.
- Second, tighten authentication requirements with robust MFA for both internal access and service-to-service authentication.
- Third, strengthen identity security testing to include scenarios like permission chain exploitation and SSO trust relationship vulnerabilities.
- Fourth, advance identity governance with regular permission reviews to limit breach impact.
- Fifth, transform security operations with identity as the cornerstone, implementing real-time verification.
- Finally, establish machine identity governance with dedicated oversight committees for these critical business assets.

For organizations still early on in their identity security journey, what’s the one thing they should focus on first?
Start by understanding your identity landscape, particularly your non-human identities. You can’t secure what you can’t see—or don’t even know about. Most organizations have hundreds or thousands of service accounts, API keys, and machine identities operating with excessive privileges and insufficient oversight. A comprehensive identity inventory, especially of non-human identities, is the foundation everything else builds upon.
What is one key piece of advice for security business leaders that you would share with our readers?
Identity security needs to evolve from a technical initiative to a business-critical priority. The C-suite must drive this transformation through strategic investment and attention. Companies that recognize “it’s the identity, stupid” and act accordingly will be far more resilient against the sophisticated threats of 2025 and beyond.
Want to learn more about protecting your organization’s identity infrastructure? Visit Silverfort’s Platform page to explore our Identity Security platform, or take a product tour.

