In today’s threat landscape, stolen credentials are one of the most common causes of data breaches. A recent report found that 61% of all breaches involve the misuse of credentials. Attackers use tactics like phishing and “push-bombing” (rapid-fire MFA push notifications) to trick users into giving away access. Just one compromised password or an accidentally approved login can let an attacker impersonate a legitimate user and infiltrate an organization’s network.
When I was a CISO with a large firm, I witnessed firsthand how a single stolen password could wreak havoc. In that incident, an attacker phished an employee’s credentials and quietly accessed sensitive systems for weeks before detection. The breach caused significant downtime and compliance headaches. After helping contain the damage, I worked with the company’s IT team to harden their identity controls—rolling out MFA to all users, tightening admin account policies, and implementing continuous monitoring. This experience underscored that strong credential security habits aren’t just best practices on paper, but real safeguards against incidents we hope to never face again.
To defend against credential abuse, organizations should cultivate “healthy habits” in identity security. In this blog, I’ll outline five essential security habits to help prevent credential breaches – and discuss how to evaluate capabilities that support each habit.
1. Implement Muti-factor authentication everywhere
One of the most effective defenses against credential attacks is multi-factor authentication (MFA). Stolen passwords alone are often not enough to breach an account if a second factor (like an authenticator app prompt or token) is required. In fact, Microsoft observed that 99.9% of compromised accounts did not have MFA enabled. The absence of MFA has been a common factor in many high-profile breaches – compromised credentials combined with lack of MFA were a shared denominator in multiple major breaches in 2024/25.
Enabling MFA for all users (especially administrators) can shut down the vast majority of opportunistic attacks that rely on stolen or guessed passwords.
Despite these benefits, many accounts still lack MFA protection. Why? Often there’s a misconception that MFA adds too much friction or that it “isn’t worth it.” Some IT teams face user pushback or lack executive support, and thus aren’t incentivized to enforce universal MFA. In other cases, organizations simply haven’t extended MFA to certain systems or legacy applications, leaving gaps by accident. The reality is that while basic MFA isn’t infallible, it stops the vast majority of automated attacks cold – making it a fundamental habit for credential security.
That said, not all MFA is equal. Attackers increasingly exploit MFA fatigue by bombarding users with repeated push notifications (so-called push-bombing). Given that people receive 60–80 mobile push notifications each day on average, it’s easy for a fatigued user to accidentally tap “Approve” on a fraudulent login prompt. To counter this, organizations should implement phishing-resistant MFA (such as FIDO2 security keys or number-matching push prompts) and educate users to never approve unexpected access requests.
It’s also essential to find solutions that help your team extend MFA protection to every resource and protocol in an environment, including systems that don’t natively support MFA. This means you should enforce MFA not just on web and cloud applications, but even on legacy on-premises systems (databases, file servers, command-line tools, etc.) that traditionally were unable to leverage MFA. By making MFA ubiquitous and difficult to bypass, you dramatically reduce the risk of a single stolen password leading to a breach.

2. Adopt a Zero Trust approach to identity
Implementing a “Zero Trust” mindset for identity is a healthy habit that goes hand-in-hand with MFA. In a Zero Trust model, no login or user session is implicitly trusted – even if the user is on the internal network or already authenticated. Every access attempt is continuously verified based on context (user role, device security, location, time, etc.) before granting access. This is vital because modern enterprises have dissolved perimeters; identity is now the new attack surface in cybersecurity. With users logging in from everywhere and attackers adept at blending in with normal user activity, it’s crucial to “never trust, always verify” each credential use.
Practicing this habit means leveraging conditional access policies and continuous monitoring for all accounts. For example, if a user suddenly logs in from an unusual location or an unmanaged device, additional verification or restrictions should kick in. Many breaches could be prevented by such context-aware controls – one investigation found that hundreds of stolen credentials remained useful to attackers simply because the target systems did not have location-based access policies to block logins from untrusted networks.
