When it comes to protecting organizations from compromise, what does visibility mean? It’s a word often used in the security industry – yet it is rarely fully defined.
In the context of identity protection, visibility is the ability to view and manage all data and security risks associated with a user account – and gain actionable insights from that information. This matters because, without full visibility into elements such as user and authentication activity, access permissions, risky identities, authorized applications, and so on, you could be leaving critical identity security gaps without even knowing it.
In this post, we’ll highlight the different challenges organizations experience when they don’t have full visibility into their user’s activity and authentication requests. Afterwards, we’ll show how Silverfort empowers customers to gain complete visibility across their environments enabling real-time detection and actionable insights into resolving identity risks with almost zero effort.
Managing Users Comes with a Lack of Context & Visibility
In most cases, a typical user is associated with several different identities across cloud or on-prem services in their organization’s hybrid environment.
Further, most user directories lack the tools to report on the data and risks associated with a particular identity. The vast amount of user data residing in systems like Active Directory or an organization’s SIEM can make it daunting to track, manage, and monitor user identities, access permissions, and view activities effectively.
Unfortunately, very few solutions can aggregate all inventory and identity data. This results in fragmented and incomplete information about who has access to what resources and how they are using them. As a result, even if security admins are aware of some or all of the identities and activities associated with a user, they might not have a clear understanding of what permissions have been assigned, inherited, or shared. This is a serious identity protection challenge.
Due to this lack of visibility, potential identity-related risks may arise, such as unauthorized access or misuse of privileges. Without complete visibility into your users and their access capabilities, it becomes increasingly difficult to protect sensitive data and critical assets. This is why it is imperative to recognize that security truly starts with visibility.
Silverfort Provides Complete Visibility to All Users
