A vulnerability in Windows Print Spooler could allow for remote code execution as “System” by authenticated domain users on Windows systems. Details and proof-of-concept for the vulnerability have been leaked on the internet. The vulnerability is being called “PrintNightmare.” Print Spooler, which is turned on by default in Microsoft Windows, is a Windows service that is responsible for managing all print jobs sent to the computer printer or print servers.
Successful exploitation of this vulnerability could open the door to complete system takeover by remote adversaries. A remote, authenticated attacker could run code with elevated rights on a machine with the Print Spooler service enabled.
When Microsoft released an advisory about a similar vulnerability in the Print Spooler (CVE-2021-1675), security researchers accidently released details of PrintNightmare (CVE-2021-34527). An attacker can exploit this vulnerability to take control of an affected system.
Silverfort Protection Against PrintNightmare Exploitation
Silverfort’s Unified Identity Protection can deliver full protection against such exploits with a simple risk-based authentication policy, applied to systems running the Print Spooler service. In this manner, any malicious access attempt access attempt by adversaries will trigger an MFA notification to the actual compromised user, which in practice would eliminate the possibility of leveraging this vulnerability to gain access into additional resources.
Silverfort’s solution can enforce modern secure access controls such as MFA on common access interfaces in Active Directory environment, materially increasing their resilience to identity-attacks that utilize compromised credentials to access enterprise resources.
“Silverfort’s ability to enforce modern secure access controls such as MFA on common access interfaces in Active Directory environment is a game changer,” said Yaron Kassner, Co-Founder and CTO of Silverfort. “Nearly all post-exploitation TTPs rely on the assumption that their targets lack the ability to prevent malicious authentications in real time. The PrintNightmare exploit is another great example of the security gap we’re addressing.”
Silverfort Security Guidance
Reduce the Attack Surface
- Scan on all machines in your environment to check where Windows Print spooler service is enabled. You can start by scanning your domain controllers with Silverfort’s free Vulnerability Assessment tool.
- Disable the Windows Print spooler service in Domain Controllers and other systems that do not print.
- Disable inbound remote printing from computers that do print, but are not accessed remotely for printing.
- Reduce membership as much as possible to the groups indicated in Microsoft’s guidance (see the Mitigations Section).
- Disable inbound remote connections in all machines accept printing servers.
Create a Risk-Based Policy
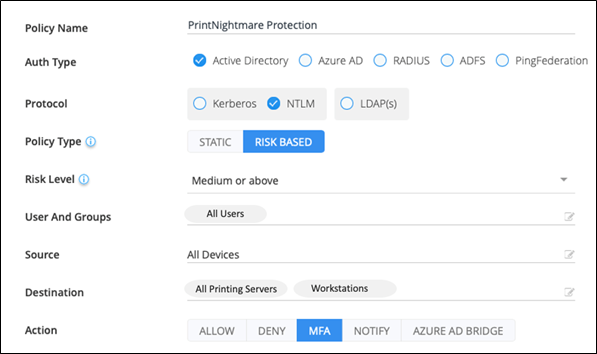
Assign a risk-based access policy that enforces MFA on any NTLM connection to machines where Windows Print spooler service is enabled. After you follow the guidance above, this should be limited to printing servers. Create a policy for any user with risk score ‘Medium’ and above. The published exploits of PrintNightmare use a pass-the-hash attack on NTLM for connections, so this policy would block high-risk access by any attacker attempting to exploit the vulnerability to access target resources.
This is what the policy would look like:
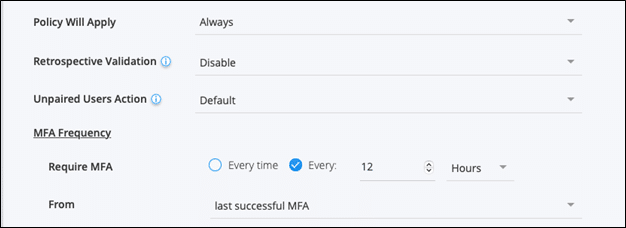
In the Advanced Settings, configure the policy to require MFA every 12 hours:
To defend against alterations of these exploits, you can also create a policy for CIFS Kerberos tickets.
Want to learn more? Schedule a demo with one of our experts.