Most security programs are laser-focused on human users, including employees, contractors, and third parties. But there’s a parallel universe growing in scale and risk that remains largely invisible: non-human identities (NHIs). These are the service accounts, machine identities, scripts, applications, secrets, tokens and automation tools that keep our systems running. And they’re multiplying fast.
Adversaries don’t just hack people. NHIs are notoriously under-observed, under-protected and over-privileged—and their numbers are growing exponentially. Combine these four factors together, and it’s easy to see why NHIs are prime targets for attackers seeking ways to slip through the cracks and move undetected through environments.
Our new research, Insecurity in the shadows: New data on the hidden risks of non-human identities, details the challenges people face finding, securing and protecting NHIs. Deep analysis into billions of authentications across hundreds of organizations with millions of identities showed us that NHIs now outnumber human users by 50 to 1 in large organizations—of which 80% have the kind of critical posture issues that expose to common attack techniques. NHIs are challenging to find and harder to protect, making them heavily targeted by attackers and one of the most unprotected elements of the identity attack surface.
The highlights
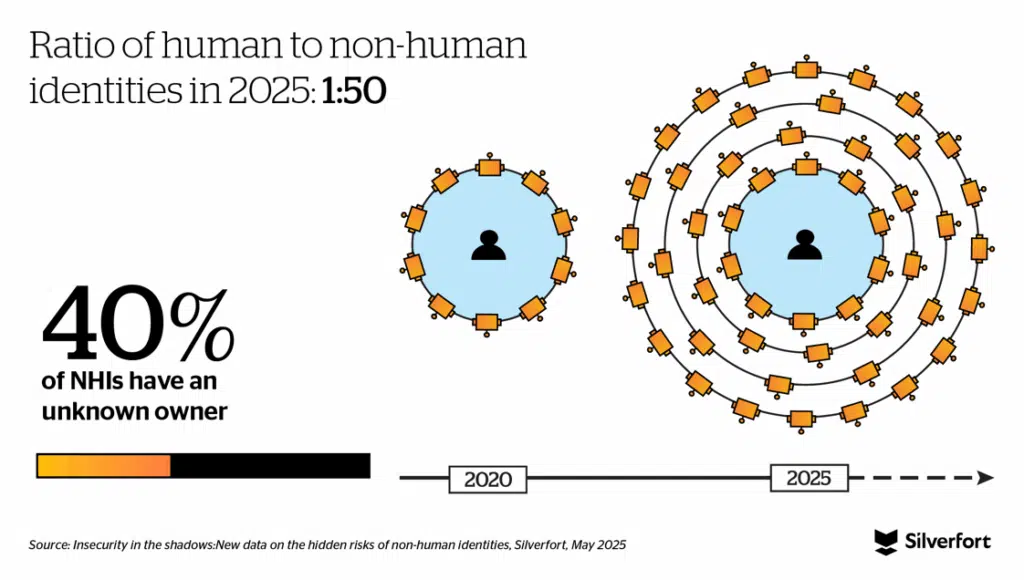
- NHIs outnumber human identities by 50:1. This means that for every user an organization manages, there are dozens of silent NHIs operating in the background.
- 40% of cloud NHIs do not have an owner. These accounts are often excluded from proper lifecycle management, leaving them unobserved, unprotected, and open to abuse.
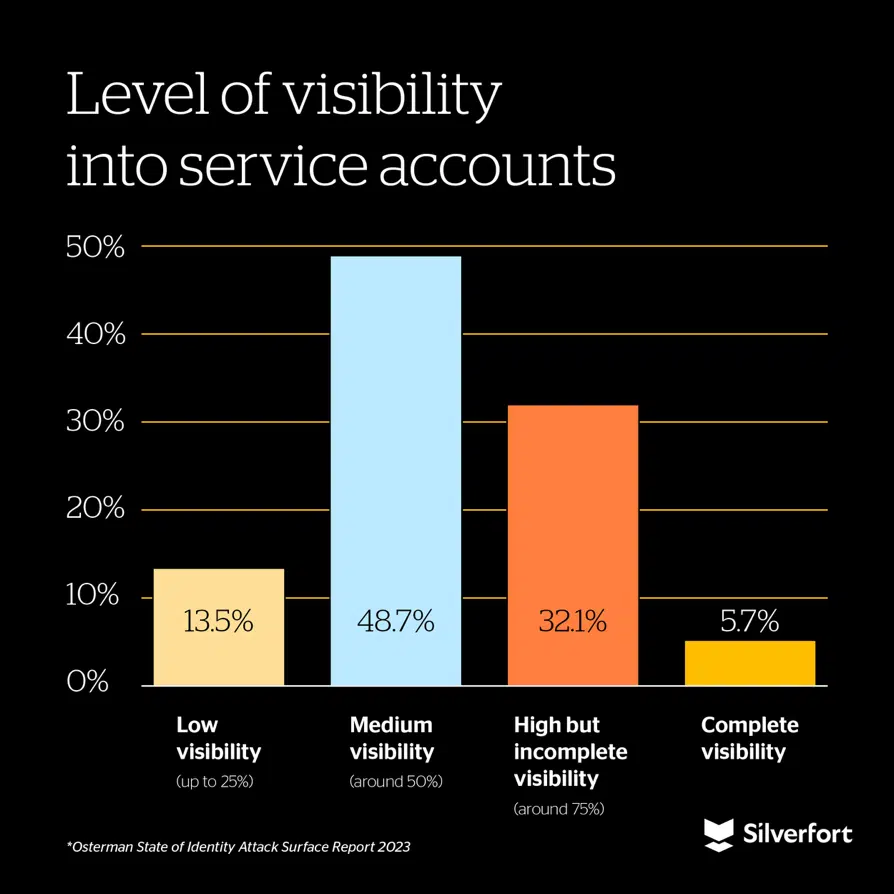
- Only 5.7% of organizations said they could accurately inventory all NHIs in their environment. Visibility remains the first—and possibly biggest—barrier to securing NHIs.