Silverfort automatically discovers and protects all user accounts in a hybrid environment from identity-based threats and provides centralized visibility into every authentication and access request. As a result of Silverfort’s native integrations with all identity providers, including Active Directory, it can log every authentication request. This provides a unified view of all network activity across every user and any resource in the hybrid environment.
With complete visibility across all user activity, Silverfort’s risk engine can determine the legitimacy of every authentication, so organizations can detect and respond to potential security threats in real-time — including blocking the access of any accounts that display anomalous behavior.
This is just a glimpse into how Silverfort’s visibility capabilities can help you strengthen your identity security posture management. Now, let’s look at how you can gain visibility into all the users in the Silverfort console.
Visibility of User Activity & Authentication
Full User Context
The Silverfort Logs screen provides full visibility into all user logs, authentication activity, and risk indicators. The moment Silverfort is integrated with your IDP, all user accounts are detected, allowing you to monitor their activity and associated risks. As each user is detected, their details are displayed, including username, risk level assigned by Silverfort, authentication type, Silverfort’s action, and the IdP result.
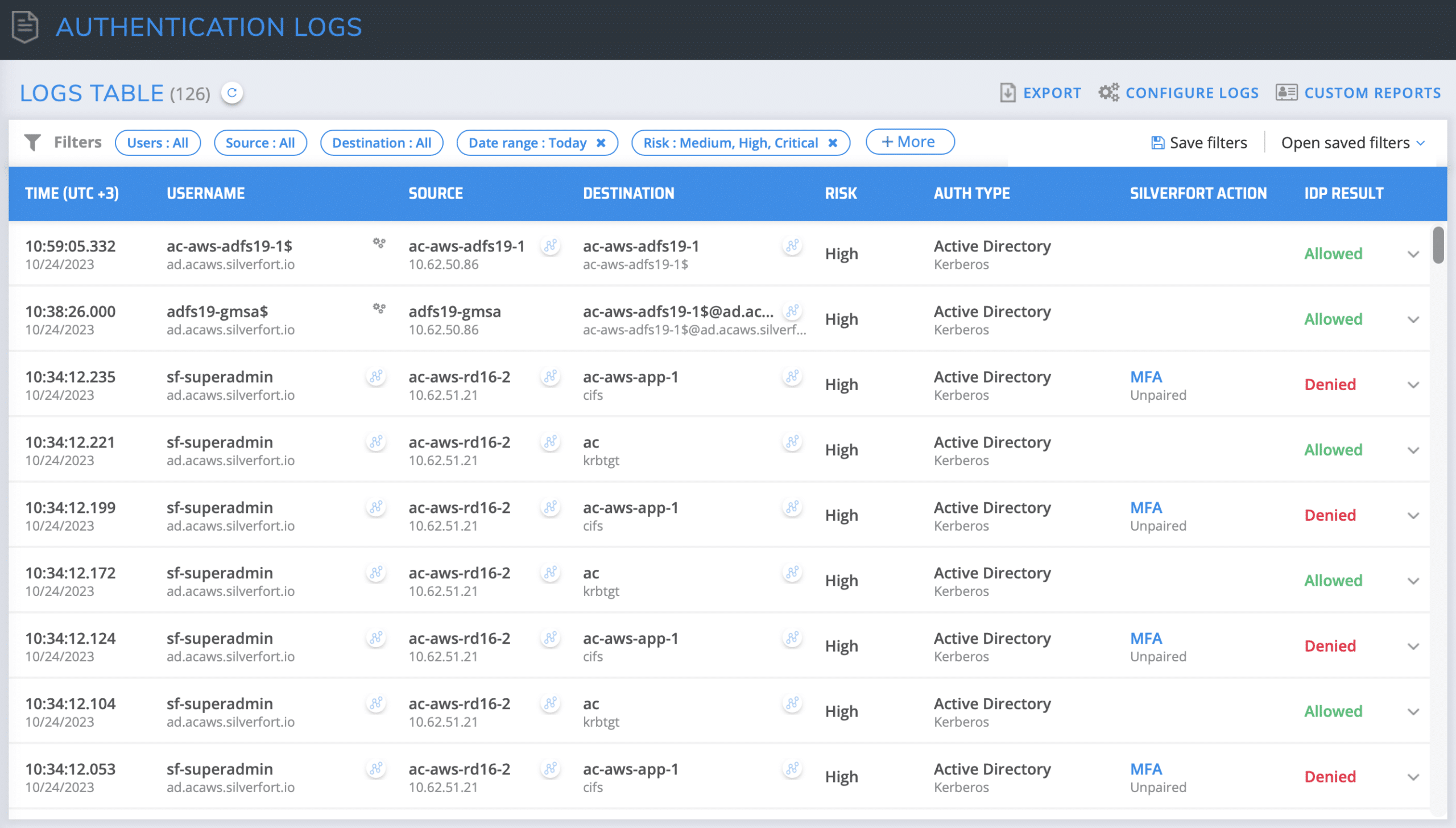
Filtering by Risk Indicators
In the Logs screen, users can filter their logs according to account type or risk indicator. This allows user to view their users by the different risk indicators that have been detected and assigned by Silverfort’s risk engine. Silverfort supports many different users’ risk indicators such as NTLMv1, kerberoasting, brute force, MFA bombing, Abnormal MFA activity, failed authentications, and many more. By filtering by risk indicator, you are empowered with complete visibility and insights into your risky users, and you can now remediate the different risk each user present.
Here are two prominent risk indicators that many of our customers tend to filter by within their Silverfort console Logs screen:
What is it? NTLMv1 is the legacy version of the NTLMv2 protocol that is used today in Active Directory environments.
What makes it risky? NTLMv1 uses relatively weak encryption algorithms, which can be easily cracked by attackers that intercept its authentication traffic. This makes environments that use NTLMv1 critically exposed to compromise.