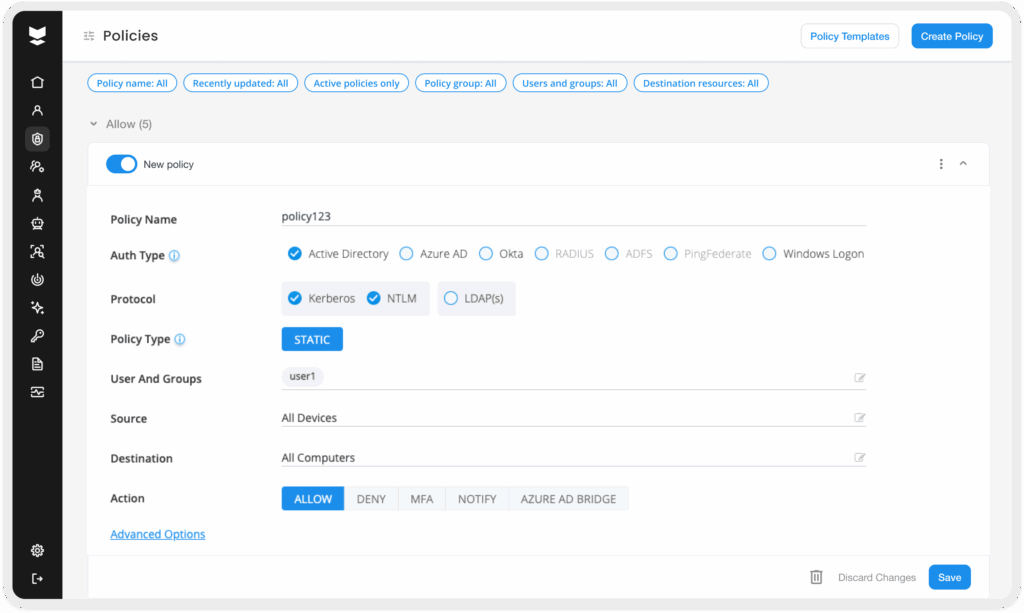
Modern identity security platforms continuously monitor every authentication and apply risk-based policies. If a login attempt deviates from normal behavior or occurs under high-risk conditions, the proper approach would be to require step-up authentication (like MFA) or even block the attempt. By treating every access as untrusted until proven otherwise, organizations can contain and thwart attackers who manage to acquire valid credentials.
3. Secure privileged and high-risk accounts with extra care
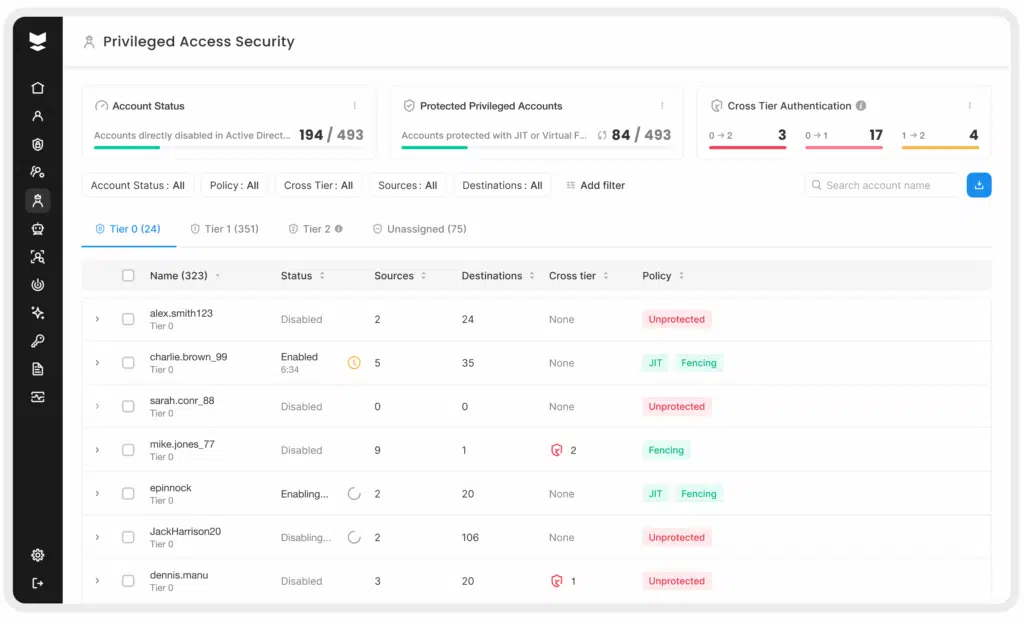
All user accounts are important to protect, but privileged accounts (administrators, service accounts, executives, etc.) deserve prioritized attention as a healthy security habit. These accounts often have broad access and, if compromised, can inflict serious damage. Unfortunately, I see many incidents where admins or other powerful accounts were left under-protected. In a recent example, a government organization was breached via a former administrator’s account – the account had retained high privileges and did not have MFA enabled. Similarly, the fallout from a 2024 cloud breach (targeting Snowflake customers) revealed that some demo and service accounts lacked SSO or MFA protection, providing an easy target for attackers. The lesson is clear: any account with elevated access should be strongly secured with multiple layers of defense.