- 56% of organizations unknowingly sync their service accounts to their SaaS directory. This makes it possible for attackers who have accessed an organization’s on-prem environment to also—fairly easily—compromise their SaaS environment too.
- 46% of service accounts are still using the now-deprecated NTLM protocol to authenticate. Deprecated protocols are insecure protocols, making them easy targets.
The key challenges of securing non-human identities
Despite their prevalence, power and usefulness, NHIs can be a thorn in identity and security teams’ sides. Silverfort’s research highlights four key problems that help explain why NHIs are such a major blind spot:
- They’re under-observed: NHIs operate behind the scenes, often without visibility or monitoring. In fact, 94.3% of organizations don’t have full visibility into their service accounts, let alone what they’re doing and what they’re accessing.
- They’re under-protected: NHIs rarely—if ever—benefit from the same security controls applied to human users. MFA cannot be enforced, and without full observability, behavior baselines cannot be established. Even more worryingly, many of them are stuck using insecure protocols: 46% of service accounts still use NTLM authenticate, despite it being deprecated in mid-2024.
- They’re over-privileged: Many NHIs are granted far more access than they need, often with domain-level or administrative privileges that persist indefinitely. 35% of all user accounts are service accounts with high access privileges and low visibility, and 56% of organizations unknowingly sync more than half of their service accounts to their SaaS directory.
- They’re everywhere: NHIs span every environment—on-prem, hybrid, multi-cloud—and touch nearly every critical system. Since 2020, the ratio of NHIs to humans has grown from 10 to 1 to a staggering 50 to 1. Their ubiquity makes them both indispensable and hard to contain.

Spotlight on one of the oldest, riskiest and more prolific NHIs: service accounts
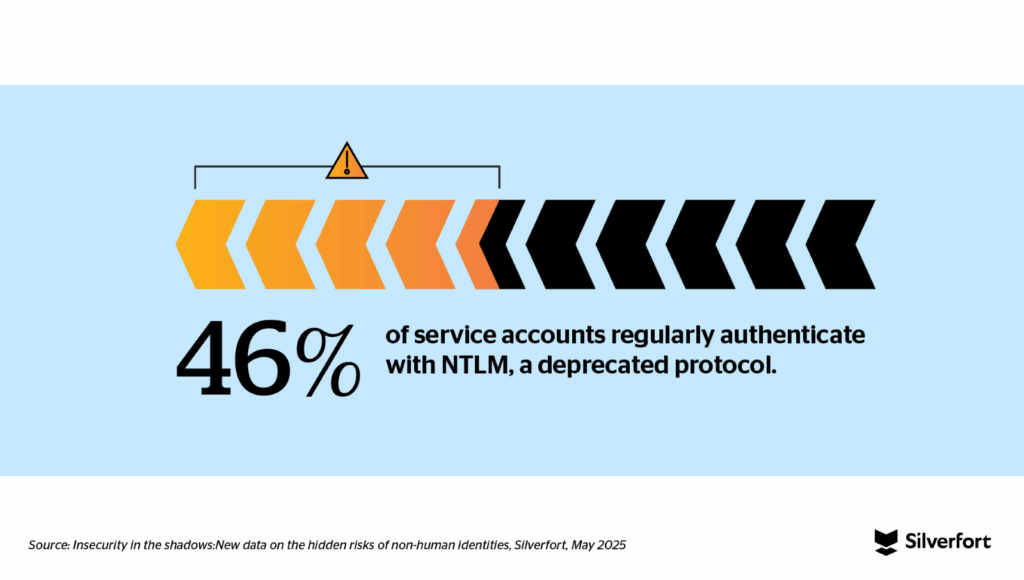
Within the large pool of NHI types, service accounts—used for machine-to-machine communication within Microsoft’s Active Directory’s (AD) environments—have been overlooked by defenders but targeted by attackers. Traditional identity security controls are almost entirely human-centric, so service accounts simply couldn’t be protected in the traditional way. Our data shows that 46% of service accounts regularly authenticate with NTLM, a deprecated authentication protocol with plenty of vulnerabilities. This year alone, several researchers unveiled vulnerabilities about NTLM. Hackers know this and use it to their advantage. You can read more about the countless attacks where NTLM is used here.