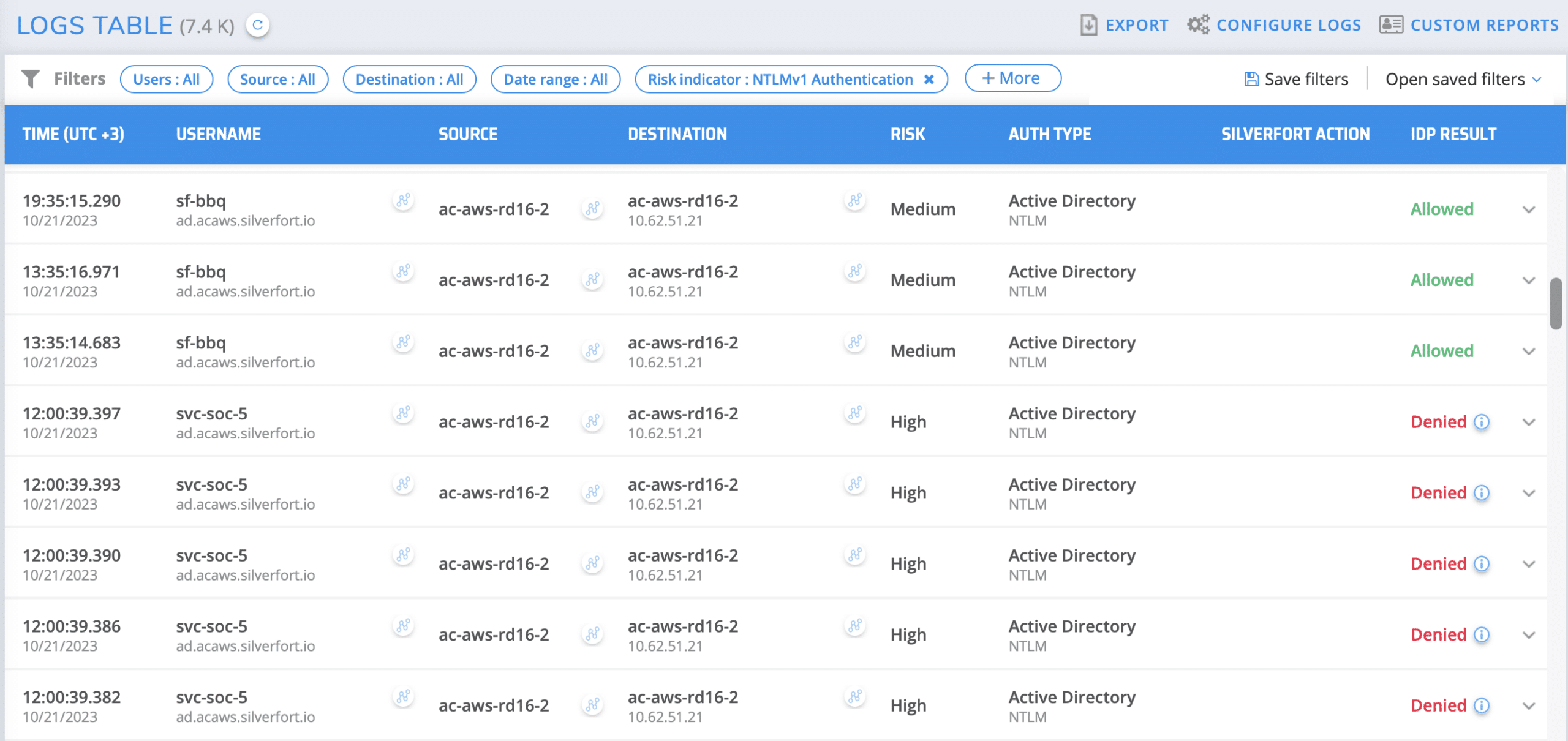
How can Silverfort users apply this feature? Silverfort discovers all NTLMv1 authentications within an environment. Silverfort’s risk engine detects NTLMv1 authentications and flags them as a risk indicator, which can be used as a filter to uncover machines that perform similar authentications and also as an access policy trigger.
Within the Authentication Logs screen, check the NTLMv1 Authentication box. Once checked, all matching authentications are displayed with all the authentication standard fields (source, destination, etc.) that can be further enhanced with additional filters.