As a habit, organizations should enforce strict Privileged Access Security (PAS) practices. This includes using dedicated admin accounts (separate from everyday user accounts), requiring MFA on every privileged login, limiting where and when these accounts can be used, and continuously auditing their activity.
In practice, this looks like ensuring admin-level accounts are always challenged with MFA and policy checks, even when they’re accessing systems like databases or remote servers that don’t normally enforce MFA. You can also implement adaptive policies (for instance, only allow domain admin login from a hardened jump-host, or only during certain hours).
For non-human privileged accounts (like service accounts that can’t do MFA), there is the concept of “virtual fencing” – essentially bounding their usage to expected systems and behaviors. By locking down privileged and sensitive accounts in these ways, you greatly reduce the odds that an attacker with a stolen admin credential can roam freely in your environment.
4. Maintain rigorous credential hygiene
Credential hygiene refers to the regular upkeep of accounts and passwords to eliminate the “low-hanging fruit” that attackers often exploit. A sobering case study from 2024 showed why this habit is so important: investigators found that 79.7% of the accounts used by attackers had been compromised years earlier and never had their passwords changed. In fact, hundreds of credentials stolen as far back as 2020 were still valid in 2024 because they were never rotated or disabled. Neglected credentials – old passwords, shared logins, dormant accounts – are a ticking time bomb. Implementing strong hygiene means regularly rotating passwords, retiring or updating any credential that is known to be exposed, and disabling accounts that are no longer needed.
Another critical aspect of credential hygiene is prompt offboarding of ex-employees. Stale user accounts that linger after someone leaves the company present an easy backdoor. Surveys have found that roughly half of businesses admit ex-employees’ accounts remain active after departure, sometimes for weeks or months. It’s no surprise that a significant number of organizations have suffered breaches due to former employee accounts that weren’t deprovisioned. Make it a habit to immediately deactivate or remove access when staff leave, and routinely audit for any “ghost” accounts in your directory.
A strong method to audit hygiene is to ensure continuous visibility into all accounts (human and non-human) and their usage. Being able to automatically discover accounts in your environment – including service accounts and unused logins – and flag those that have been inactive for a long period as “stale users” helps make sure you have an ongoing inventory of the identities that exist. Security teams can then swiftly review and either remove these accounts or apply policies to block any access attempts using them.