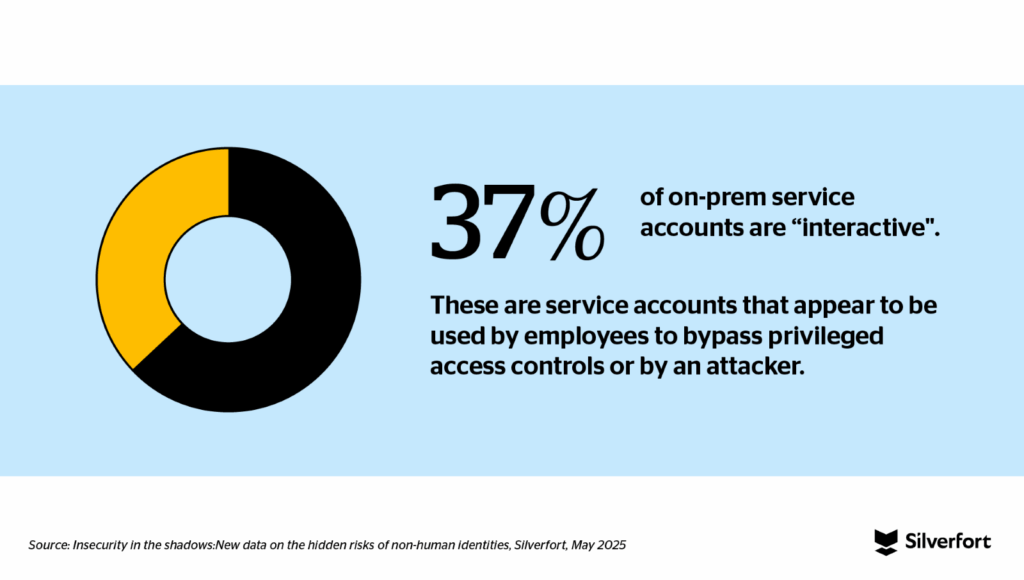
We also found that 37% of service accounts are what we call “interactive”. These are service accounts that appear to be “interacted” with by employees—or attackers—to bypass privileged access controls.
It began with human admins creating service accounts across multiple systems, apps, platforms and services without a centralized view of what they are responsible for, who created and owns them, and what they need access to. For most organizations, there has never been a single source of truth for NHIs, nor any standardized onboarding, offboarding, or ownership processes, leaving their inventories incomplete at best.
Securing your NHIs is a must, not a nice-to-have
Threat actors have already realized what many organizations have not: non-human identities are often the weakest link in an enterprise’s identity fabric.
1. API key or token theft
Internet Archive Breach (October 2024): Attackers exploited unrotated API keys leaked from the Internet Archive’s GitLab repository, gaining access to over 800,000 support tickets containing sensitive user information.
2. Overprivileged service accounts
Dropbox Sign Breach (May 2024): Attackers compromised a backend service account with excessive privileges, accessing the customer database and exposing sensitive user data, including email addresses, usernames, hashed passwords, API keys, and OAuth tokens.
3. OAuth application abuse
Microsoft and Okta Attacks: Nation-state actors have been seen to abuse OAuth applications to move laterally across cloud environments. Major software companies like Microsoft and Okta have fallen victim to attacks leveraging compromised machine identities, highlighting the vital need to connect non-human identities with their human counterparts for complete visibility and protection.
These aren’t isolated incidents—they reflect a systemic trend. NHIs are now integral to one of the most exploited attack vectors: identity. Unlike human identities, NHIs cannot be protected by the most common safeguards, such as MFA, creating a vast, invisible, and vulnerable attack surface that many defenders are ill-equipped to secure.
It’s easy to see the trend at play here. While organizations have invested heavily in securing human users, NHIs still fly under the radar. But all is not lost—there is something they can do about it.
A new approach: Silverfort’s expanded NHI Security
Recognizing the growing risk and operational complexity around NHIs, we have expanded our Non-Human Identity Security capabilities to provide continuous protection and visibility to all NHIs—including NHIs on-prem and the cloud. This includes:
- Unified coverage for both on-prem and cloud NHIs.
- Complete discovery and ownership mapping.
- Real-time, scalable protection of service accounts with virtual fencing.
- Seamless integration across platforms.
Learn more about out expanded NHI security offering, and how it can help you find and map your unknown NHIs, enforce security controls and remediate misconfigurations and identity weaknesses with actionable recommendations.
Final thoughts
Non-human identities are no longer a niche IT concern—they are a central pillar of enterprise infrastructure and a rapidly expanding attack surface all their own. The evidence is clear: NHIs are everywhere, they have elevated access, and they’re largely invisible to traditional security controls. As attackers increasingly exploit this blind spot, organizations must act quickly to secure their non-human identity landscape.
The path forward starts with visibility, is strengthened through policy enforcement, and culminates in continuous, adaptive protection, so every dimension of identity is known and secured.