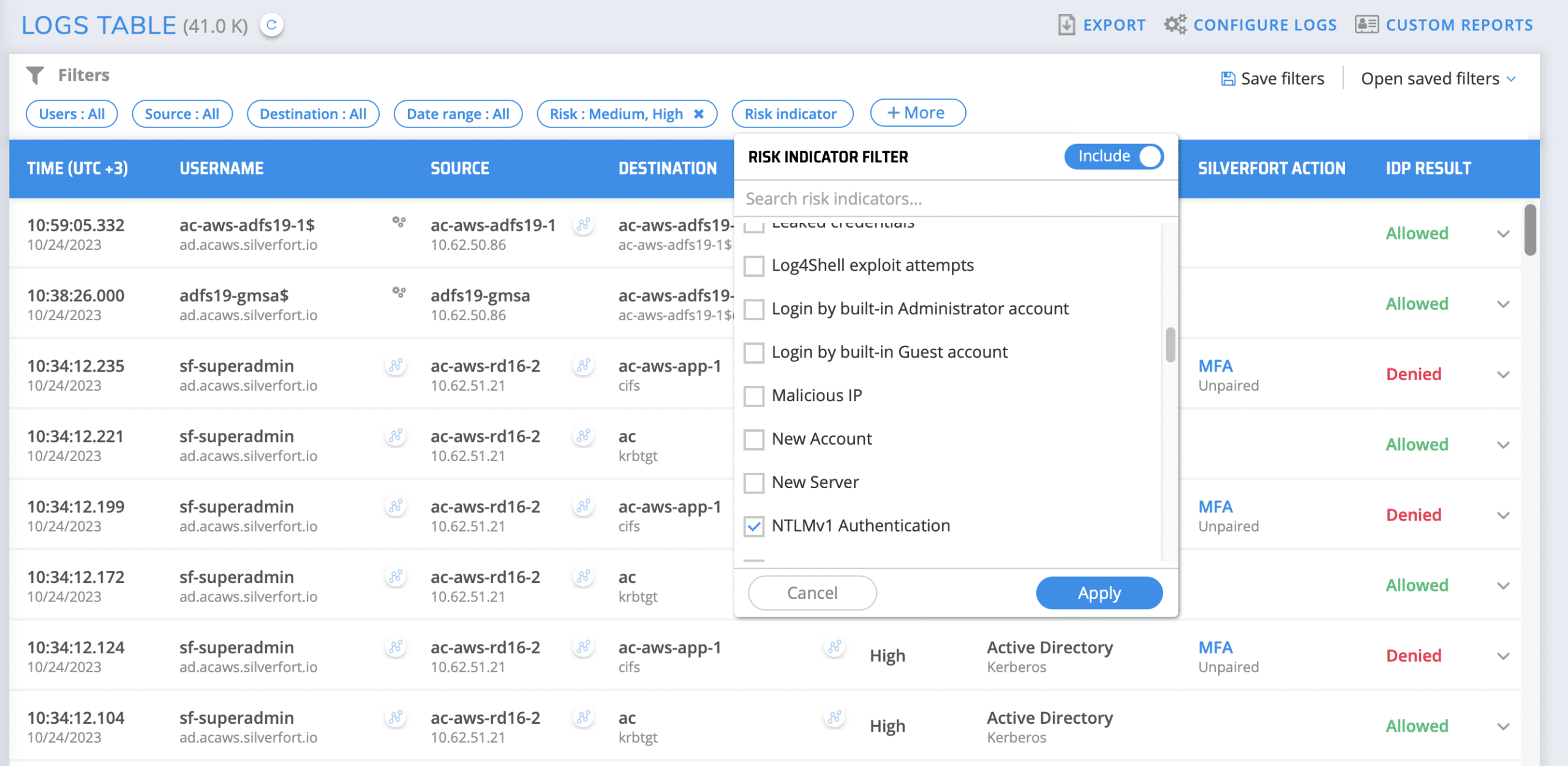
As well as providing visibility into when NTLMv1 authentications are being used, Silverfort can also protect you and your organization by preventing the use of NTLMV1. Our blog post Silverfort Enables Organizations to Resolve the Risks of NTLMv1 details how you can protect against the use of NTLMv1 authentications.
Shadow Admins
What is it? Shadow admins are user accounts that either possess admin access or are capable of obtaining it, despite not being members of a documented admin group. IT teams are typically unaware of these accounts as there is no documentation of the excessive privileges they possess.
What makes them risky? Since these accounts are not regarded as admin accounts by the IT team, they are not subject to common admin account security controls (PAM, MFA., etc.). This makes these accounts a lucrative target for adversaries that can easily compromise them and abuse their privileges for malicious access.
How can I detect shadow admins with Silverfort? In Silverfort’s Authentication Logs screen, add the Risk Indicator filter and check Shadow Admins. Click Apply and adjust the time range to suit your monitoring schedule This will display all shadow admins that have been added to the environment during this period.