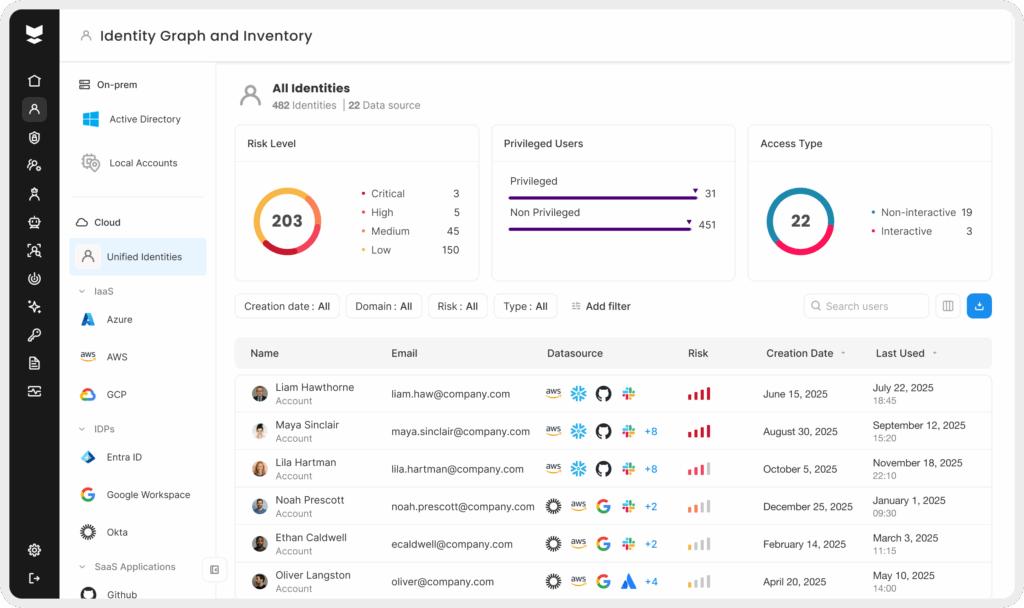
This kind of identity inventory and cleanup is vital: it closes the door on one of the easiest paths attackers use to infiltrate networks. In short, keeping credentials fresh, tightly managed, and cleaned up will drastically limit what an attacker can leverage, even if they do obtain some login secrets.
5. Continuously monitor and respond to identity threats
Even with preventive measures like MFA and good hygiene, organizations should operate under the assumption that credential compromises can still happen. Thus, a “healthy” security posture includes robust detection and response focused on identity.
Traditional security tools like XDRs may struggle to catch an attacker using legitimate credentials – these actions often blend in with normal user behavior and fly under the radar. It’s crucial to habitually monitor authentication logs and user activities across all systems for signs of suspicious behavior, and to retain those logs for long enough to investigate incidents. In fact, maintaining a centralized log collection with a proper retention policy is considered a basic security must-have to discover and analyze credential attacks. Many breaches that went undetected for months (or years) could have been identified much earlier if organizations had been aggregating login audit trails and alerting on anomalies.
To make this habit feasible, leverage tools that provide unified visibility and smart analytics on identity events. Silverfort’s platform, for example, acts as a centralized brain for monitoring all authentication traffic in real time. It uses machine learning and behavioral analytics (UEBA) to detect when a user’s access patterns deviate from the norm, which can indicate a compromised account. If an employee’s account suddenly attempts logins in strange locations or tries to access unusual resources, Silverfort will flag or automatically block that activity, preventing the attacker from escalating further. Moreover, Silverfort’s console gives security teams a live identity inventory and activity feed, so they can quickly spot and investigate any suspicious account usage.

Cultivating this level of awareness – and rehearsing incident response plans for credential breach scenarios – ensures that even if one defensive layer fails, you can promptly detect and contain the threat before it mushrooms into a full-blown breach.
Taking action on the 5 essential habits
Credential breaches continue to be a top cyber threat, but adopting these five security habits can significantly strengthen your organization’s defenses.
By requiring MFA universally, treating every access attempt with Zero Trust, locking down high-impact accounts, keeping your identity store clean, and monitoring continuously, you create multiple layers of protection that attackers must overcome.
None of these habits are “set and forget” – they require ongoing diligence and the right tools to support them.
This is where unified, identity-first security platforms can be a game-changer.
They’re purpose-built to help you embed these healthy security practices into your environment: enforcing MFA and conditional access everywhere, safeguarding privileged and legacy accounts, illuminating blind spots like stale users, and continuously watching for threats.
With strong habits and identity-first security capabilities working in tandem, enterprises can dramatically reduce the risk of credential-based breaches and ensure that a stolen password never easily translates into a successful attack.
To learn more about how to put incorporate these healthy habits into your cybersecurity strategy, download our guide “The Identity Security Playbook.”

