
Secure every transaction. Protect every customer.
Ransomware actors target retailers to move laterally, disrupt operations, and steal customer data. Silverfort stops them in real time, blocking malicious access from compromised users and service accounts before attackers can reach payment systems, POS networks, or customer records.
“With Silverfort, we enforce MFA on critical systems, protect AD service accounts, and secure privileged access—without disrupting users. It gives us confidence in who's accessing our systems and helps us stay ahead of identity-based attacks and ransomware risks.”
Head of IAM, Major Multinational Retailer
Identity is where cyber resilience ends—and where attackers strike first.
With Silverfort, retailers can defend against identity-first attacks with frictionless identity security, blocking ransomware spread paths in real time—even across the most complex, hybrid retail environments.
Granular visibility into every account
Gain a centralized view of all your user accounts and their access trail across POS networks, loyalty platforms, supplier portals, inventory tools and other critical resources.
MFA everywhere
Enforce MFA policies on all user access to AD managed resources, whether it’s carried locally or remotely with command-line access tools or RDP.
Rapid incident response
Expedite and optimize your incident response with the ability to freeze all access in a single click and automate the detection of compromised accounts with full disclosure of the attack’s path.
Protect your retail environment with ease and efficiency.
From in-store systems to e-commerce platforms, secure every identity across your retail operations—without slowing down your business.
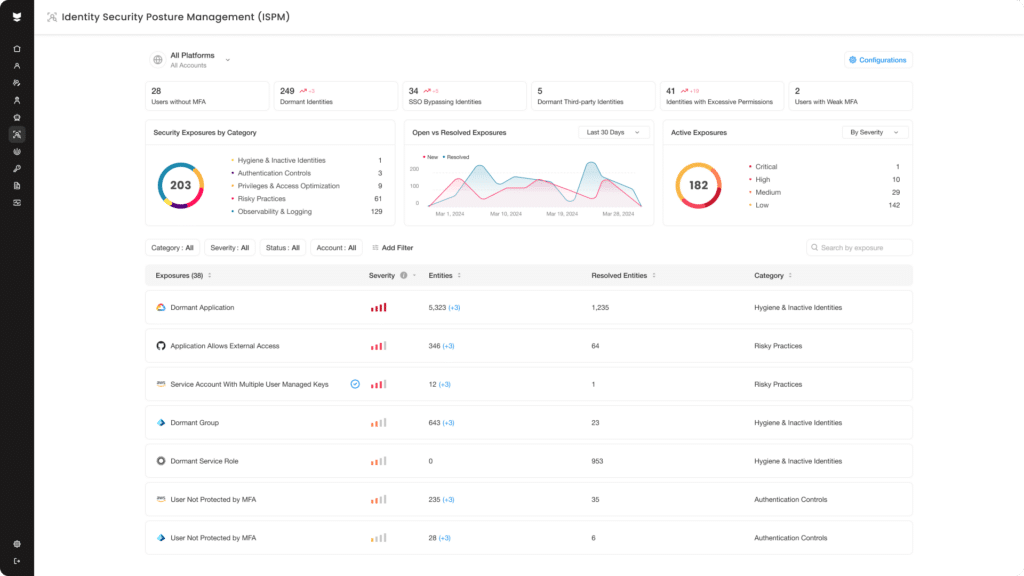
Enhance identity resilience
Discover and resolve the hidden gaps that expose employee and vendor accounts to credential compromise, privilege escalation, or lateral movement—across both physical and digital storefronts.
Extend MFA to all users and access points
Apply MFA to all critical retail systems—including file shares, legacy POS applications, databases, and IT infrastructure—even those previously out of reach.
Secure your service accounts
Automatically discover and lock down service accounts so they can access only what they’re meant to—blocking attackers from hijacking them to move laterally across store networks and backend systems.