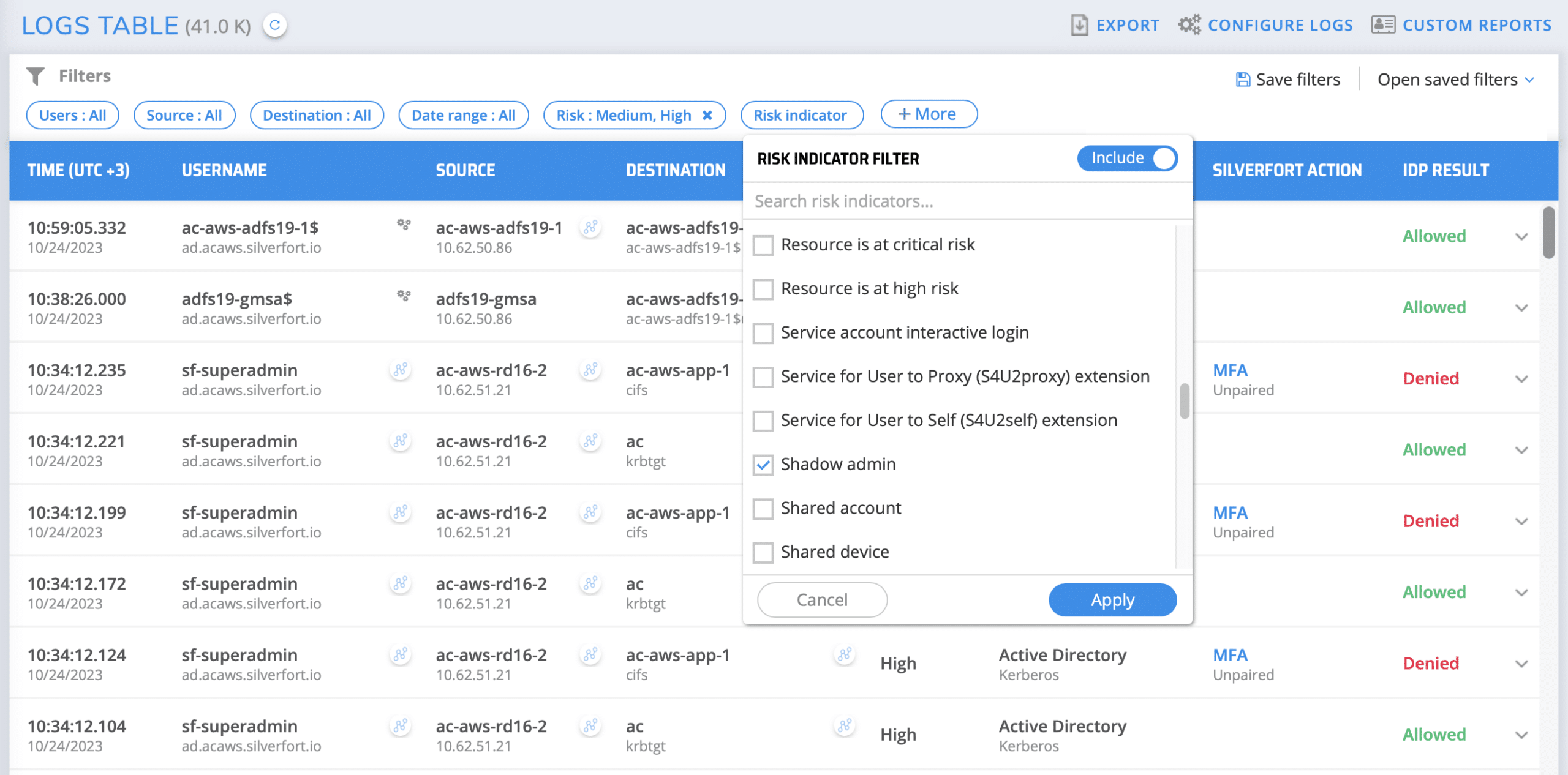
Upon discovering an account, you can click the investigation icon to see exactly which resources it has attempted to access since it was created. You can then decide whether to remove them entirely or remove their redundant permissions.
Identity Security Posture Management
Organizations can view the identity inventory of their environment in the insights screen of the Silverfort console, including users, resources, risky users, and more.
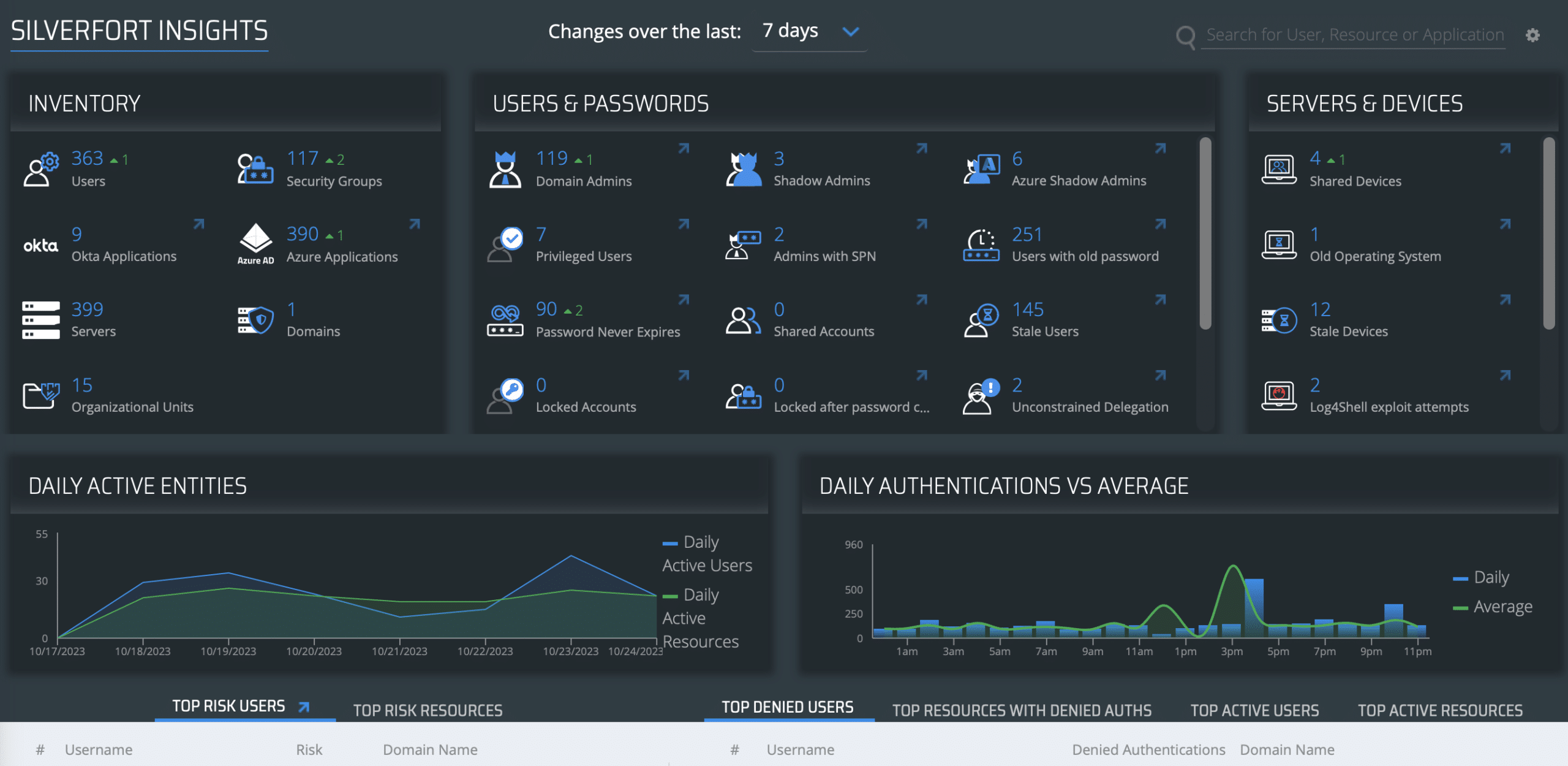
This screen displays the types of users and resources in your environment as well as the weaknesses in your security that adversaries may abuse to launch identity threats. Among these are the shadow admins, admin users with SPNs, accounts with passwords that do not expire, and many more.
This screen enables you to gather actionable insights on your environment’s security posture and take action to resolve it, making it significantly harder for threat actors to attack your business.
Real-Time Visibility is the Foundation of Identity Protection
Complete visibility into resources and users across hybrid environments is becoming a top priority for organizations looking to adopt a proactive approach to identity protection. The good news is that with Silverfort, they can gain comprehensive visibility into their entire identity attack surface in an effortless, fully automated manner. This is the first step towards hardening your environment against identity threats and reducing the likelihood of a successful attack.
Looking to gain complete visibility across your environment? Reach out to one of our experts here.

